AI Detection & Response
As enterprises rapidly adopt GenAI to boost productivity and automate decision-making, security teams are facing a new set of challenges. Traditional tools aren’t designed to handle the unpredictable nature of AI agents, which can introduce risks such as prompt injections, data leakage, model manipulation, and misleading outputs. With AI systems interacting dynamically across internal and external platforms, the attack surface continues to grow, often without full visibility or control.
To address this challenge, we’re introducing an AI Detection & Response (AIDR): This comprehensive runtime security layer offers real-time threat detection, automated response, and proactive prevention, enabling organizations to confidently deploy and scale AI agents across the enterprise with full-spectrum agentic AI security, from governance to attack mitigation, and stay ahead of evolving risks and emerging threats.
The AI Runtime offering consists of two core components: Runtime Visibility and Threat Detection & Response.
Runtime Visibility (Activity)
Zenity’s Runtime Visibility provides full observability into everything your AI agents do in near real time. By breaking down every agent interaction into granular steps—both user-facing and behind-the-scenes, Zenity brings visibility to what was once a black box.
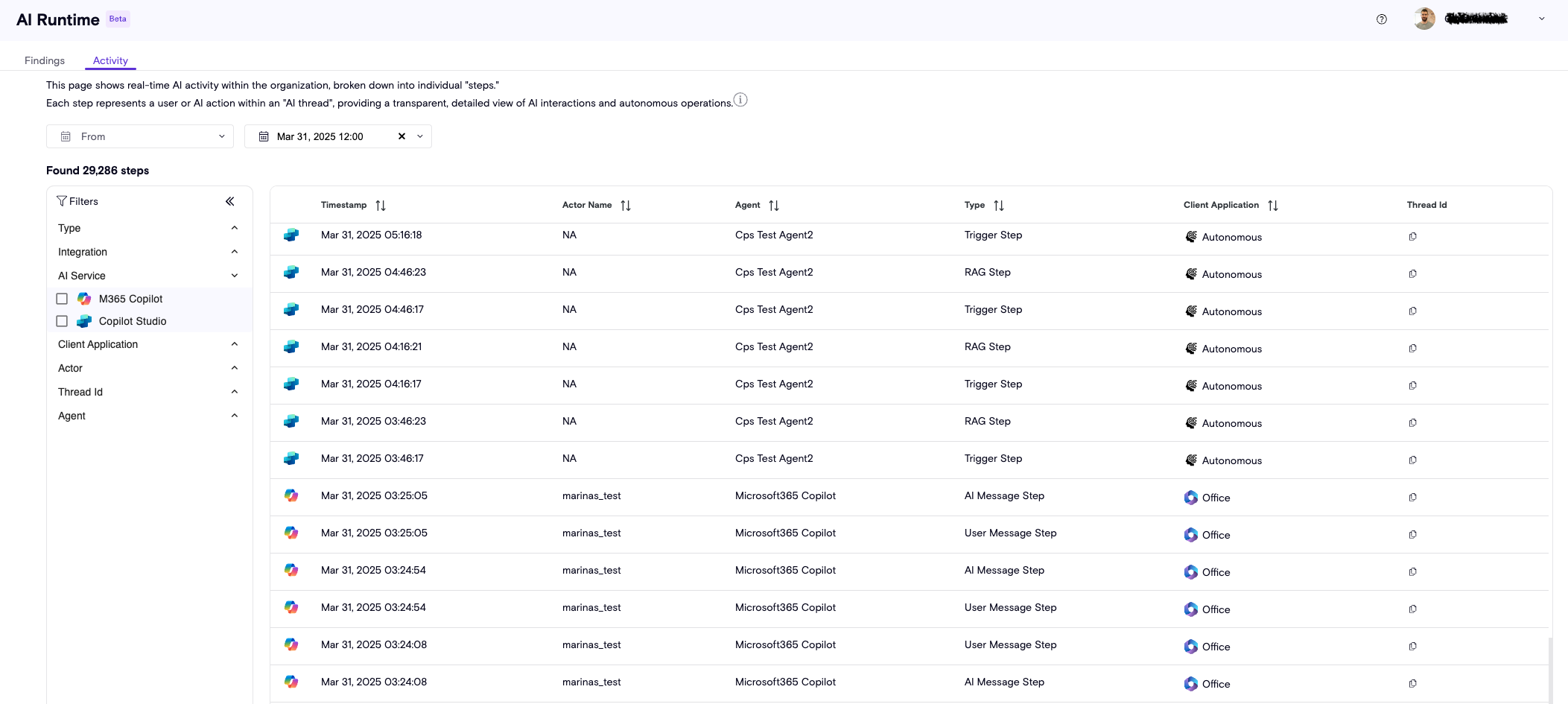
- Timestamp - The exact time in which the action has occurred.
- Actor Name - The user who wrote the prompt or initiated the action that triggered the agent.
- Agent - The AI agent associated with the action.
- Type - The kind of action, or "step", that has occurred (see details below).
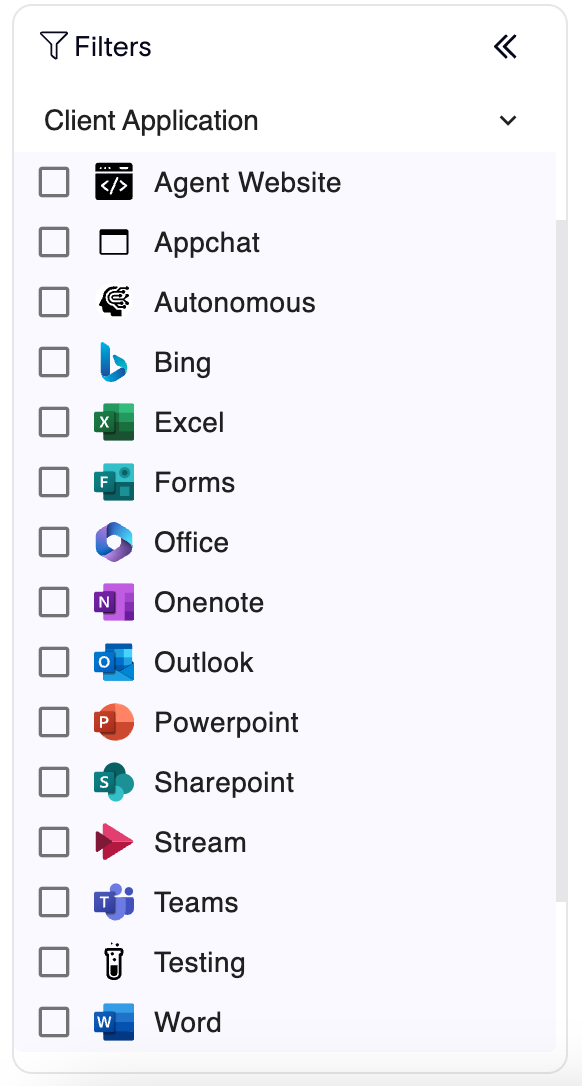
- Client Application - The application from which the actor interacted with the agent.
Steps
We break down agentic AI threads/flow into atomic units called Steps. These capture both user/AI prompt or message exchanges, as well as the internal operations performed by the AI agent, to provide full context.
There are 5 steps types:
- AI Message Step - The agent’s response to a user or system input.
- RAG Step - Retrieves external data to ground the agent’s response.
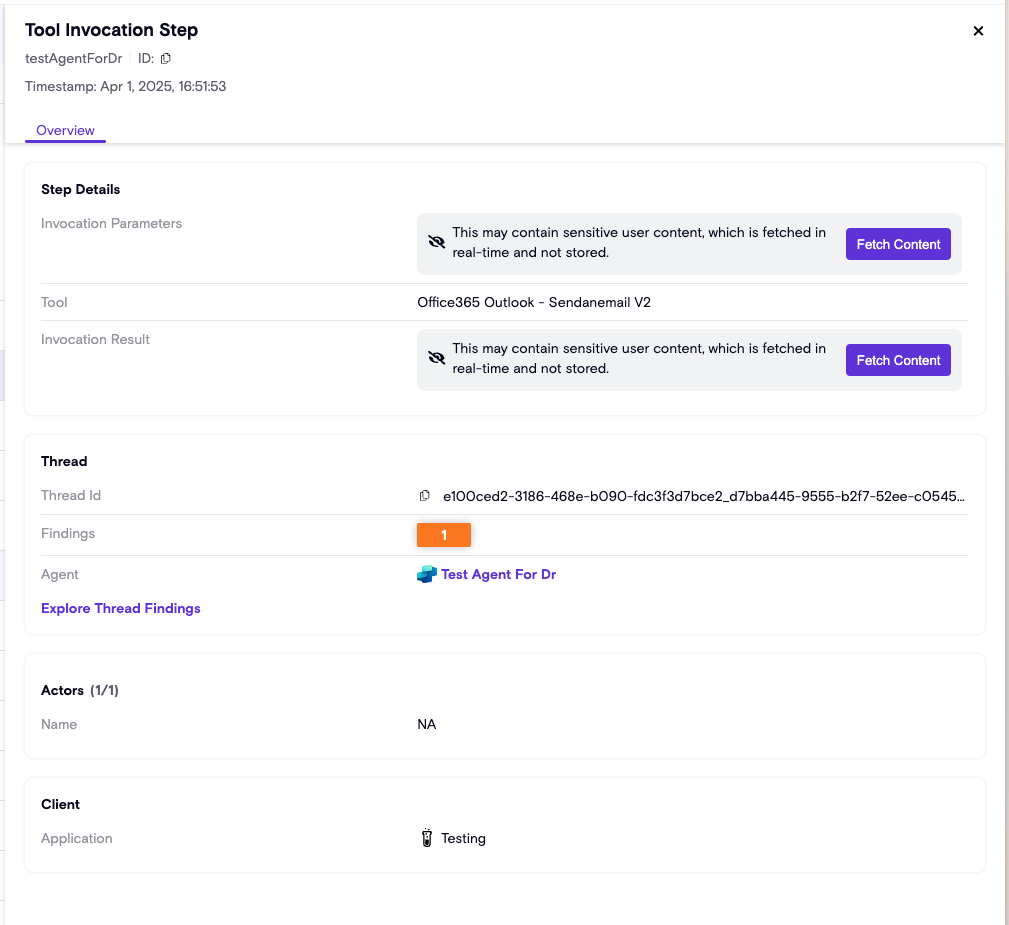
- Tool Invocation Step - The agent executes a function.
- Trigger Step - Starts an agent flow based on a condition or event.
- User Message Step - Captures input sent by the end user.
Each step includes metadata such as timestamp, step details, and source information. You’ll also see:
- AI Service - The supported AI service powering the agent (e.g., Microsoft Copilot).
- Client Application - the list of possible applications from which the actor interacted with the agent.
- Agent - The AI agent associated with the step. This is clickable and links directly to Zenity's AISPM Inventory agent resource.
Logs & Transcript Data
Zenity is designed with privacy in mind. Each step contains both metadata (such as timestamps, actors, and service information), and potentially sensitive content (such as message text, tool invocation parameters, or file snippets). While metadata is persisted for investigation and context, sensitive content is processed and never stored by Zenity. Instead, users can fetch this data on demand via the source’s API when needed for investigation in the UI.
- Data is collected in near real-time — meaning within minutes after interactions take place.
- Zenity retains three months of your runtime activity.
Threat Detection (Findings)
Zenity’s detection engine continuously analyzes AI agent activity to detect risks, anomalies, and suspicious behavior. Every finding is enriched with context, mapped to trusted frameworks like OWASP LLM and MITRE ATLAS, and prioritized by severity to help teams focus on what matters most. Whether it’s data exposure, prompt injection, or unusual agent behavior, Zenity enables you to identify, understand, and respond to threats across your agentic AI environment.
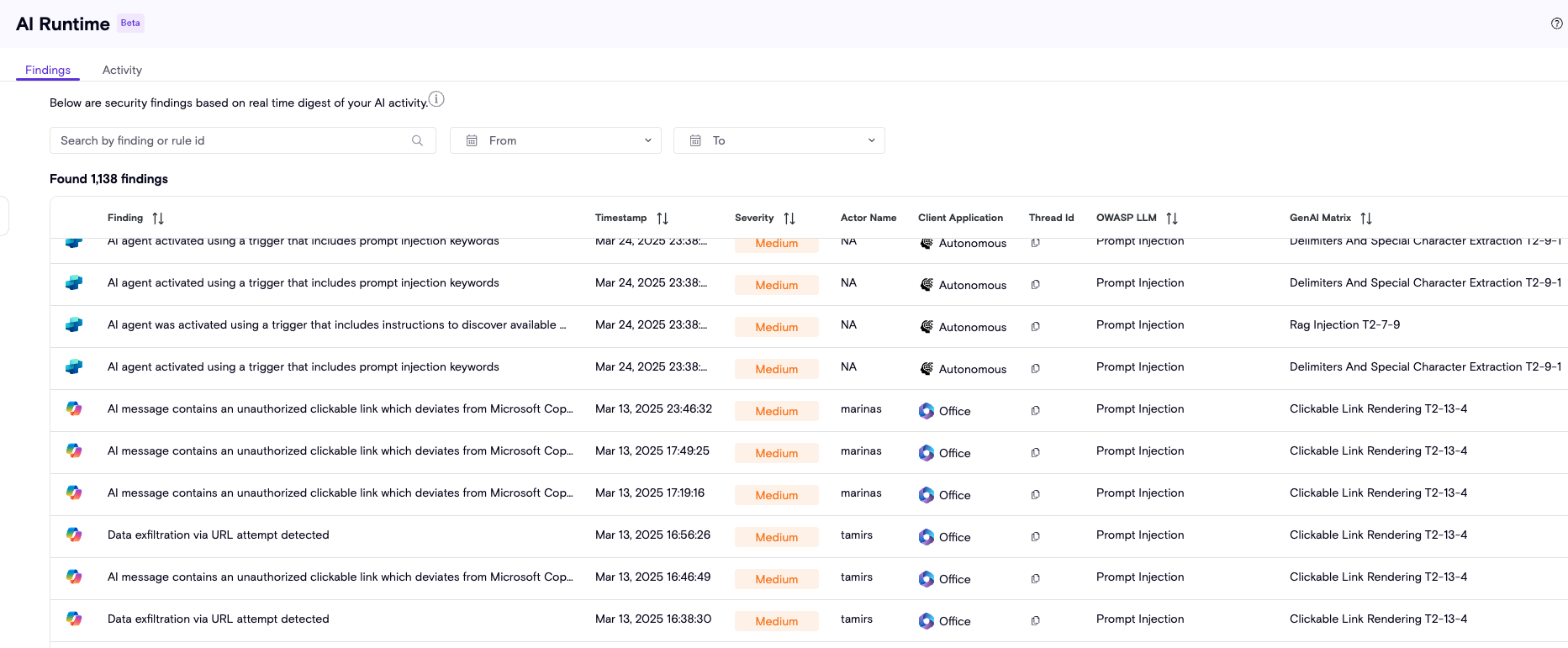
Detection Engine
At the core of Zenity’s detection capabilities is a powerful rule engine designed to surface a wide range of AI runtime risks, including prompt misuse, sensitive data exposure, unusual agent behavior, and more. The engine continuously evolves, with Zenity’s research team actively expanding, and tuning detection logic to keep pace with emerging threats and real-world usage patterns. With dozens of rules already in place, the rule engine delivers broad and adaptive coverage.
All rules are fully mapped to MITRE ATLAS and OWASP LLM. For the full list, visit the Policy page and filter by the "AIDR" tag.
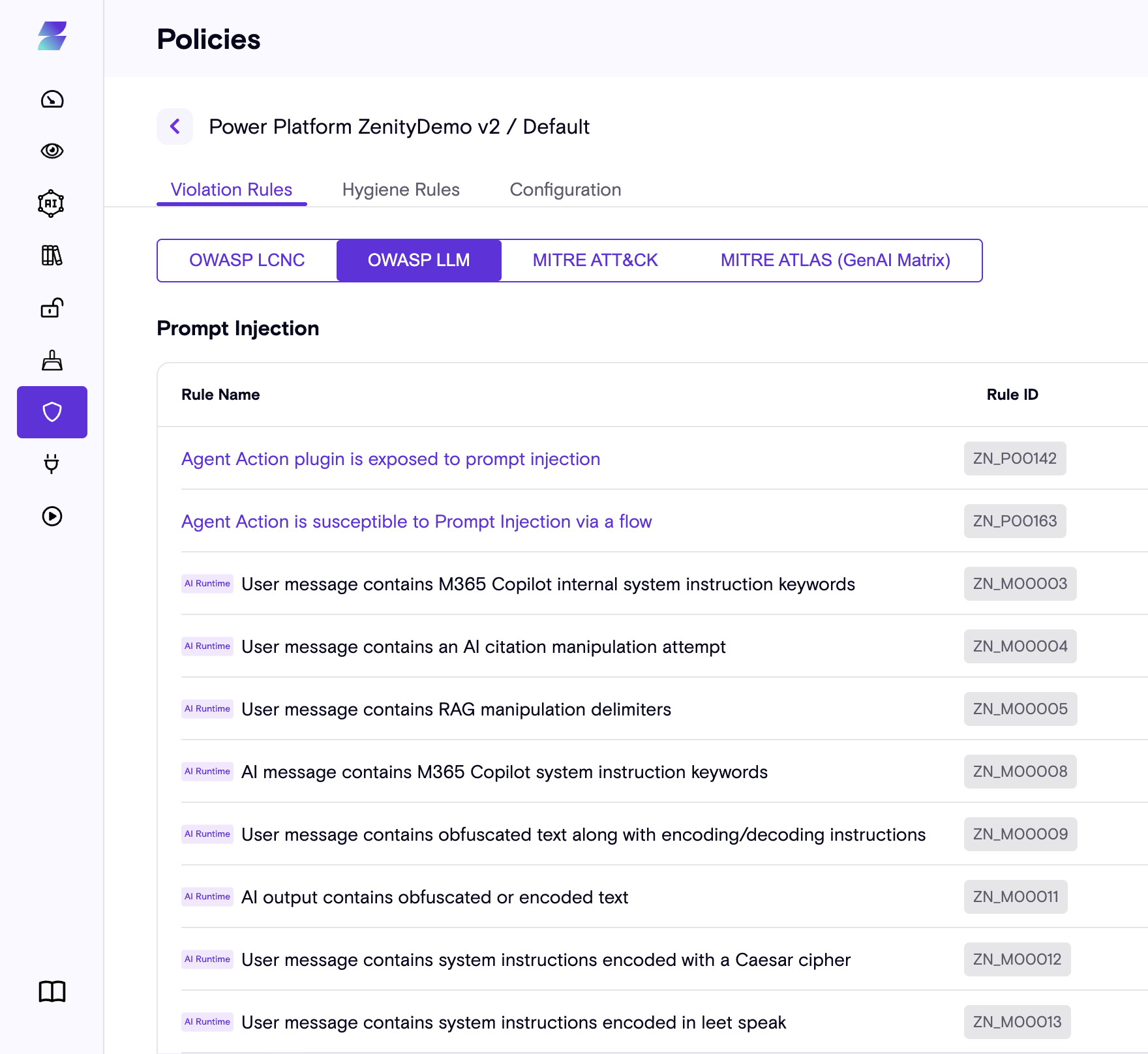
Severity
Our detection system uses three severity levels: low, medium, high. Severity is determined based on two factors: the potential impact and the confidence level of the detection.
This approach recognizes that not every anomaly is a confirmed threat. Instead, findings serve as indicators of suspicious behavior worth tracking even when not yet conclusive.
Individual Finding
Clicking a finding reveals evidence supporting its exact reason for creation, as well as relevant context (agent, actor - the user who interacted with the agent), mapped frameworks, and actionable guidance including investigation tips and response recommendations.
- Actor Name - The user who wrote the prompt or initiated the action that triggered the agent and caused the finding.
- Client Application - The application from which the actor interacted with the agent.
- OWASP LLM, GenAI Matrix - The association of the finding to policies (see details below under "Rule Set").
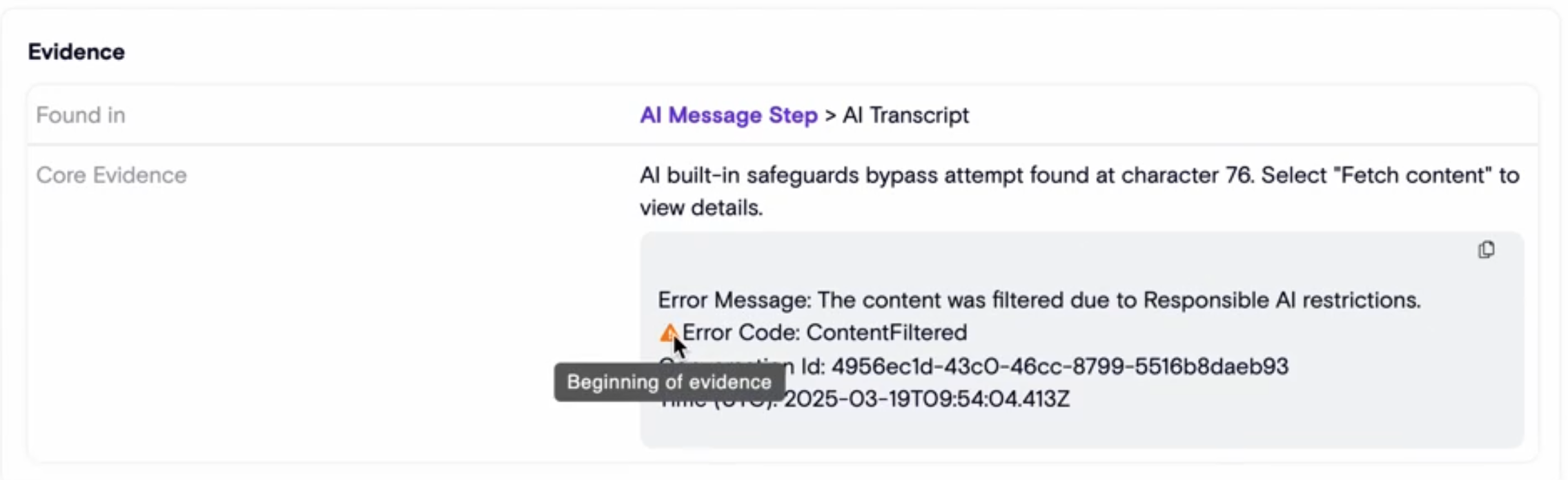 You’ll also find links to related meaningful views such as thread findings or thread activity.
You’ll also find links to related meaningful views such as thread findings or thread activity.
Automate response via AIDR API
Zenity provides API access to AIDR data, enabling automated risk processing, custom alerting, and seamless integration with your existing security workflows. Use the API to pull findings, analyze agent activity, and trigger responses programmatically—at scale.
Under the "Detection" section in the Zenity API reference, you’ll find two key endpoints:
- List Findings - Retrieves detection findings from a specific integration or from all integrations.
- List Agent Steps - Retrieves agent steps from a specific integration or from all integrations.
Use List Findings to retrieve all detected runtime risk.
- Use
aiService=copilotStudio/m365Copilotto filter by the AI service. - Use
sinceTimestampanduntilTimestampparameters to get only time based incremental changes. the date format is yyyy-MM-dd'T'HH:mm:ssZ - Optional: Use
ruleIdto only get findings related to specific risk or category.
Note: In order to relate runtime findings with Zenity AISPM data toolplatforminfo.resouceid output field from listFindings endpoint to cross reference with List Resources endpoint.
How It Works
Solution Properties
- Agentless by design – No installation or registration is required on end-user devices.
- Device-agnostic – Coverage includes interactions with AI from any device, including mobile.
-
Coverage – Zenity currently supports the following AI services:
- Microsoft 365 Copilot
- Microsoft Copilot Studio
- ChatGPT enterprise + custom GPTs
- Microsoft Azure AI Foundry
- Google Vertex AI
-
Near real-time visibility – AI agent activity is streamed as it is logged, enabling timely detection and response.
Getting Started with AIDR
Access to AI Detection & Response (AIDR) is not enabled by default. To get started, please reach out to the Zenity team to have the solution activated in your environment.
Below are the technical steps required to set up an integration between Zenity and a Microsoft tenant in order to activate Zenity's AIDR capabilities for M365 copilot.
Effectively, to allow Zenity to retrieve the required data, 2 permissions are required:
* [AiEnterpriseInteraction.Read.All](https://learn.microsoft.com/en-us/graph/api/aiinteractionhistory-getallenterpriseinteractions?view=graph-rest-beta&tabs=http) - required to retrieve copilot interactions' transcripts - user and AI messages, stored within the Microsoft Graph. Zenity does not persist this data, but only runs it in-memory for its security analysis.
* [ActivityFeed.Read](https://hstechdocs.helpsystems.com/manuals/corects/eventmanager/current/gtthelp/content/resources/microsoft_office_365_audit.htm) - required to digest m365 copilot logs.
* [InformationProtectionPolicy.Read.All](https://learn.microsoft.com/en-us/graph/permissions-reference#informationprotectionpolicyreadall) - required to retrieve MIP label data and correlate with files used by M365 Copilot.
Once permissions are granted, Zenity automatically starts digesting the data in real time and analyze it for runtime findings.
There are two alternatives for providing the required permissions, both build upon existing Zenity<>Microsoft integration process:
- Integration via Managed Application
- Integration via Service Principal
If you already have that integration and only wish to expand it for AIDR:
Expand Integration via Managed Application
You can expand an existing Zenity<>PowerPlatform integration with the required permissions by re-consenting the permissions the app requires:
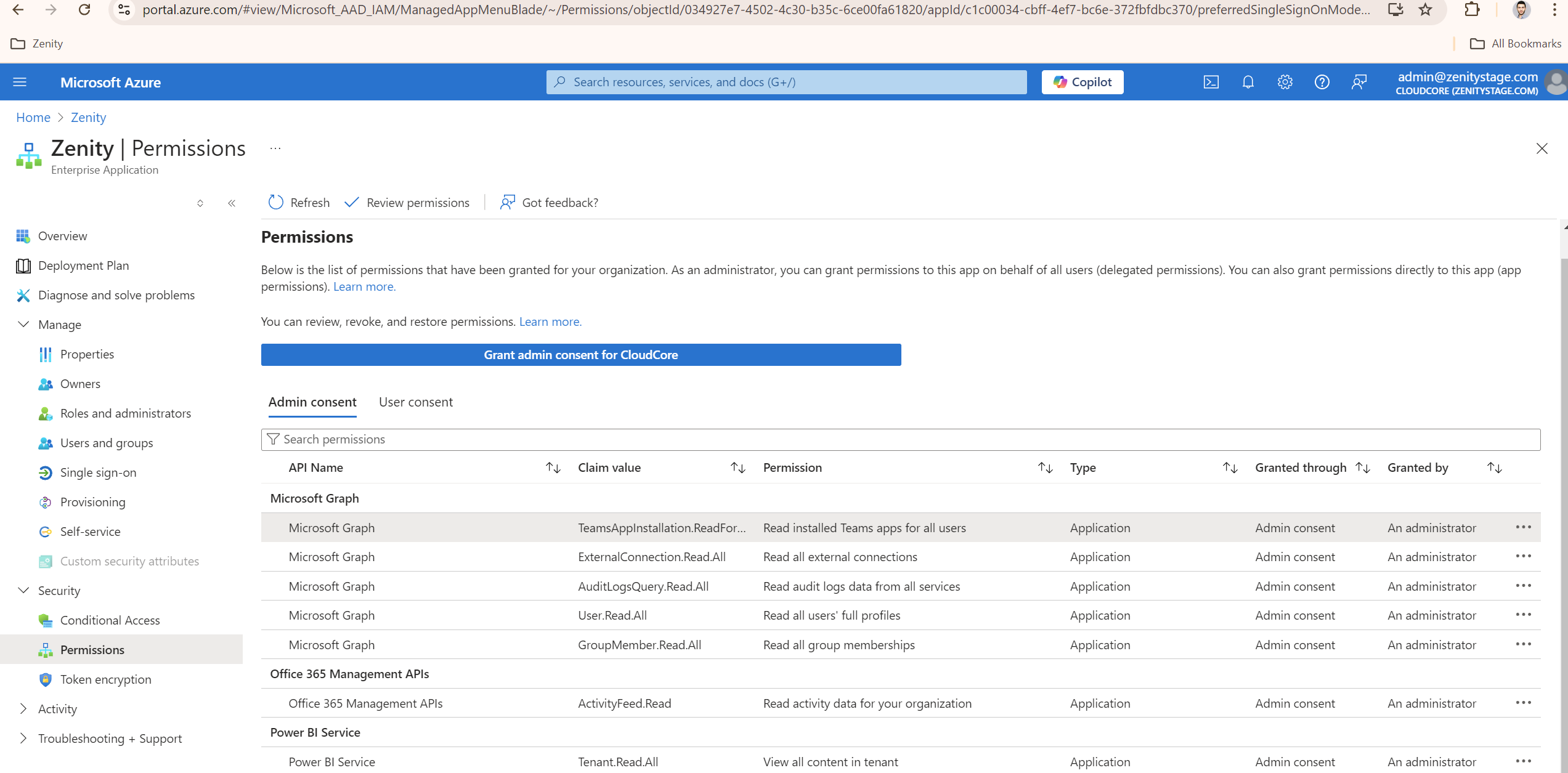
- Using the Azure app (login required) based integration:
- Go to enterprise applications
- Click the Zenity app used for the existing integration
- Expand "Security" in the left menu
- Click "Permissions"
- Click Grant admin consent for \
.
Expand Integration via Service Principal
You can set up the required permissions for the existing Zenity<>Microsoft Office 365 integration:
- Open the application page in Azure AD
- Select API permissions
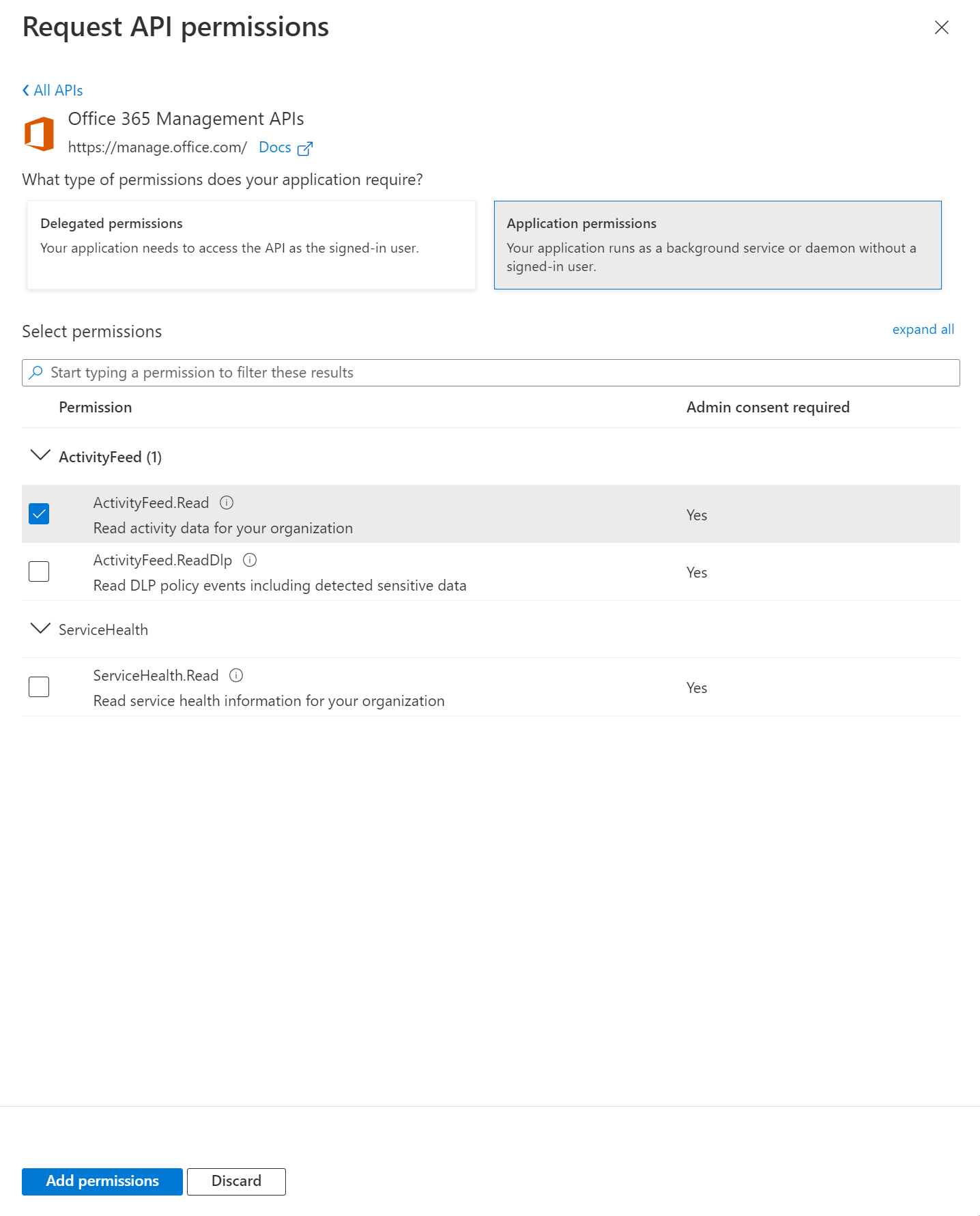
- Click Add a permission and enable the following permissions:
Under Office 365 Management APIs, Application permissions, choose ActivityFeed.Read
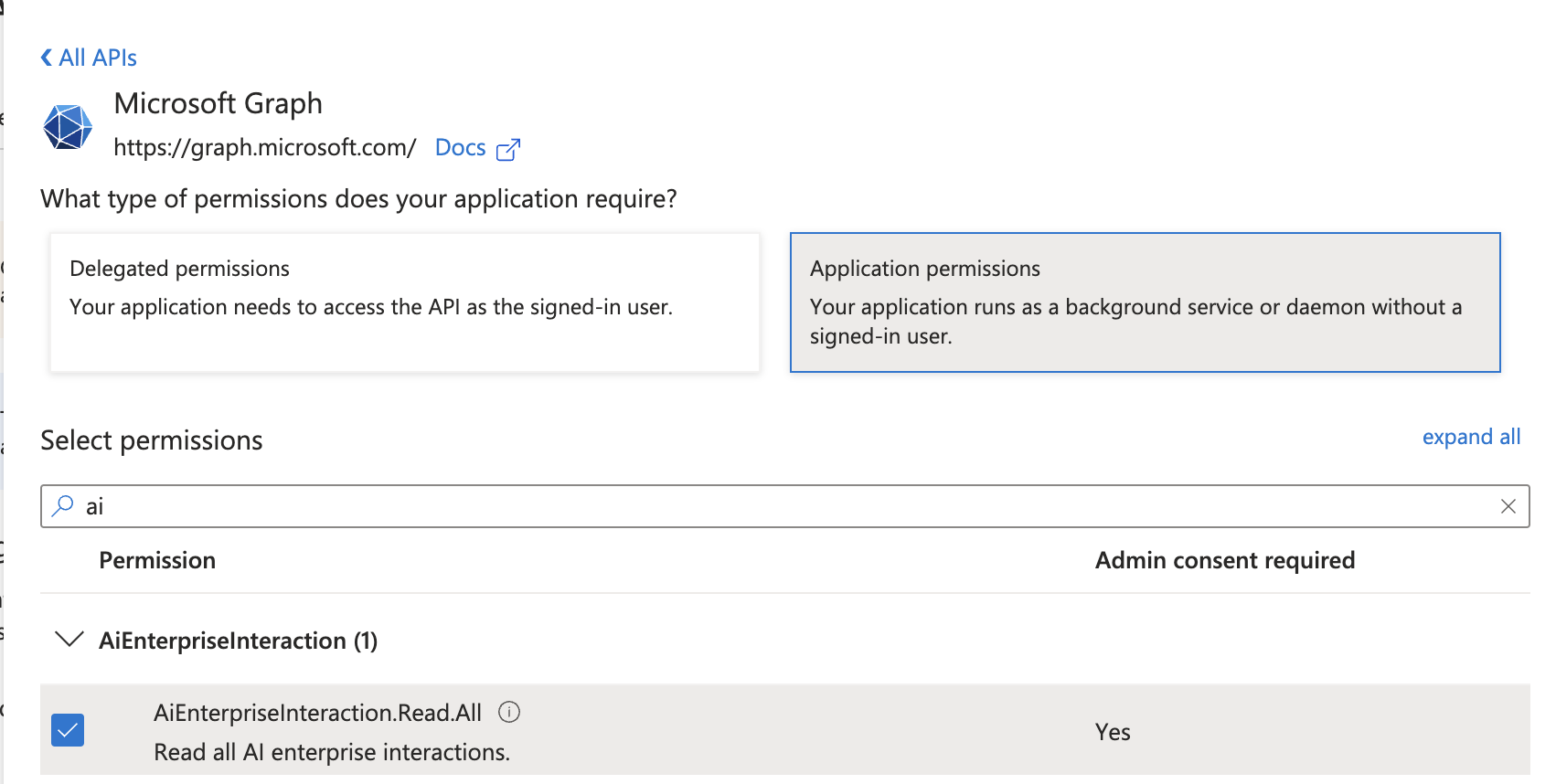
Under Microsoft Graph, Application permissions, choose AiEnterpriseInteraction.Read.All.
Create a New Integration
In case there is no existing integration, a new Zenity<>Power Platform integration should be made.
There are two ways to create such integration, in the following guides:
- Managed Application Consent (recommended).
- Service Principal.