Zenity December-2025
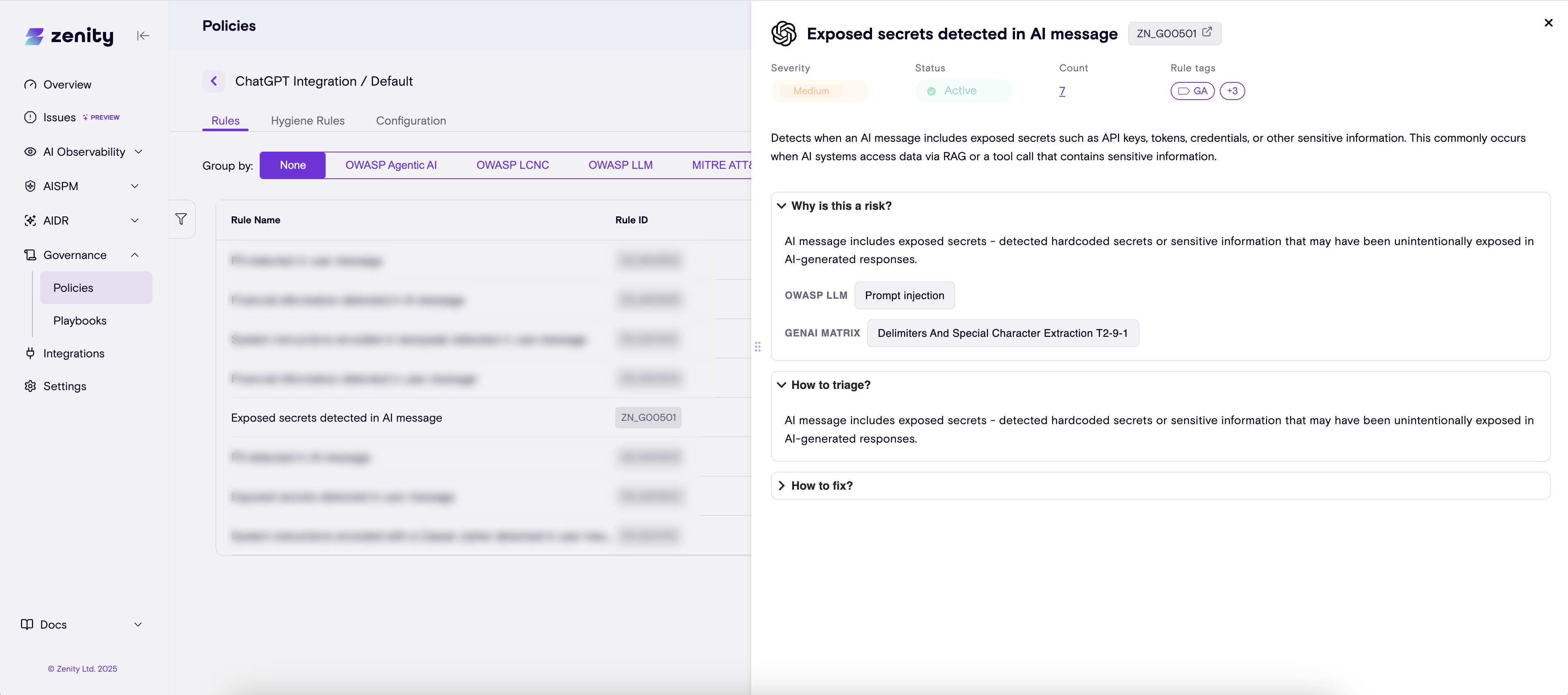
Introducing the Rule Details Side Panel
With the new Rule Details Side Panel, clicking any rule now opens a rich view showing its full metadata and context:
- What the rule detects
- Why it matters
- How it maps to industry frameworks
- Recommended steps to fix or triage
Faster decisions, clearer explanations, and smoother workflows — all from one place.
UX Enhancements
Playbooks
- Playbook actions: A new column was added to the Playbooks table showing the actions
- Playbook description: Hovering over the Playbook name shows the description, hinting on th its purpose
Overview Dashboard
- Open Violations & Agents by Platform widgets are now clickable and lead you to the relevant filtered data
Zenity November-2025
26-Nov-2025
Rule enhacements:
| Rule ID | Rule Title | AI Service | Change |
|---|---|---|---|
| ZN_M00501 | Exposed secrets detected in AI message | M365 Copilot | Excludes Base64-encoded images that match secret detection patterns but aren't genuine secrets. |
23-Nov-2025: AI Detection & Response Rules Now Generally Available
Runtime detections require ongoing refinement as threat landscapes evolve. After demonstrating consistent value and stability, the following AI Detection & Response (AIDR) rules are now generally available with improved clarity in their naming:
| Rule Title | Rule ID(s) | AI Service(s) |
|---|---|---|
| Destructive query executed by AI agent | ZN_P00253 | Copilot Studio |
| Disallowed email address detected in AI agent trigger content | ZN_P00239 | Copilot Studio |
| Disallowed email sender triggered AI agent | ZN_P00232 | Copilot Studio |
| Disallowed recipient domain detected in email sent by AI agent | ZN_P00236 | Copilot Studio |
| Exposed secrets detected in AI message | ZN_V00501, ZN_F00501, ZN_P00501, ZN_M00501, ZN_G00501, ZN_C00501 | Vertex AI, Microsoft Foundry, Copilot Studio, M365 Copilot, ChatGPT Enterprise, Agentcore |
| Exposed secrets detected in user message | ZN_V00500, ZN_F00500, ZN_P00500, ZN_M00500, ZN_G00500, ZN_C00500 | Vertex AI, Microsoft Foundry, Copilot Studio, M365 Copilot, ChatGPT Enterprise, Agentcore |
| Financial information detected in AI message | ZN_V00505, ZN_F00505, ZN_P00505, ZN_M00505, ZN_G00505, ZN_C00505 | Vertex AI, Microsoft Foundry, Copilot Studio, M365 Copilot, ChatGPT Enterprise, Agentcore |
| Financial information detected in user message | ZN_V00504, ZN_F00504, ZN_P00504, ZN_M00504, ZN_G00504, ZN_C00504 | Vertex AI, Microsoft Foundry, Copilot Studio, M365 Copilot, ChatGPT Enterprise, Agentcore |
| PII detected in AI message | ZN_V00503, ZN_F00503, ZN_P00503, ZN_M00503, ZN_G00503, ZN_C00503 | Vertex AI, Microsoft Foundry, Copilot Studio, M365 Copilot, ChatGPT Enterprise, Agentcore |
| PII detected in user message | ZN_V00502, ZN_F00502, ZN_P00502, ZN_M00502, ZN_G00502, ZN_C00502 | Vertex AI, Microsoft Foundry, Copilot Studio, M365 Copilot, ChatGPT Enterprise, Agentcore |
| Promptware detected in Loops file snippet | ZN_M00041 | M365 Copilot |
| Reconnaissance query executed by AI agent | ZN_P00254 | Copilot Studio |
| Sensitive database name detected in AI agent action | ZN_P00252 | Copilot Studio |
| Server-side MCP secrets exposed by AI agent | ZN_P00277 | Copilot Studio |
| Suspicious database cluster name detected in AI agent action | ZN_P00251 | Copilot Studio |
| Suspicious IP address used to access AI agent | ZN_M00020 | M365 Copilot |
| System instructions encoded in leetspeak detected in user message | ZN_V00013, ZN_F00013, ZN_P00513, ZN_M00013, ZN_G00013, ZN_C00013 | Vertex AI, Microsoft Foundry, Copilot Studio, M365 Copilot, ChatGPT Enterprise, Agentcore |
| System instructions encoded with a Caesar cipher detected in user message | ZN_V00012, ZN_F00012, ZN_P00512, ZN_M00012, ZN_G00012, ZN_C00012 | Vertex AI, Microsoft Foundry, Copilot Studio, M365 Copilot, ChatGPT Enterprise, Agentcore |
| Unintended RAG access due to AI content misinterpretation | ZN_M00045 | M365 Copilot |
Deprecations and updates:
- "User message includes code with exposed secrets" (ZN_F00044, ZN_P00044, ZN_M00044) is deprecated. Use the new "Exposed secrets detected in user message" rule instead.
- "User message contains sensitive information (PCI/PHI/PII)" (ZN_M00006, ZN_F00242, ZN_V00242, ZN_P00242, ZN_G00242) is deprecated. Use the new "PII detected in user message" and "Financial information detected in user message" rules instead.
- "AI message contains sensitive information (PCI/PHI/PII)" (ZN_M00010, ZN_F00010, ZN_V00010, ZN_P00241, ZN_G00010) is deprecated. Use the new "PII detected in AI message" and "Financial information detected in AI message" rules instead.
Zenity October-2025
⭐ Highlights
Playbooks Now Support Existing Violations: Brownfield Remediation Campaigns
Enterprise security teams often need to run remediation campaigns on existing violations that have accumulated over time. Zenity's new playbook capabilities now enable customers to run comprehensive remediation campaign handling either existing, new or all violations.
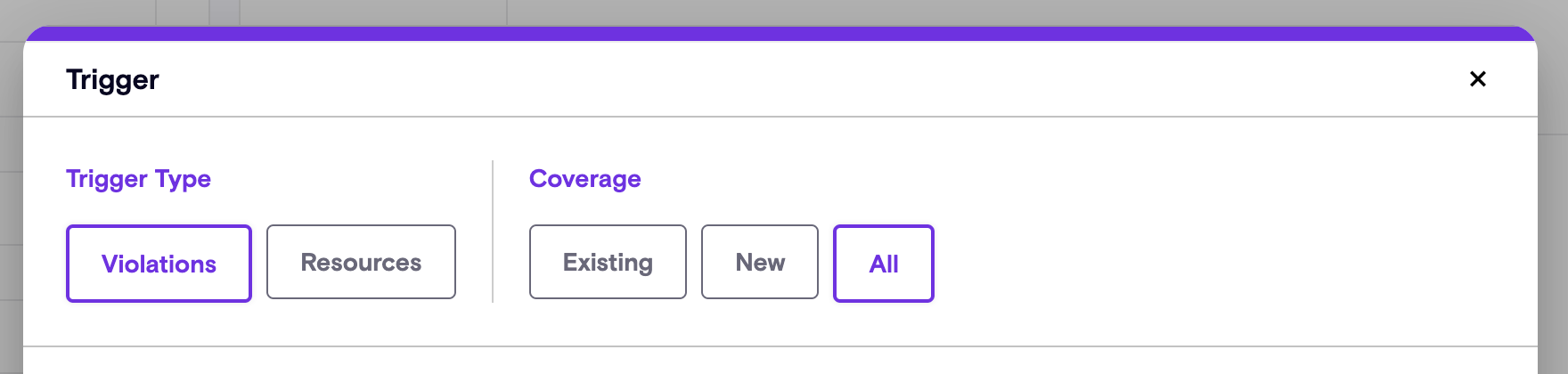
New Playbook Coverage Types
Playbooks now adapt their execution based on the selected coverage type:
- Coverage = Existing: Triggers when the playbook is created or edited in the UI, acting on existing violations/resources
- Coverage = New: Triggers at the end of scans, and continously monitors for new violations/resources
- Coverage = All: Combines both behaviors for comprehensive coverage
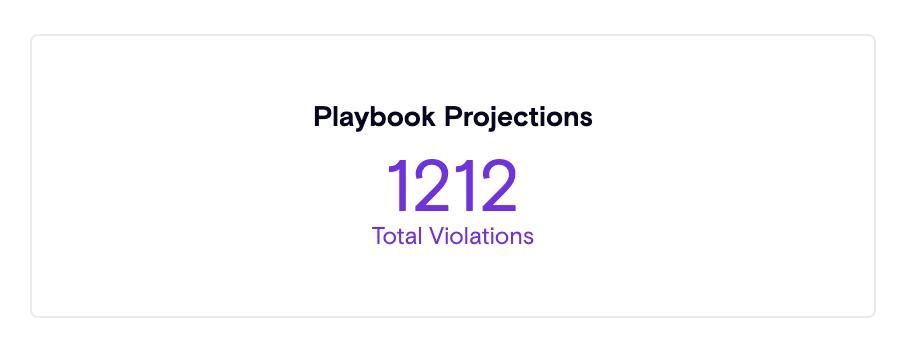
Playbook Projections
During playbook creation, users can now see the number of affected violations that would be processed. Clicking on the projection amount provides a direct link to the filtered violations page, enabling users to review and validate the scope before activating the playbook.
Key Benefits
- Unified Remediation: Single platform with a standardized approch for both new and existing violation remediation
- Operational Efficiency: Eliminates need for external automation platforms for existing violations
- Better Visibility: Granular projections and filtering capabilities
This enhancement elevates Zenity into a comprehensive remediation platform, empowering organizations to address both new and existing violations and fully meet the diverse security needs of the enterprise.
Example Use Cases Beyond Remediation
While the primary goal of playbooks is to remediate existing violations, Zenity's new playbook capabilities unlock a range of additional use cases that empower security teams to operate more efficiently and strategically:
-
Bulk Labeling of Violations for Future Analysis:
Use playbooks to apply custom labels to large sets of violations in bulk. This enables teams to categorize violations by risk, business unit, or remediation status, making it easier to filter, report, and analyze trends over time. -
Re-running Past Executions Using Violation Labels:
With violation labels in place, teams can easily re-run playbooks on specific subsets of violations - whether those were previously remediated, failed, or skipped. This is especially useful for re-attempting failed playbook executions, auditing successful remediations, or targeting violations with shared characteristics. -
Test-Running Playbooks on a Handful of Violations:
Before launching a wide-scale remediation campaign, teams can use playbooks to "test-run" actions on a small, controlled set of violations. This allows for validation of playbook logic, assessment of potential impact, and fine-tuning of remediation steps—reducing risk and ensuring confidence before broader rollout.
These advanced use cases help organizations maximize the value of Zenity playbooks, supporting not just remediation, but also investigation, validation, and continuous improvement of security operations.
AI Detection & Response Findings Labels
Zenity introduces Labels for AI Detection & Response (AIDR) Findings, providing tools to organize, track, and automate management of runtime detections. Findings can now be labeled using existing Zenity system and custom labels known from the Zenity AISPM, with full support for filtering and automation, which can be applied manually in the UI or programmatically via API, and Playbooks can automatically assign labels as part of response workflows. This makes it easier to mark false positives, assign findings to the right teams, and focus on new or unresolved ones.
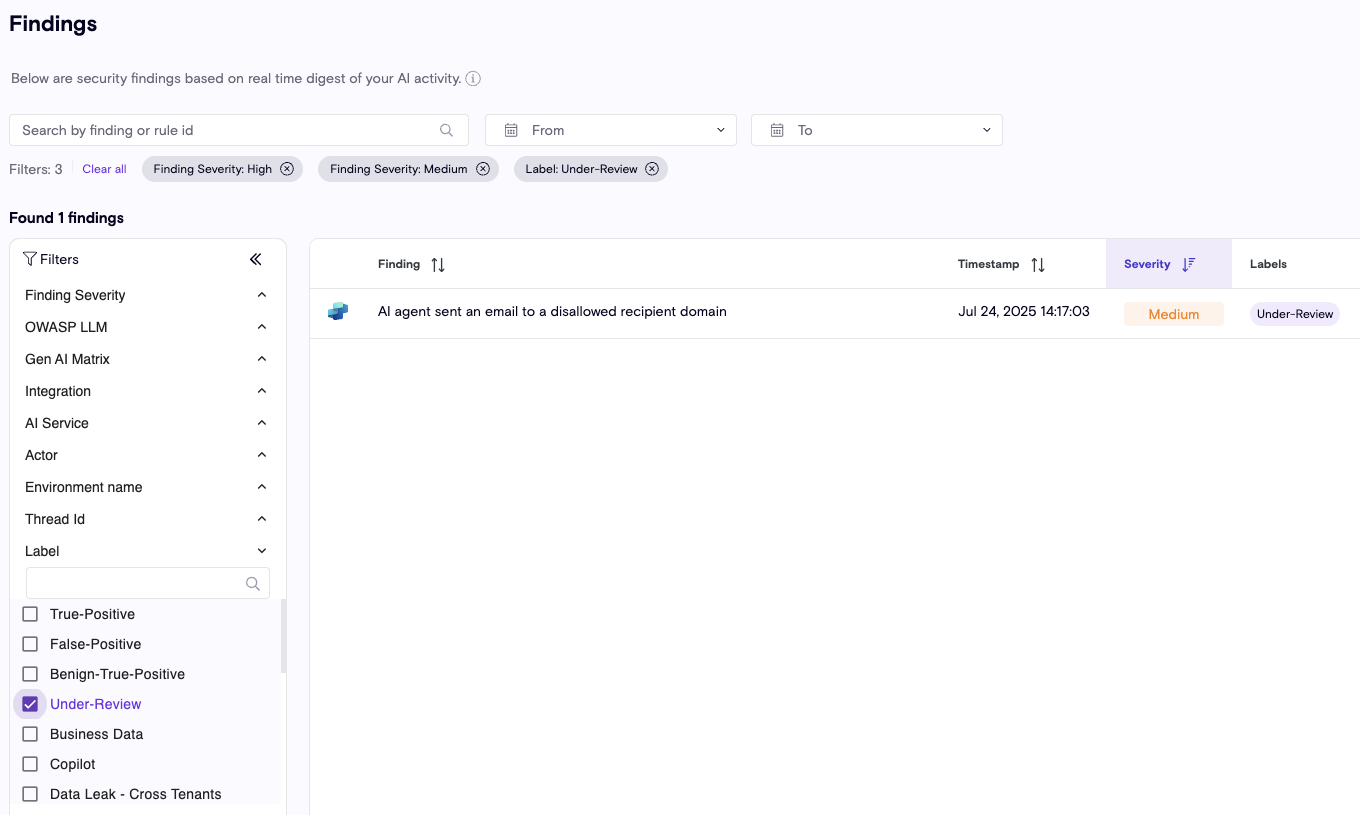
Audit Logs
Audit Log gives you full visibility into key actions taken across your environment. This feature helps admins and security teams monitor activity, ensure accountability, and streamline compliance reporting.
What’s new?
- Track who made a change, what was changed, and when it happened.
- Filter and search logs to quickly find relevant events.
- Export logs for audits, investigations, or compliance requirements.
With the Audit Log, you can maintain transparency, improve oversight, and accelerate troubleshooting across your organization. The Audit log can be found under the Settings page and can be accessed only by an Admin (data is collected from Sep 15th, 2025).
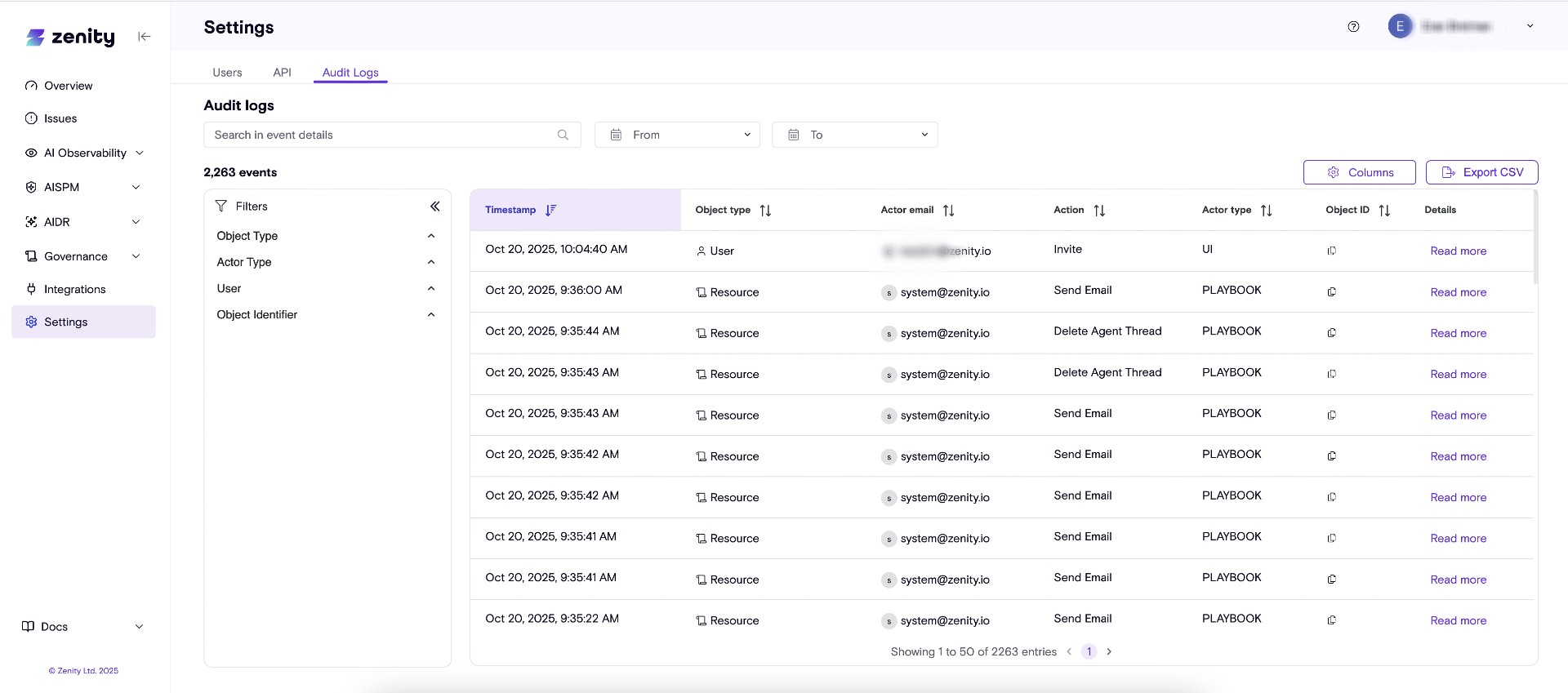
AIDR Thread View
This new view under Findings page introduces a major user experience uplift, allowing users to review full agent threads (conversations/flows), including all activity and runtime risk detected in one unified view.
Findings Page Enhancements
- Findings are now automatically grouped by threads, providing meaningful context for AI activity
- Easily toggle between the new thread-grouped view and the classic individual findings list
New Thread Side Panel
- Click any thread to open a comprehensive side panel view
- Activity timeline displayed on the right, with all detected risks on the left
- Expand findings directly within the panel for detailed review—no more navigating back and forth
Smart Focus Features
- Auto-focus on risk: Filter to show only findings related to risky activity for faster triage
- Contextual navigation: Click on step types within a finding to automatically scroll to the relevant activity in the thread
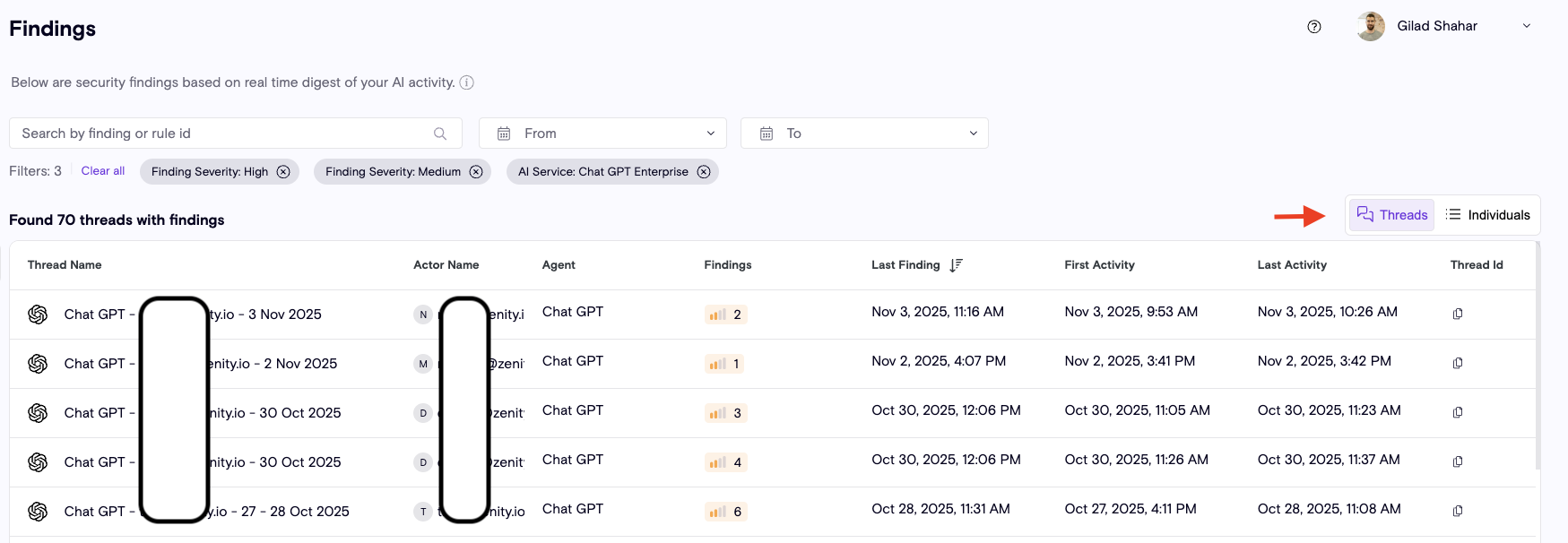
Bulk Upload for Allowed Domains
Managing trusted domains just got much easier.
Zenity now supports bulk upload of Allowed Domains, making it simple for organizations to define their trusted environments at scale.
Previously, customers had to manually add each domain one by one, a time consuming and error prone process, especially for large enterprises with thousands of domains.
With this new capability, security and governance teams can now upload a complete list of domains via a single file, instantly updating their organization’s policy.
Why It Matters
- Faster onboarding: Add thousands of domains in seconds instead of days.
- Reduced manual effort: Eliminate repetitive entry and potential mistakes.
- Better coverage: Reduce FPs and noise
How It Works
- Navigate to Policies → Allowed Domains in your Zenity portal.
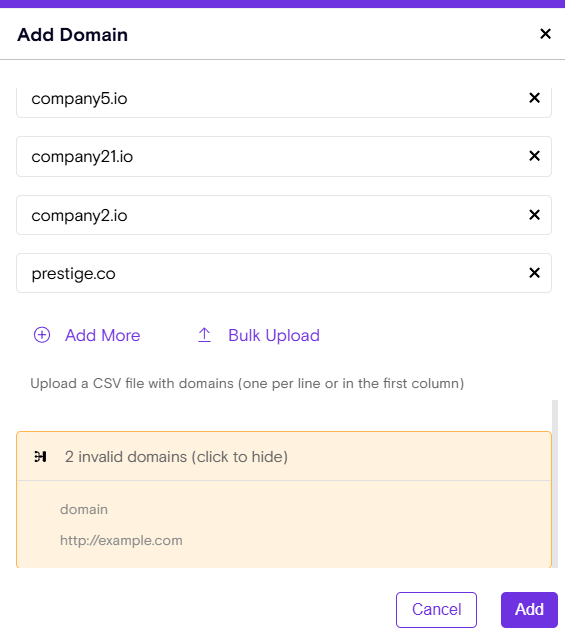
- Click Add Domain → Bulk Upload and select your file (Upload a CSV file with domains (one per line or in the first column,limited to 2000 domains per file).
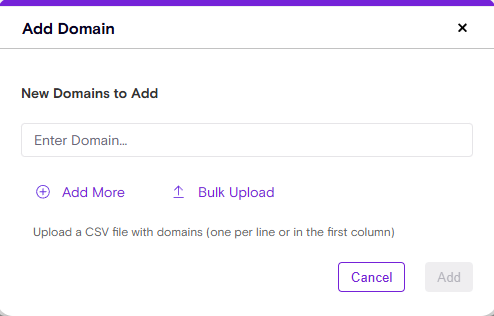
- Review and confirm to instantly apply your changes.
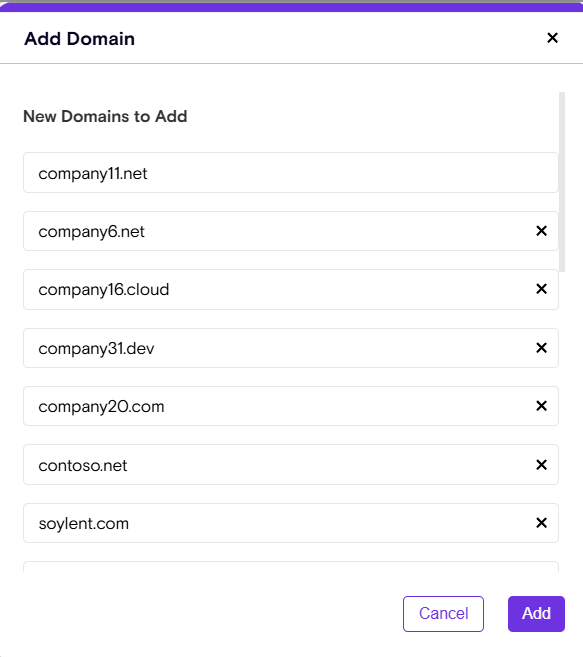
Zenity will also show all invalid entries and will highlight duplicates.
This feature is now generally available to all Zenity customers.
New Violation Rules (a full description can be found in the Zenity policy page)
| Rule ID | Rule Title | Platform / AI Service |
|---|---|---|
| ZN_BR00001 | Agent instructions contain a hard-coded secret | Amazon (Bedrock) |
| ZN_BR00002 | Agent action parameters have secrets | Amazon (Bedrock) |
| ZN_BR00003 | Agent is stale | Amazon (Bedrock) |
| ZN_BR00004 | Knowledge base is using disallowed endpoint | Amazon (Bedrock) |
| ZN_BR00005 | Unconstrained multi-agent collaboration | Amazon (Bedrock) |
| ZN_BR00006 | Sensitive Agent is susceptible to data poisoning from the web | Amazon (Bedrock) |
| ZN_BR00007 | Overly Permissive Data Retention | Amazon (Bedrock) |
| ZN_CG00004 | GPT Canvas exposed a secret | ChatGPT Enterprise |
| ZN_CG00016 | GPT is dormant | ChatGPT Enterprise |
| ZN_P00267 | MCP connector uses a disallowed endpoint | Microsoft (Copilot Studio) |
| ZN_P00268 | Custom connector uses a disallowed endpoint | Microsoft (Copilot Studio) |
| ZN_P00274 | Agent is dormant | Microsoft (Copilot Studio) |
| ZN_P00300 | Agent instructions contain hard-coded secrets | Microsoft (Copilot Studio) |
| ZN_P00301 | Agent instructions contain hyperlink | Microsoft (Copilot Studio) |
| ZN_P00302 | Agent instructions contain untrusted URL | Microsoft (Copilot Studio) |
| ZN_P00303 | Sensitive Agent connected to another agent | Microsoft (Copilot Studio) |
| ZN_P00304 | Agent Action uses an untrusted domain | Microsoft (Copilot Studio) |
| ZN_P00305 | Business critical agent action requires no authentication | Microsoft (Copilot Studio) |
| ZN_P00306 | Connection is implicitly sharing Azure AI Search connection | Microsoft (Copilot Studio) |
| ZN_P00307 | Agent Topic requests sensitive inputs | Microsoft (Copilot Studio) |
| ZN_P00113 | Custom connector configured with custom policy templates that may include hard-coded secrets | Microsoft |
| ZN_PB00025 | Dataset is using a datasource connection with disallowed endpoints | Fabric |
| ZN_S00084 | Agent instructions contain a hyperlink | Salesforce (Agentforce) |
| ZN_S00085 | Agent instructions contain a hard-coded secret | Salesforce (Agentforce) |
| ZN_S00086 | Agent action uses external services | Salesforce (Agentforce) |
| ZN_S00087 | Agent topic instructions contain a hard-coded secret | Salesforce (Agentforce) |
| ZN_S00088 | Agent topic instructions contain a disallowed URL | Salesforce (Agentforce) |
| ZN_S00092 | Agent action will change records without user approval | Salesforce (Agentforce) |
| ZN_S00093 | Agent created or changed by external user | Salesforce (Agentforce) |
| ZN_S00095 | Agent accepting unauthenticated chat | Salesforce (Agentforce) |
| ZN_S00096 | Enhanced conversation logging disabled | Salesforce (Agentforce) |
| ZN_SN00001 | Business critical agent runs using AI user | Service Now (AI Agent Studio) |
| ZN_SN00002 | AgentTrigger can be triggered by anonymous users | Service Now (AI Agent Studio) |
| ZN_SN00003 | Autonomous agent action with write action | Service Now (AI Agent Studio) |
| ZN_AT00001 | Untrusted user has privileged access to base | Airtable |
| ZN_AT00002 | Base contains sensitive tables with untrusted user | Airtable |
| ZN_AT00003 | User without 2FA enabled | Airtable |
| ZN_AT00004 | User invited by external/untrusted user | Airtable |
| ZN_AT00005 | Base has many privileged identities | Airtable |
| ZN_AT00006 | Base has no tables | Airtable |
| ZN_BB00001 | Flow is publicly accessible through webhook | Budibase |
| ZN_BB00002 | Datasource SSL certificate verification is disabled | Budibase |
| ZN_BB00003 | Workspace has too many privileged identities | Budibase |
| ZN_BB00005 | Irreversible SQL query is potentially exposed to public users | Budibase |
| ZN_BB00006 | Business-critical datasource is publicly available | Budibase |
| ZN_BB00007 | Untrusted app user | Budibase |
| ZN_BB00008 | Datasource uses plaintext Bearer token authentication | Budibase |
| ZN_BB00009 | Flow is shadow triggering another flow | Budibase |
| ZN_BB00010 | Unencrypted Traffic for MS SQL Server datasource | Budibase |
Zenity September-2025
⭐ Highlights
AI Detection & Response Playbooks
Zenity launches AI Detection & Response (AIDR) Playbooks, enabling automated, event-driven responses to runtime findings. Playbooks can now trigger instantly when detections occur, eliminating the need for manual polling or custom API workflows. Users can configure triggers based on any AIDR detection rule, group them by severity or AI service, and choose from flexible response actions such as HTTP webhooks or email notifications. This enhancement accelerates response times, simplifies automation, and empowers security teams to act immediately on AI runtime risks like secret exposure or PII detection.
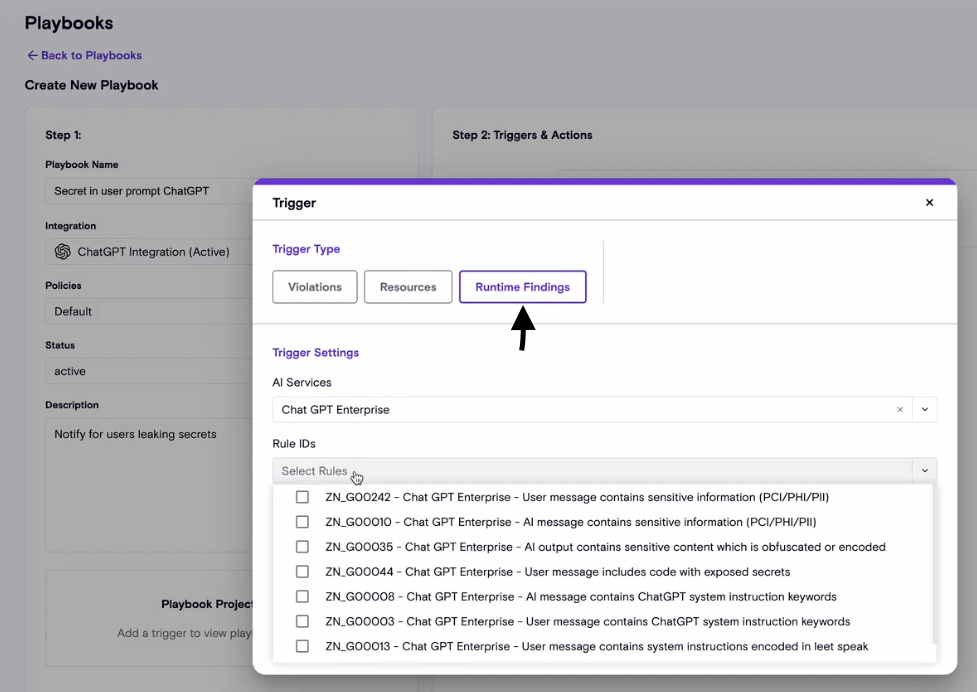
MCP support in AI Detection & Response
As Model Context Protocol (MCP) is becoming the industry-standard interface for AI agents to interact with external tools and data sources, Zenity keeps expanding the value provided with MCP users. Today, we're happy to share the initial support in AIDR, including:
MCP activity
Users can now view all MCP activity across their environment, including AI platforms, users, and agents. To help identify MCP-related risks, the new "tool origin" filter allows users to isolate tool invocations discovered via MCP, distinguishing them fro other sources:
- Platform-defined: Tools provided by the AI platform that are available out-of-the-box for all agents
- Agent-defined: Custom tools created by the agent builder within a specific agent's scope
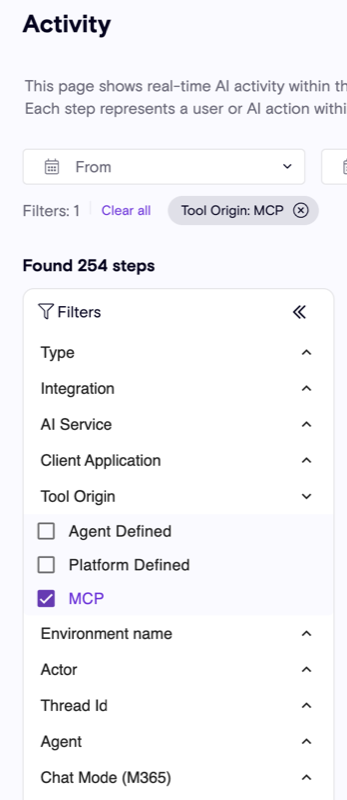
MCP-related detections
Several MCP-specific detection rules have been deployed to identify risks unique to MCP usage, including:
- ZN_P00276 User performs discovery actions on MCP server: A user performs discovery actions on an MCP server attached to the agent, potentially for reconnaissance.
- ZN_P00277 AI agent exposed server-side MCP secrets: AI agent includes MCP secrets in its response that were embedded server-side and returned through the agent interaction with MCP.
- ZN_P00279 AI agent response includes suspicious clickable link after MCP interaction: this suggest an abnormal behavior after MCP was activated.
- ZN_P00280 User exploits AI agent to deliver SQL injection to MCP server - SQL injection through MCP.
For complete details, see the Zenity policy page. Scope: preview-status rules, in Copilot Studio.
Zenity August-2025
⭐ Highlights
AIDR Pipeline Now Available in US Region
Enterprise customers with regulatory or compliance requirements can now deploy Zenity’s AIDR pipeline fully within the US, ensuring all collected and generated data remains stored in US regions.
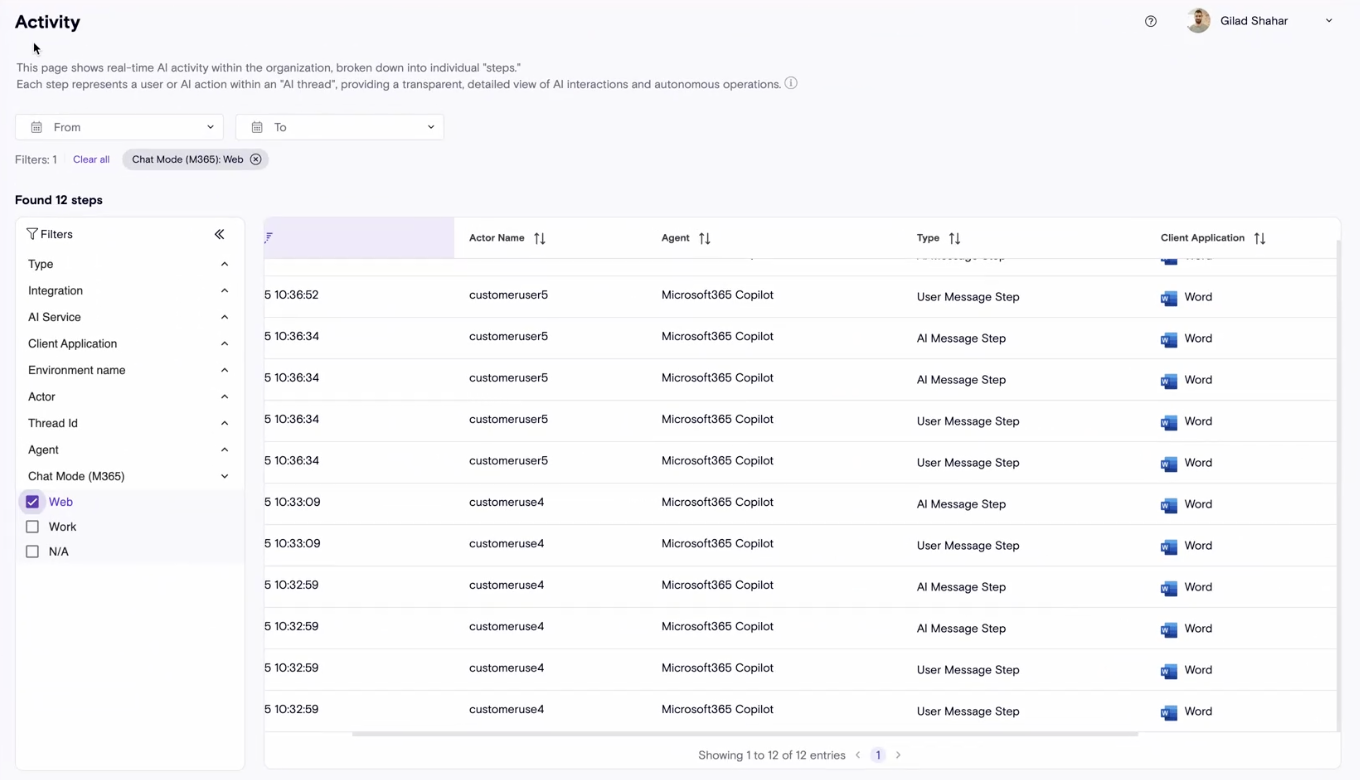
Distinguish Microsoft 365 Copilot Work vs Web Mode
Zenity now differentiates between Work Mode (licensed, organization connected) and Web Mode (internet only) usage in Microsoft 365 Copilot. With a single click, customers can see which mode is in use, bringing clarity and control to Copilot governance across Outlook, Word, and the entire M365 suite.
Zenity July-2025
⭐ Highlights
New Integrations: Azure AI Foundry & Google Vertex AI
Zenity expands AI Detection & Response coverage to Microsoft Azure AI Foundry and Google Vertex AI, enabling full runtime visibility and threat detection for home-grown AI agents.
What’s New?
- Ingests agent interactions including user and agent prompts, tool invocations, and RAG fetches.
- Streams activity through the AIDR detection engine to flag threats and runtime governance risks.
Get started with Microsoft Azure AI Foundry
Get started with Google Vertex AI
Zenity June-2025
⭐ Highlights
New Integration: Visibility & Risk Management for Salesforce Agentforce AI Agents
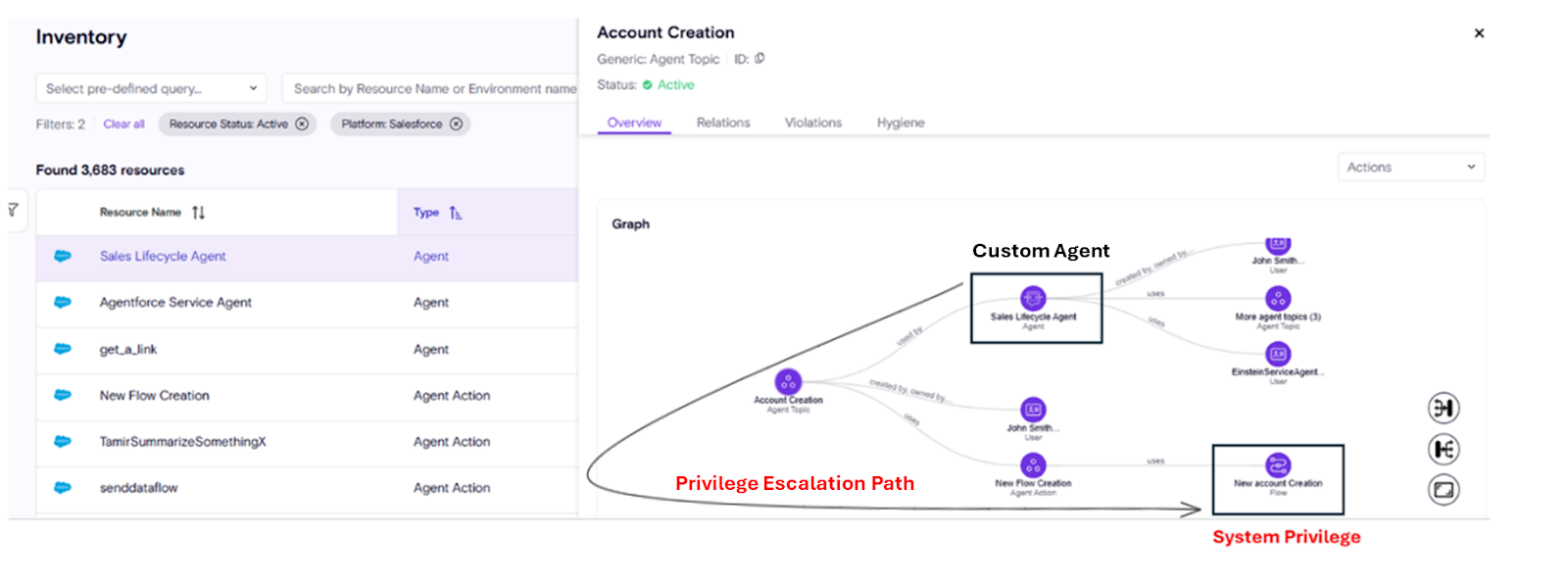
We’re excited to announce a major update to Zenity AISPM: security teams can now gain deep visibility and risk management for AI agents built on Salesforce’s Agentforce platform. This is the first time Zenity provides comprehensive insight into Agentforce, closing a critical blind spot for enterprise customers.
What’s New?
- Zenity now inventories and analyzes custom Agentforce agents and their interactions with Salesforce assets—including Topics, Actions, Flows, and Apex code.
- Security teams can surface risk scenarios such as privilege escalation, data leakage, and improper execution logic.
- Zenity automatically maps end-to-end execution chains, revealing hidden risk paths across interconnected Salesforce components.
How does it work?
Zenity ingests metadata from the Agentforce API and correlates it with native Salesforce resources. This enables detection of risky agent configurations, elevated permissions, and policy violations. By leveraging Zenity’s deep understanding of Salesforce’s structure, the platform provides actionable insights that go beyond agent-focused telemetry.
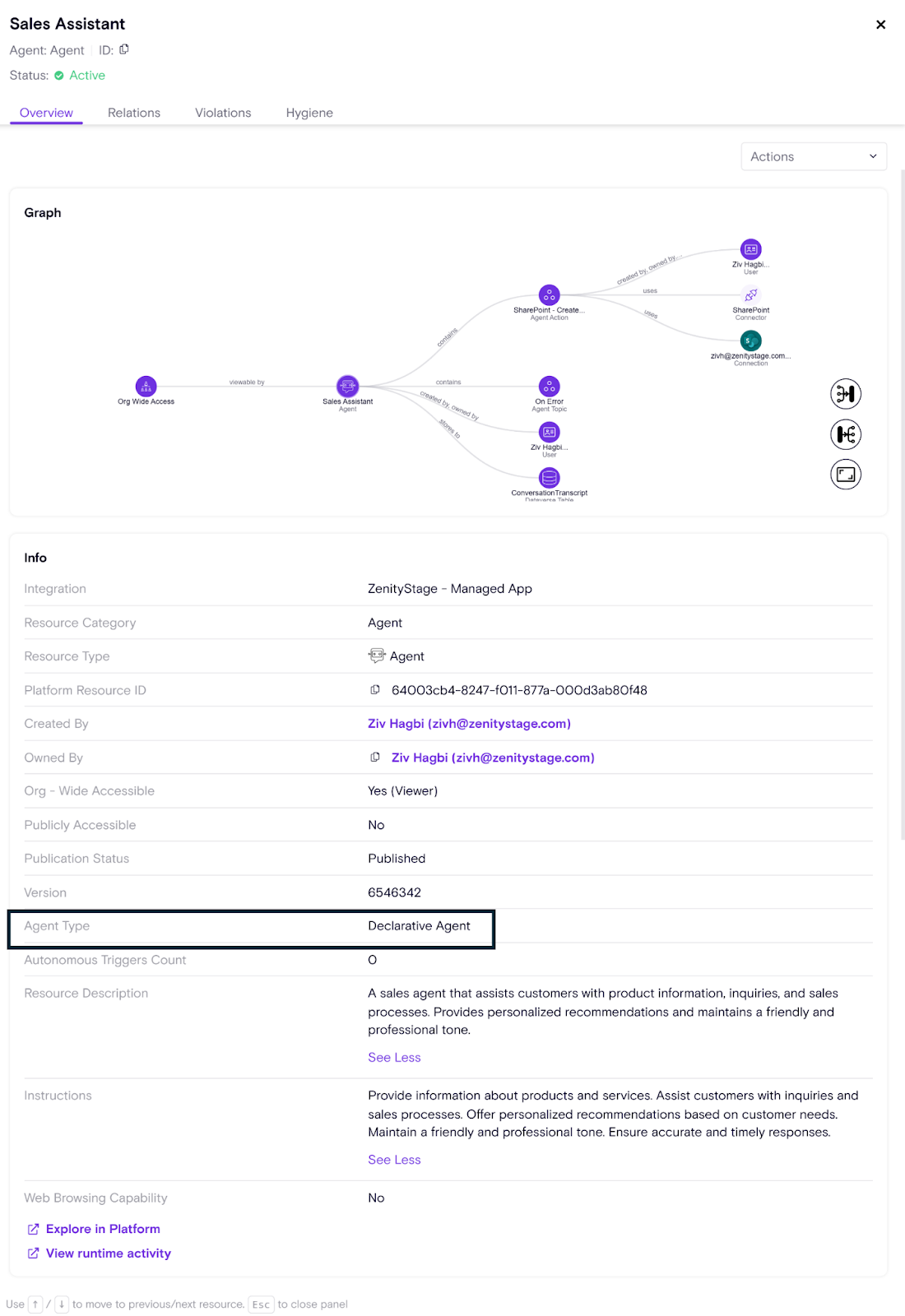
Zenity now supports Declarative Agents!
Zenity now supports Declarative Agents for Microsoft 365 Copilot, providing visibility, risk assessment, and remediation for these new agent types built via Copilot Studio.
What are Declarative Agents?
Declarative Agents are customized versions of Microsoft 365 Copilot, allowing organizations to create tailored AI experiences directly in M365 Copilot. These agents are built and published through Copilot Studio, then made available to users in M365.
New Capabilities:
- Declarative Agents are uniquely identified and displayed in Zenity's Inventory.
- Risk assessment is tailored for Declarative Agents, recognizing their unique properties and publication status.
- New and adjusted remediation actions (Click-2-Fix and Playbooks) are available for Declarative Agents.
- Additional agent-specific data & configurations are collected.
- Declarative Agents are connected to Teams and Microsoft 365 Copilot in the Zenity graph for published agents.
Securing Copilot Studio MCP Usage
Securing Copilot Studio MCP Usage
The Model Context Protocol (MCP) is becoming the industry-standard interface for AI agents to interact with external tools and data sources. However, as adoption grows, security challenges have emerged around authentication, tool access, and auditability.
This feature introduces Zenity's initial support for MCP security, providing visibility and policy enforcement for MCP environments.
By integrating MCP awareness into Zenity's AI Security Posture Management (AISPM), Zenity will: - Automatically inventory MCP servers and tools in use across endpoints and cloud. - Identify vulnerabilities and insecure configurations. - Enforce organization-specific allow/block policies in real-time. - Provide observability of AI → MCP flows. - Enable remediation and alerting actions for risky or shadow MCPs.
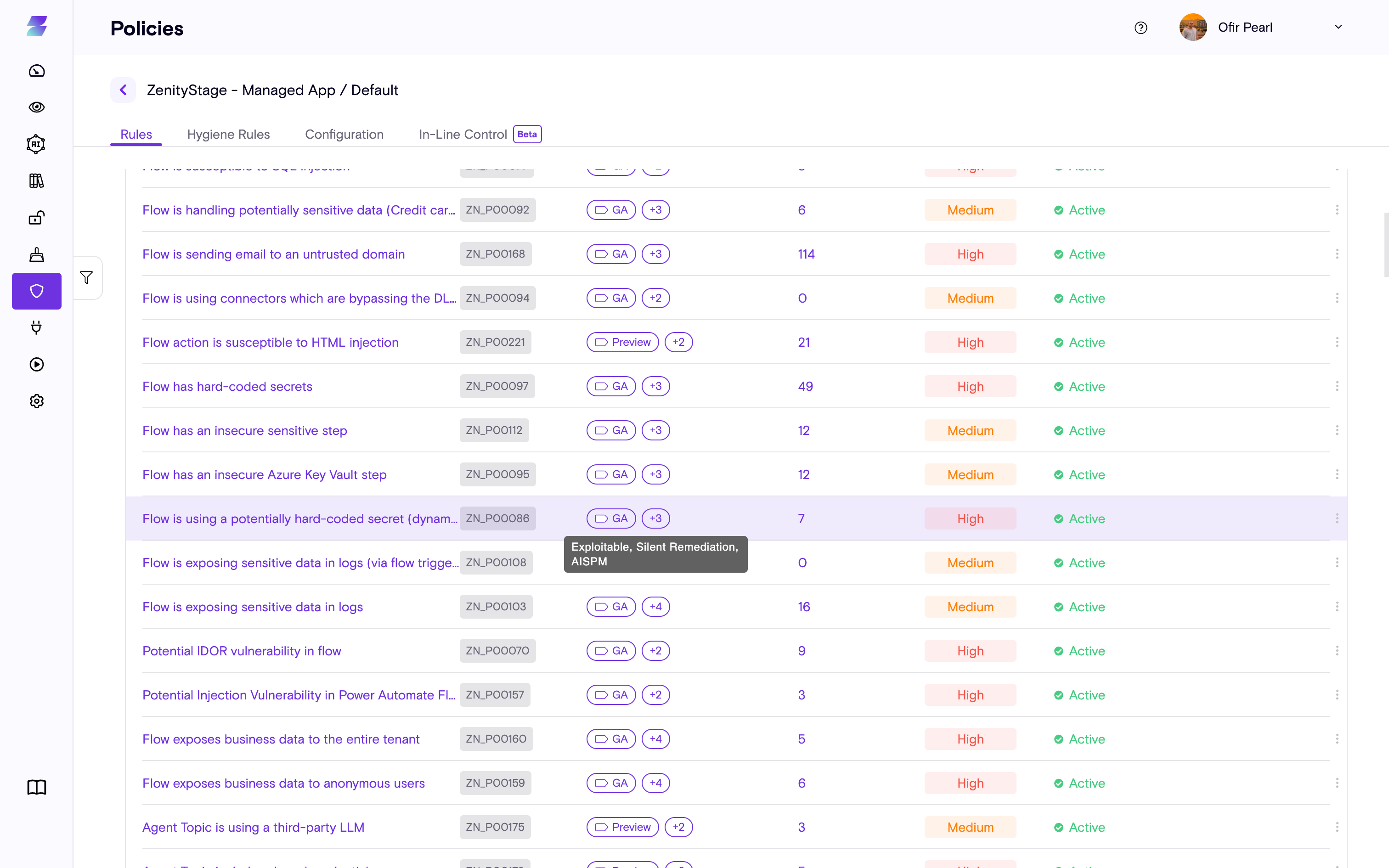
New Rule Tags
We've expanded our Rule Tags feature to include new tags that provide even deeper insight into your security posture.
These new tags help users quickly understand the risk behind each violation rule and clarify the most appropriate remediation paths.
What's new?
- Additional tags now highlight the risk level and remediation guidance for each rule.
- Users can filter and search for rules based on these new tags, making it easier to prioritize and address security issues.
- The new tags offer more granular context, empowering security and compliance teams to make faster, more informed decisions.
New Rule Tags Available:
- Silent remediation - Rules that can be automatically remediated without user intervention
- Org wide access - Rules related to organization-wide permissions and access controls
- Hard-coded secret - Rules identifying hardcoded credentials or sensitive information
- Guest access - Rules concerning guest user permissions and access
- Member access - Rules related to member-level permissions and access controls
- Implicit sharing - Rules identifying implicit or unintended sharing configurations
- Admin configuration - Rules related to platform administrative settings and configurations
- Public exposure - Rules identifying publicly accessible resources or data
- Security boundaries - Rules concerning security perimeter and boundary configurations
- GenAI - Rules specifically related to Generative AI features and configurations
- Business data - Rules concerning business-critical data access and protection
Benefits:
- Enhanced risk visibility for every violation rule.
- Clearer, actionable remediation guidance.
- Improved efficiency in managing and investigating violations.
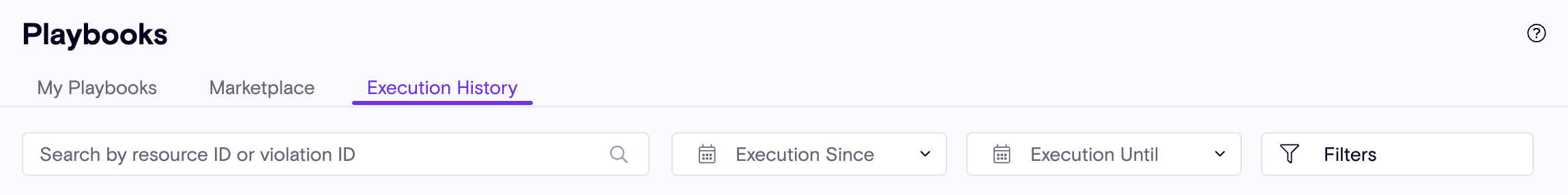
Search Playbook Execution History
Customers can now quickly find specific playbook runs using a new search box in the Playbook Execution History page. Now users can track how a specific violation/resource was impacted by a playbook. Previously, users could only filter by "Playbook Name" and "Execution Status." With this update, you can search by:
- Violation ID
- Resource ID
This enhancement makes it much easier to investigate how a playbook managed a particular violation or resource, streamlining troubleshooting and compliance reviews.
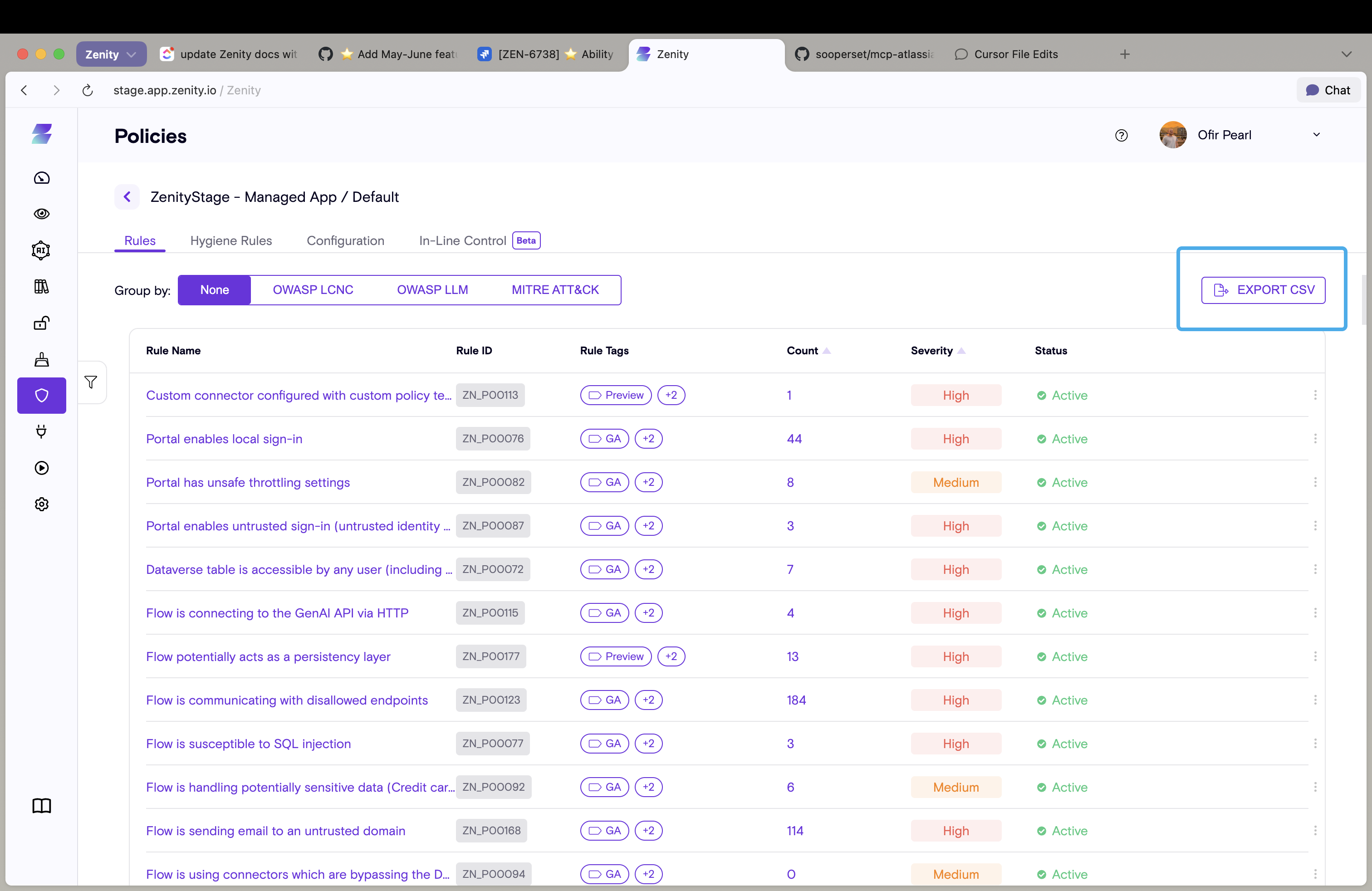
Export Policy Page
Customers can now export their policy rules mapping directly from the Policies page in a single click. This feature provides a convenient way to get an Excel export of all open rules, similar to the data presentation already available in the Policies interface.
What's new? - One-click Excel export functionality from the Policies page - Exports include the complete mapping of open rules - Maintains the same data structure and format as displayed in the UI
Benefits: - Streamlined compliance reporting and analysis - Easy sharing of violation data with stakeholders - Consistent data format for external processing and documentation
Zenity May-2025
⭐ Highlights
New ChatGPT Enterprise Security Rules
Zenity now includes additional comprehensive security rules specifically designed to protect ChatGPT Enterprise environments from various security threats and compliance violations.
New Rules Added:
-
Rule ZN_CG00003: GPT Action contain hard-coded secret - Detects when GPT actions contain hardcoded secrets, credentials, or sensitive information that could be exposed
-
Rule ZN_CG00012: GPT Actions contains malicious instructions - Identifies GPT actions that contain potentially malicious code or instructions that could compromise security
-
Rule ZN_CG00017: GPT Action server is external url - Alerts when GPT actions are configured to connect to external servers outside the organization's control
-
Rule ZN_CG00010: GPT definition contains hyperlink - Detects hyperlinks within GPT definitions that could lead to unauthorized external resources
-
Rule ZN_CG00013: GPT has many privileged identities - Identifies GPTs with excessive privileged access that could pose security risks
-
Rule ZN_CG00015: GPT definition contains external url - Alerts when GPT definitions reference external URLs that may not be authorized
-
Rule ZN_CG00016: GPT Knowledge contains external url - Detects external URLs within GPT knowledge bases that could expose sensitive information
Benefits:
- Comprehensive protection for ChatGPT Enterprise environments
- Early detection of security vulnerabilities and compliance issues
- Automated monitoring of GPT configurations and actions
- Enhanced visibility into potential data leakage and unauthorized access
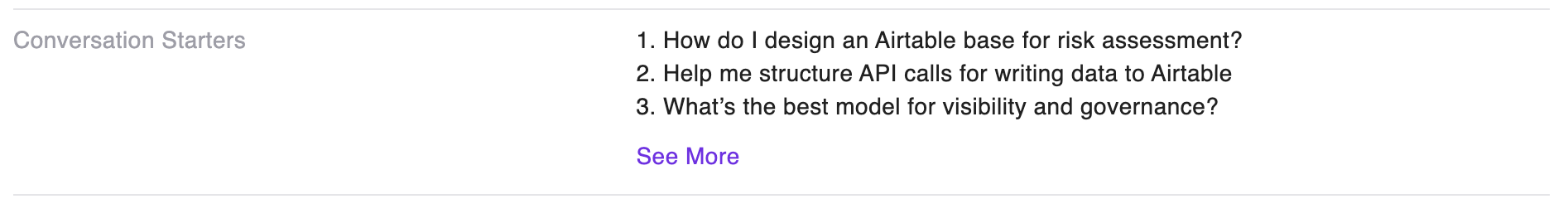
Agent Conversation Starters & Instructions Display Enhancement
The Conversation Starters and Instructions fields in the ChatGPT inventory side panel have been improved to display conversation starters and instructions as properly formatted numbered lists.
What's new: - Conversation starters now display as a clean, numbered list with each item on a separate line - Improved readability and scanning for users reviewing ChatGPT configurations - Consistent formatting with other expandable fields in the inventory interface
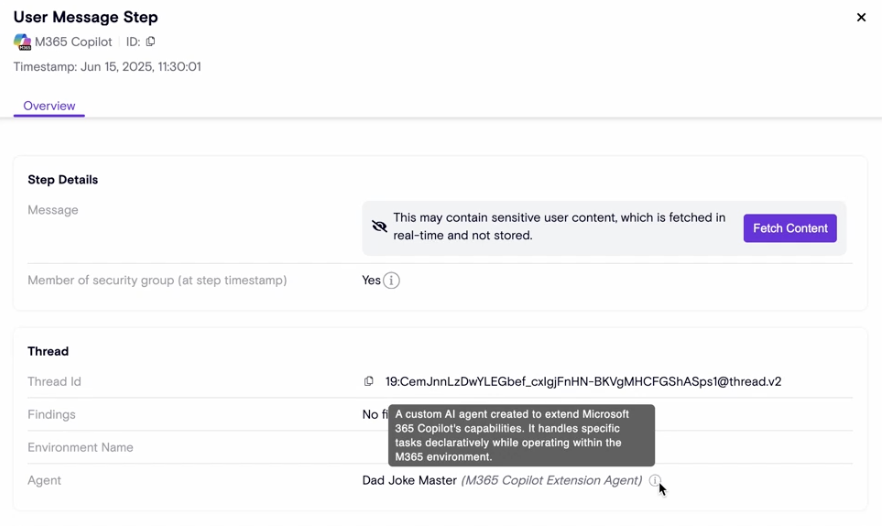
Declarative Agents in AIDR Activity
AIDR Activity now shows when declarative agents built via agent-builder are used in M365 Copilot, helping users understand M365 Copilot behavior and thread transitions.
Zenity April-2025
⭐ Highlights
Zenity for ChatGPT Enterprise: End-to-End Security for the Agentic Era
We’re thrilled to introduce Zenity for ChatGPT Enterprise, the industry’s first and only security and governance platform purpose-built to protect AI Agents across the entire ChatGPT Enterprise ecosystem. As enterprises increasingly adopt ChatGPT Enterprise for custom agent development, cross-functional collaboration, and knowledge sharing, Zenity now gives security teams the deep visibility and control they need to enable innovation—without compromise.
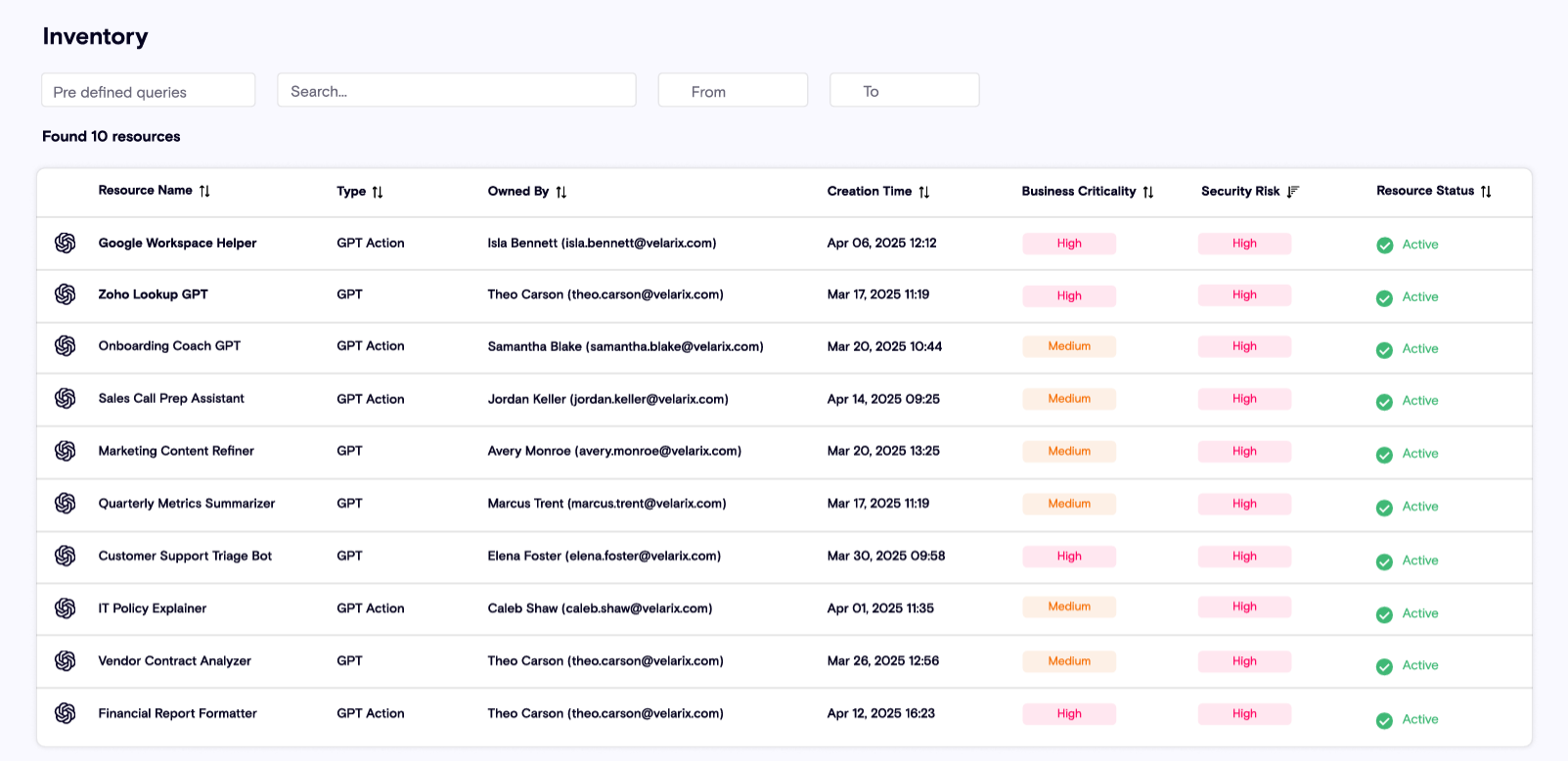
Full Lifecycle Protection – From Build to Runtime
ChatGPT Enterprise isn’t just a chat tool—it’s an AI development platform. Business users are building Custom GPTs, uploading proprietary knowledge files, integrating with business systems, and collaborating via Canvas—all often without security oversight. Zenity now brings complete lifecycle visibility and security to every layer:
Buildtime Protection: Automatically scan GPTs during development to detect for example:
- Hardcoded secrets
- Excessive permissions
- Weak or missing authentication
- Public or org-wide sharing risks
- Misconfigured tools and actions
- Data leakage routes
- Privilege escalation paths
Posture Management: Enforce secure defaults and align with governance policies across GPTs, tools, actions, knowledge files, and user access permissions.
Runtime Monitoring: Observe how GPTs behave in production to detect for example:
- Prompt injection
- RAG manipulation and data leakage
- Sensitive data exposure
and much more..
Real-Time Threat Detection & Response
Zenity’s integration with the OpenAI Compliance API allows continuous monitoring of GPT interactions and configuration changes. This includes:
-
Threat mapping aligned with OWASP LLM Top 10 and MITRE ATLAS
-
Detection of suspicious behavior patterns like indirect prompt injection, excessive data access, or rogue agents
-
Instant remediation via Click-to-Fix actions: isolate risky agents, revoke access, or delete sensitive files at the push of a button.
Agent-Level Observability Across the Entire Workspace
-
Security teams now get real-time, unified visibility into every aspect of ChatGPT Enterprise, including:
-
Custom GPTs (configuration, purpose, and user access)
-
Canvas documents and collaboration patterns
-
Knowledge files (including sensitive content or risky metadata)
-
User actions and content shared through the GPT interface
Zenity tracks how each of these components is connected, used, and modified—giving you the full context to assess risk, enforce policies, and respond effectively.
Built for Security Teams, Designed for the Business
Zenity bridges the gap between business-led AI innovation and enterprise-grade security expectations:
-
Detects risks that traditional tools miss—like credential sharing through GPT logic
-
Enables proactive guardrails that prevent unsafe GPTs from engaging with users
-
Empowers security to say yes to ChatGPT Enterprise adoption—safely, at scale
Real-World Use Cases and Risk Scenarios
Whether it’s a sales team building a GPT that integrates with the CRM or a developer creating an internal automation Agent, Zenity catches real-world security issues like:
-
GPTs using power-user API keys shared across the org
-
Actions authenticated with a single identity and no audit trail
-
Publicly shared agents unknowingly exposing sensitive data or triggering unintended actions
Why This Matters
This isn’t just a product update—it’s a defining moment for secure AI adoption. As more organizations move toward GPT-driven productivity and automation, Zenity ensures security and compliance teams stay in control. From misconfigurations to malicious misuse, Zenity covers it all—platform to prompt and everything in between.
New Violation Rules (a full description can be found in the Zenity policy page)
- ZN_CG00001 - GPT instructions have hard-coded secrets
- ZN_CG00013 - GPT has many privileged identities
- ZN_CG00009 - GPT is accessible by anonymous users
- ZN_CG00017 - GPT action server is an external endpoint
- ZN_CG00010 - GPT definition contains hyperlink
- ZN_CG00015 - GPT definition contains external URL
- ZN_CG00030 - GPT action performs business critical operation with author credentials
- ZN_CG00029 - GPT action uses author credentials
- ZN_CG00007 - GPT accessible by the entire organization
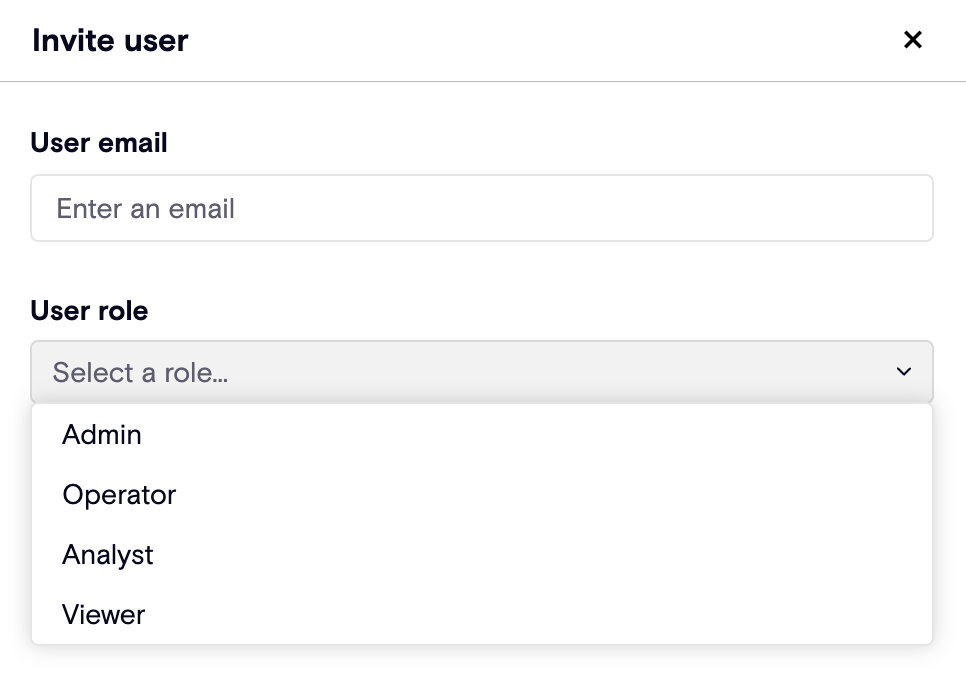
Introducing the 'Analyst' role
In response to customer feedback, we’ve introduced a new Analyst role in Zenity.
This role provides read access to all data necessary for effective risk analysis, including sensitive information such as Copilot transcripts (prompts) and tool invocation parameters.
The Analyst role enables users to investigate and triage violations and runtime findings, while maintaining strong access controls—no modification or remediation actions can be performed by users in this role.
This new role fills the gap between:
- Viewer – which provides read-only access but excludes sensitive data
- Operator – which includes full read access plus the ability to initiate remediation actions
The Analyst role strikes the right balance between visibility and control, empowering analysts without compromising governance.
Zenity March-2025
⭐ Highlights
Expanded Support for Microsoft Copilot Studio
Zenity now supports Microsoft Copilot Studio agents, allowing security and compliance teams to gain deeper visibility and control over this growing ecosystem of low-code AI assistants.
New remediation Action
We’ve added four new out-of-the-box actions to help you take proactive control over agent behavior:
🔹 Delete Agent – Remove unwanted or deprecated agents from your environment.
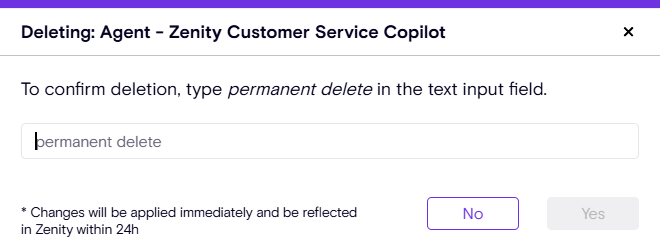
🔹 Disable Agent Action – Temporarily block agent activity without permanent deletion.
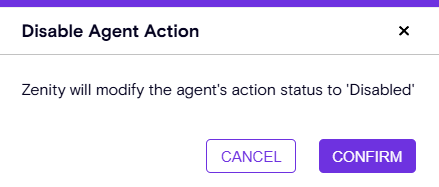
🔹 Delete Agent Action – Remove unwanted or deprecated actions from your environment.
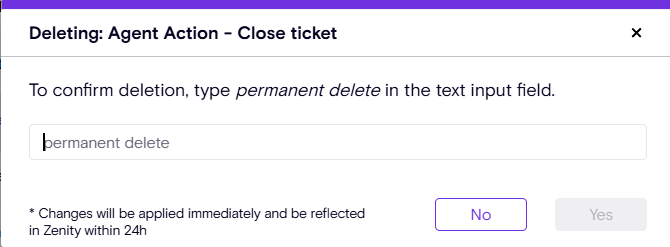
🔹 Enforce End-User Confirmation – Require user confirmation before an agent performs sensitive tasks.
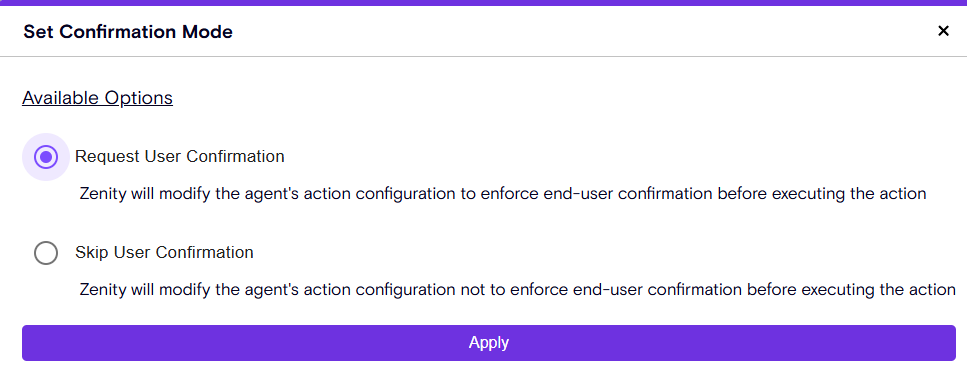
🔹 Enforce End-User Authentication – Ensure only authenticated users can trigger agent actions.
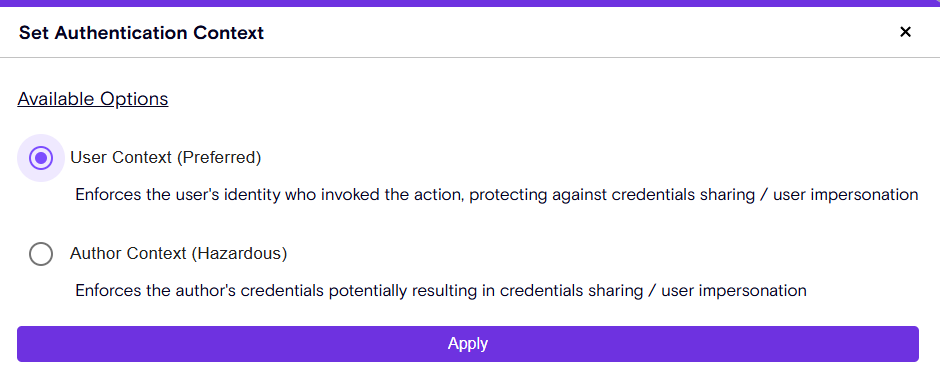
Action Privilege Insights
Gain greater transparency into what your agents are doing with:
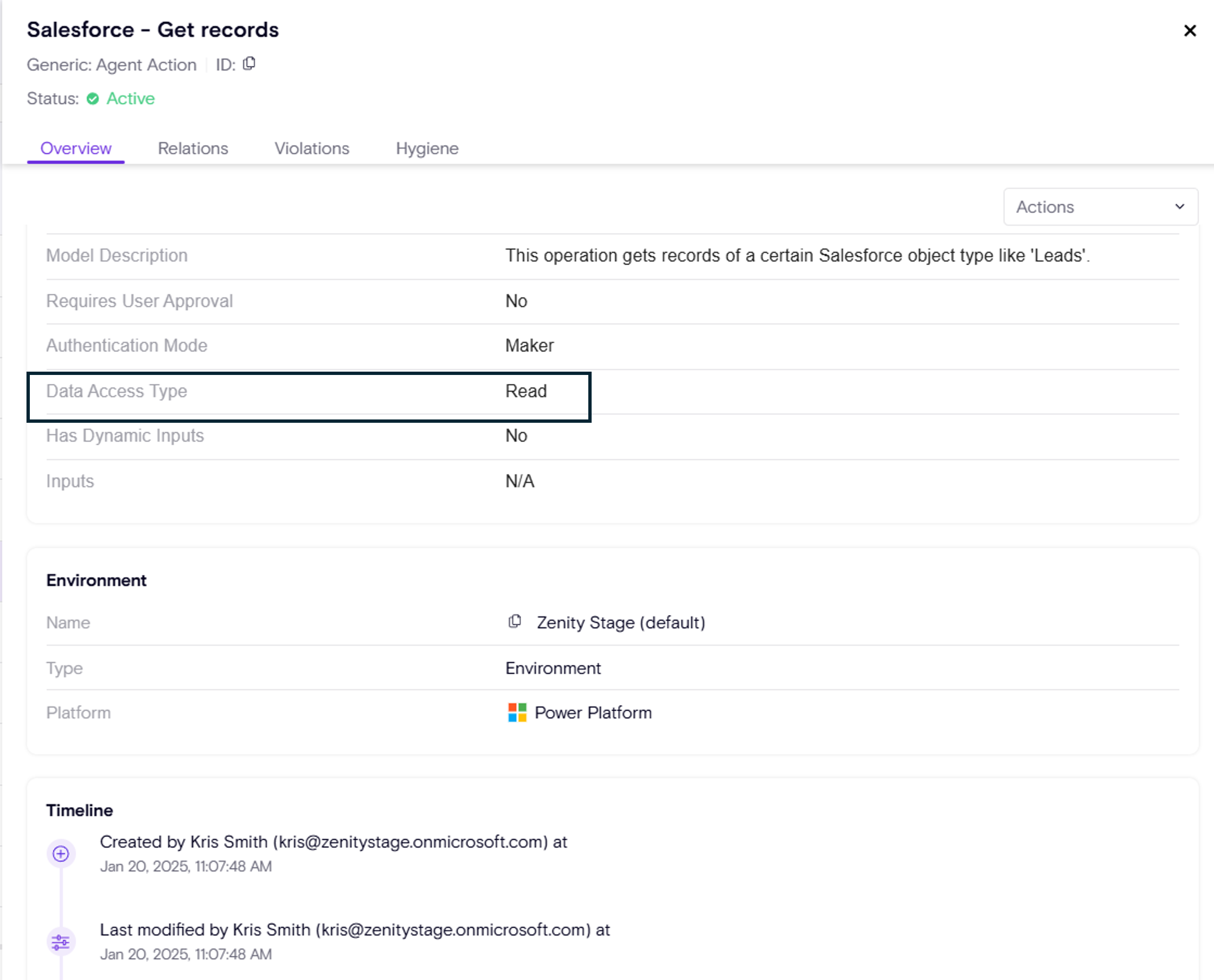
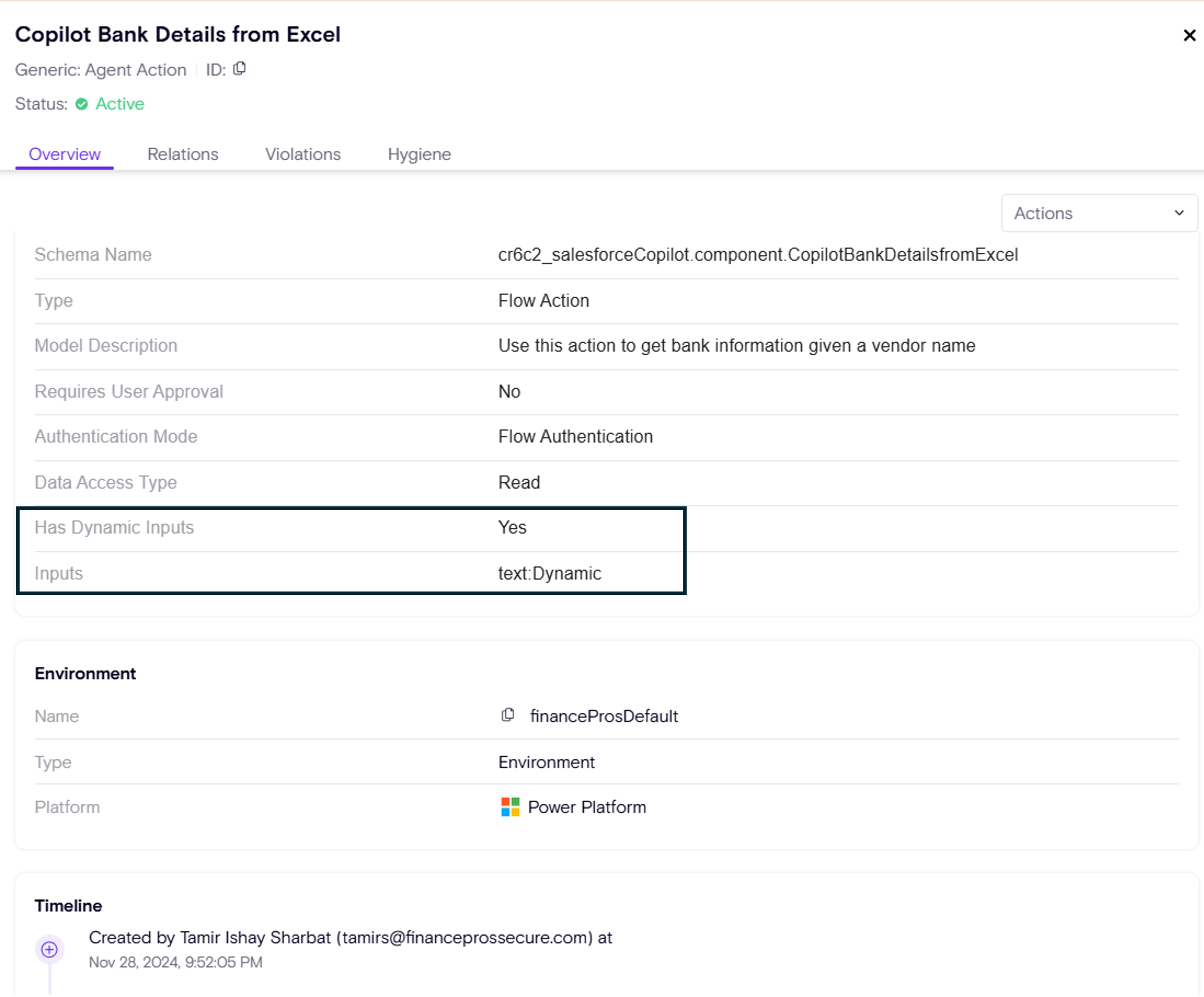
-
Read vs. Write Privilege visibility – Understand whether an action is viewing data or making changes. This provides the ability to understand what the agent can actually do.
-
Dynamic Input Visibility – Identify when agents are using dynamic or user-supplied input in their logic, which can introduce injection risks.
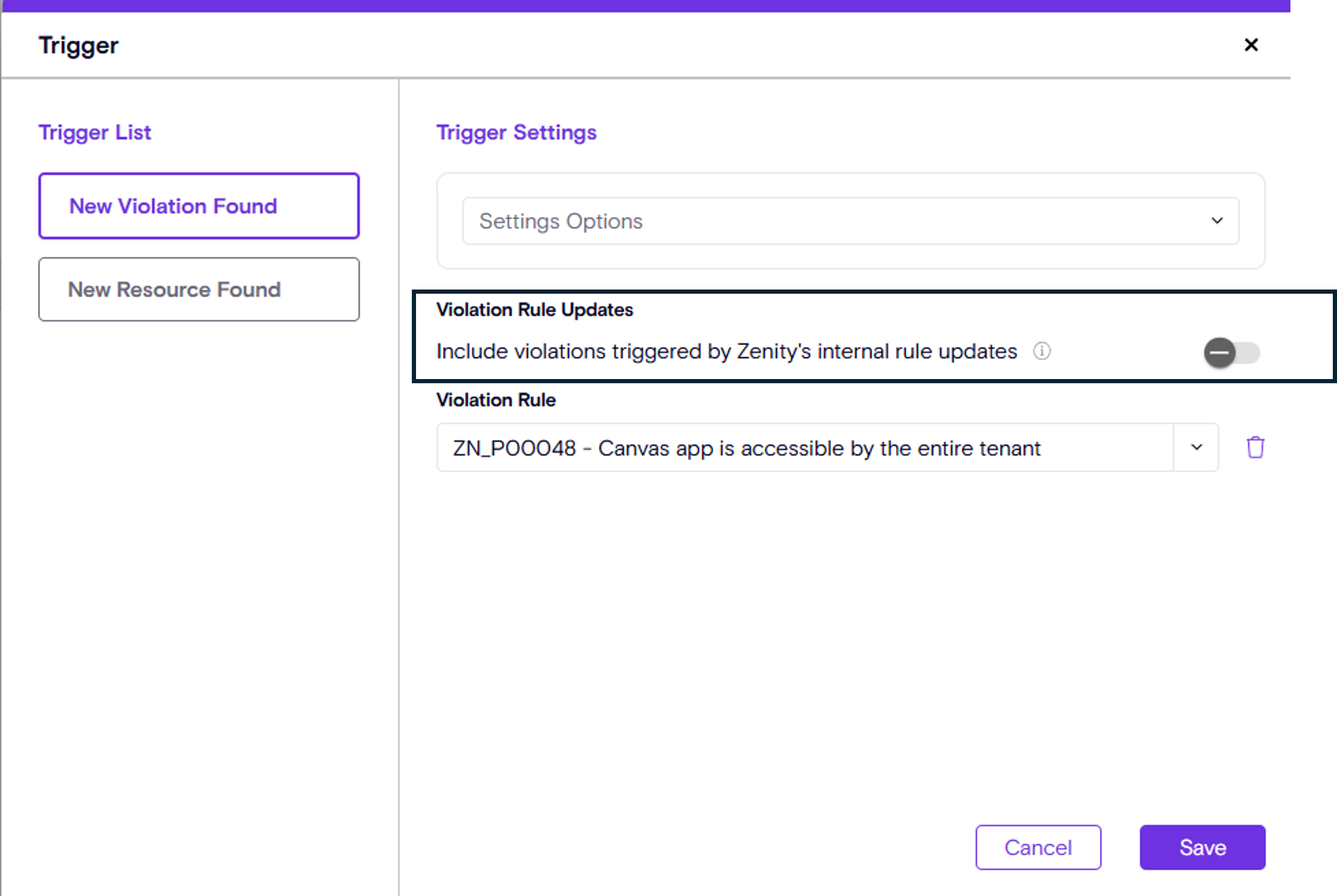
Smarter Playbook Execution
We’ve made playbooks even smarter. From now on, playbooks will only trigger on new violations, ensuring that updates made to rules by Zenity won't re-trigger violations unless the customer opts in. This gives you cleaner, more meaningful automation without unnecessary noise or unexpected consequences.
New Violation Rules (a full description can be found in the Zenity policy page)
- ZN_P00221 - Flow action is susceptible to HTML injection
- ZN_P00156 - Power Pages Site enables local sign-in
- ZN_P00175 - Agent Topic is using a third-party LLM
- ZN_P00172 - Agent Topic includes shared credentials
- ZN_P00154 - Canvas app is using a deprecated connector
- ZN_P00153 - Flow is using a deprecated connector
- ZN_P00155 - Agent topic is using a deprecated connector
- ZN_P00177 - Connection is using a deprecated connector
Detailed Evidence for AIDR Findings
Runtime findings now include the exact evidence detected by Zenity, providing clear visibility into why each finding was generated. Previously evidence included the step ID where the actual reason for genrating the findigs resides in. Now, each runtime finding includes a structured evidence section containing: * the location of the evidence: the step and the subsection within the step. * the "Core Evidence" which includes what was exactly found in this specific finding intance. * when the evidence is in sensitive content Zenity doesn't store (e.g. user prompts), a single click fetches the sensitive content from the source AI service platform and marks where the evidence is located within the fethced content.
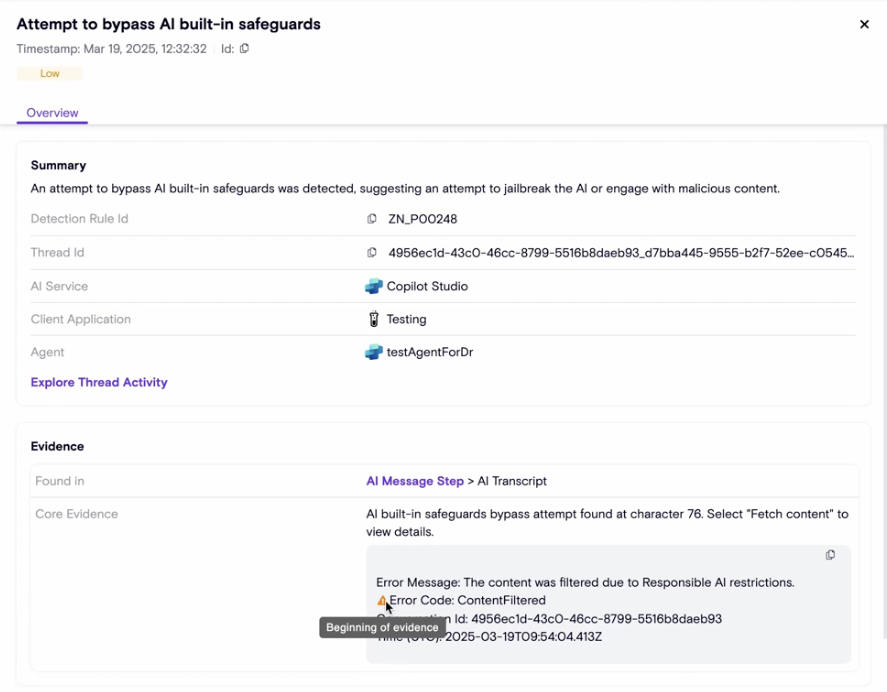
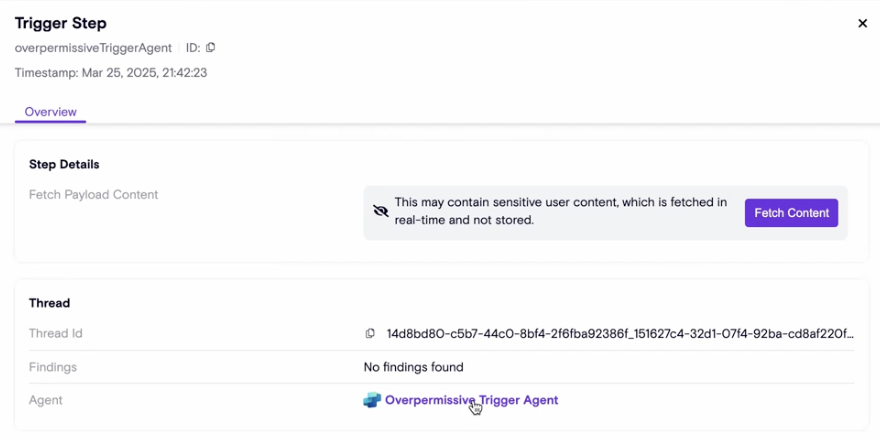
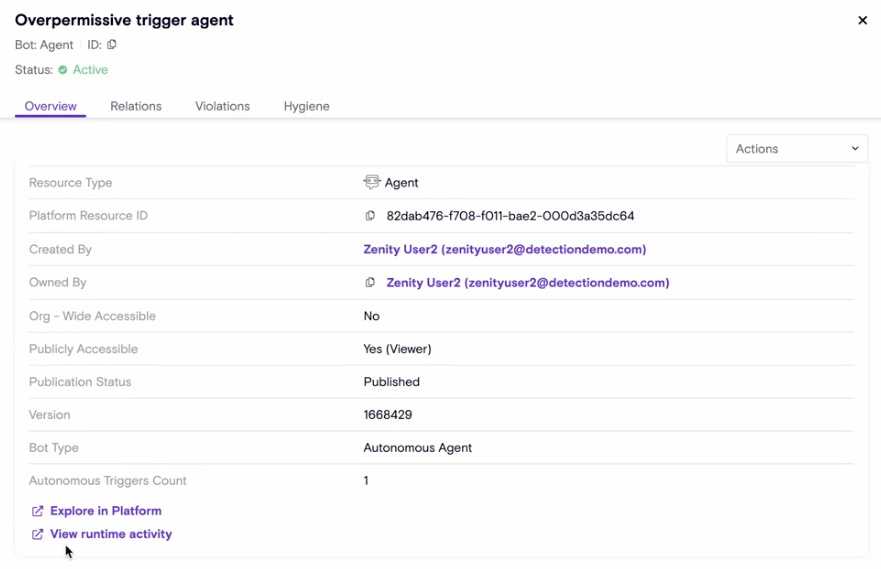
Two way AISPM<>AIDR one-click navigation
Users can now see runtime activity by navogating from an agent inventory resource page, and click on agent name in a runtime agent step and reach the agent resource page.
Zenity February-2025
⭐ Highlights
Fabric Integration customization enhancements
Customers have requested more granular control and customization for the 'Excessive Access' risk scenarios in Microsoft Fabric. We’re excited to introduce policy configuration enhancements, allowing customers to fine-tune policies to meet their specific security requirements.
🔹 Customers can now define their own custom thresholds, overriding Zenity’s default values.
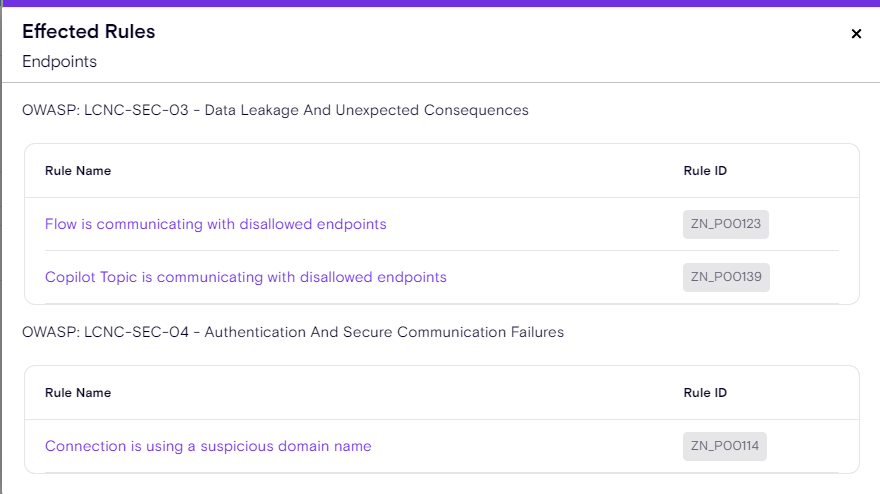
🔹 To see which rules are impacted by this new configuration, simply click 'View Rule' for instant insights.
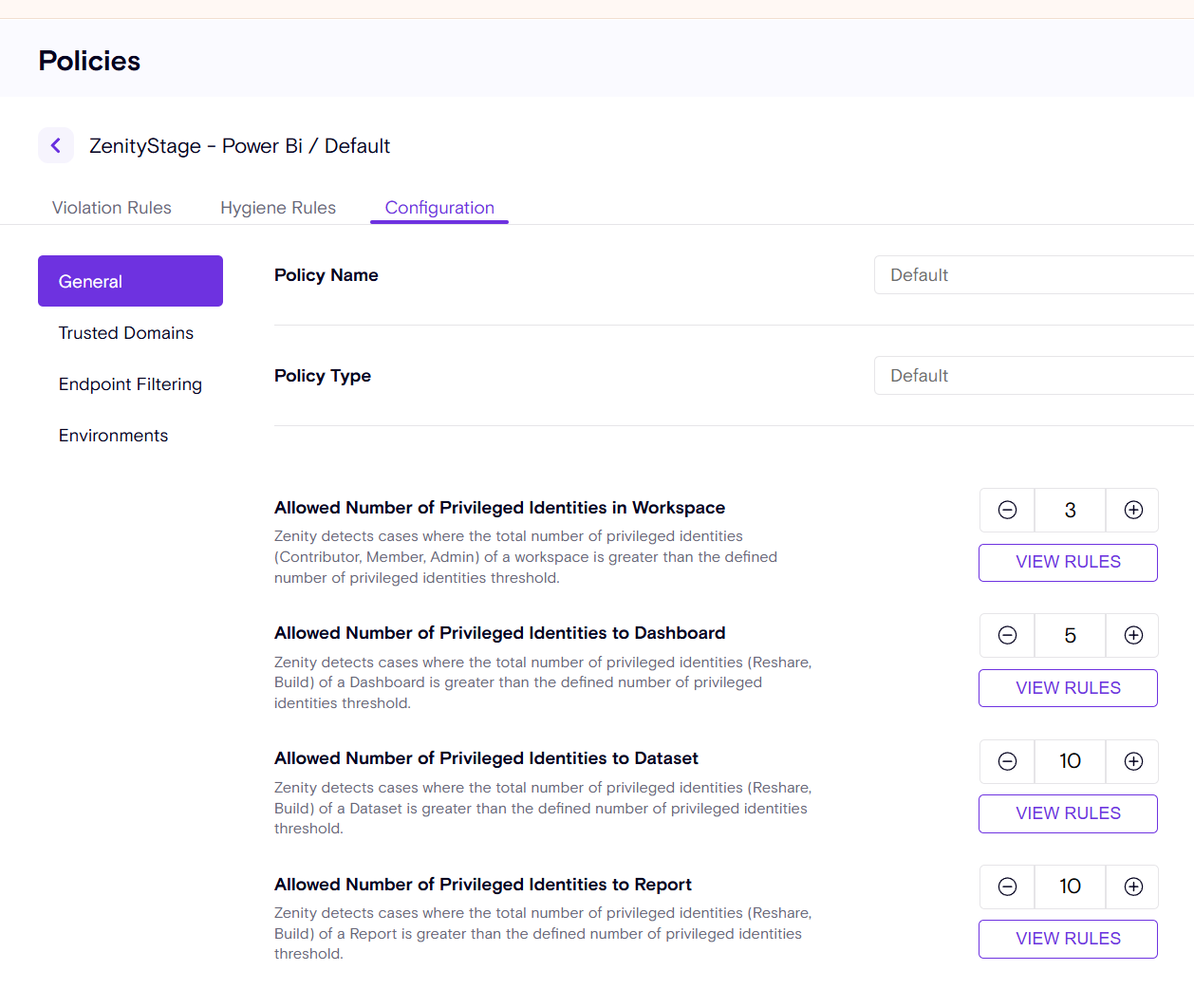
In case customers would like to know which rules are impacted by the new configuration, all they have to do is click on 'View Rule'
Execution insights persistency
A key factor in risk investigation is understanding whether a resource has been actively used or executed.
For example, an automation configured to push data outside the tenant is already a significant risk—but knowing that it has actually been executed elevates the risk severity.
Different platforms store execution data for limited retention periods:
🔹 Power Automate: Flow execution logs are available for 28 days.
🔹 Microsoft Fabric: Semantic model refresh logs are stored for only 7 days.
This data expiration leaves security teams without critical evidence on past executions.
This also plays a crucial role in risk remediation, as AppSec teams often need to delete risky resources.
For example, if a resource has not been executed in the past 12 months, it becomes a prime candidate for removal, reducing potential attack surfaces while minimizing unnecessary risk exposure.
-
Zenity now persists execution insights, ensuring that even if execution logs are deleted from the source platform, Zenity retains the history.
-
Additional Benefit: If an automation was never executed or Zenity began scanning after execution logs were deleted, we provide an anchor reference—indicating how long there has been no activity on a given resource.
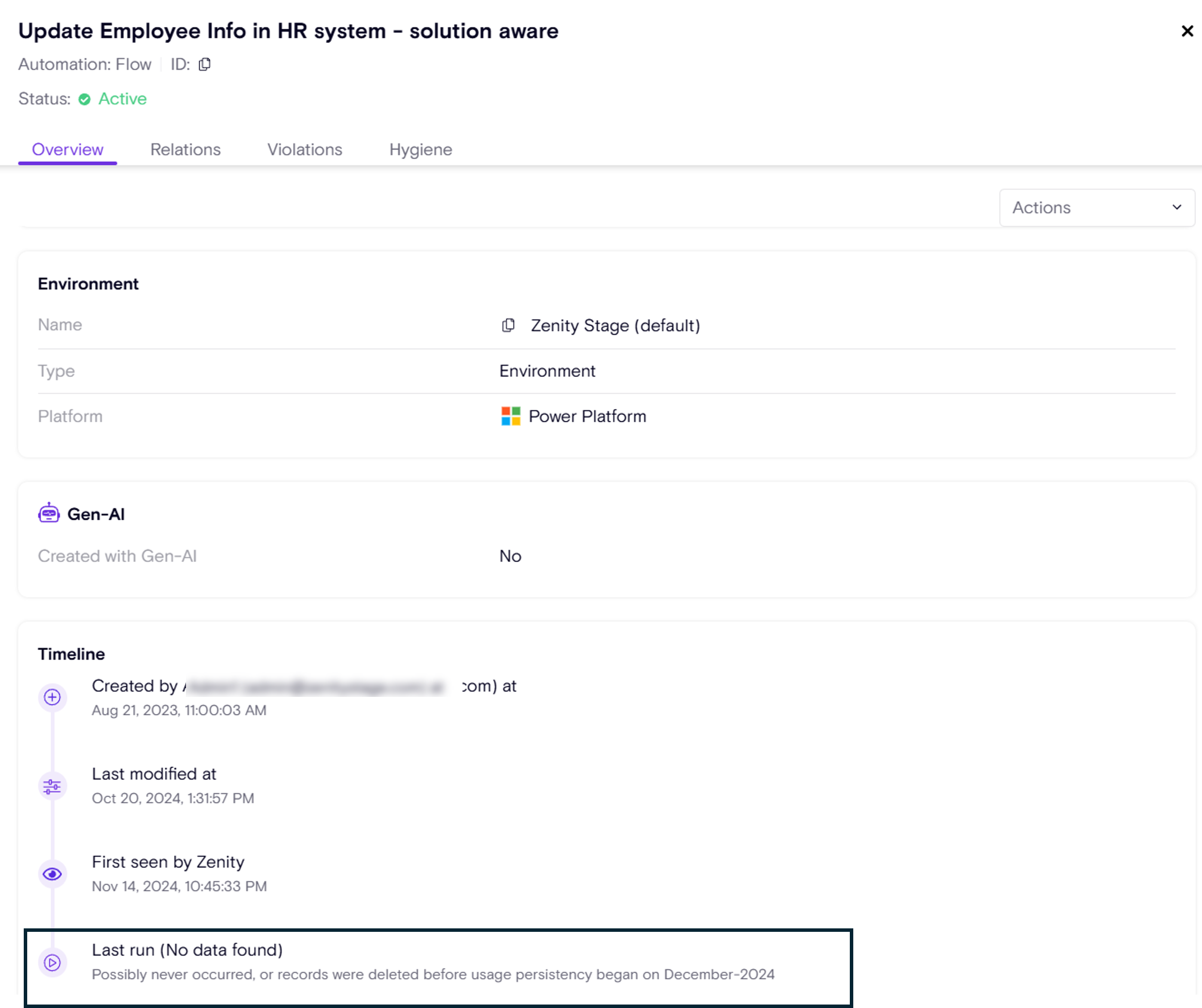
GenAI Feature Visibility in Power Platform Environments
Customers are adopting GenAI technologies all over the business, PowerPlatform is no different. AppSec & IT team need visibility into where those highly advanced features are available and in use to ensure they comply with company standard and policies.
Zenity now streamlines this process by flagging environments where the PowerPlatform AI Hub is activated, including * AI Prompts * AI Builder
In addition to enhanced metadata insights, Zenity introduces a new rule to detect and track AI feature usage, allowing customers to:
- Build security playbooks around GenAI adoption.
- Ensure GenAI capabilities are only enabled in permitted environments.
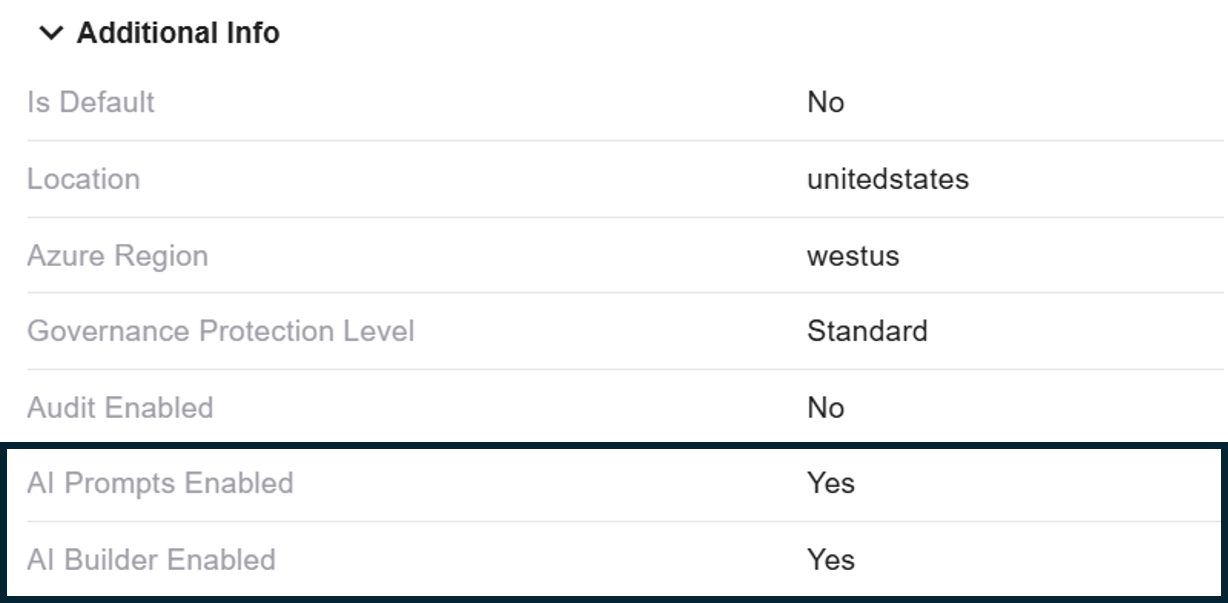
Enhanced Graph Capabilities - Introducing the New 'Relations API'
One of Zenity’s most powerful capabilities is our attack graph, which provides a visual representation of security risks and relationships between resources.
We're taking this further with the release of our new 'Relations API', the first of many planned enhancements to our Graph Query functionality.
The Relations API helps answer key security questions, such as:
✔️ What Flows are being used by a specific Agent?
✔️ Which Connectors are used in a given App?
✔️ What users have access to an automation and many more...
Currently the API is limited to a single graph hop, meaning a direct relation between resources.
In time this will become much more granular and robust, the API is in a beta phase and customers are welcomed to provide feedback.
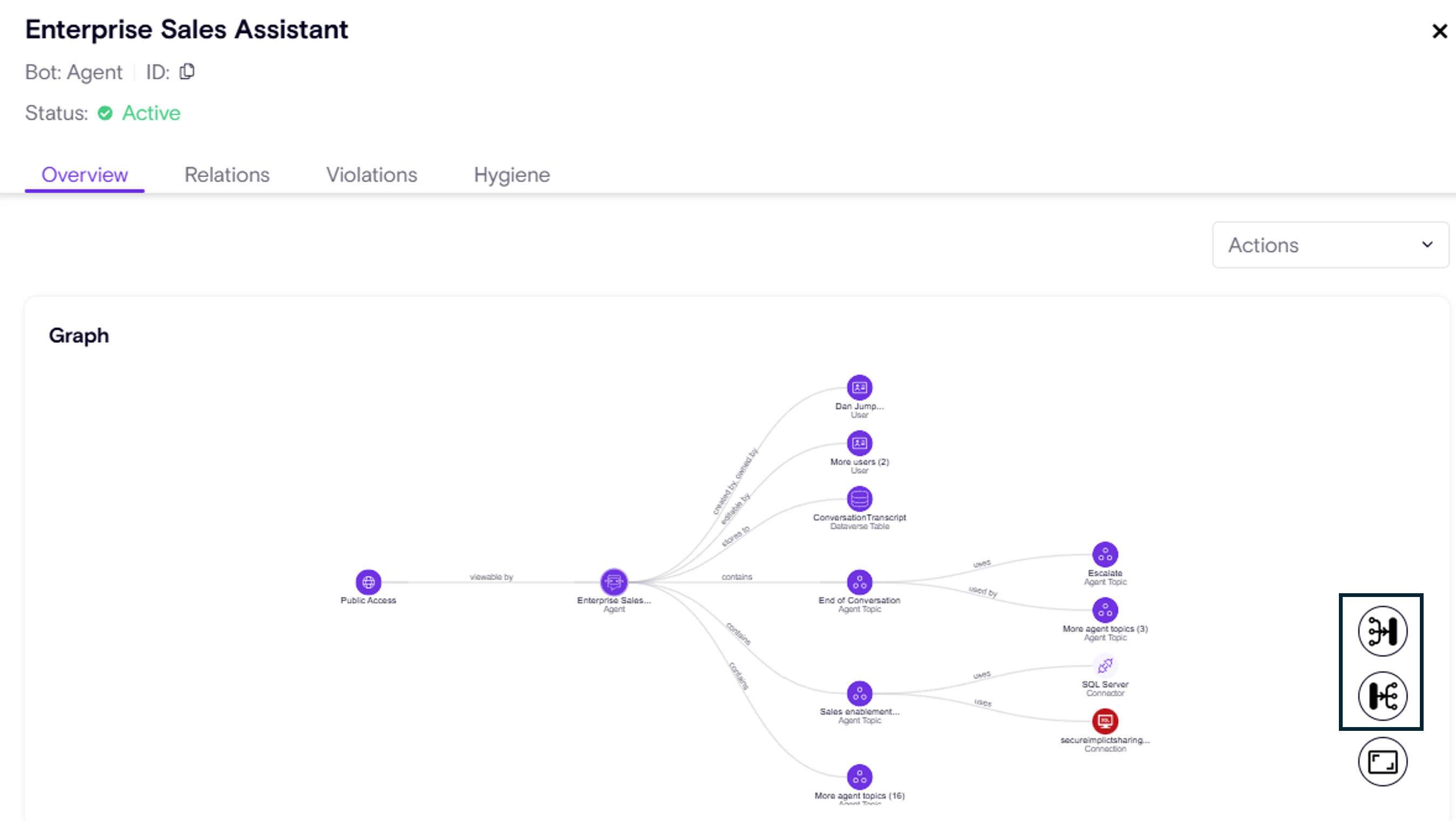
Advanced Graph User Controls
By default, the Zenity Graph intelligently groups similar nodes of the same type for clarity.
However, until now, flattening and re-grouping nodes as needed was not always intuitive.
To enhance usability, we’ve introduced two new controls: - Expand – Instantly reveal all grouped nodes for deeper investigation. - Collapse – Re-group nodes back into their original structure for a cleaner view.
This allows users to seamlessly switch between high-level insights and granular details within the Graph.
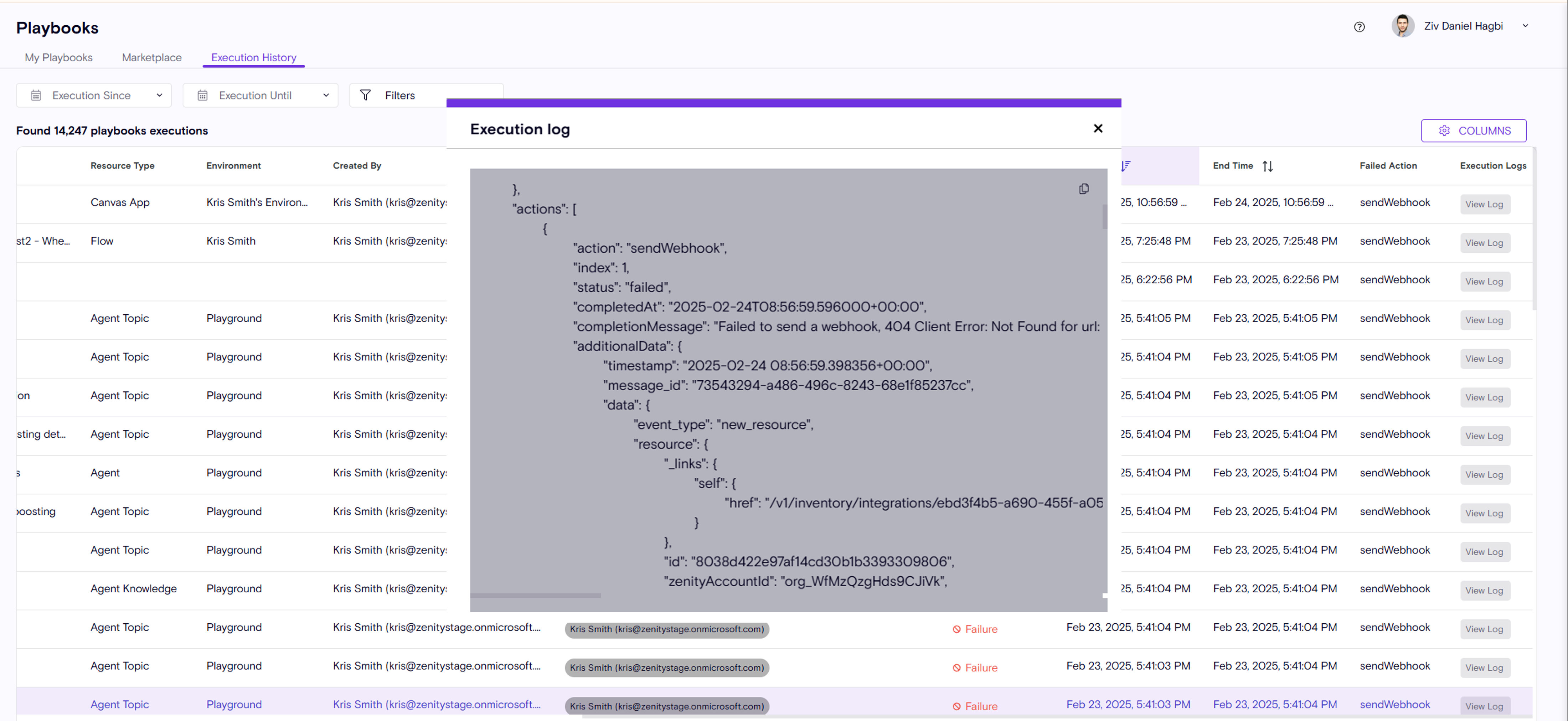
Simplifying Playbook execution log investigation
Customers rely on the Playbook Execution History log to investigate individual playbook runs and diagnose issues.
However, the previous log format was difficult to read and navigate, making it challenging to quickly understand what happened during execution.
🔹 We’ve restructured the log format to standard JSON, significantly improving readability. 🔹 Investigating playbook execution is now faster, clearer, and more intuitive.
This update ensures smoother troubleshooting and easier visibility into execution details.
New Violation Rules (a full description can be found in the Zenity policy page)
- ZN_P00153 - Flow is using a deprecated connector
- ZN_P00156 - Power Pages Site enables local sign-in
- ZN_P00161 - Canvas App has Secure implicit connections setting disabled
- ZN_P00177 - Flow potentially acts as a persistency layer
- ZN_P00183 - Agent Topic has hard-coded secrets
Upcoming Change to Resource IDs in Zenity
We’re reaching out to inform you about an upcoming change in how Zenity handles the Inventory Resource IDs for automations in Power Platform.
What’s Changing?
To prevent automation duplication scenarios across Power Platform environments, Zenity is updating the way we generate the Inventory Resource IDs for automations.
This ensures that automations in different environments do not share the same ID.
What Does It Look Like?
Inventory Page:

API:
What This Means for You:
-
No impact on existing violations, all identified risks and security issues remain intact.
-
The ‘Zenity Inventory Resource ID’ will change, existing automations will receive a new Zenity ID.
If you export resource data from Zenity for local use, we recommend re-exporting your data after this change to ensure consistency.
Next Steps: This update will be rolled out on March 9th, If you have any questions or need assistance, feel free to reach out to the Zenity support team at support@zenity.io.
Zenity January-2025
⭐ Highlights
Agentic AI is Here: Introducing SPM for Autonomous Agents & Agent Triggers in Copilot Studio
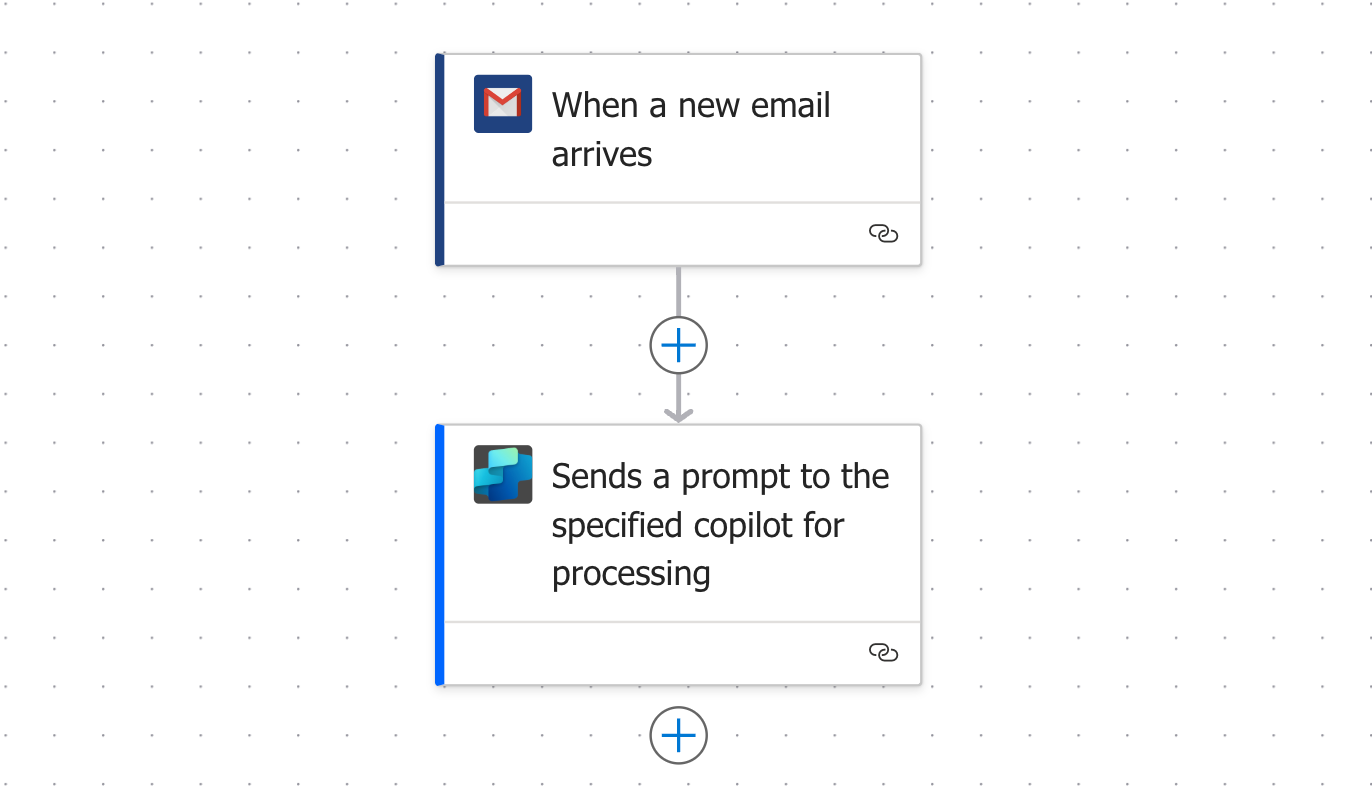
Microsoft has recently announced that anyone can now build Autonomous Agents in Copilot Studio. Autonomous Agents are AI Agents that can be triggered by things outside of the traditional chat console, whether it be data changes, API calls, emails, calendar invites, or otherwise. Autonomous Agents then act on their own to make dynamic decisions and actions to drive the business forward.
A key aspect of Autonomous Agents is their capability to operate independently and without direct chat interaction. To make that happen, Copilot Studio introduces Agent Triggers. Agent Triggers are things that respond to external events, automatically activated a designated Autonomous Agent with dynamic data inputs, enabling it to act intelligently without manual intervention. These Triggers act, and are set up as Power Automate Cloud Flows, as shown in the screenshot below.
Enhanced Visibility Capabilities
Agent Triggers can be created by any user with minimal permissions to the Agent, including the Agent owner, editors, and viewers.
While owners and editors can view the Triggers they created from within Copilot Studio, they are unable to monitor instances of users independently triggering the Agent via Power Automate.
This creates a scenario where users can access the Agent, along with its related knowledge and actions, without the owner’s awareness - even if the Agent is unpublished. Such unrestricted access raises the potential for improper or even malicious use.
To address this issue, Zenity now maps all Agent Triggers to their corresponding Agents, ensuring full traceability. Additionally, Zenity introduces several new capabilities to enhance visibility into the usage of Autonomous Agents and Triggers, effectively preventing any unauthorized or “shadow” use of Agents and their resources.
New Agent Properties
- Bot Type = Autonomous Agent (for Agents that have GenAI orchestration enabled in Copilot Studio - see screenshot)
- Autonomous Triggers Count

New Flow Property
- Is Bot Trigger = Yes/No

New Predefined Queries
- Get all Autonomous Agents
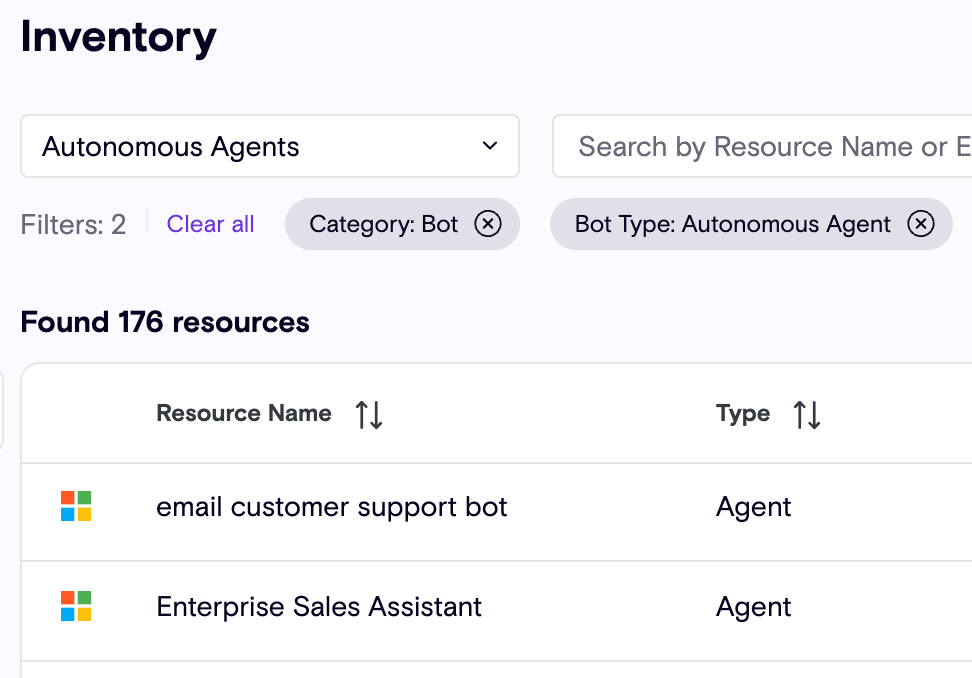
- Get all Agent Trigger Flows
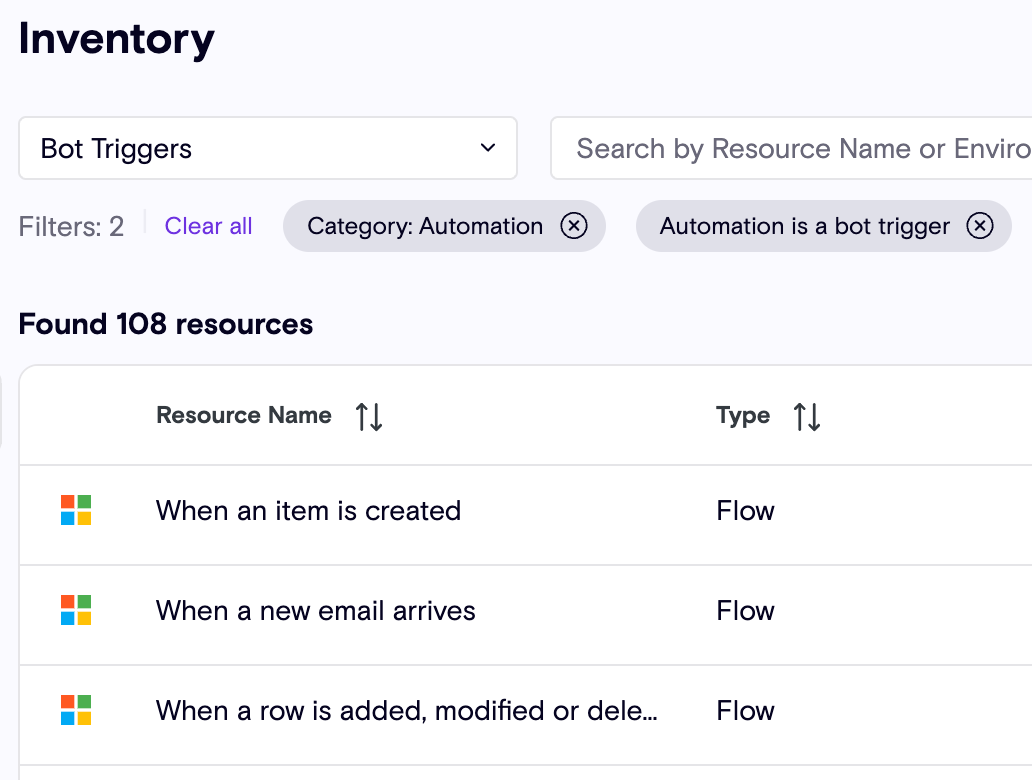
New Power Platform Violation Rules
ZN_P00180 - Potentially sensitive agent has a trigger which is vulnerable to manipulation by anonymous users through email
ZN_P00184 - Flow is exposed to anonymous users through email trigger
Autonomous Agents, which were previously accessible only through chat via a published channel, can now be executed using Power Automate flows. This shift in functionality transfers the responsibility for governing agent access from the agent’s owner to the flow owner. Consequently, anyone with access to the flow also has access to the agent, making proper access management critical. Improperly secured flows could potentially expose the agent to unauthorized or even anonymous users.
A common use case for agent triggers involves a flow that executes an agent in response to incoming emails, such as customer support requests. However, if these email-triggered flows are not properly configured with robust safeguards, they could allow any sender to trigger the agent by merely emailing the designated inbox. Such vulnerabilities expose the agent to potential misuse or manipulation by unauthorized parties.
To mitigate this risk and endure secure and authorized usage, two new detection rules identify improperly configured email trigger flows, as well as agents affected by such vulnerable flows.
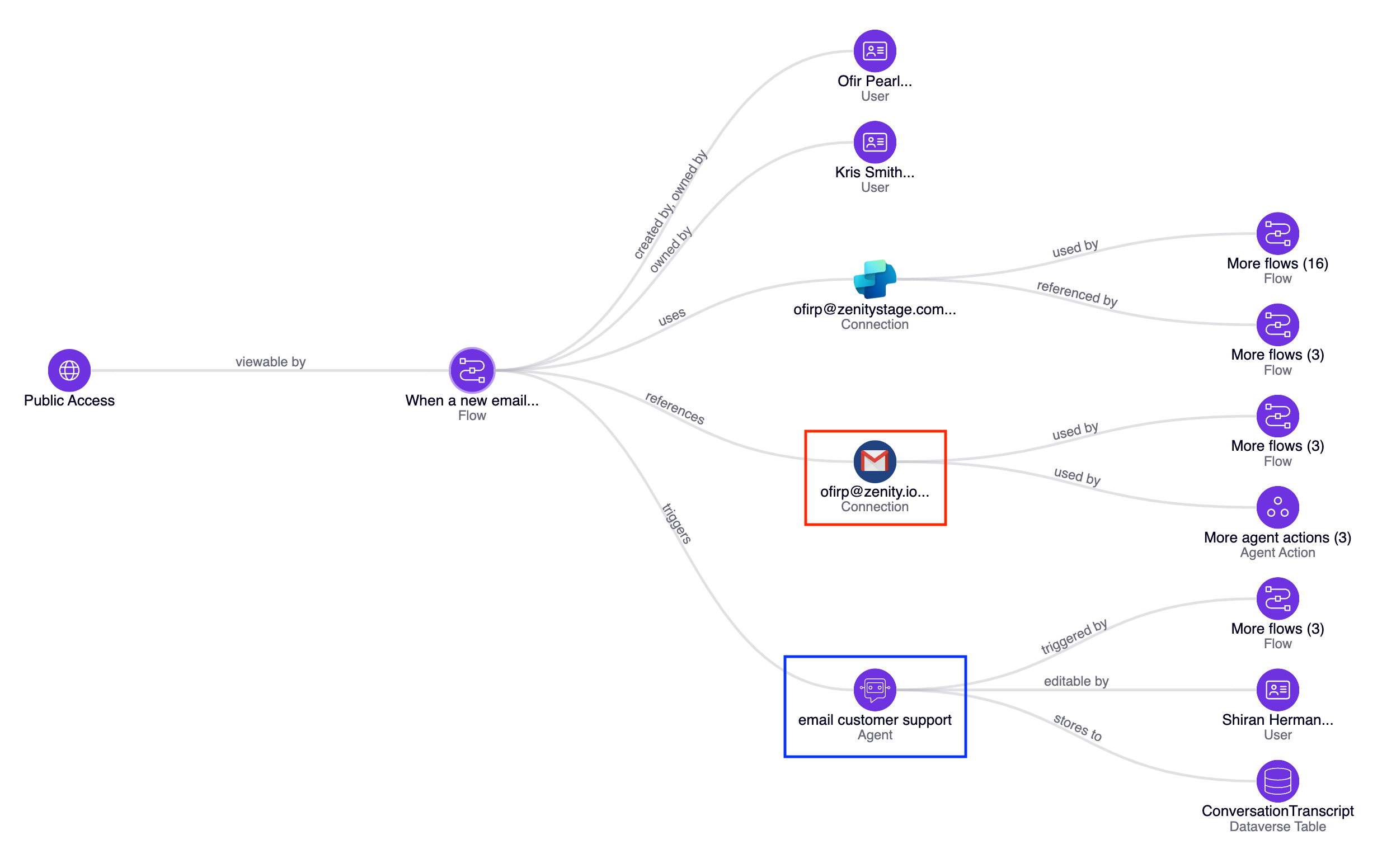
ZN_P00182 - Agent is triggered by a shadow trigger flow
Agents Triggers can be created either by the owners of the agent within Copilot Studio or by users with viewer permissions through Power Automate. Since agent owners only have visibility into the triggers they created in Copilot Studio, a new potential risk is introduces where users can create triggers that access the agent and its components without the owner’s knowledge. Such activity could lead to improper or even malicious use of the agent.
To mitigate this risk, a specific rule has been implemented to empower administrators to detect and address any unauthorized or “shadow” triggers. This measure ensures the proper and secure utilization of sensitive agents and their resources, protecting them from unintended or harmful exploitation.
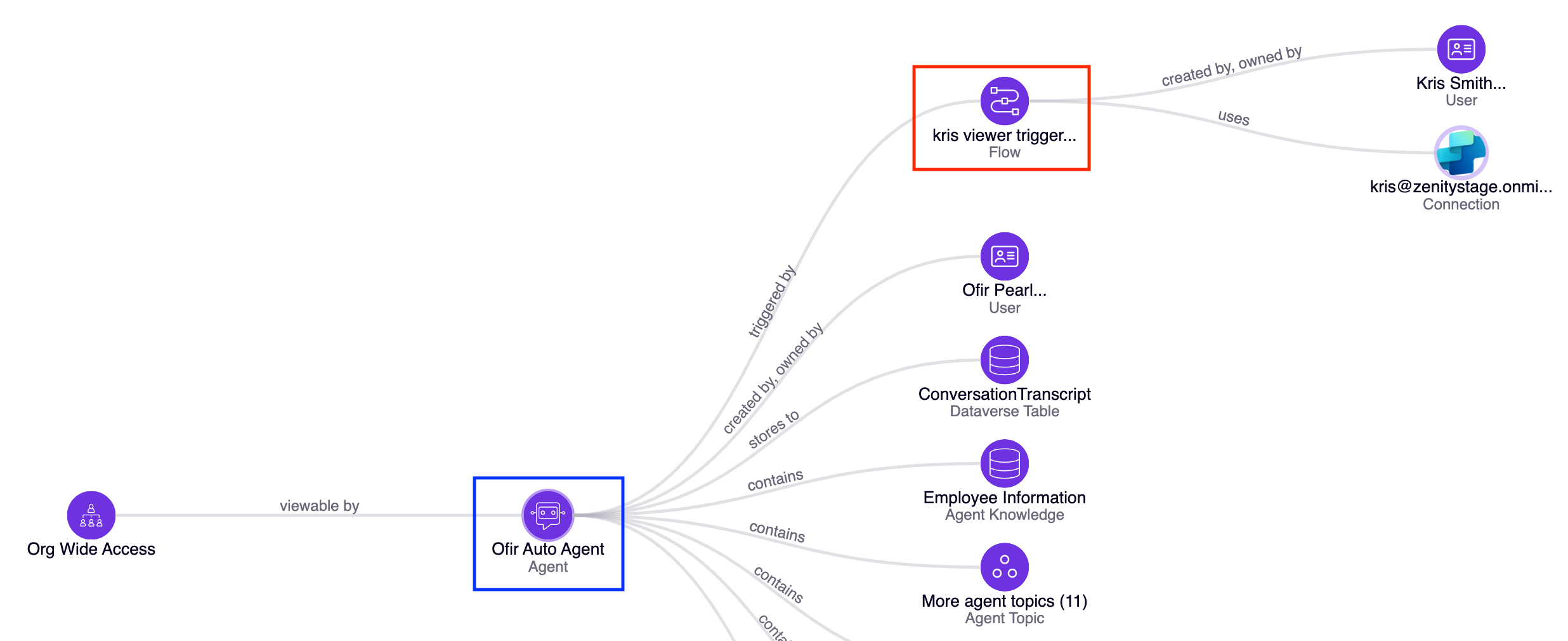
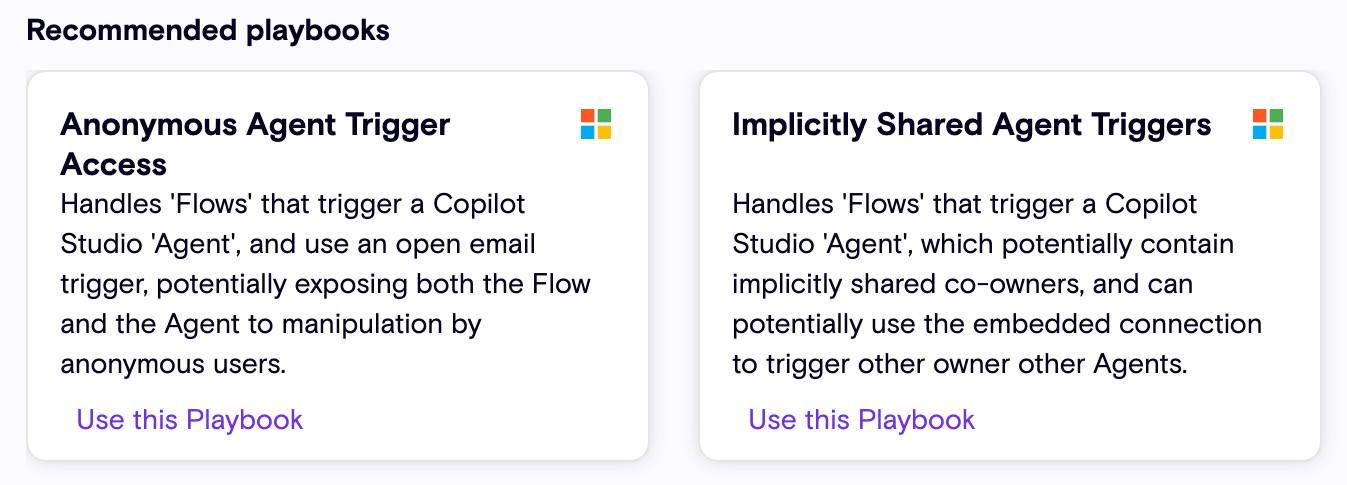
New Remediation Playbook Templates
In our Playbook Marketplace you can find two new Playbook Templates to remediate security risks related to Agent Triggers:
- Anonymous Agent Trigger Access - Stop all flows that are potentially exposed to anonymous users manipulation via HTTP or open email trigger.
- Implicitly Shared Agent Triggers - Isolates all Agent Trigger Flows, securing the Flow owner's embedded Copilot Studio credentials.
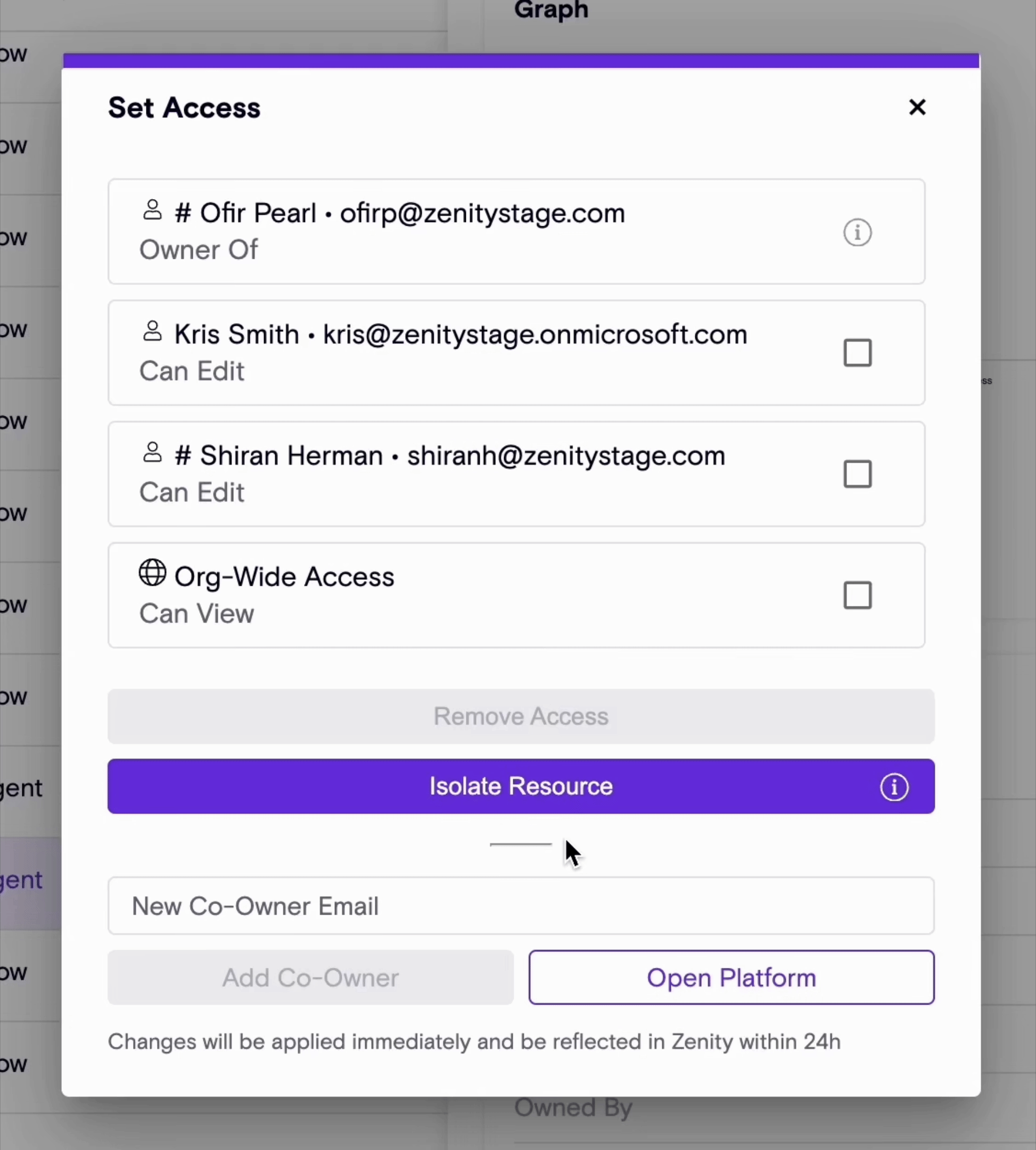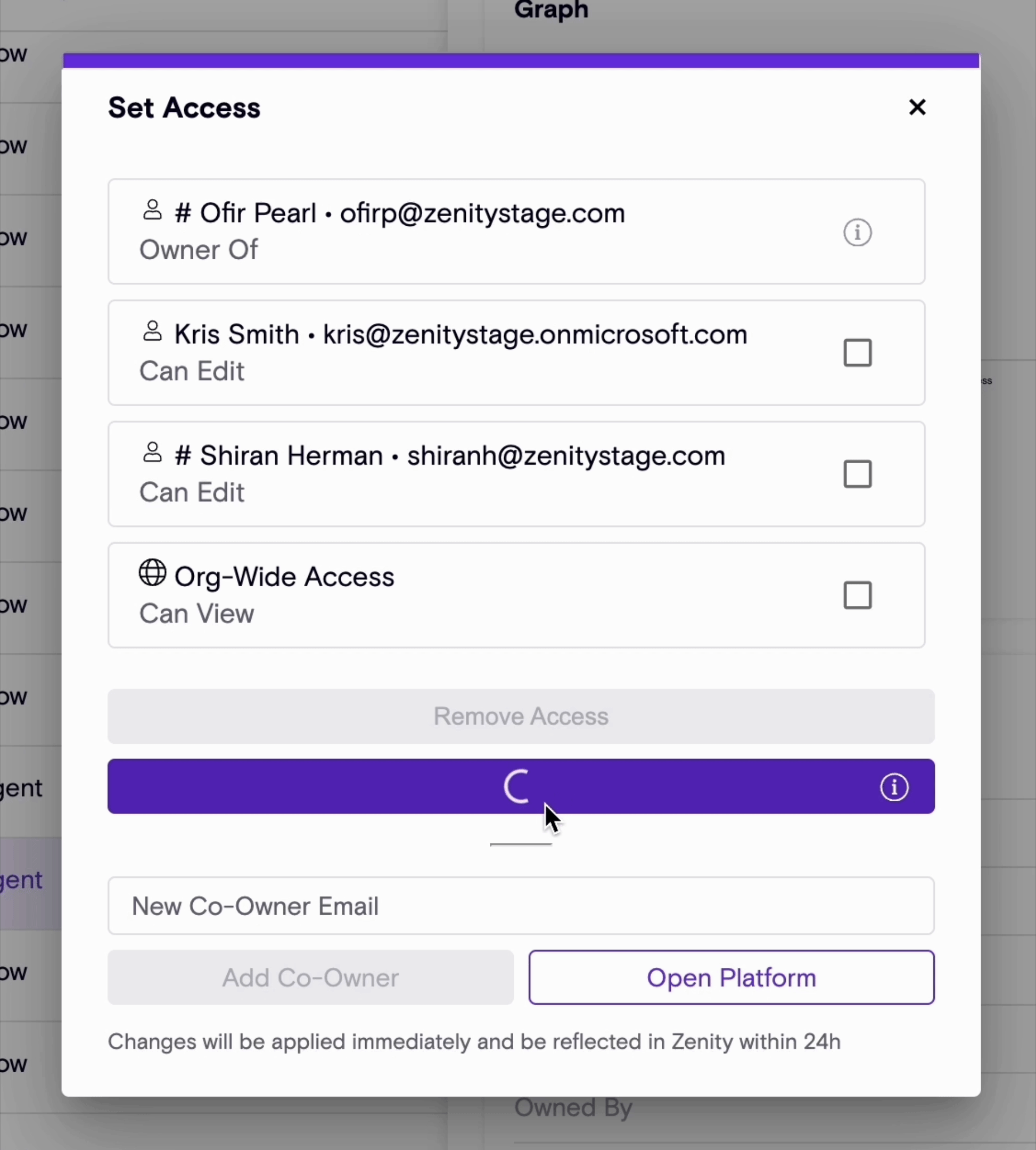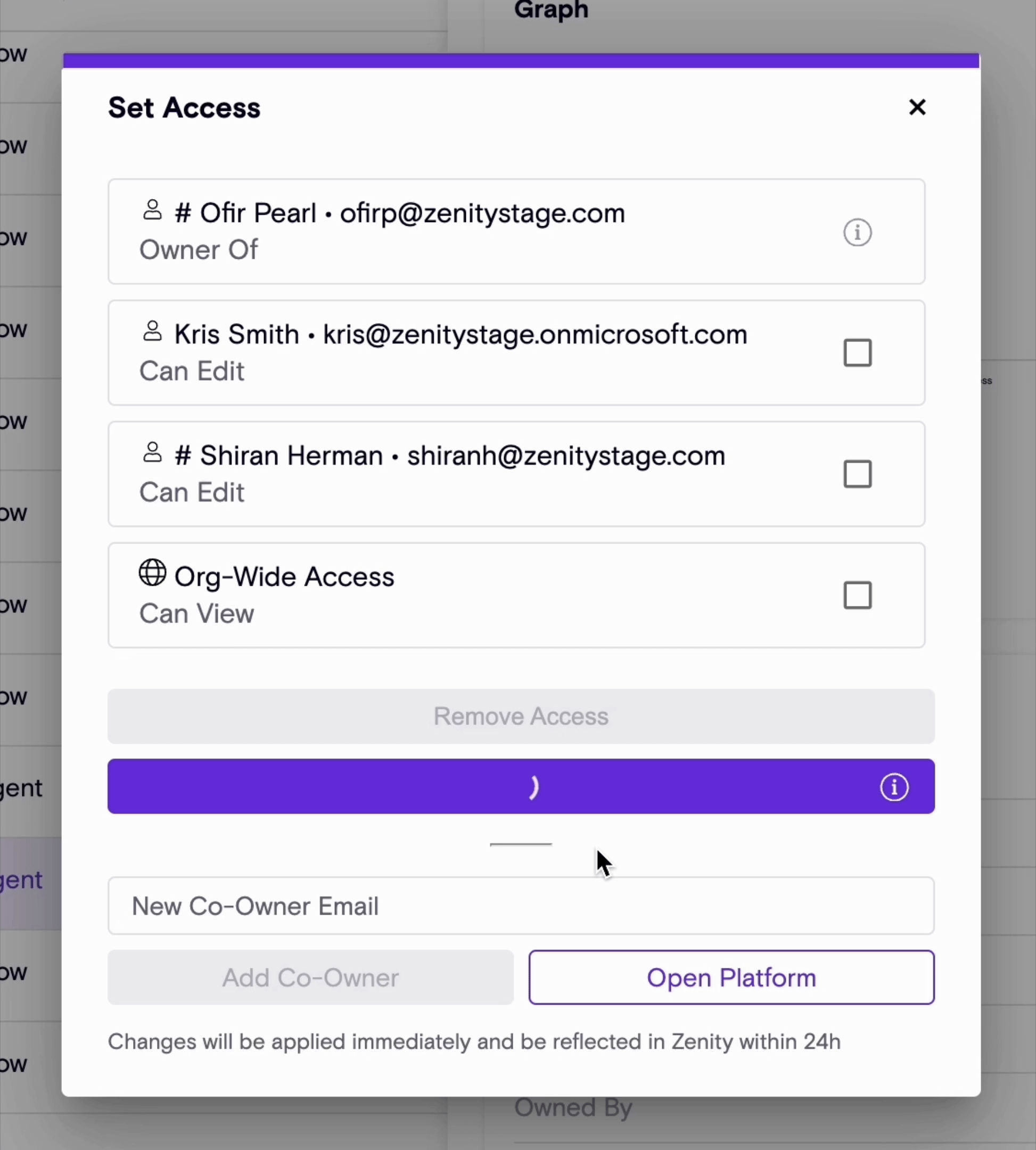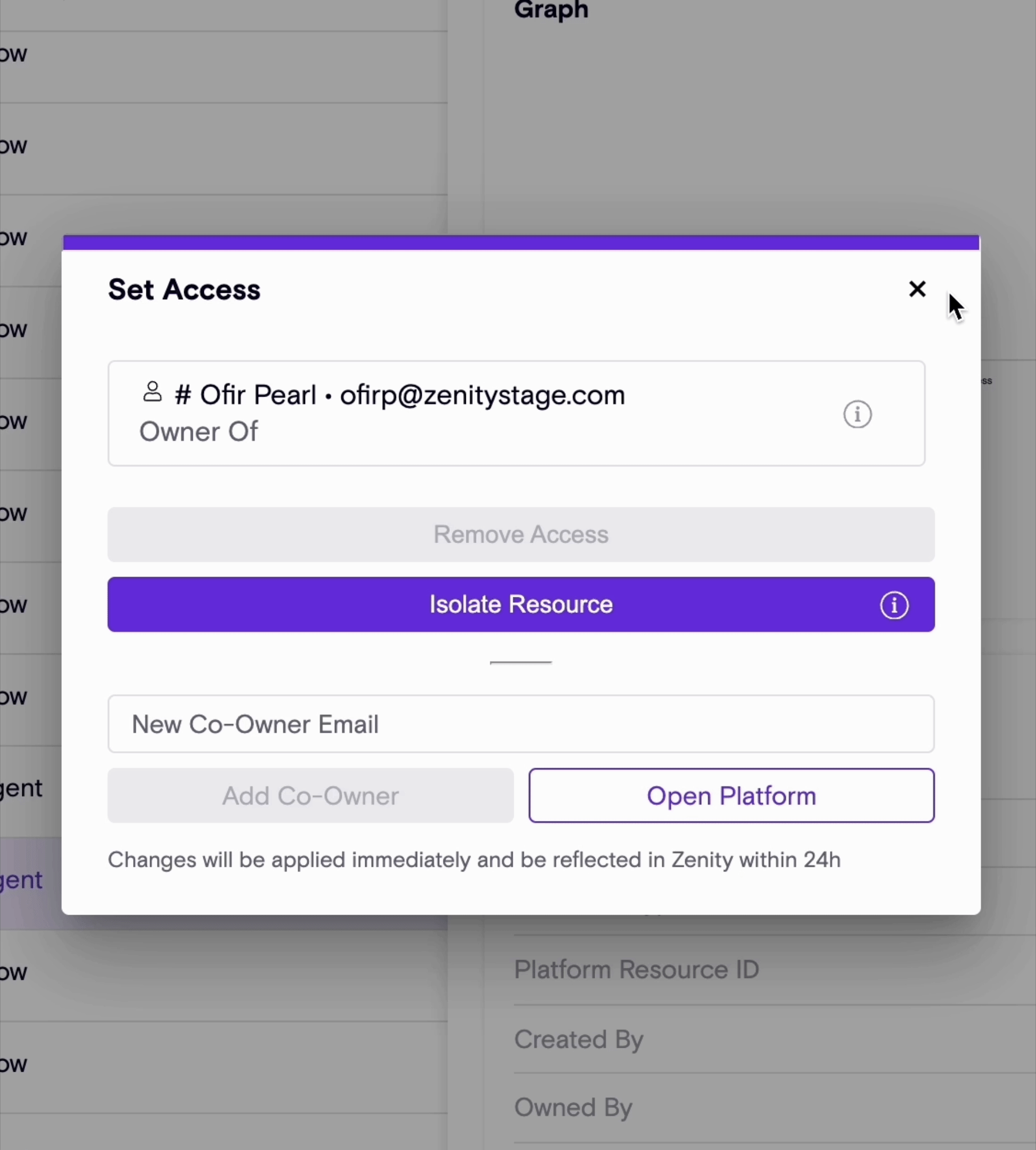
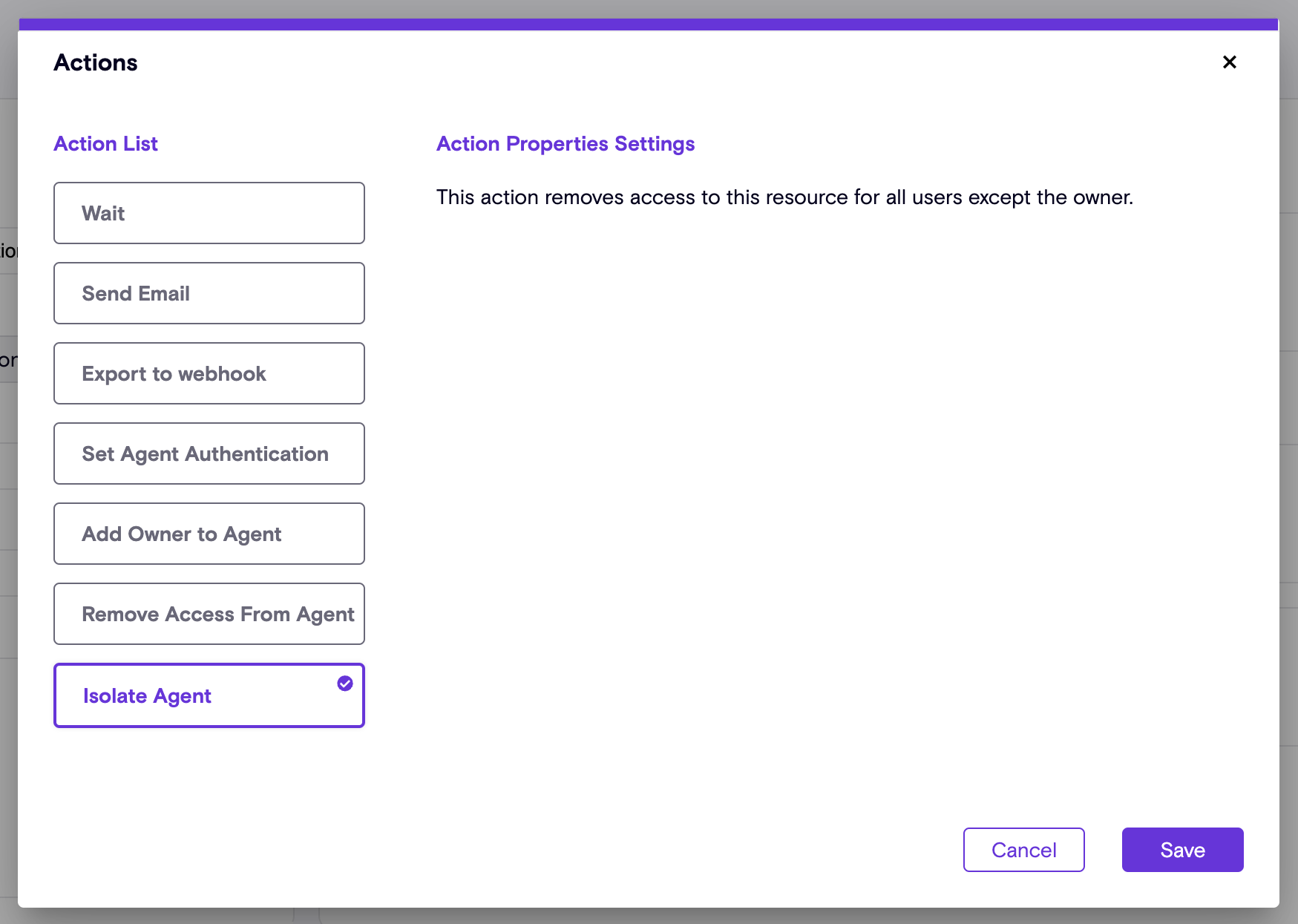
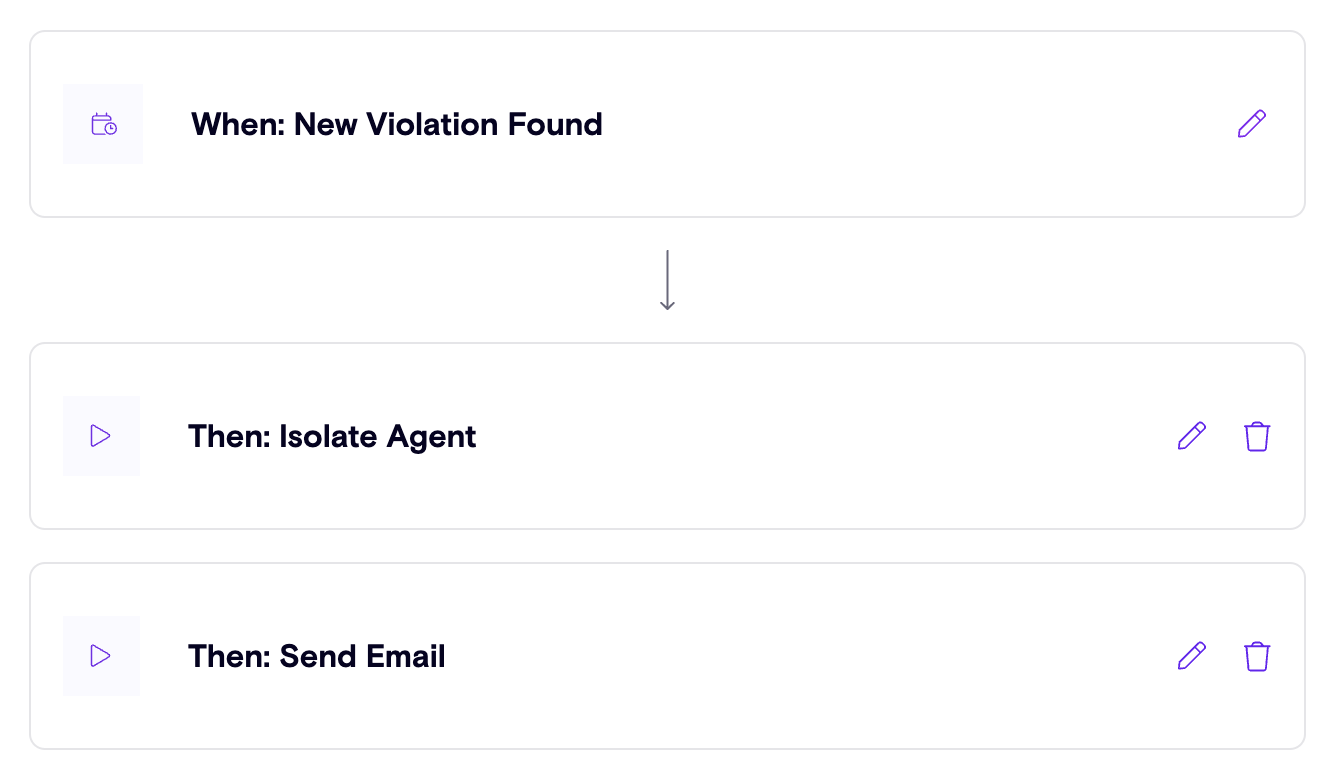
Enhanced Oversharing Governance: Introducing The New 'Isolate' Feature
Low-Code/No-Code resources can easily be overshared by builders, potentially allowing unauthorized access to internal company assets & sensitive information. A few common scenarios include:
- Agents shared with Unauthorized Guest users
- Agent shared with the entire tenant, allowing all tenant users both chat with the Agent and trigger it via Power Automate.
- Flow Implicitly shares embedded owner connection.
Building on Zenity’s “Remove Access” feature (see release notes), the newly introduced “Isolate” capability empowers users to swiftly revoke all access to a resource - both editor and viewer permissions - except for the primary resource owner.
With a single click, Zenity enables both manual remediation (Click2Fix) and automated Playbook actions to streamline governance efforts, ensuring robust control over shared resources and reducing potential security and compliance risks.
Isolate Click2Fix Action
Isolate Playbook in action: Agent Oversharing Remediation
Copilot Studio Rebranding: "Copilot" → "Agent"
Following Microsoft's rebranding presented in the recent Ignite 2024 event, all LLM Agents built with Copilot Studio are now named "Agents" and not "Copilots", where "Copilot" remains the correct definition for the chatbot accessible through Microsoft365-integrated apps & services.
Zenity has updated all the relevant resources & data points in the app accordingly, including:
Inventory Resource Types
- Copilot → Agent
- Copilot Knowledge → Agent Knowledge
- Copilot Topic → Agent Topic
- Copilot Action → Agent Action
Zenity Rules
- All rule titles, descriptions, and findings now use the correct terminology.
- Changes will not affect resolved violations.
Zenity December-2024
⭐ Highlights
Introducing AI Detection & Response (AIDR)
Zenity introduces AI Detection & Response (AIDR) — a new runtime security layer designed to protect enterprise AI agents from emerging GenAI threats such as prompt injections, data leakage, and model manipulation.
The offering supports M365 copilot and Copilot Studio agents, and includs:
- Runtime Visibility: Gain near real-time observability into every AI agent interaction, including user prompts, AI responses, and internal tool invocations. View granular Steps (User Message, AI Message, RAG, Tool Invocation, Trigger) enriched with metadata like actor, timestamp, and service.
** Sensitive content is processed but never stored, ensuring data privacy.
** Zenity retains 3 months of runtime metadata for investigations.
- Threat Detection & Response: A continuously evolving detection engine identifies risks, anomalies, and suspicious behaviors in AI agent activity.
** Findings are mapped to OWASP LLM and MITRE ATLAS frameworks.
** Severity levels (low, medium, high) help prioritize threats based on impact and confidence.
** Each finding includes detailed evidence, contextual metadata, and recommended response actions.
- API-based response: Automate response through the new AIDR API.
** List Findings and List Agent Steps endpoints support filtering by AI service, time range, or rule ID.
** Enables seamless integration with existing security workflows and custom alerting pipelines.
Detailed user guide API Reference
Surfacing Accurate Resource Ownership across Zenity
Zenity streamlines the remediation process between Application Security teams and the actual makers.
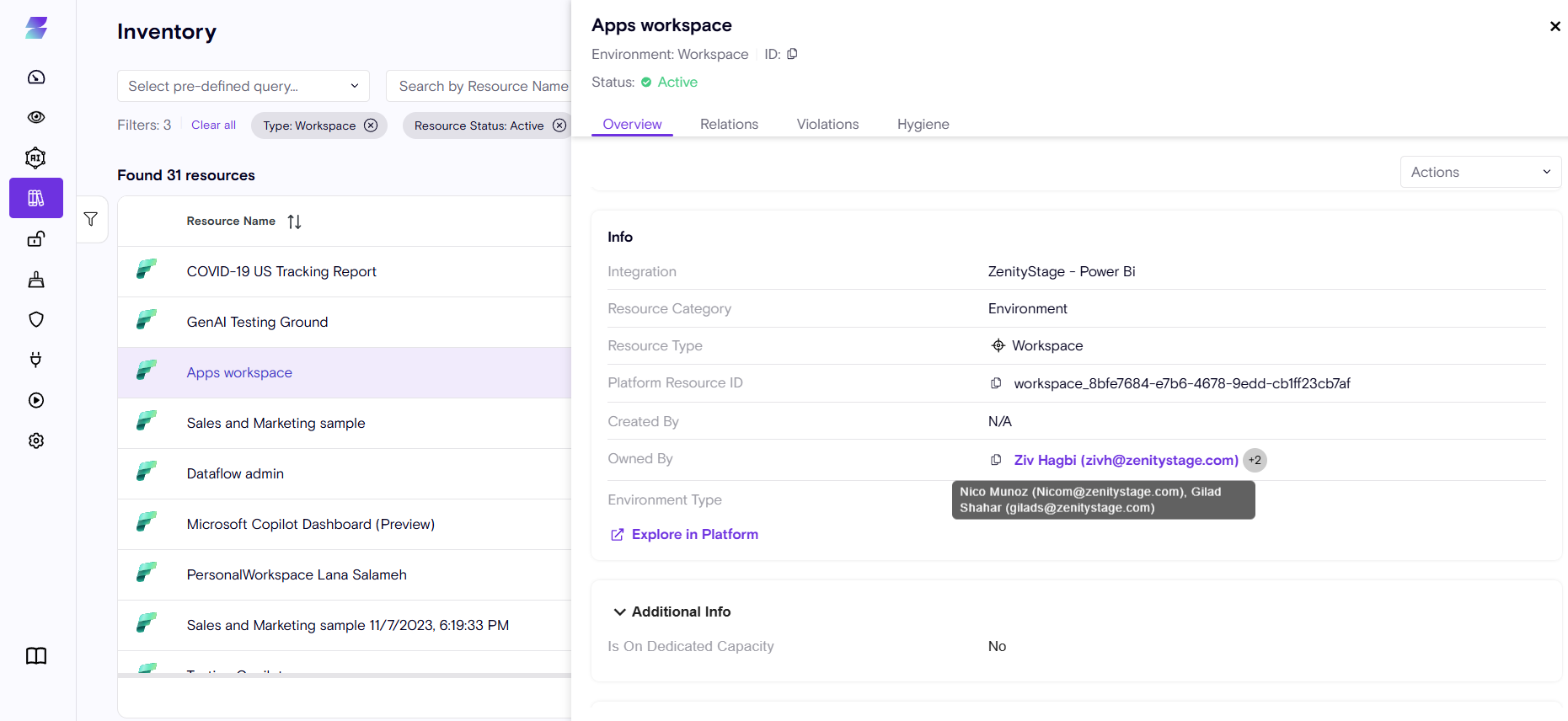
As such, the most relevant person to own an issue is the Owner of the resource and not necessarily the user who created it.
Now, Zenity provides full visibility into Resource ownership that helps target the right user to address the risk.
This is true throughout the product:
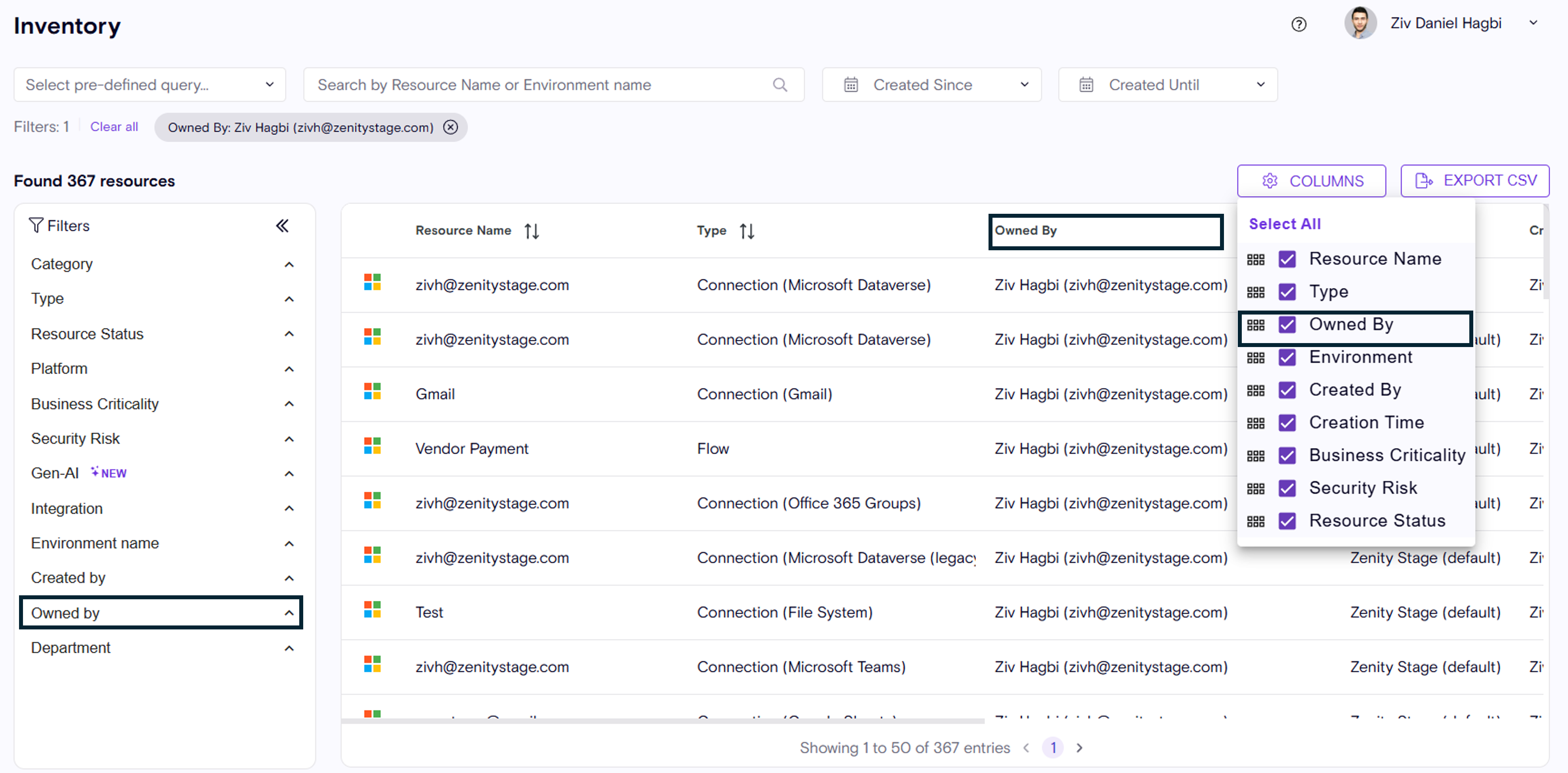
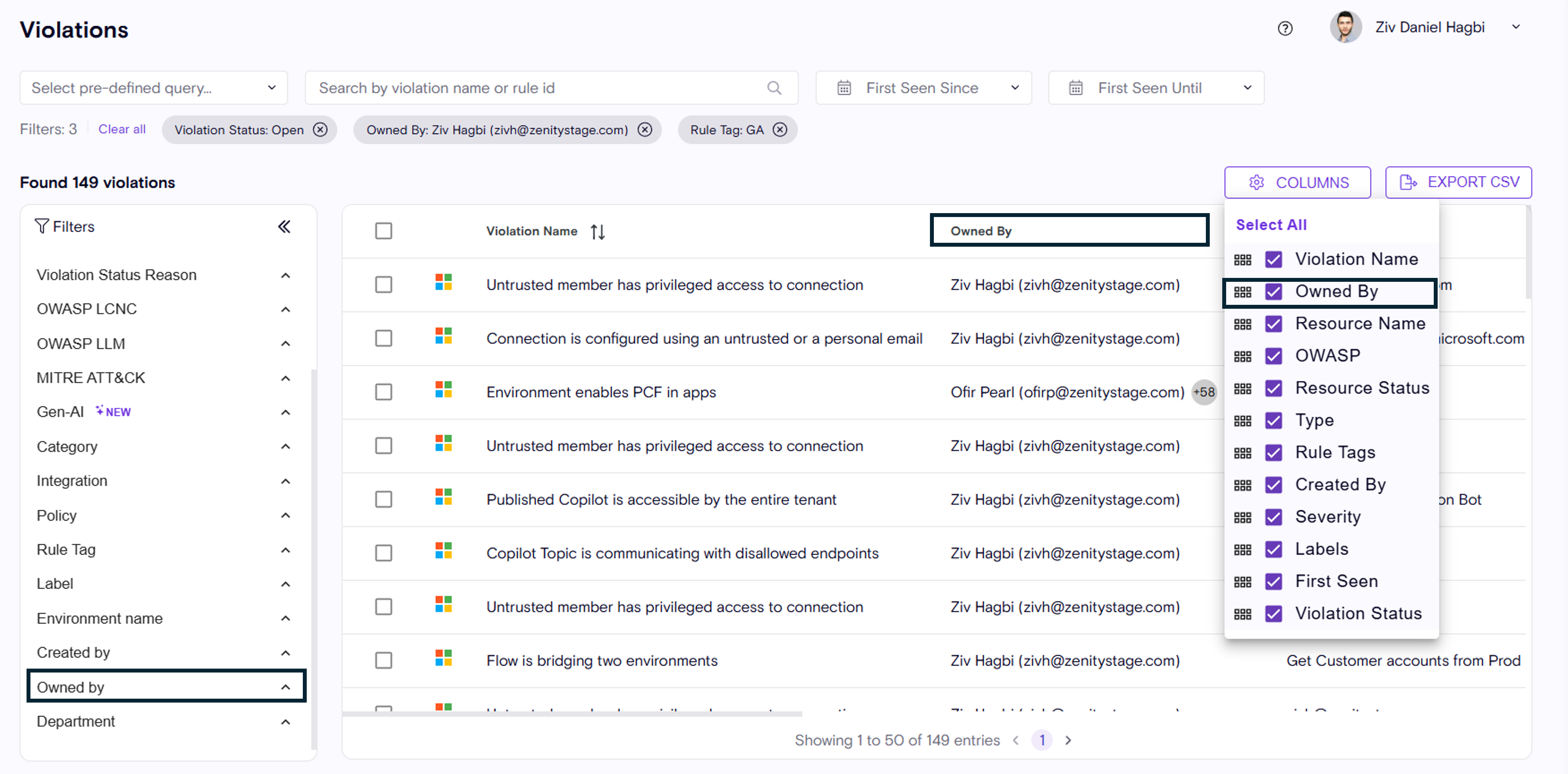
- Violation & Inventory experiences, including, Columns representation, Filters, and data-model.
Inventory
Violations
Playbooks
- In some cases a resource might have multiple owners, Zenity will present them as such and allow you to view them all.
Introducing AI-SPM Support for Fabric AI-Skills
Zenity is the 1st company in the world who keeps track over AI-Skills and their underlying data.
AI-Skills in Fabric are LLM engines that simplify interactions with data.
This AI-Skills can be highly sensitive as the data they expose can be critical for the organization.
Hence, it's imperative to have eyes over who can access the AI-Skills and the underlying data and ensure there is no unauthorized access to sensitive skills.
AI Skill
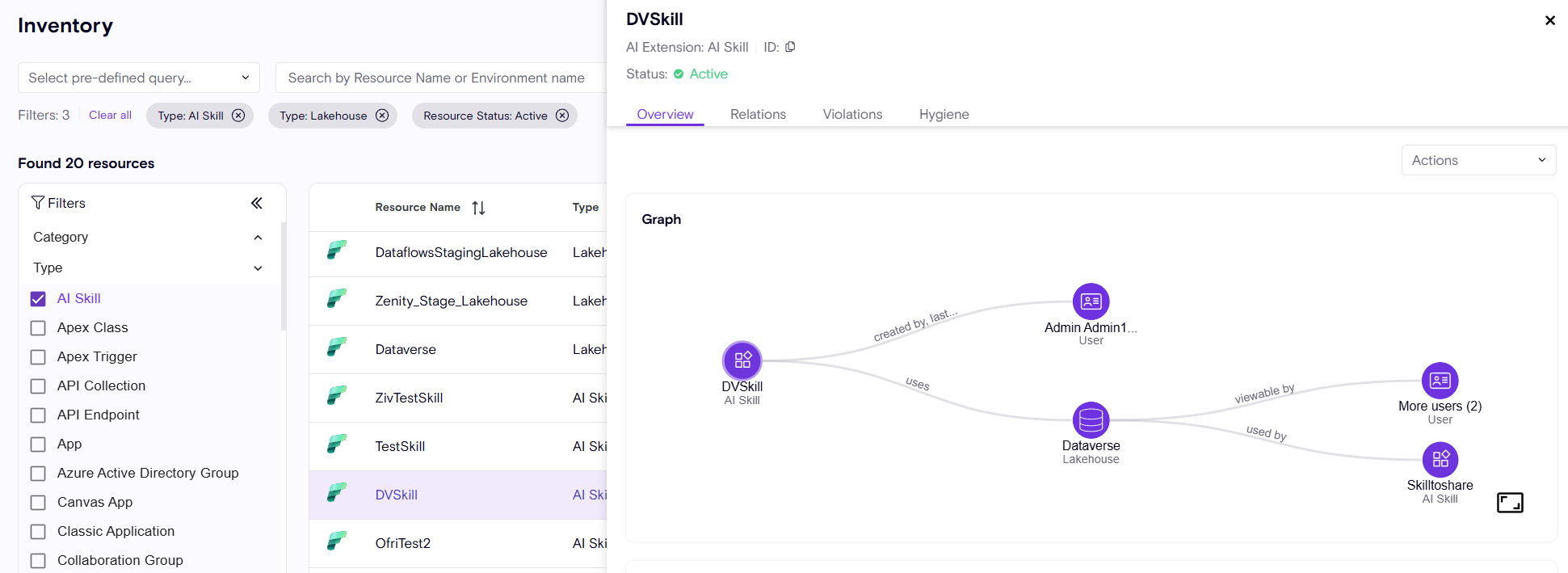
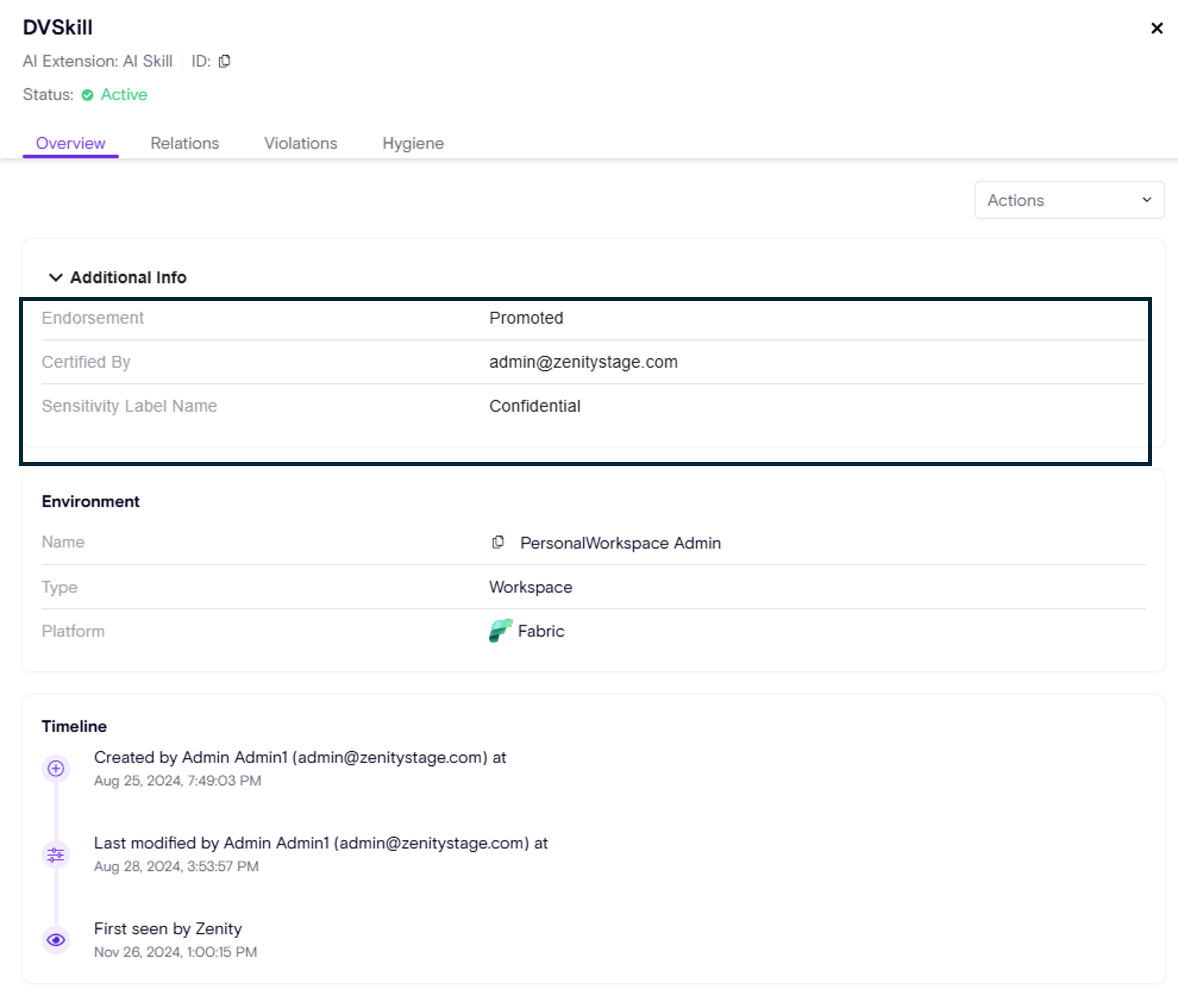
Zenity provides additional measurements to enrich the risk context.
- Sensitivity label (as applied by users or Microsoft Purview)
- Endorsement - the level of trust the org has for this AI-Skill (Promoted, Certified) and of by who.
In addition, to AI-Skills we are adding supports to the actual underlying resources used by the AI-Skills. These are called 'Lakehouses', they as well have additional information to quantify risk:
- Sensitivity label (as applied by users or Microsoft Purview)
- Endorsement - the level of trust the organization has for this AI-Skill (Promoted, Certified) and by who.
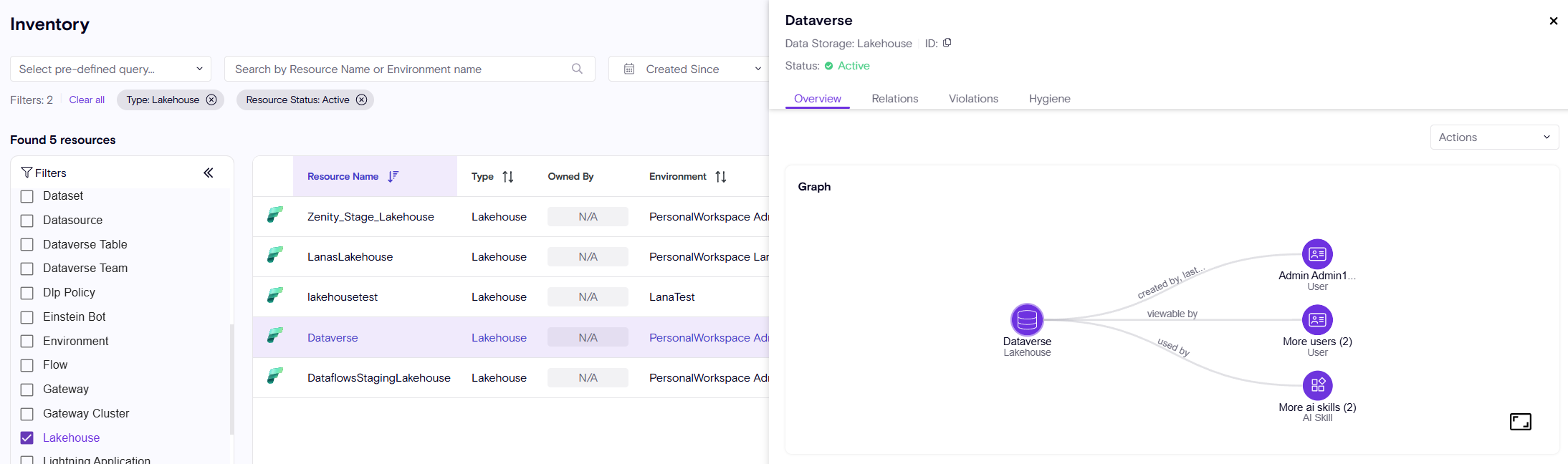
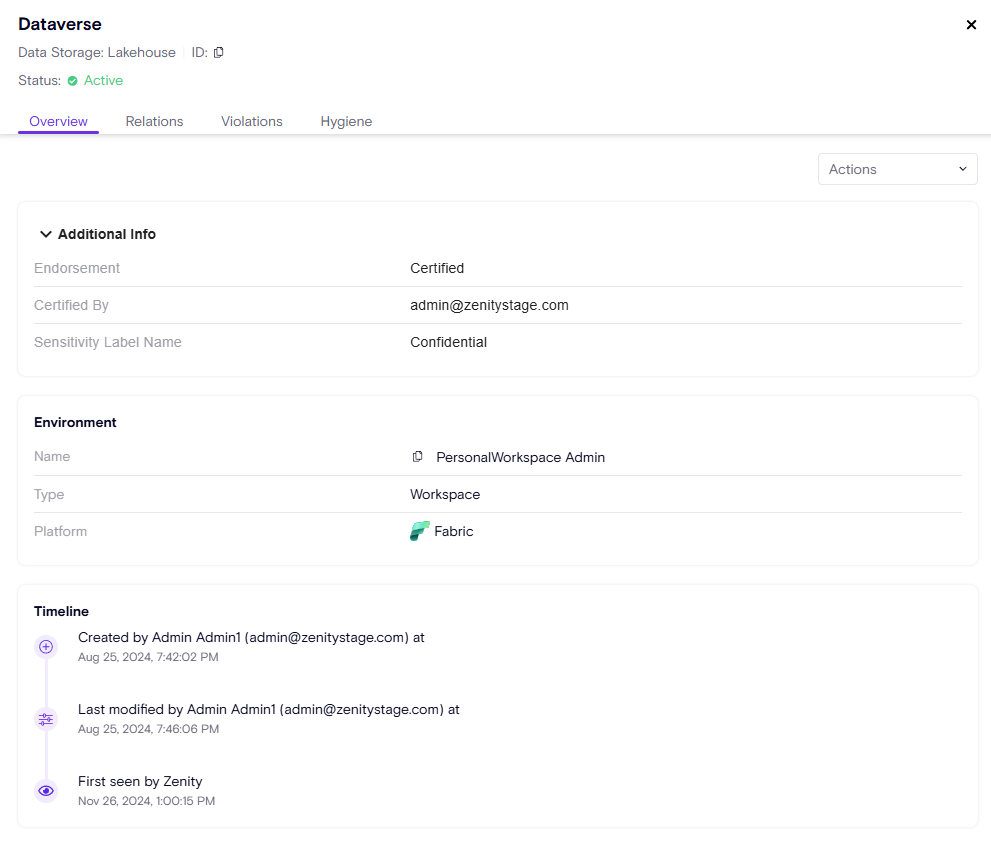
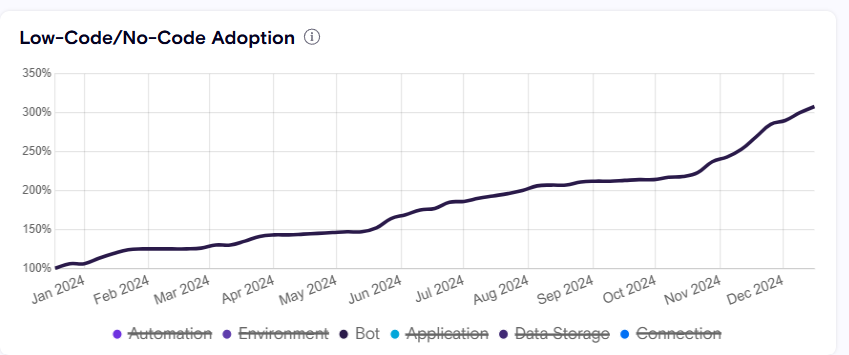
Providing Dashboard aggregations for Agents
Zenity now supports AI Agents across the dashboards.
Overview Page
Visibility Page
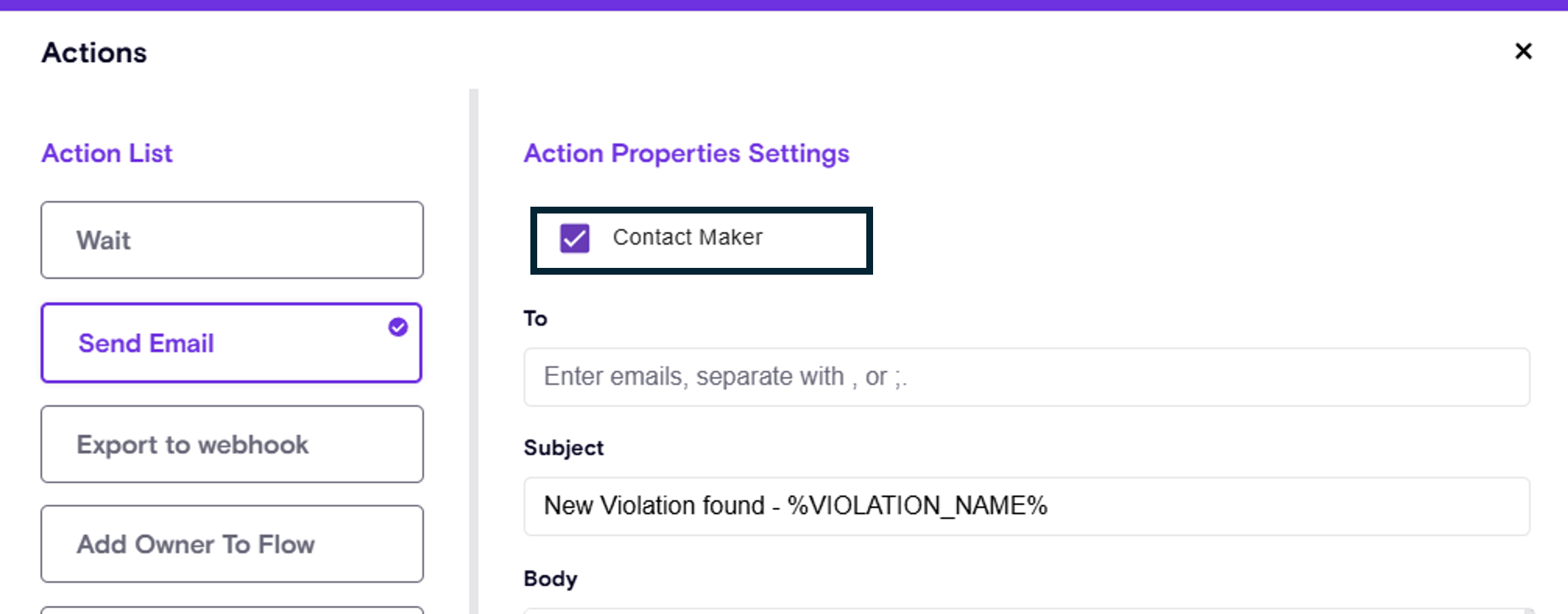
Contact Maker action
The Contact Maker action in the Zenity playbooks now supports contacting by default the current owner.
Meaning, Zenity will identify and send the information to the resource owner.
As a fallback if the owner doesn't exists, it will contact the user that created the resource.
Upcoming Improvement to Platform Resource ID Presentation & Deprecation announcement
We’re streamlining how Platform Resource IDs for Dataverse resources are displayed in Zenity to improve clarity and usability.
Starting December 24, 2024, only the Platform Resource ID will be shown, eliminating the need for references that include the Environment ID (e.g., Environment_ID@@Platform_Resource_ID).
This update has minimal to no impact on your experience and is designed to enhance navigation and search accuracy.
What You Need to Know:
If you use the full ID (Environment_ID@@Platform_Resource_ID) locally for any references, it will no longer match correctly and you would need to:,
- Re-export your violations/resources after the change.
- Use only the part after the @@, which corresponds to the Platform Resource ID.
If you don't, no action is required.
As a part of this effort we are also deprecating 'theget_resource_by_platform_resource_id' API route as it is no longer in use.
Thank you for your understanding as we make this improvement.
If you have any questions or concerns, feel free to reach out to our support team
New Violation Rules (a full description can be found in the Zenity policy page)
- ZN_P00161 - Canvas App has Secure implicit connections setting disabled
Violation Rules Updates (a full description can be found in the Zenity
After careful examination, rule ZN_P00017 (Connection is using a deprecated connector) will be moved to the hygiene category. There is no customer action required.
Zenity October-2024
⭐ Highlights
Enhanced experience in the 'Playbook Execution History' table
The execution history table capabilities were updated to provide an easier experience for our users, including:
- Resizing of columns
- Add/Remove Columns
- Reposition columns
Visibility into 'Re-Open' violations
As violations can re-manifest, users should re-assess them with care. Potentially a malicious user or an innocent user repeating the same mistake over and over again.
Zenity allows users to filter by these violations that were 'Re-Opened' persisting the 1st time they triggered.
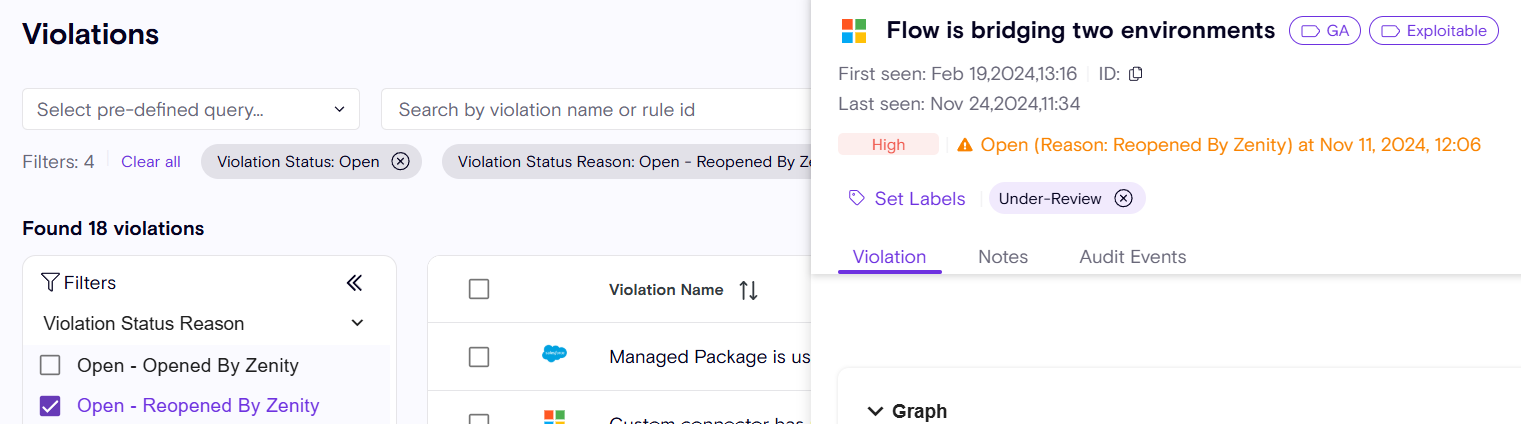
Visibility into integration auth method
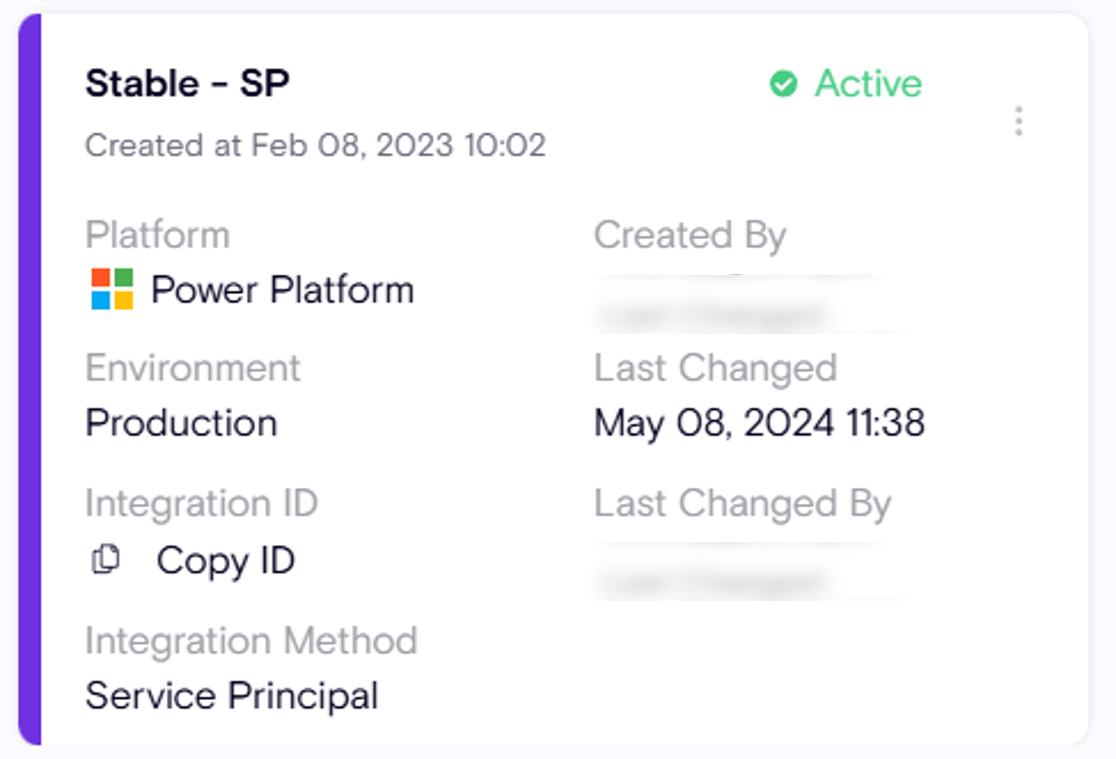
Many times users would like to have a quick understanding of how the integration was set up. For this an Admin would have to go and pull that information, tedious and time consuming. Now any user who has access to the Integrations page will be able to view it.
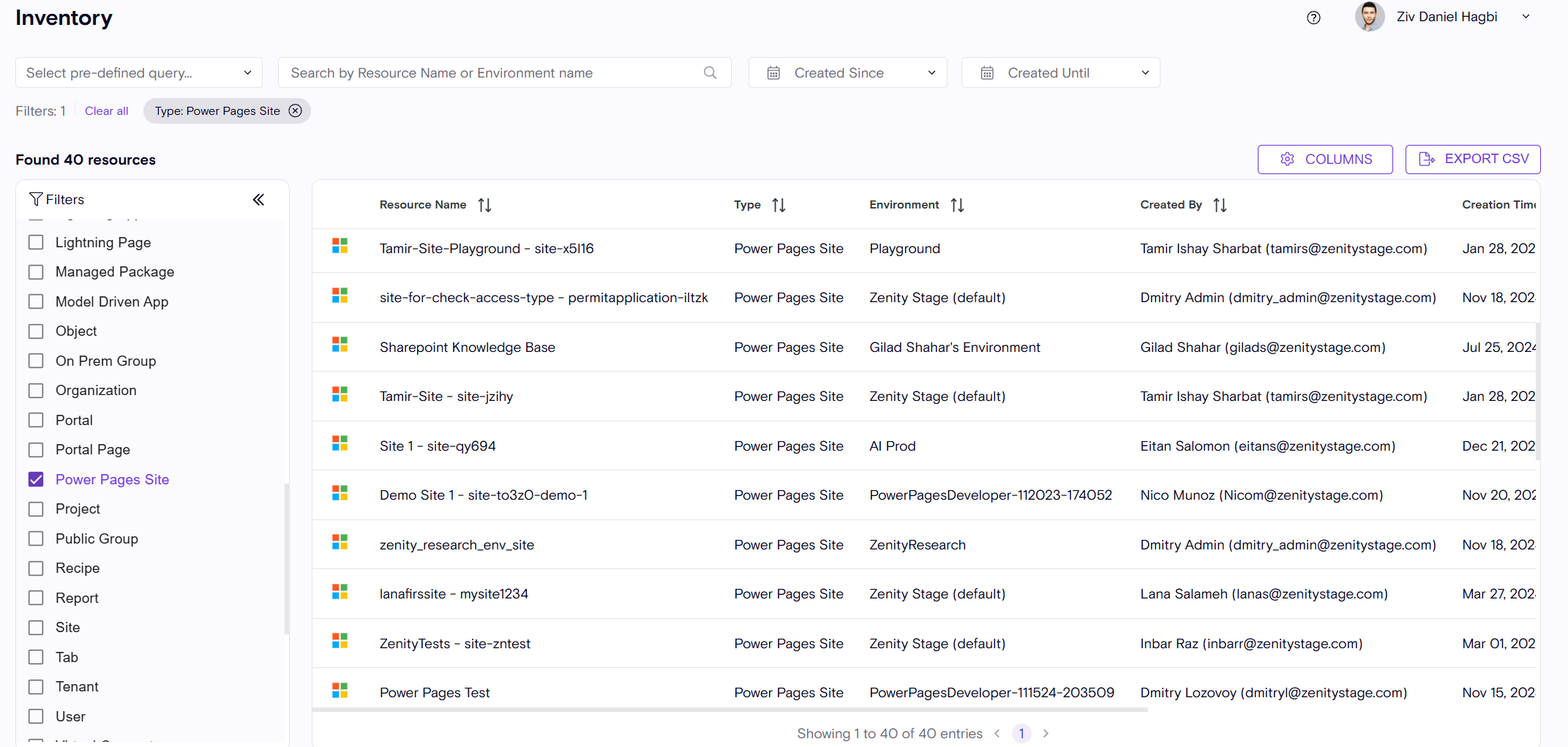
Visibility into PowerPages sites
With the increasing usage of the PowerPages (websites) in PowerPlatform. Now customers can use Zenity to view all created Sites and their associated risks.
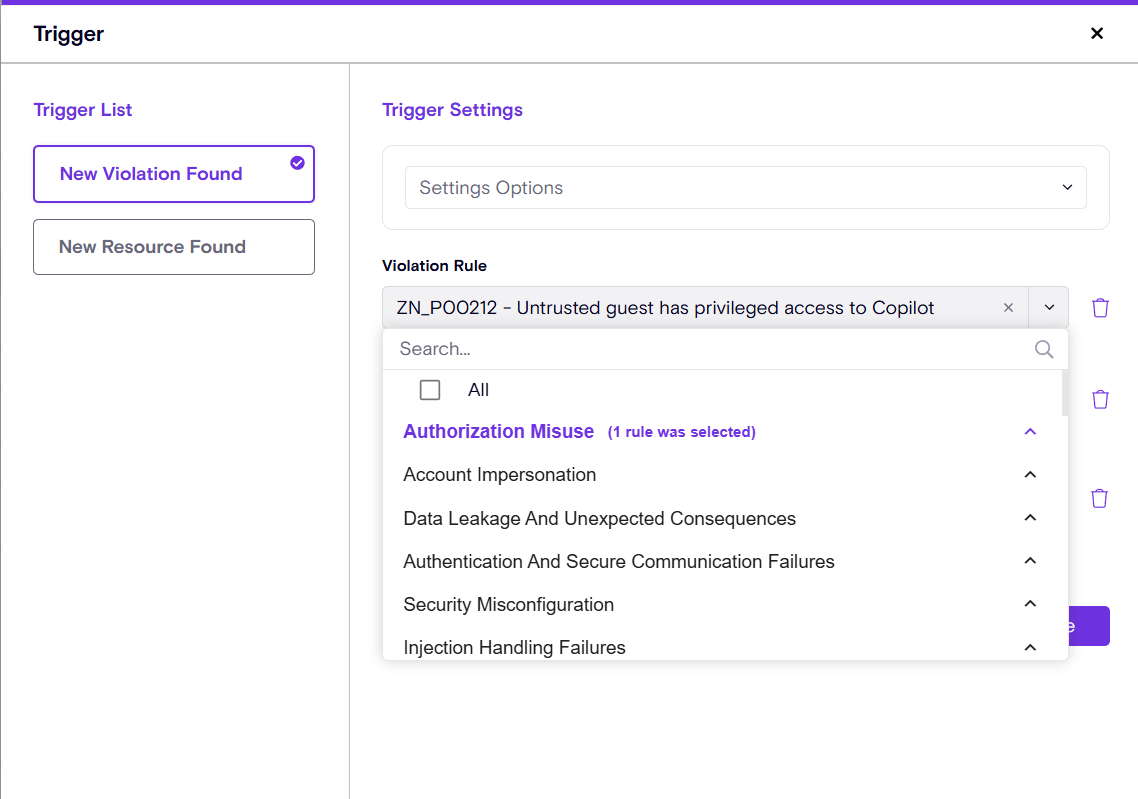
Better experience modifying playbooks
Zenity now supports a more intuitive way of viewing how the trigger was configured. Instead of trying to find the selected rules, they will be presented 1st, bolded with a clear indication of how many rules were selected.
Account reference
Under the user's profile, user can now view the specific account they are logged into.
New Violation Rules (a full description can be found in the Zenity policy page)
- ZN_P00168 - Flow is sending email to an untrusted domain
- ZN_P00170 - Power Page Site exposes sensitive data through its API
Zenity August-2024
⭐ Highlights
Enhanced AI-SPM Support for Copilot Studio & Copilot M365
Zenity continues to lead the way in securing Enterprise Copilots, expanding our platform to provide even greater visibility and risk assessment capabilities in this evolving space.
We’re excited to announce that our inventory now offers deeper insights into key Copilot components, enabling AppSec teams to have a more comprehensive understanding of how Copilots are created and configured, and how risky they may be.
Zenity now extends visibility to two critical resources within Copilot Studio (Custom Copilot Builder):
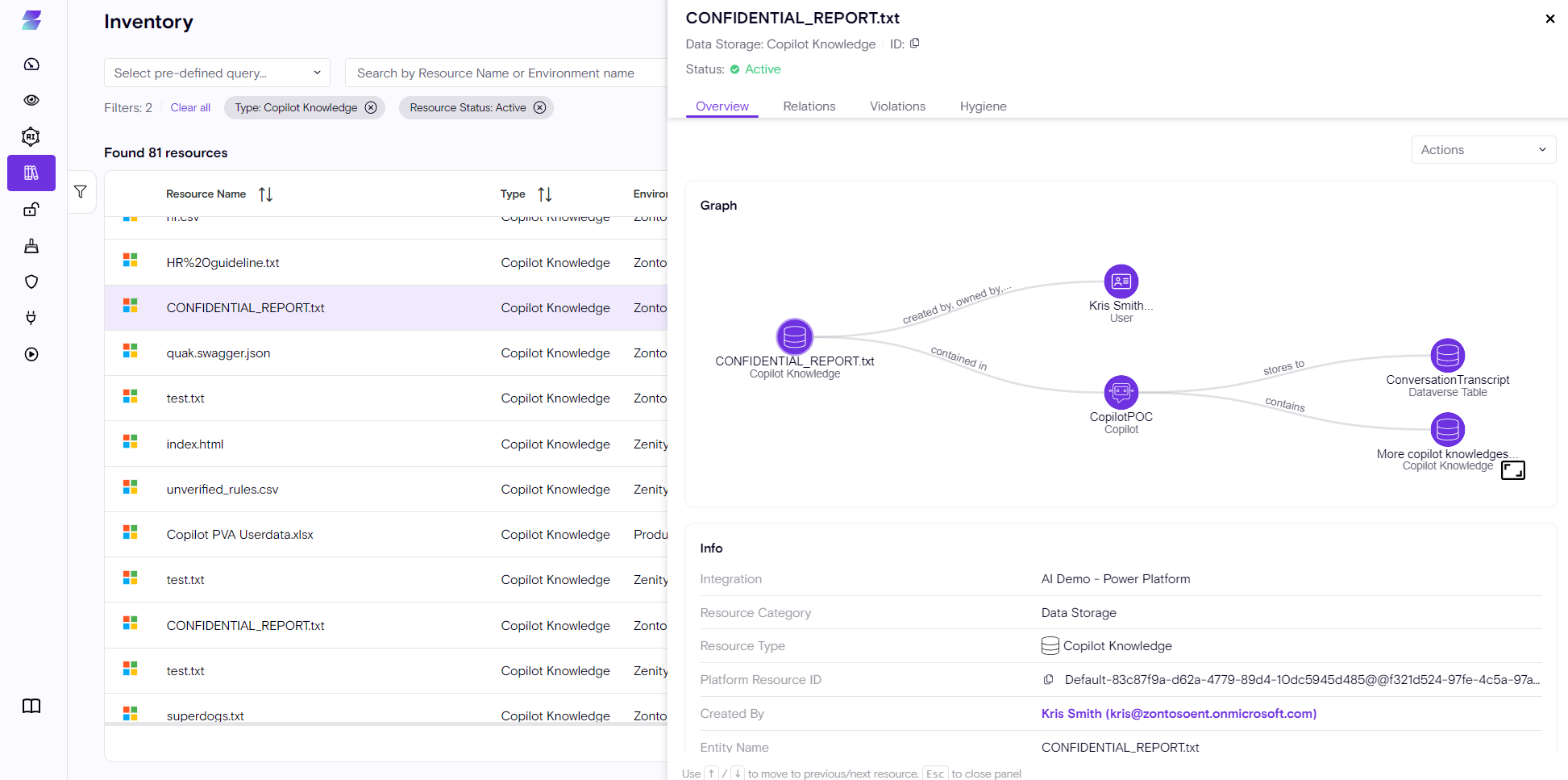
1. Copilot Knowledge
The Knowledge resource represents the 'Grounding' data on which the Copilot is using as context to assess user input.
This is crucial as it often involves the organization’s sensitive data, making it a key factor in the security assessment of custom Copilots.
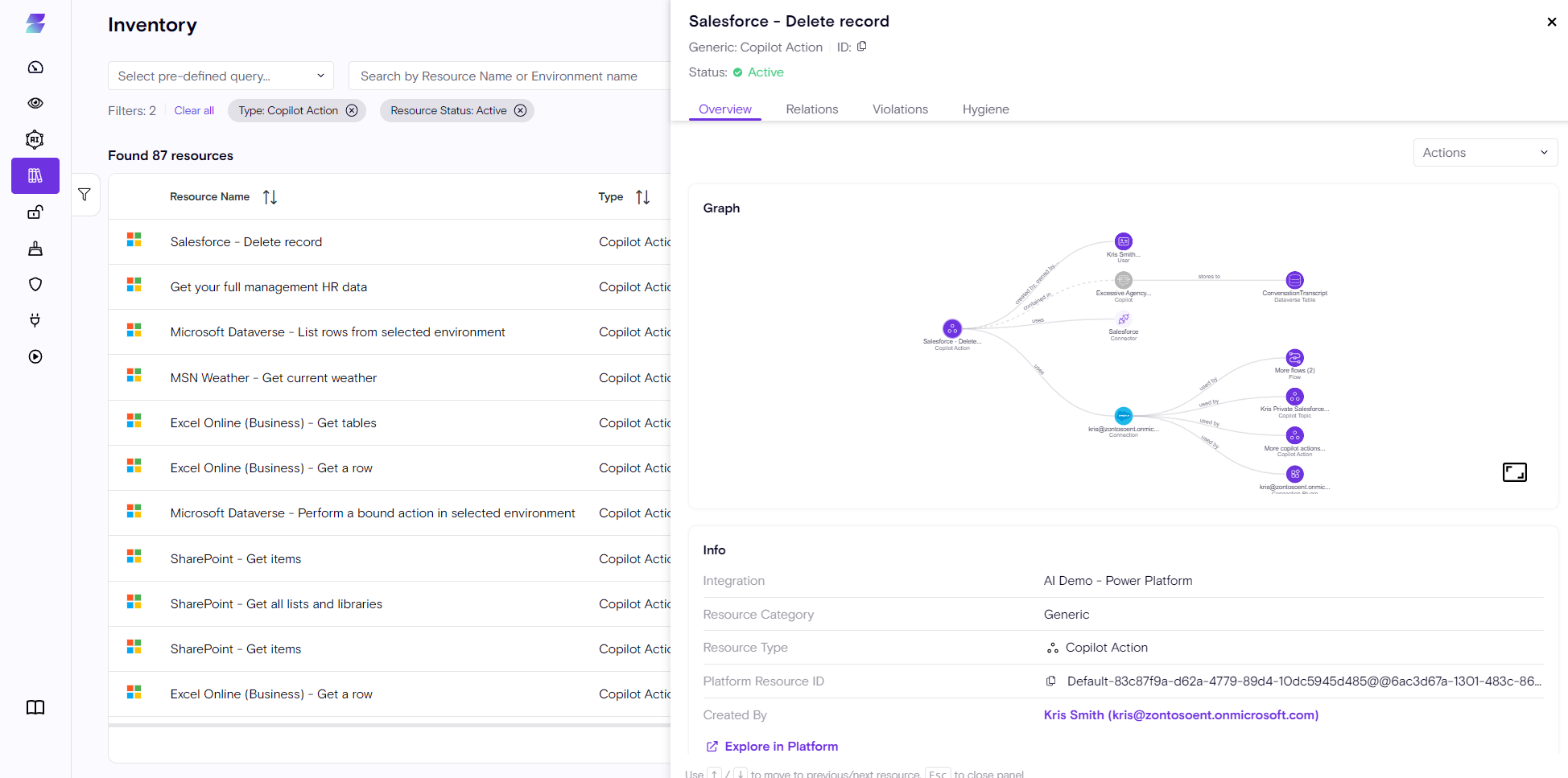
2. Copilot action
Actions refer to the execution capabilities of Custom Copilots, and can also extend the capabilities of Copilot M365.
.
These carry significant risk as they can be extended via Flows, executed without explicit consent, and potentially act on behalf of the user.
Both of these core resources are now fully integrated into our Inventory, with accompanying rules to help assess and mitigate associated risks.
Be sure to check out the 'New Violation Rules' section for a detailed overview of the latest security rules.
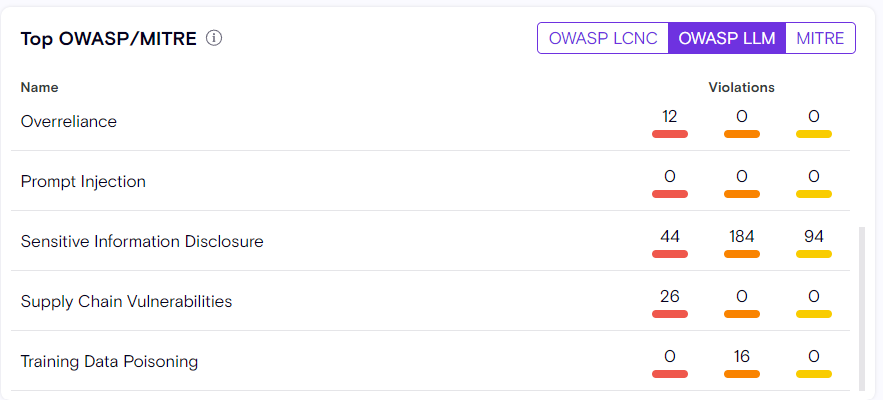
New Support for OWASP LLM Top10
We are excited to announce that Zenity is now incorporating a comprehensive mapping for Copilot Studio and Copilot for Power BI, aligning with the new OWASP Large Language Model (LLM) Security standard. This enhancement ensures that Zenity adheres to industry standards and best practices when it comes to securing AI-driven copilots.
The OWASP LLM Security Project provides a framework for identifying and mitigating the unique risks associated with large language models in enterprise environments. By integrating this mapping into Zenity, we not only provide visibility into potential vulnerabilities but also empower AppSec teams to assess these risks in accordance with established industry guidelines. This alignment enhances Zenity’s capability to deliver robust and secure solutions for enterprise copilots, offering our customers the confidence that their use of Enterprise Copilots is both safe and compliant with the latest security standards.
Enhanced Auditing in the Playbooks Execution History Table
Customers now have access to a more granular table, providing quicker insights into playbook executions. We've added 'Resource Name,' 'Environment Name,' and 'Owner' details for the resource or violation the playbook was triggered on. This enhancement will significantly reduce the time it takes to find these insights at the log level, making it easier and more efficient for users to pinpoint relevant data.
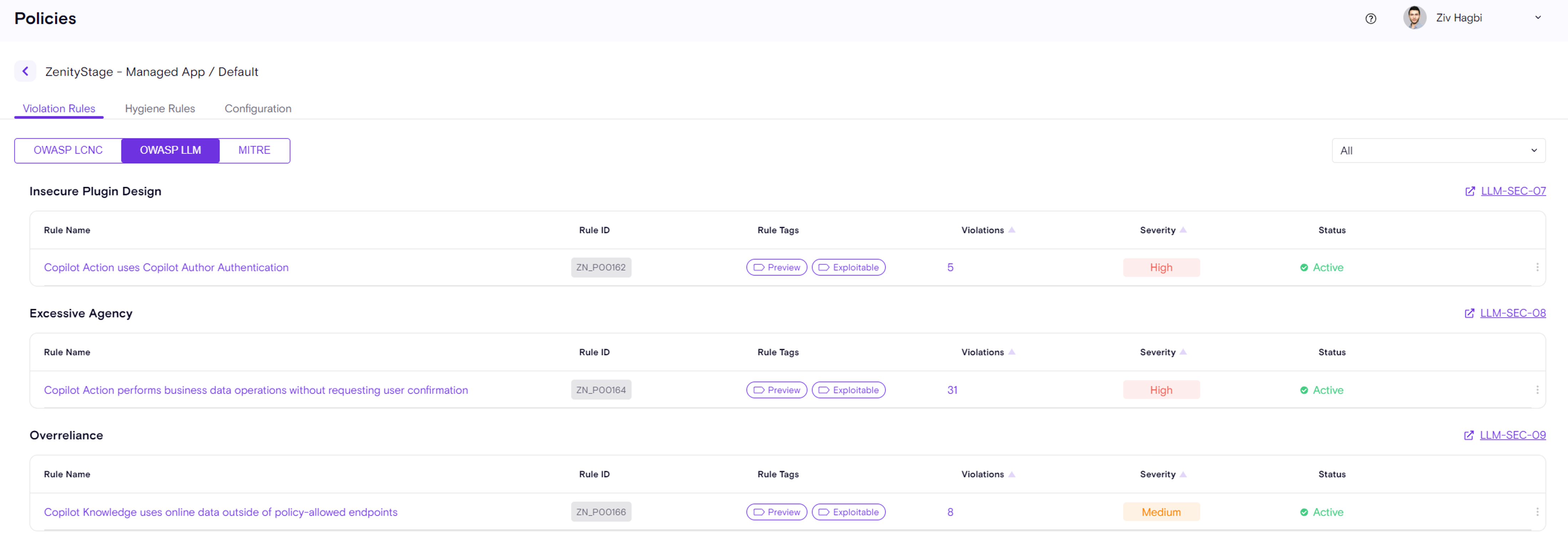
New Violation Rules (a full description can be found in the Zenity policy page)
Copilot Studio
- ZN_P00162 - Copilot Action uses Copilot Author Authentication
- ZN_P00163 - Copilot Action is susceptible to Prompt Injection via a flow
- ZN_P00164 - Copilot Action performs business data operations without requesting user confirmation
- ZN_P00165 - Copilot Action exposes business data to an unauthenticated chat
- ZN_P00166 - copilot knowledge uses data from disallowed endpoint
- ZN_P00167 - Copilot Knowledge exposes business data to an unauthenticated chat
Power Automate
- ZN_P00157 - Potential Injection Vulnerability in Power Automate Flow
Zenity is splitting the existing rule, ZN_P00070 - Potential IDOR Vulnerability in Flow, into two rules. One will focus on IDOR vulnerabilities, and the other on SQL injection scenarios.
In order to ensure there are no duplicate violations between the rules, the relevant IDOR violations focusing on SQL injection scenarios will be resolved and will be covered by the new SQL rule, currently in Preview.
How can you view which ones were resolved? easy, use this filter
As usual the new SQL Injection rule is in preview so there is no customer impact.
To learn more, watch the following video:
Important Update: Rule Updates
- ZN_P00017 - Connection is using a deprecated connector - now also supports the 'Microsoft Dataverse (legacy)' connector.
Microsoft has announced its deprecation and transition to the new 'Microsoft Dataverse' connector. Customers will be notified so they can transition accordingly.
Action item:
- Update all Apps/Flows/Copilots etc...using the deprecated connector to use the new and improve connector.
- Update any connections from the legacy connector to the new one (meaning, delete the old ones and create new ones to be used instead)
Important Update: feature Deprecation
Earlier this year, Zenity introduced the 'Created By Gen-AI' functionality, which identified all Apps/Flows created by Copilot.
After a thorough evaluation, we have decided to deprecate this feature due to the unreliability and inaccuracy of the PowerPlatform API in ensuring a high true-positive rate.
We will remove this feature from the platform by 10.2.2024.
No action is required from customers, except for those who have integrated the 'Gen-AI' filter into their playbooks—they should remove it ahead of time.
Important Update: Rules Deprecations
Zenity is committed to continuously improving our rule base and risk assessments. From time to time, we will deprecate rules, either to merge them with others or because they are no longer applicable due to platform changes.
Here is the list of rules we plan to deprecate on 09.04.2024:
- ZN_P00069 - Flow is potentially exposing sensitive data in logs
- ZN_P00013 - Flow is bridging business data and untrusted resources (high-risk connector)
- ZN_P00014 - Flow is bridging business data and untrusted resources (unmanaged endpoint connector)
- ZN_P00015 - Flow is bridging business data and untrusted resources (on-prem connector)
- ZN_P00036 - Flow is using communication and a high-risk connector
- ZN_P00037 - Flow is using communication and an unmanaged cloud endpoint
- ZN_P00038 - Flow is using on-prem and a high-risk connector
- ZN_P00039 - Flow is using on-prem and social media
- ZN_P00040 - Flow is using on-prem and unmanaged cloud endpoint
- ZN_P00041 - Flow is using business data and social media
The rules were deemed with a relativly high false-positive ratio and doesn't provide enough security value.
Important Update: Rules Deletion
Based on previous deprecation announcements, the following rule will be deleted on 09.15.2024:
-
ZN_P00121 - Flow run log contains potentially sensitive data (PHI - Protected Health Information) The rule is being deprecated to make room for a more advnaced rule
-
ZN_P00061 - Environment is recently created The rule is being deleted as it is not relevant anymore, as customers can get the same value via the both the Inventory and Playbooks.
Secure Flow Steps Update
Zenity can detect and encrypt sensitive steps within Power Automate flows using the 'Secure Flow Steps' action. For this action to work, two conditions must be met:
- The flow must be part of a solution.
- The solution must be un-managed.
This default behavior ensures that an 'un-managed' layer is not created in a managed solution.
No further action is required from the user.
Fabric Semantic Model enhancments
For Fabric customers, ensuring the freshness of their semantic models is essential—idle semantic models are candidates for removal. Zenity now provides visibility into the last refresh time of the semantic model. Please note, due to a restriction in the Fabric API, this data is limited to the last 7 days.
Zenity July-2024
⭐ Highlights
Introducing Our Advanced Support for Salesforce
Salesforce is the leading next-generation CRM platform, widely adopted by enterprise organizations. Over the years, it has evolved from a traditional CRM to a comprehensive Low-Code/No-Code and Enterprise AI platform.
Zenity extends its robust capabilities to Salesforce, offering comprehensive visibility, risk assessment, and governance for business application development. Our solution ensures that security and compliance are maintained, whether apps, automations, or copilots are being built by citizen developers or professional developers on the Salesforce platform.
To utilize Zenity's features for Salesforce, customers must create a new integration. Please ensure your Zenity license covers Salesforce by consulting with our customer success team. Without the appropriate license, the integration will not function properly.
Shadow Apps/Flows/Bots/Sites/Apex code and other resources are now a thing of the past as customers can view all of them within the Zenity Inventory.
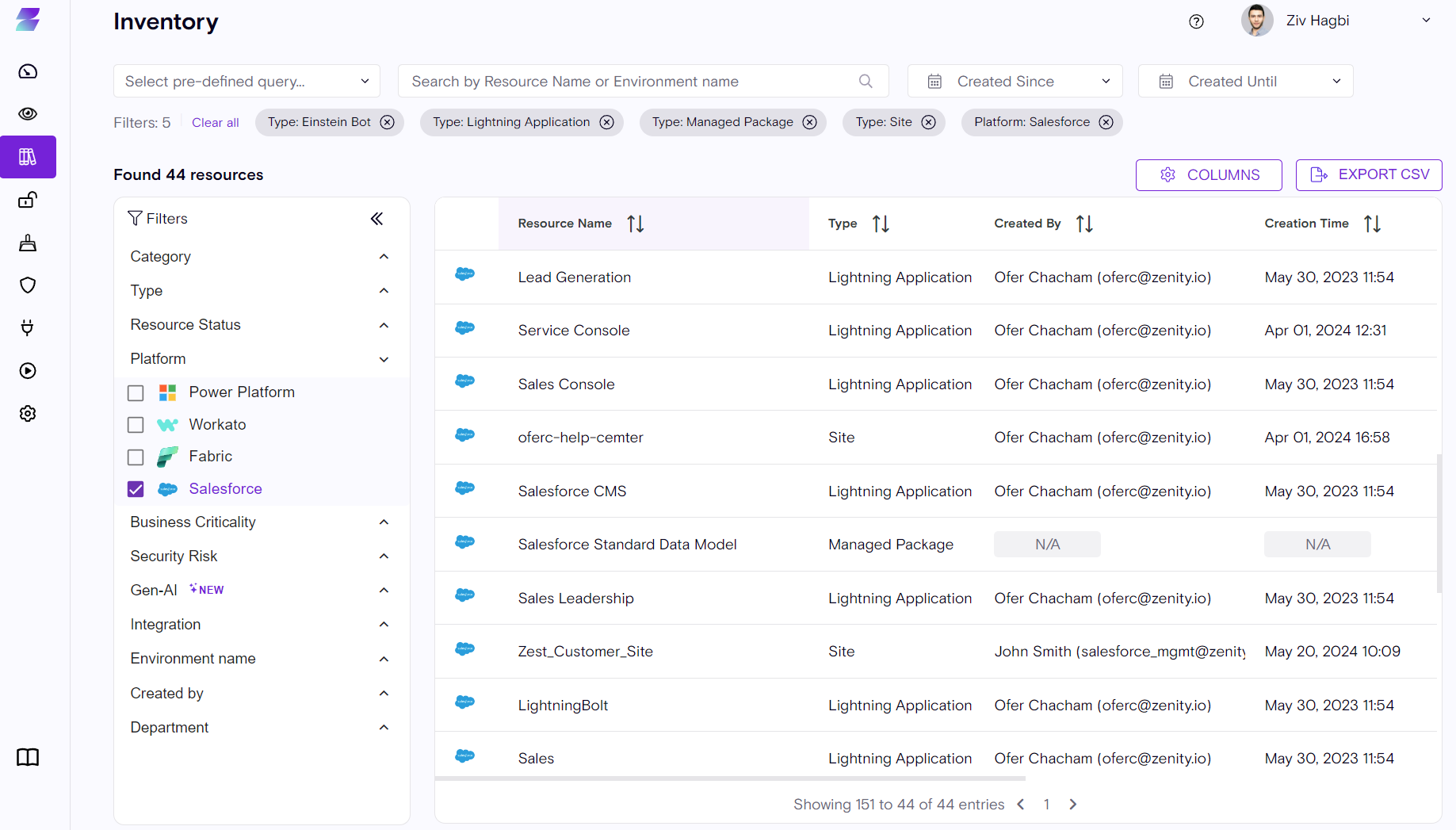
For the full list view the Salesforce User-Guide.
Zenity's core strength is our ability to identify critical risks.
Zenity detects various risk scenarios for Salesforce, including:
-
External User Access
-
Suspicious Endpoints communication
-
Privileged role abuse
-
Sensitive Information exposure (credentials)
-
Injection vulnerabilities
-
Privilege Escalation Paths
-
Permissions Validation Issues
-
Organization wide access
-
Authentication issues / Anonymous access
-
Resource Oversharing
-
Data Leakage
-
Security Configuration issues
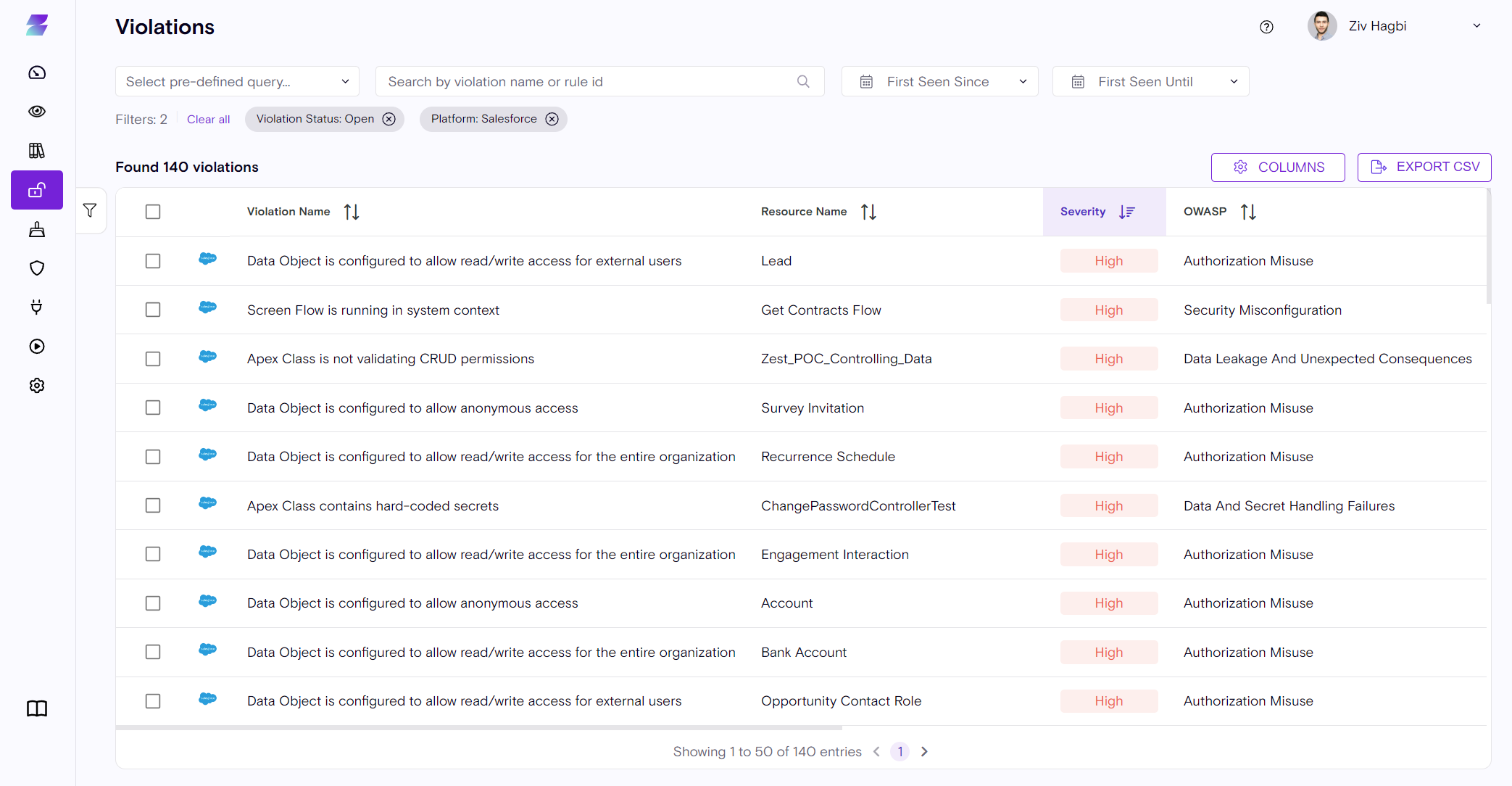
For the full list view the Zenity Policy page.
Orchstrations
Alongside Salesforce Visibility, customers can now start integrating Zenity's violation detections into their existing processes. Zenity provides out-of-the-box playbooks to facilitate orchestrating the remediation process with the relevant users. This can be done via Webhook (HTTP callout to integrate with other platforms) or Email.
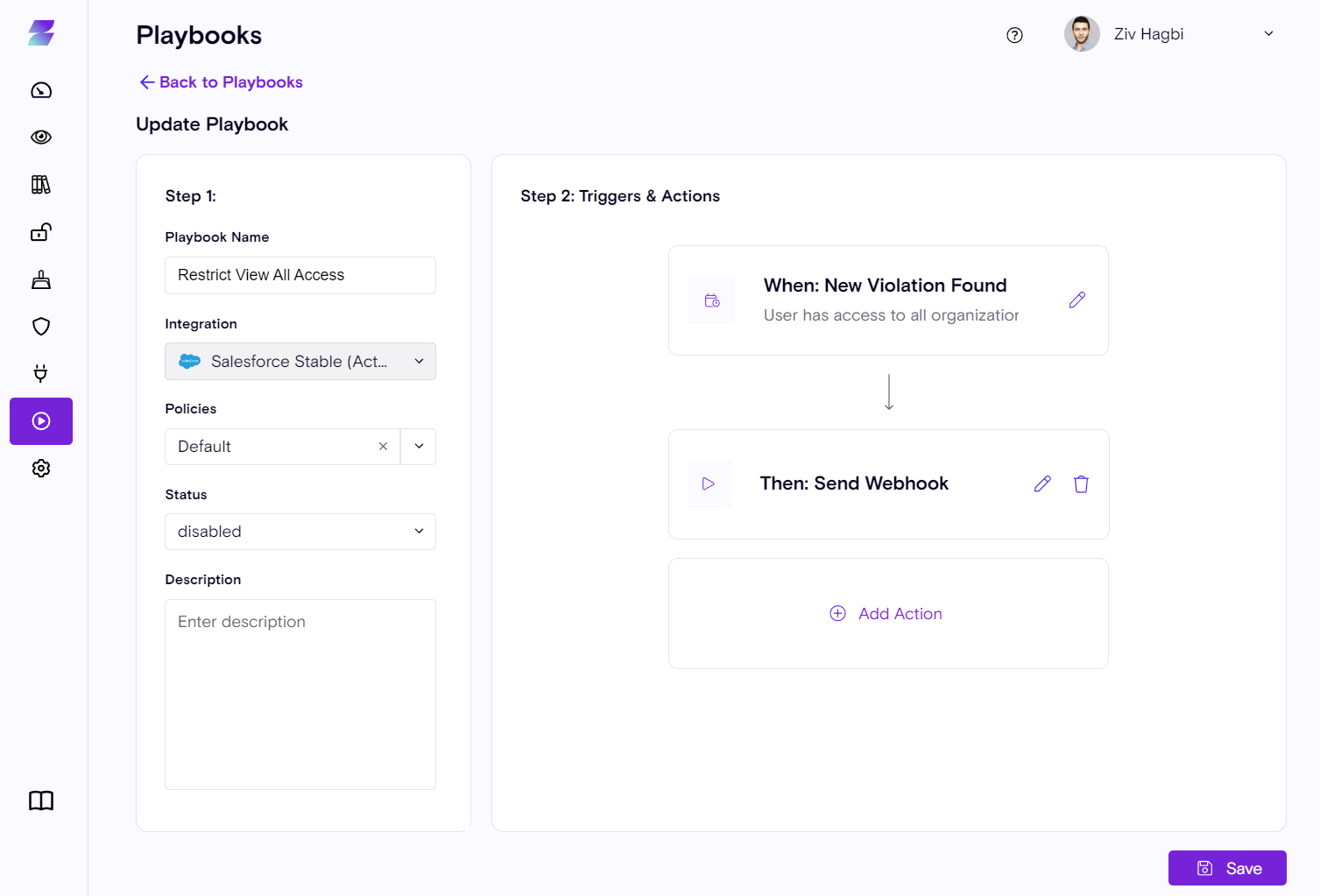
New Violation Rules (a full description can be found in the Zenity policy page)
PowerPlatform
- ZN_P00125 - Canvas App implicitly shares a connection
- ZN_P00159 - Flow exposes business data to anonymous users
- ZN_P00160 - Flow exposes business data to the entire tenant
Salesforce
- ZN_S00001 - User has access to all organization records
- ZN_S00002 - Screen Flow is running in system context
- ZN_S00003 - A non system administrator user with permission to view encrypted data
- ZN_S00004 - Apex Class contains hard-coded secrets
- ZN_S00005 - Non-compliant setting: Enable clickjack protection for customer Visualforce pages with headers disabled
- ZN_S00006 - Non-compliant setting: Enable clickjack protection for customer Visualforce pages with standard headers
- ZN_S00007 - Non-compliant setting: Enable clickjack protection for non-Setup Salesforce pages
- ZN_S00008 - Non-compliant setting: Enable clickjack protection for Setup pages
- ZN_S00009 - Non-compliant setting: Enable CSRF protection on GET requests on non-setup pages
- ZN_S00010 - Non-compliant setting: Enable CSRF protection on POST requests on non-setup pages
- ZN_S00012 - Non-compliant setting: Let users verify their identity by text (SMS)
- ZN_S00013 - Non-compliant setting: Lock sessions to the domain in which they were first used
- ZN_S00014 - Non-compliant setting: Maximum invalid login attempts
- ZN_S00016 - Non-compliant setting: Security risk file types with Hybrid behavior
- ZN_S00017 - Non-compliant setting: Require HttpOnly attribute
- ZN_S00044 - Apex Class is using inherited sharing
- ZN_S00045 - Apex Class is running in system context
- ZN_S00046 - Data Object is configured to allow anonymous access
- ZN_S00047 - Data Object is configured to allow read/write access for external users
- ZN_S00048 - Data Object is configured to allow read access for external users
- ZN_S00049 - Data Object is configured to allow read/write access for the entire organization
- ZN_S00050 - Data Object is configured to allow read access for the entire organization
- ZN_S00051 - Flow is sending email to an untrusted domain
- ZN_S00052 - User without MFA
- ZN_S00053 - Admin without MFA
- ZN_S00056 - Managed Package is using a remote site on a disallowed endpoint
- ZN_S00057 - Managed Package is using a remote site with insecure communication
- ZN_S00070 - Apex Class is using bad crypto
- ZN_S00071 - Apex Class is not validating CRUD permissions
- ZN_S00072 - Apex Class is executing a dangerous command
- ZN_S00073 - Apex Class is using an insecure endpoint with setEndpoint()
- ZN_S00074 - Apex Class is using an unsafe open redirect
- ZN_S00075 - Apex Class is using DML without explicit sharing mode
- ZN_S00076 - Apex Class is vulnerable to SOQL Injection
- ZN_S00077 - Apex Class is using hardcoded credentials with setHeader()
- ZN_S00078 - Apex Class is using error messages with disabled escaping
- ZN_S00079 - Apex Class is using unescaped or unsanitized URL parameters
- ZN_S00080 - Apex Class is using an insecure URL
- ZN_S00081 - Apex Class is using a disallowed endpoint
- ZN_S00082 - System Administrator is inactive
- ZN_S00083 - Apex Class can lead to privilege escalation
A full description can be found in the Zenity policy page)
Important Update: Rules Deprecations
Zenity is always working on enhancing and improving our rule base and risk assessment.
As such, from time to time, we will deprecate rules, either to merge them with others or if they are no longer applicable due to changes in the platform.
Here is the list of rules that we are planning to deprecate by 08.14.2024:
- ZN_P00121 - Flow run log contains potentially sensitive data (PHI - Protected Health Information) The rule is being deprecated to make room for a more advnaced rule
Misc**
Advanced Playbook Filtering
Customers are heavily using Zenity's automation engine, "Playbooks."
One of the key methods of tracking violations and classifying them is through Labels.
Now, customers can label violations and exclude or include them in our playbooks. For example, a customer can label a certain violation as FP and exclude it from the playbook, ensuring it won't be processed.
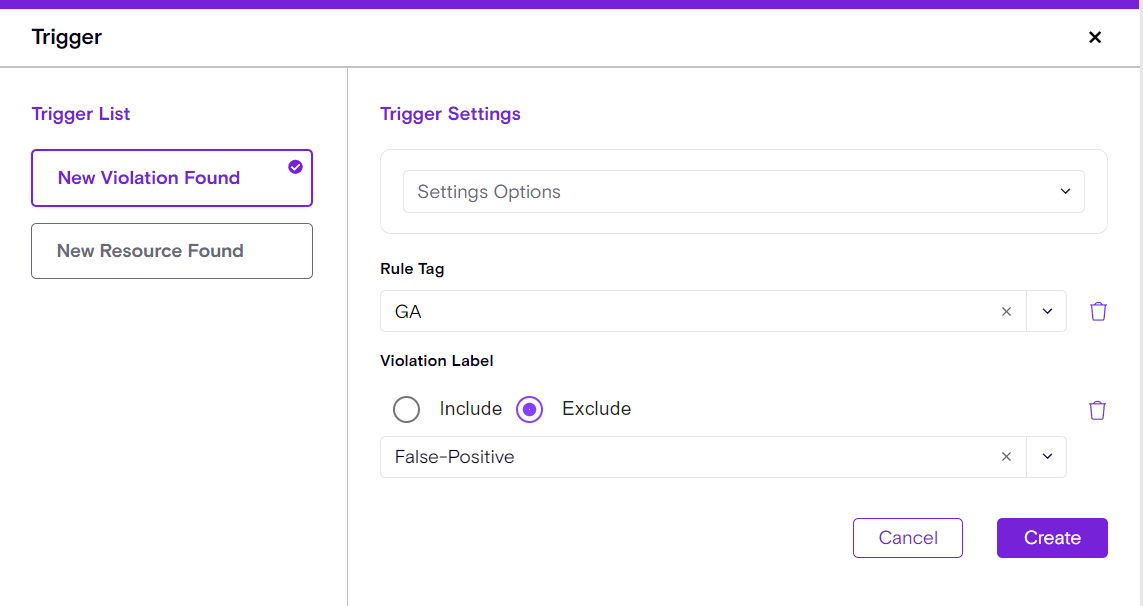
Secure Flow Steps Update
Zenity has the ability to detect and encrypt sensitive steps in Power Automate flows. This is done via the 'Secure Flow Steps' action.
In order for this action to work, two conditions should be met.
- The flow must in a solution
- The solution should be un-managed.
This is the default behavior to avoid creating an 'un-managed' layer in a managed solution.
Zenity April-2024
⭐ Highlights
Violation Rule Configuration Mapping
Zenity provides dozens of security violation rules. Many of them have out-of-the-box settings that users can customize to achieve a more granular control of their security posture.
However, customer always had a challenge knowing which settings impacts which rules. So, in case they want to alter a certain config, how would they asses the impact?
Now, Zenity introduces the Rule Configuration Mapping in-product, allowing users to understand which settings impact which rules.
General
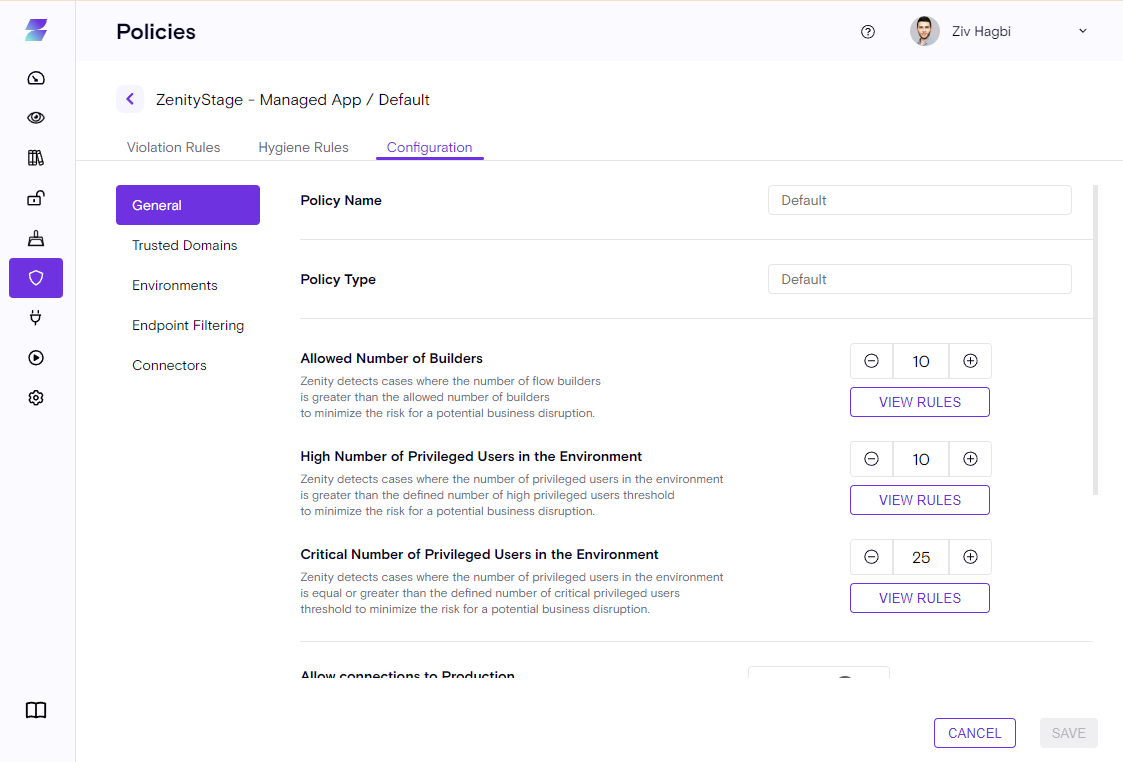
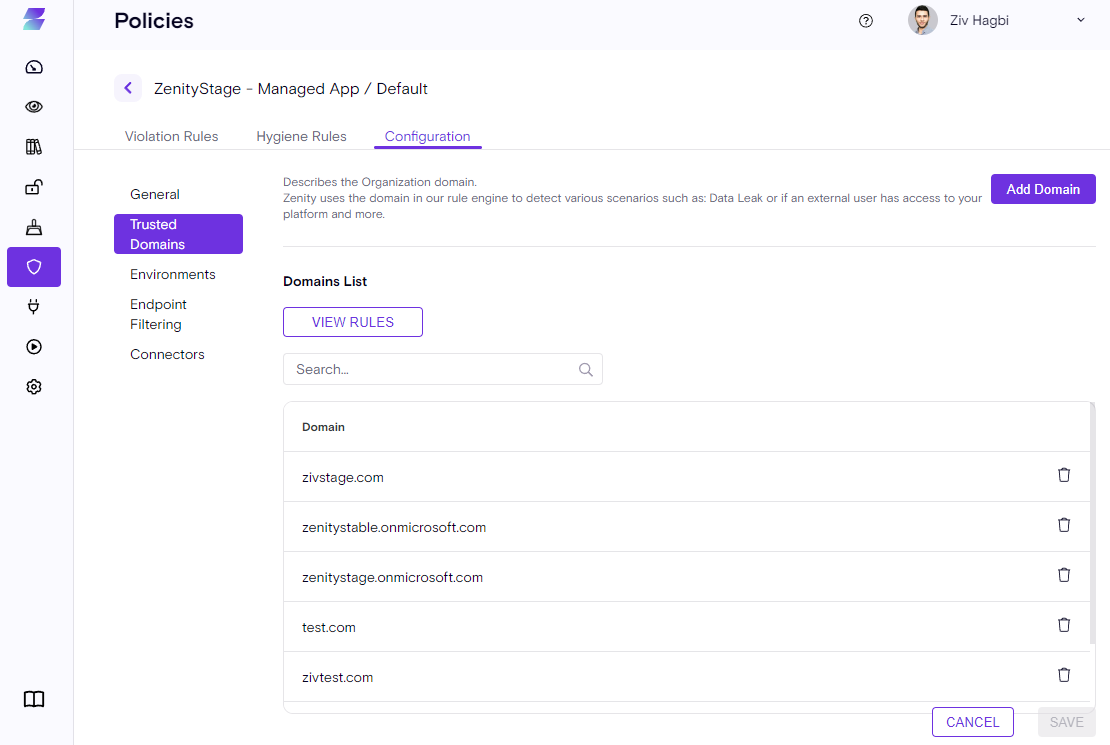
Trusted Domains
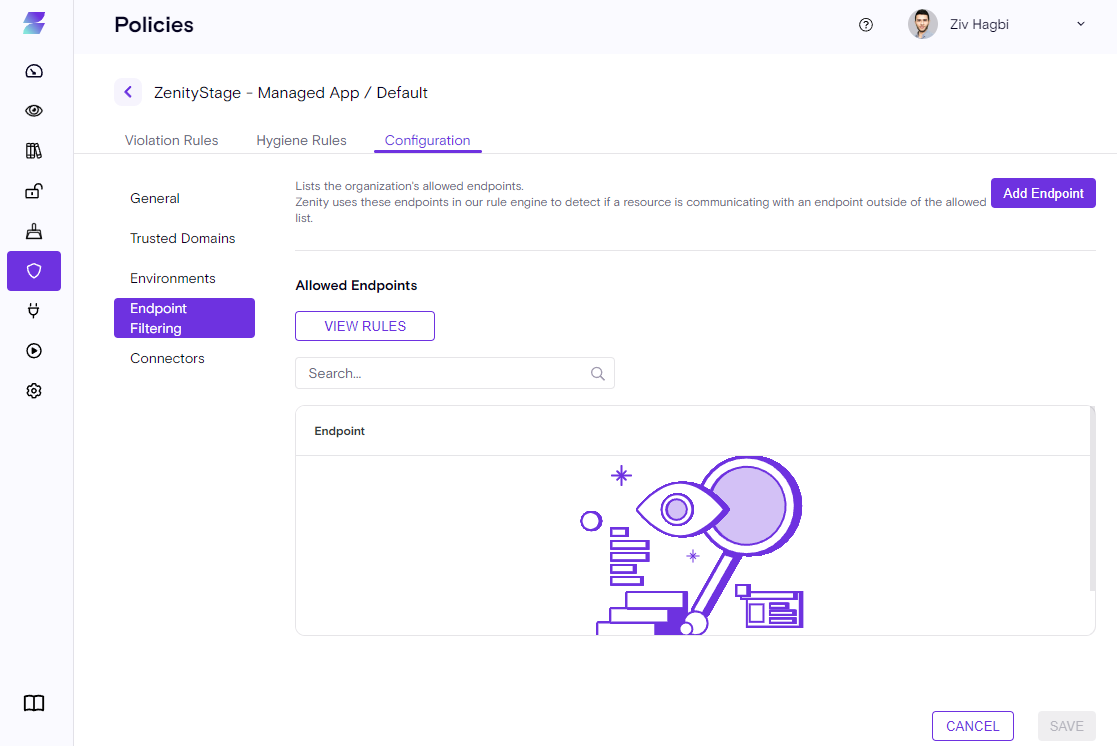
Endpoint Filtering
Drill-Down
Remove Access Improvements
Zenity has introduced the 'Remove Access' action in our playbooks to automate risk burndown of suspicious access issues, like Guest sharing and Tenant wide access. Based on customer feedback we've made improvements to the action, making it more clear and simple for user to use.
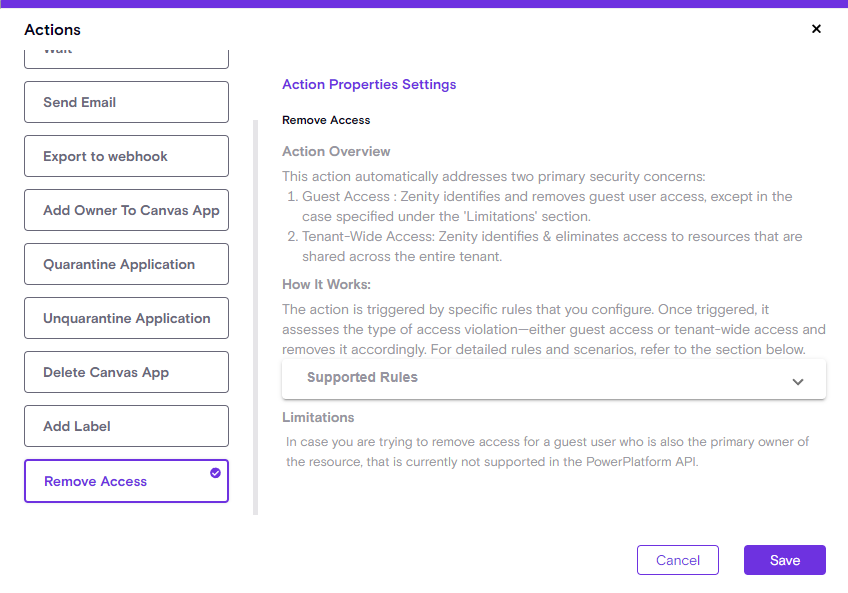
Now Zenity users can easily understand the purpose of the action, coverage and limitation.
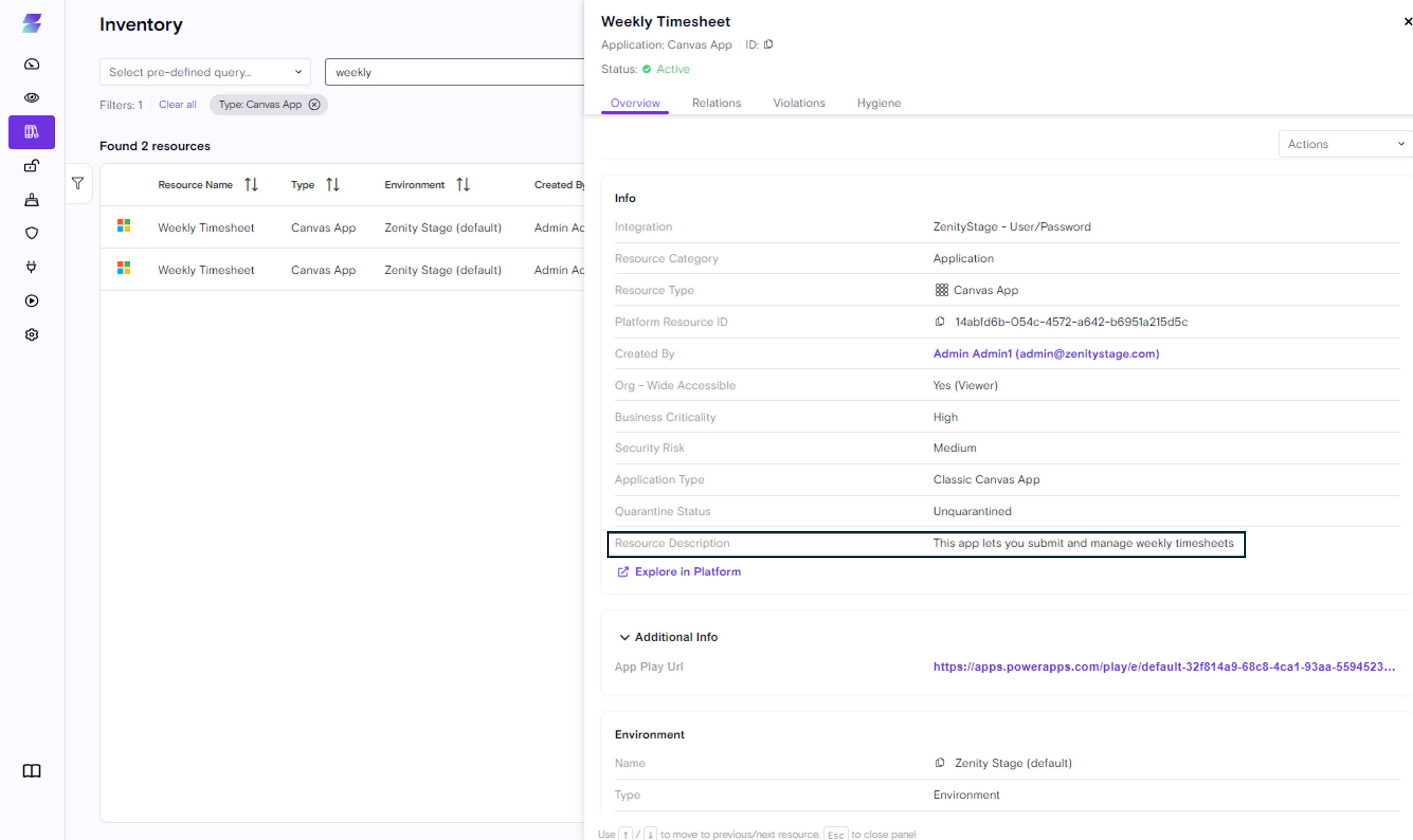
App / Flow Description
Citizen developers many times add custom description to their resources, articulating the purpose of the App/Flow. That Information can be useful when trying to answer the question "What does this App/Flow do?"
For any App/Flow that has this description it will now be shown in Zenity.
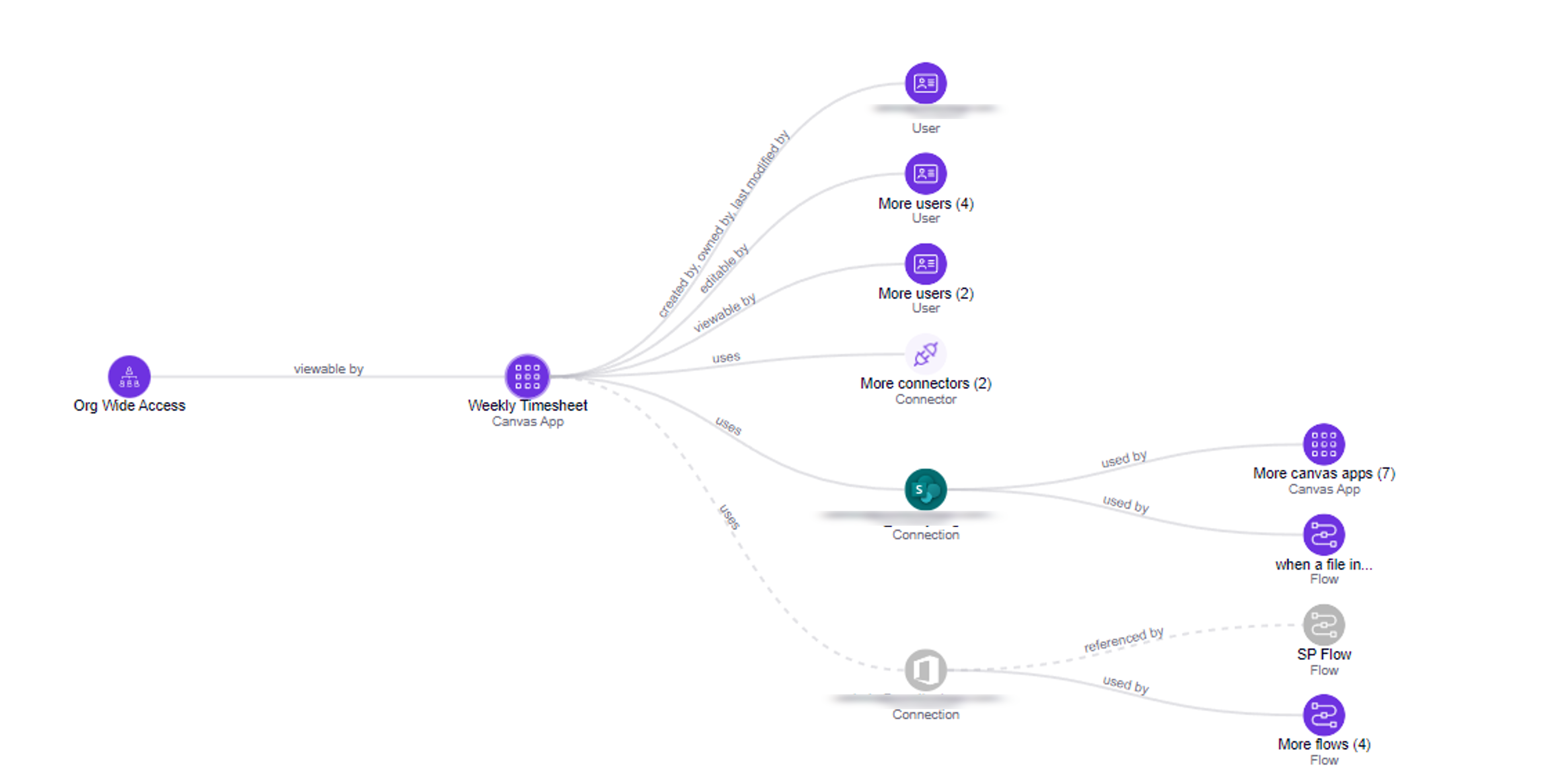
Graph improvements
The Zenity Attack Graph provides many benefits, for example: - Providing risk context - Allowing to assess impact - Streamlining investigation efforts and much more....
While the Graph provides a lot of value, it could be challenging to understand all of the nodes of how they affect each other.
For ease of use and explainability we now added the 'Resource Type' for any resource on the graph in addition to its name. So in case a customer is looking at a resource called "Employee Onboarding" he can easily know if it's an Canvas App or an Flow or anything else.
Custom Connector
Zenity customers world-wide are building amazing risk burndown processes on top of Zenity's data using our automation capabilities.
Zenity aims to simplify this process and provides a lot of out-of-the-box value to all of our customers.
Many of the customers are using the Zenity's API to extend zenity's capabilities into their own security eco-system. Connecting Zenity to SIEM, SOAR and LCNC automation platforms.
For that reason, we decided to go the extra step and create a "Zenity Connector" for PowerPlatform which elevates our API layer to the LCNC space for everyone to use easily.
Now, users can use the custom connector to build complex automation using our API, for example, getting violations at will or invoking different remediation actions like Quarantine an App.
Use this link to get started.
Zenity Mar-2024
⭐ Highlights
Automatic Removal of Guest Access
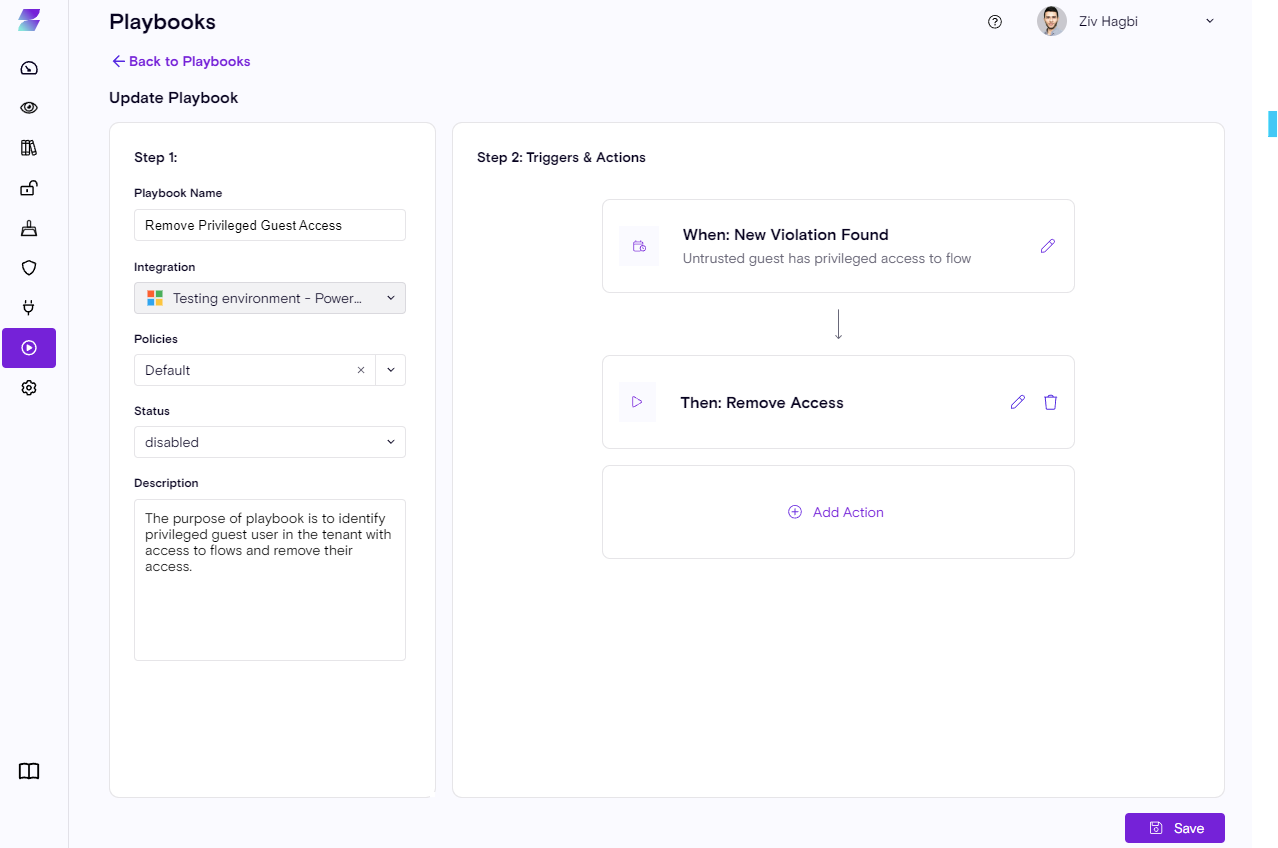
In Power-Platform, sharing your work is very common, it could be a flow or a Canvas apps and other resources. Sharing has risk by definition, as other identities have access to your data. This is especially risky when the shred identity is a guest user.
Zenity can identify cases where suspicious guest users have access to the company’s resources.
Whether it's privileged or non-privileged Zenity allows AppSec teams to create automatic remediation flows to mitigate the risk.
Through the Zenity’s Playbook engine security teams can easily detect and remove access thus mitigating the risk.
Based on the trigger configuration, the action will remove the suspicious guest user.
Automatic Removal of Tenant-Wide Access
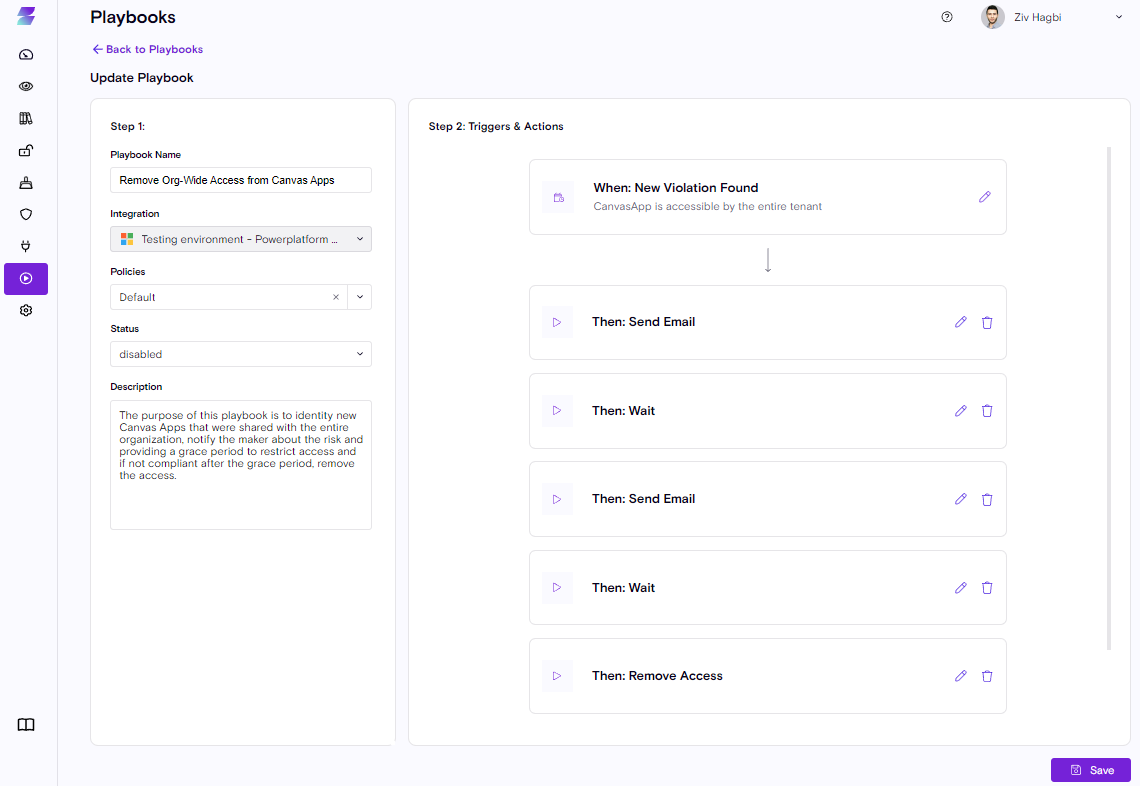
In Power-Platform it's very common to share a Canvas Apps or a Connection with everyone.
This is very simple for the average business user and of course contradicts the least privilege principle.
Zenity can identify cases where Canvas Apps or Connections are accessible by the entire tenant.
Sharing a data connection or a canvas app with the entire tenant (including guests) poses a big risk as now everyone has access to the data.
Through Zenity’s Playbook engine security teams can easily detect tenant wide access & remove it, mitigating the risk.
Expose Resource Ownership
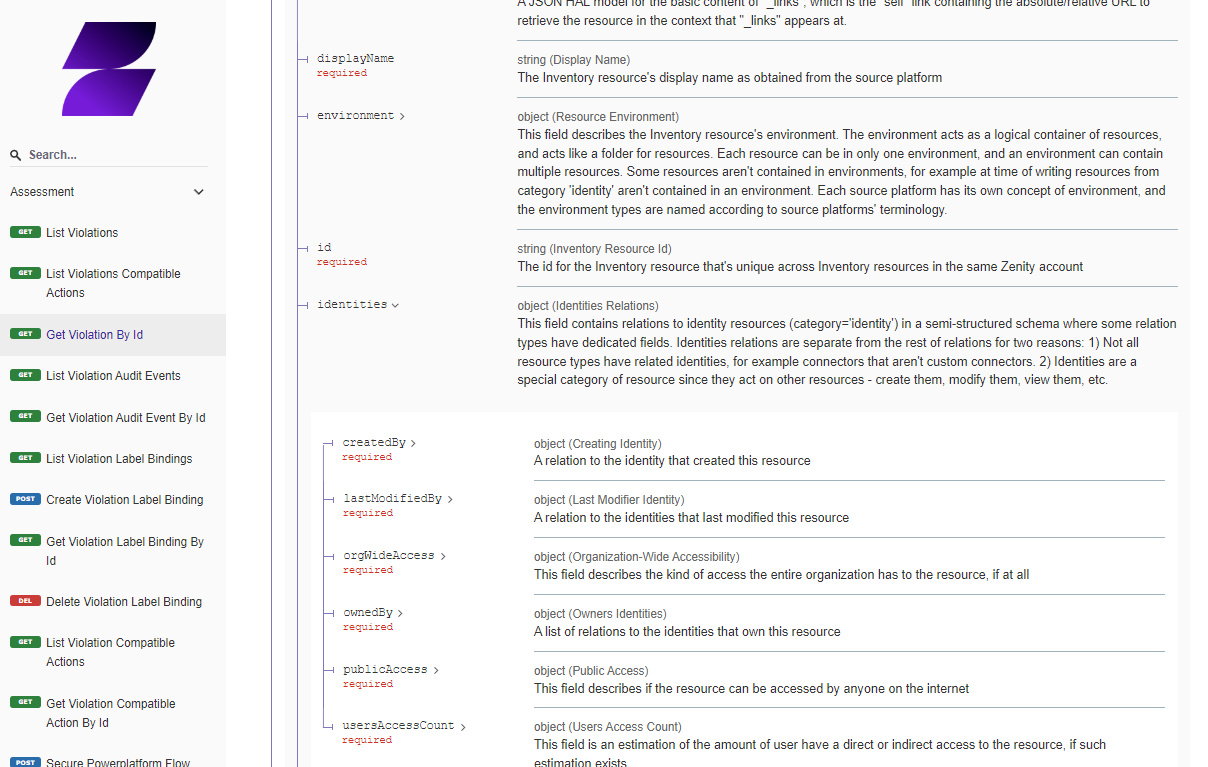
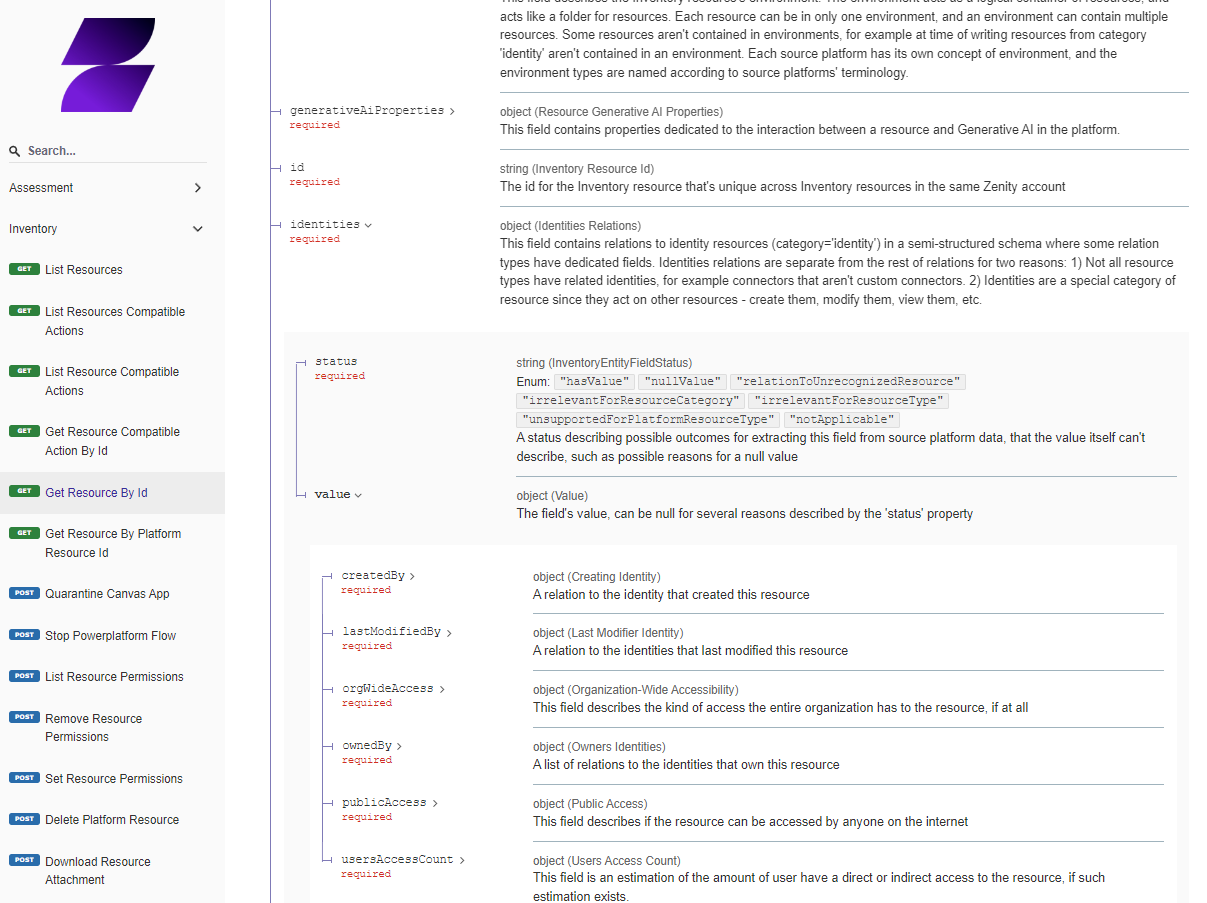
Zenity identifies the relevant end-user within the LCNC platform that is responsible for fixing a violation.
Security teams use this information to know who they should contact, especially when performing automatic risk burndown at scale.
Until today, it was hard to find the 'Owner' of a resource and in many cases, customers used the 'Creator' as the best reference.
However, the creator is not always the best match, as he could leave the company, role etc. Rendering the automation useless.
Now, Zenity has surfaced in our data model the actual Owner of a resource and customers can use it as a 1st point of reference.
It's now available via the API and will later be available in the UI.
Resolved Violations Reasons
In Zenity violations go through a life-cycle, from Open to Resolved. Knowing why violations were resolved is critical to understand the overall risk.
In the effort of making that crystal clear, Zenity introduces the 'Violation Status Reasons'. This feature provides a deeper and granular approach to understand why a violation was resolved.
It splits, actual 'Fixed' from 'Resource Deleted', 'Policy Update' & 'Rule update', allowing our users to focus on what matters most.
For ease of use, they are also available via filters.
Replace Owner for Canvas Apps
In Power Platform, there is a restriction when trying to remove the original owner of a Canvas app. This was simply not supported.
This is of course an issue as sometimes Security teams might want to revoke his access, for example a suspicious guest user who has built an App processing sensitive data.
In a recent API update, this was changed and now Zenity provides the ability to Replace the primary owner.
By default, the Primary owner will be downgraded to a 'read-only' user, allowing for his full removal.
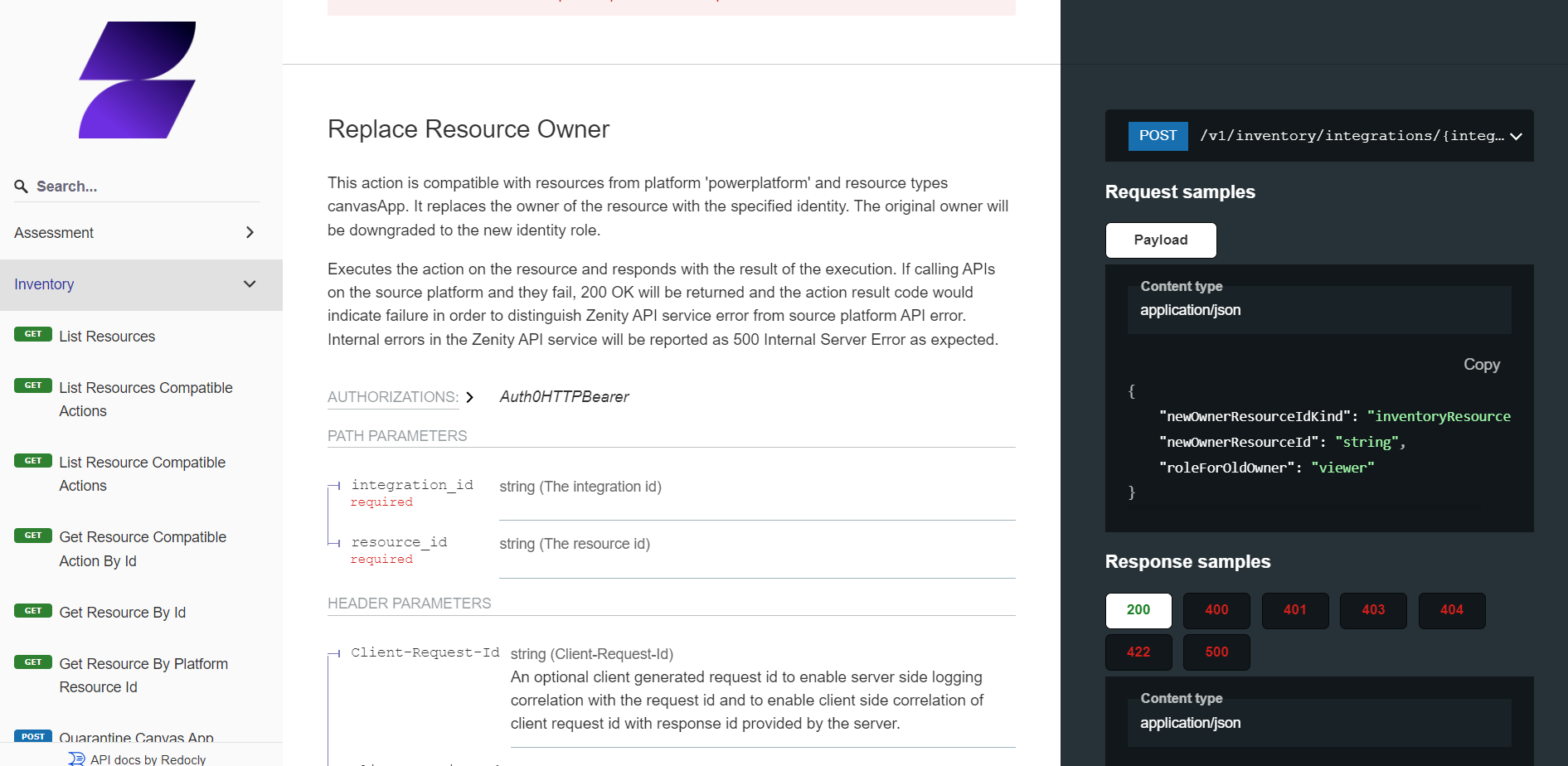
It's now available via the API and will later be available in the UI.
'Send Email' action enhancment
Customers are using Zenity to contact the end-users responsible for fixing the violations.
There was a gap in the 'Send Email' action (manual action) that didn't support the 'Contact Maker' like what is supported through Playbooks.
This caused frustration as the user had to copy the maker's email every time, now it's automatic.
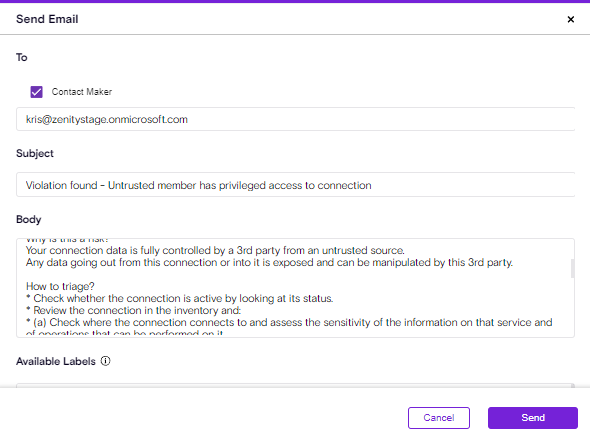
In addition, customers could not use the variables acting as placeholders, like what is supported through Playbooks. This caused an issue as the existing custom email templates used in our playbooks did not work.
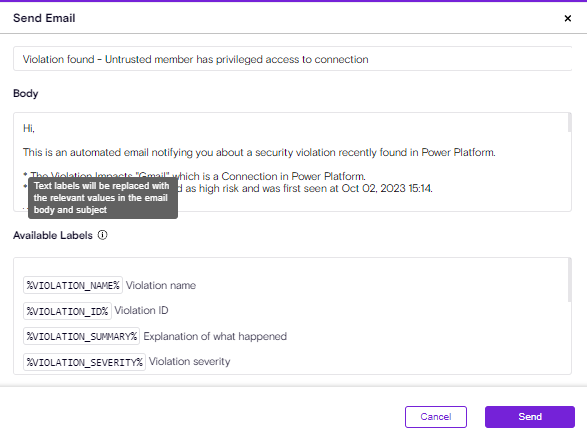
Both gaps were bridged and are now fully functional.
Zenity Feb-2024
⭐ Highlights
Rule Tags
Zenity has many rules and the number keeps on growing and it's hard for our customers to keep track of their purpose and their life-cycle. For that we decided to add tagging (Zenity controlled) metadata to allow our customers to easily comprehend the context around the rule.
This is a growing effort but for now, to understand the life-cycle of the rule users have the 'Preview', 'GA' and 'Deprecated' tags. In addition, we added the 'exploitable' tag that lets our customer know that certain rules are identifying scenarios where a path to exploit exists.
This is more than just tagging; it allows them to understand where they should expect accuracy and where items are still in work.
In addition, Zenity users can filter using the new 'Rule Tag' filter to find only relevant violations.
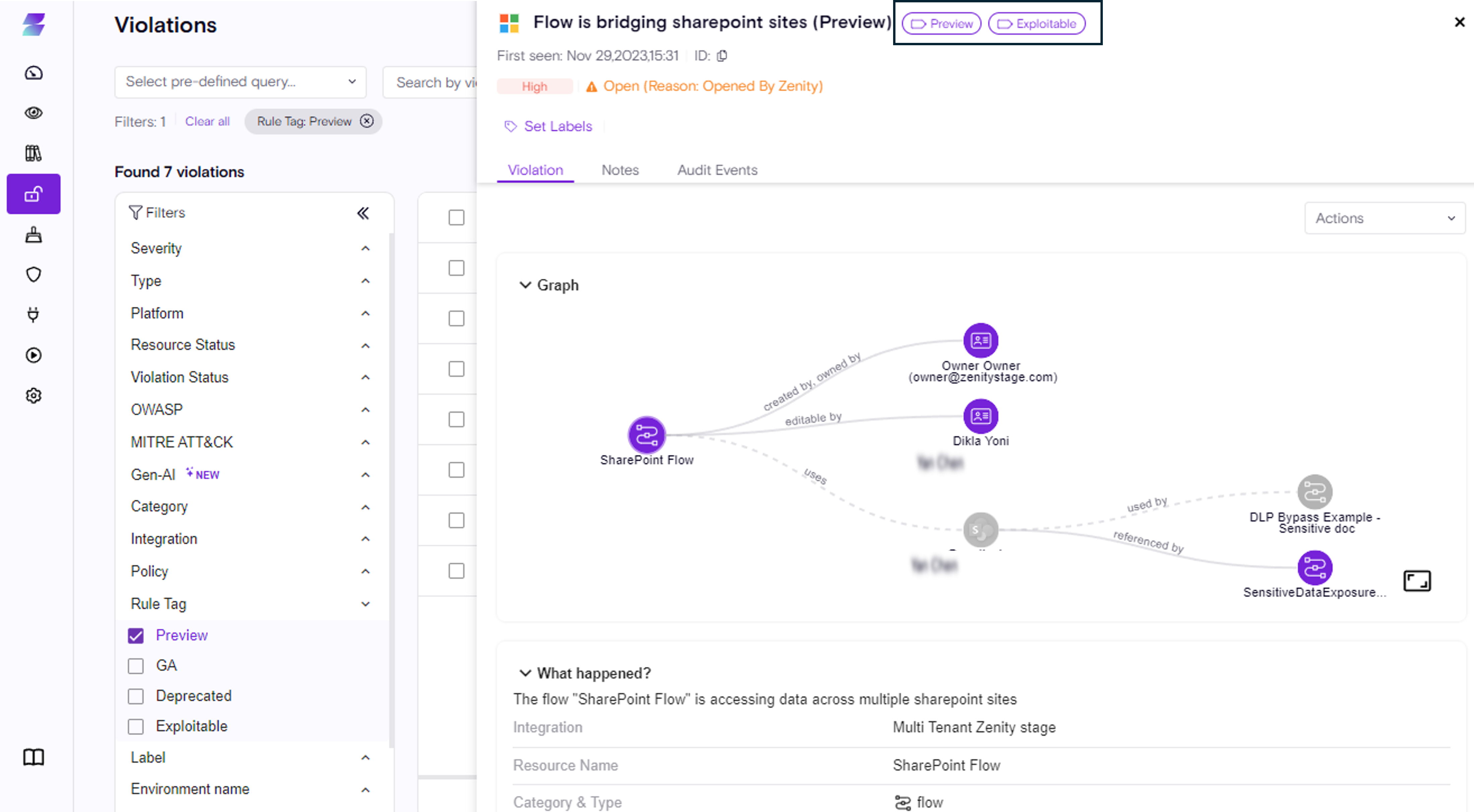
Playbooks also run on GA rules by default.
Scan Freshness
Customer needs constent scan visibility to make sure their data is fresh and is up to date.
This comes is critical for every customer, especially customers that rely on the freshness for their remediation process.
Now, users can view the last scan time across the board for every violation (available also via the API)
Cross Environment/Region Data Flow
PowerPlatform has recently added the ability for Power Automate flows to push/pull data between different environments. This ability was available in the past using a method that they have deprecated but is not available again and is even more robust.
Now business users can easily break the barrier between environments, potentially resulting in Data leakage and Compliance issues.
Use-Cases: A business user can pull sensitive data from a Production Environment and sync it with a less sensitive environment, for example the Default one. A business user can move sensitive data between data regions for example moving data from US/EU to Asia breaking compliance.
Here is an example of how this looks from a PP user's perspective.
In this example, data is pulled from a production environment into a personal productivity environment accessible to all users.
Zenity can identify these cases and flag them as risky. Here is an example of how Zenity would flag this risk.
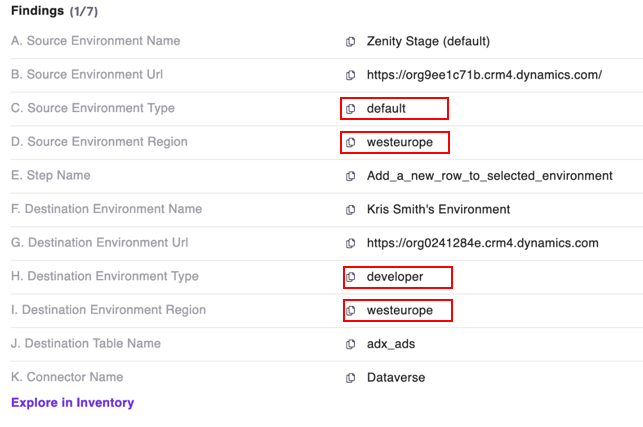
New Violation Rules (a full description can be found in the Zenity policy page)
- ZN_P00147 - Copilot is consuming uploaded files with potentially sensitive data (PCI - Payment Card Industry)
- ZN_P00148 - Copilot is consuming uploaded files with potentially sensitive data (PHI - Protected Health Information)
- ZN_P00149 - Copilot is consuming uploaded files with potentially sensitive data (PII - Personally Identifiable Information)
Important Update: Rules Deprecations
Zenity is always working on enhancing and improving our rule based and risk assessment as such from time to time we will deprecate rules, either to merge them with others or if they are no longer applicable due to changes in the platform.
Here is the list of rules that we are planning to deprecate by 4.2.2024.
- ZN_P000132 -
- ZN_P00116 - Gateway is unpatched and vulnerable
In case you have existing playbooks or other automation using these rules, please replace them with the relevant rules below.
For any question, please contact zenity through your dedicated customer support or open a ticket to support.
Important Update: Filter deprecation
In order to facilitae a more robust and production grade experience, some of the filters available in the dashboard are going to be deprecated. This is done after examining the usage of those filter and ROI they provide to customers.
The relevant filters are:
- Resource Status
- Environment
Both will be deprecated only from the Main Dashboard and the Visibility dashboard, they will continue to work it all other areas of the product.
Zenity Jan-2024
⭐ Highlights
Ensure compliance with Zenity Audits Events
Customer have asked us many times, how can we know what happened to a violation?
How can we track who did what to handle & Process it?
For example, when If it was exempted (when, who and why) or a certain label was added or removed.
Zenity now introducing the violation 'Audit Events'.
The audit events tell the life-cycle story for each violation.
Customers can view the audit and see when a violation changed its status (why, when and by whom, including a clear description). Zenity also tracks all labels that were added or removed (Why, When and whom).
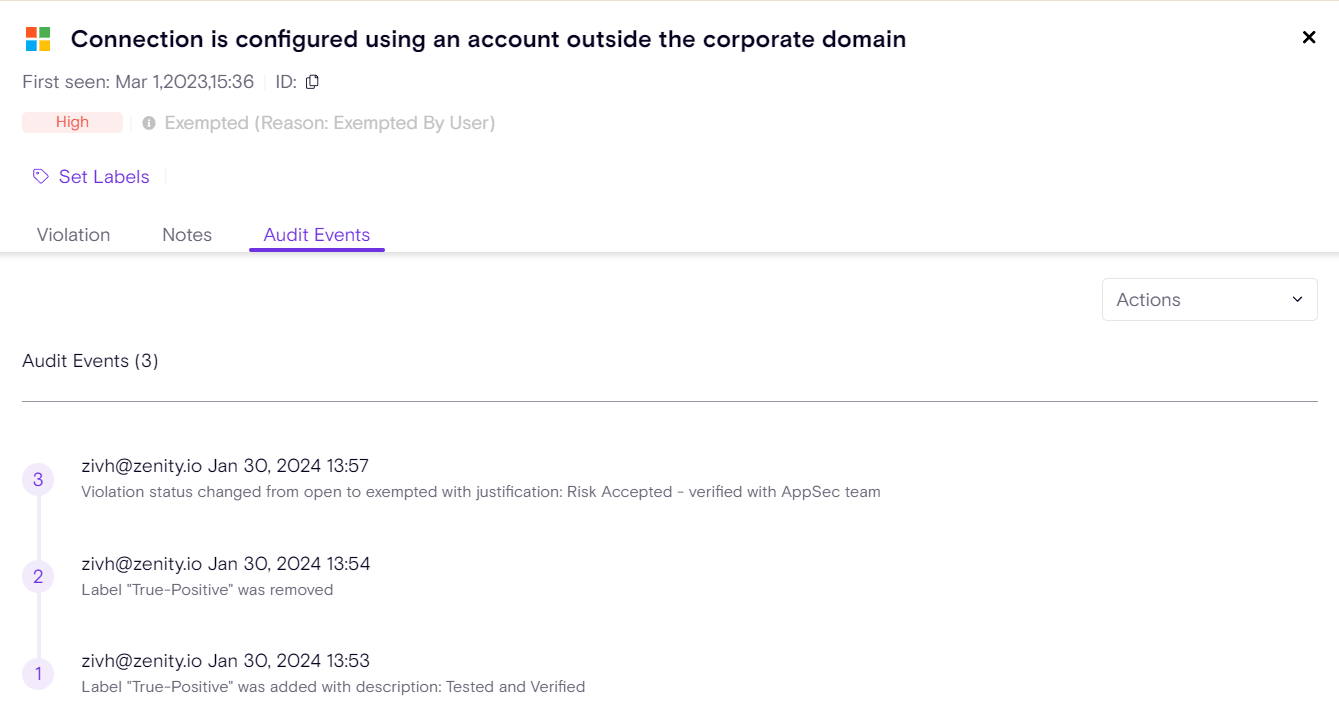
The audit events can be viewed in a new tab called "Audit Events".
Audit Events are immutable and cannot be changed or deleted.
Reducing Copilot Oversharing Risk with the newly introduced 'Set Access' feature
Copilots created on the Copilot Studio can easily be overshared.
Here are a few examples:
- Copilots shared with Unauthorized Guest users
- Copilot shared with the entire tenant
Zenity flags both of these scenarios as violations, and now we allow customers to remediate them from within Zenity.
Using the 'Set Access' action Zenity unleashes several use-cases at the customer disposal:
- In case a team member from the AppSec team or PowerPlatform Admin wants to view a specific Copilot in depth, through Zenity he can get access using the 'Add Owner' action (after he is done he can also remove the same permission).
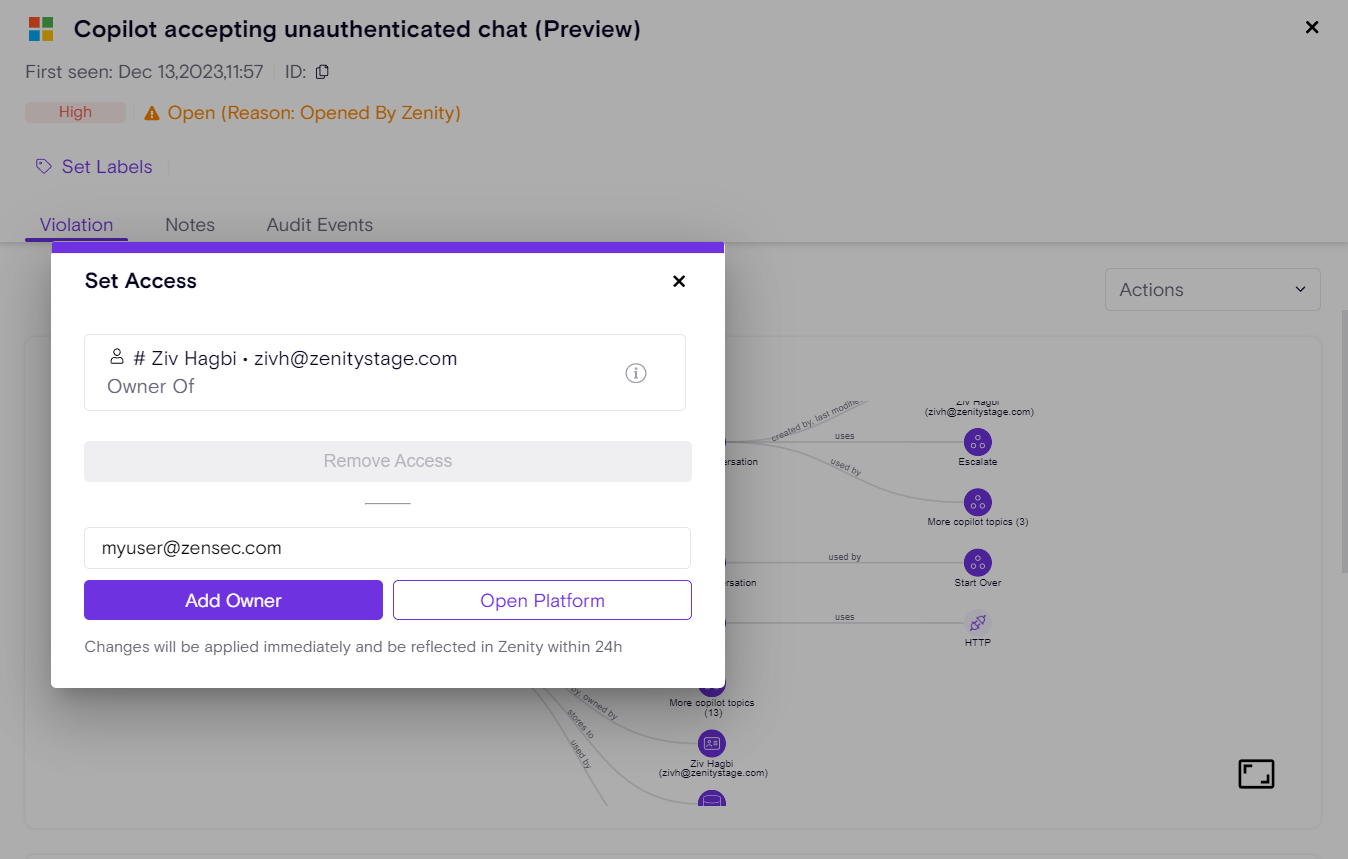
- In case the Copilot is shared with Guest users, Zenity users can view them and remove guest access.
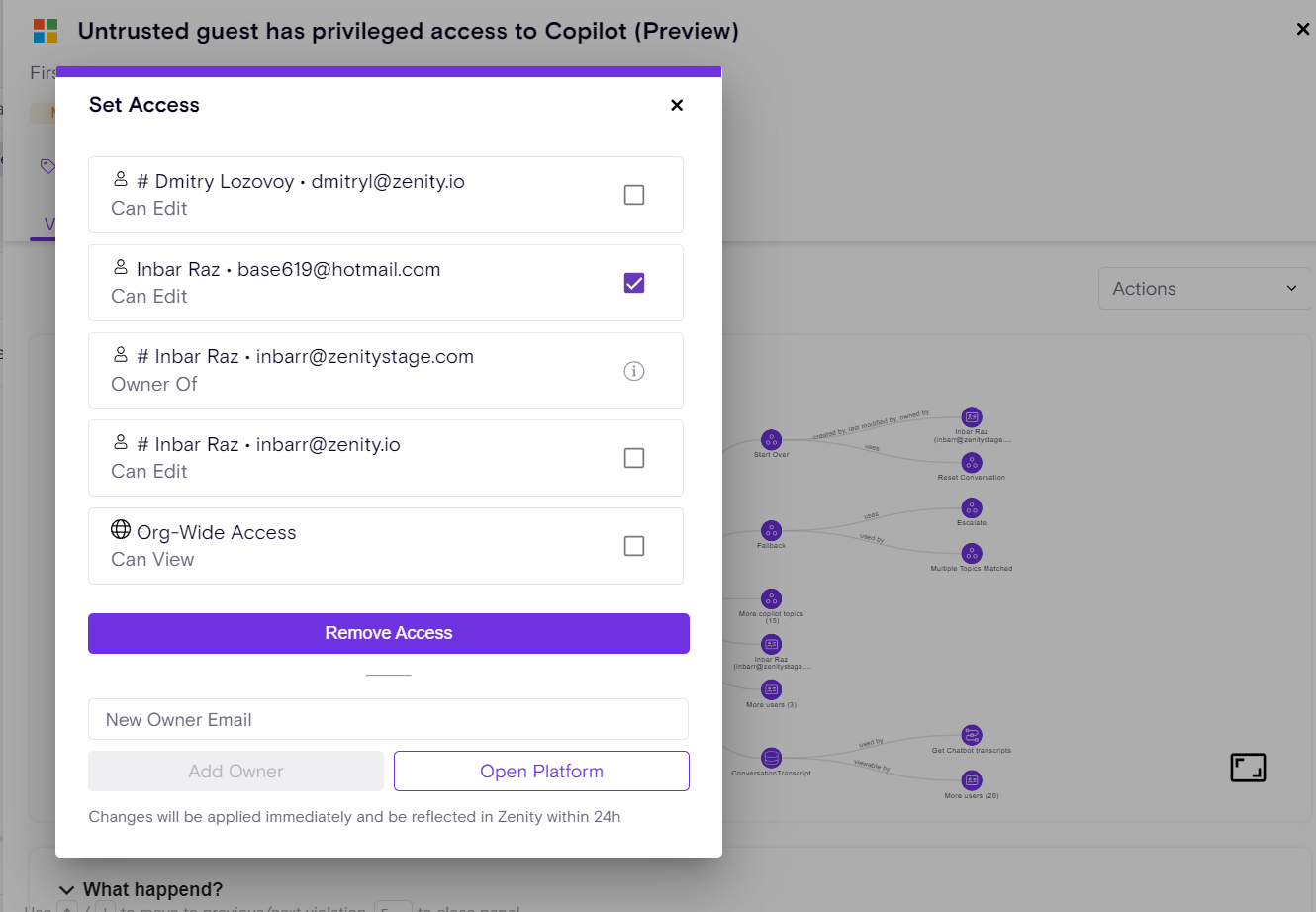
- In case the Copilot is shared with the entire tenant, Zenity users can view it and remove that access.
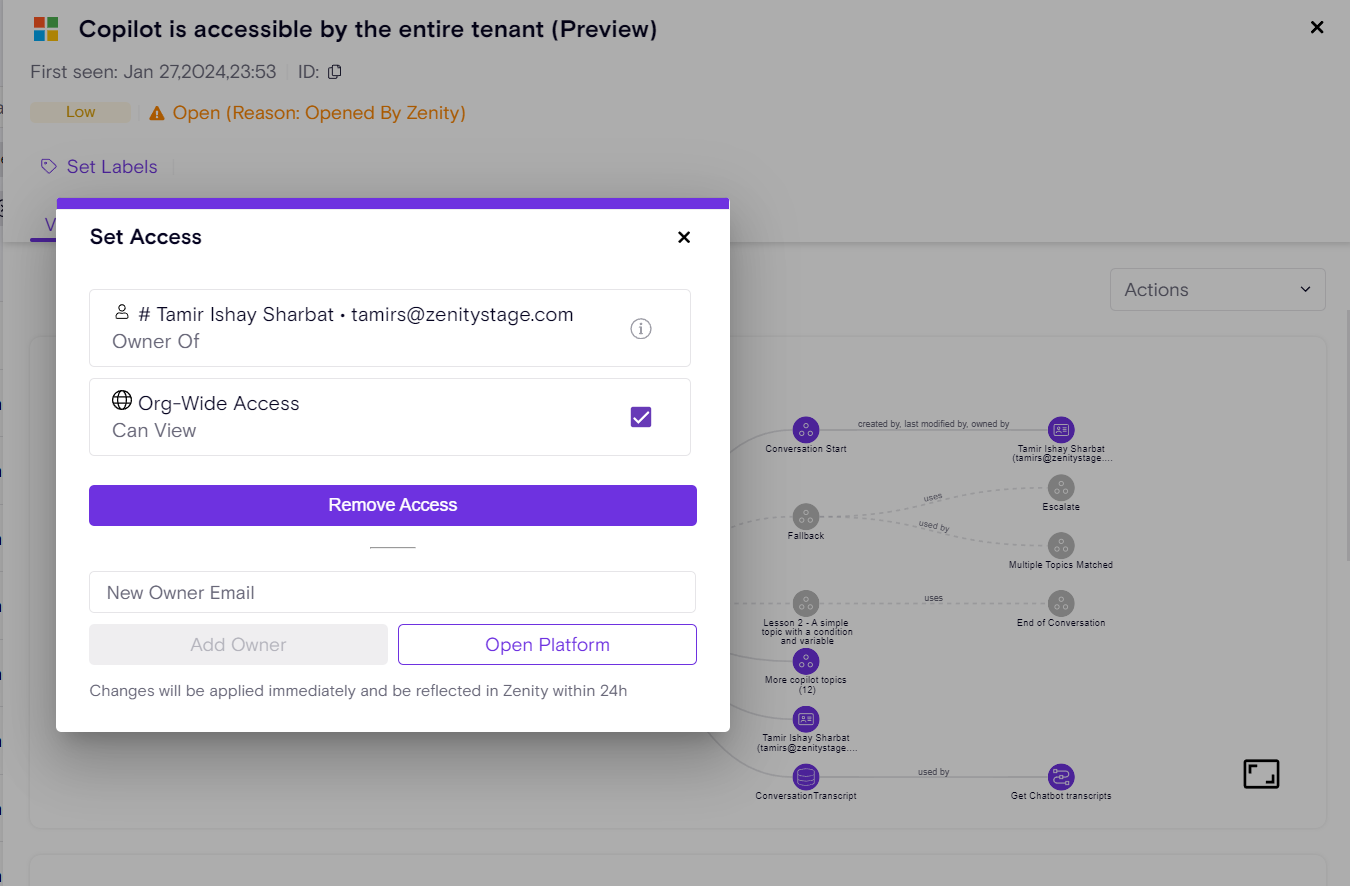
This action is available through both our API and UI.
Reducing Credentials Sharing Risk with the newlyintroduced 'Set Access' feature for PowerPlatform Connections
Power Platform has a rich interface for sharing resources, however with this capability comes a grave risk of abusing sharing that can cause identity impersonation and data leakage.
This especially risky when it comes to sharing data connections, for example a SQL Server DB connection.
Imagine a user created a SQL DB connection using his SQL Admin credentials and shared the connection with the entire tenant (instead of going down the route of explicit sharing).
Now other users, can view this connection and use it as their own (keep in mind this is a highly privileged user).
Users can create Apps and Automation using the same connection impersonating the original maker.
They can pull data outside the original scope of what the maker used in his usage of the connection and even potentially purging it completely.
Zenity flags this scenario as violation, and now allows customers to remediate it from within Zenity.
Using the 'Set Access' Zenity unleashes several use-cases at the customer disposal:
- In case a team member from the AppSec team or PowerPlatform Admin wants to view the specific Connection in depth, through Zenity he can get access using the 'Add Owner' action (after he finished he can also remove the same permission).
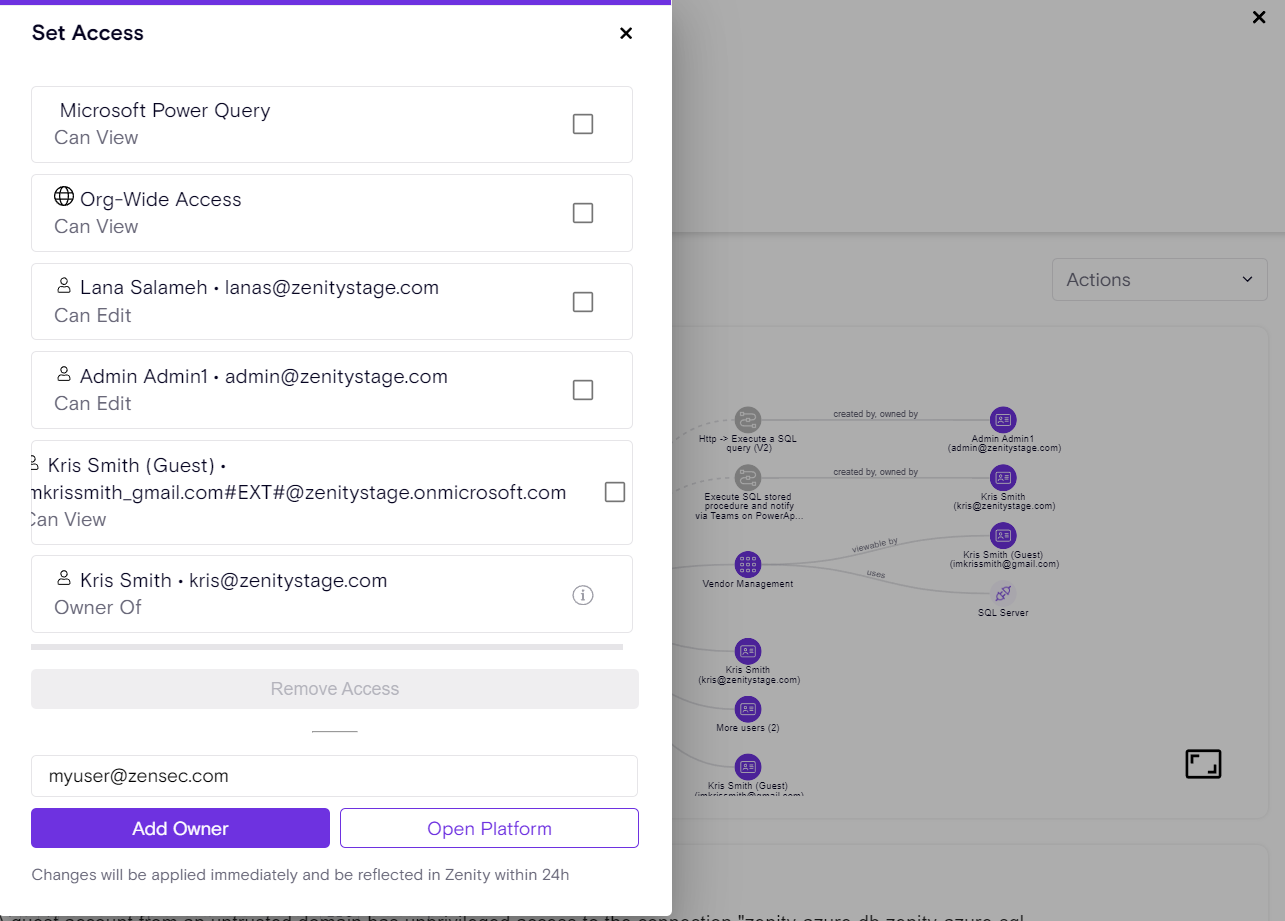
- In case the Connection is shared with Guest users, Zenity users can view them and remove guest access.
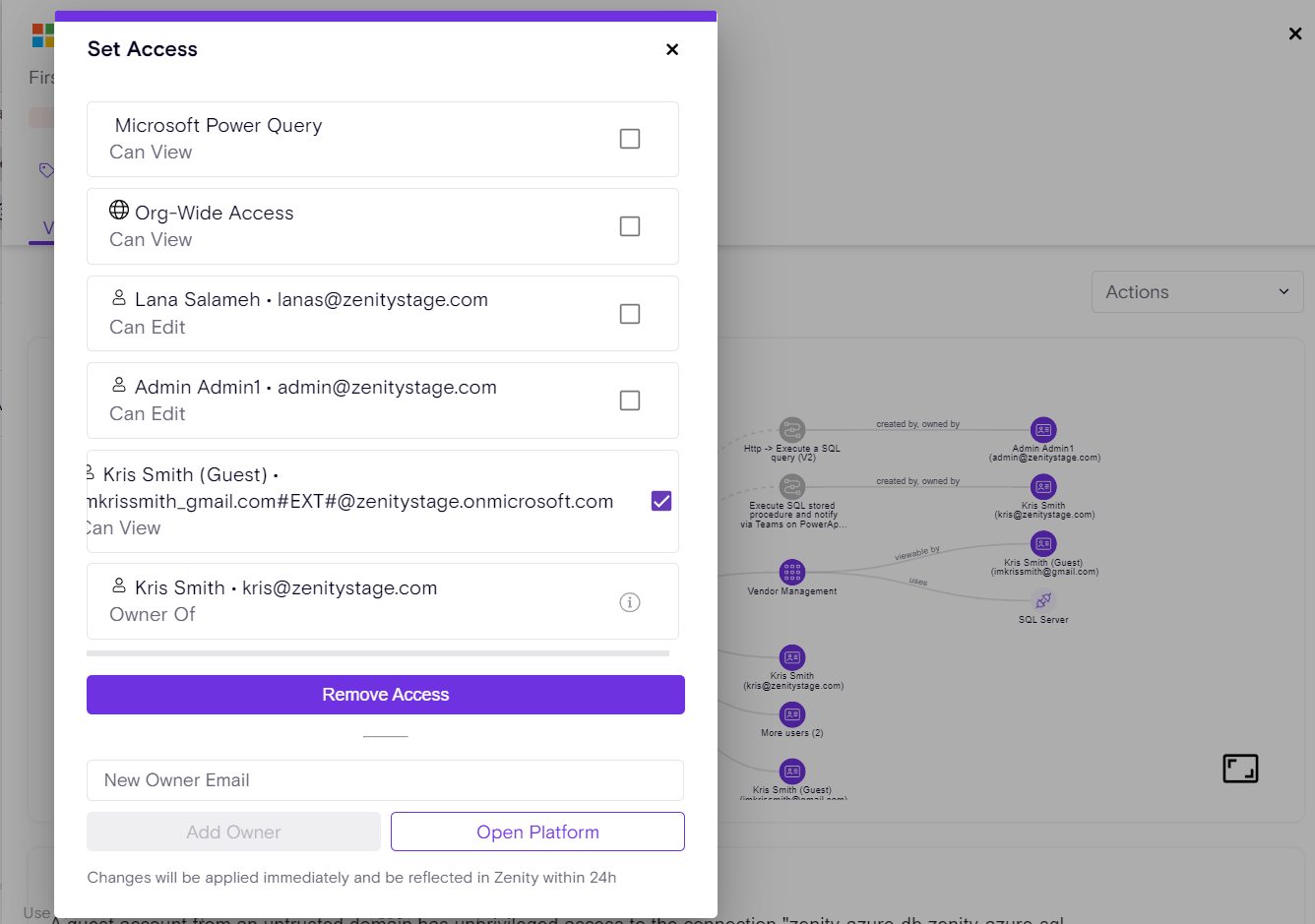
- In case the Connection is shared with the entire tenant, Zenity users can view it and remove that access.
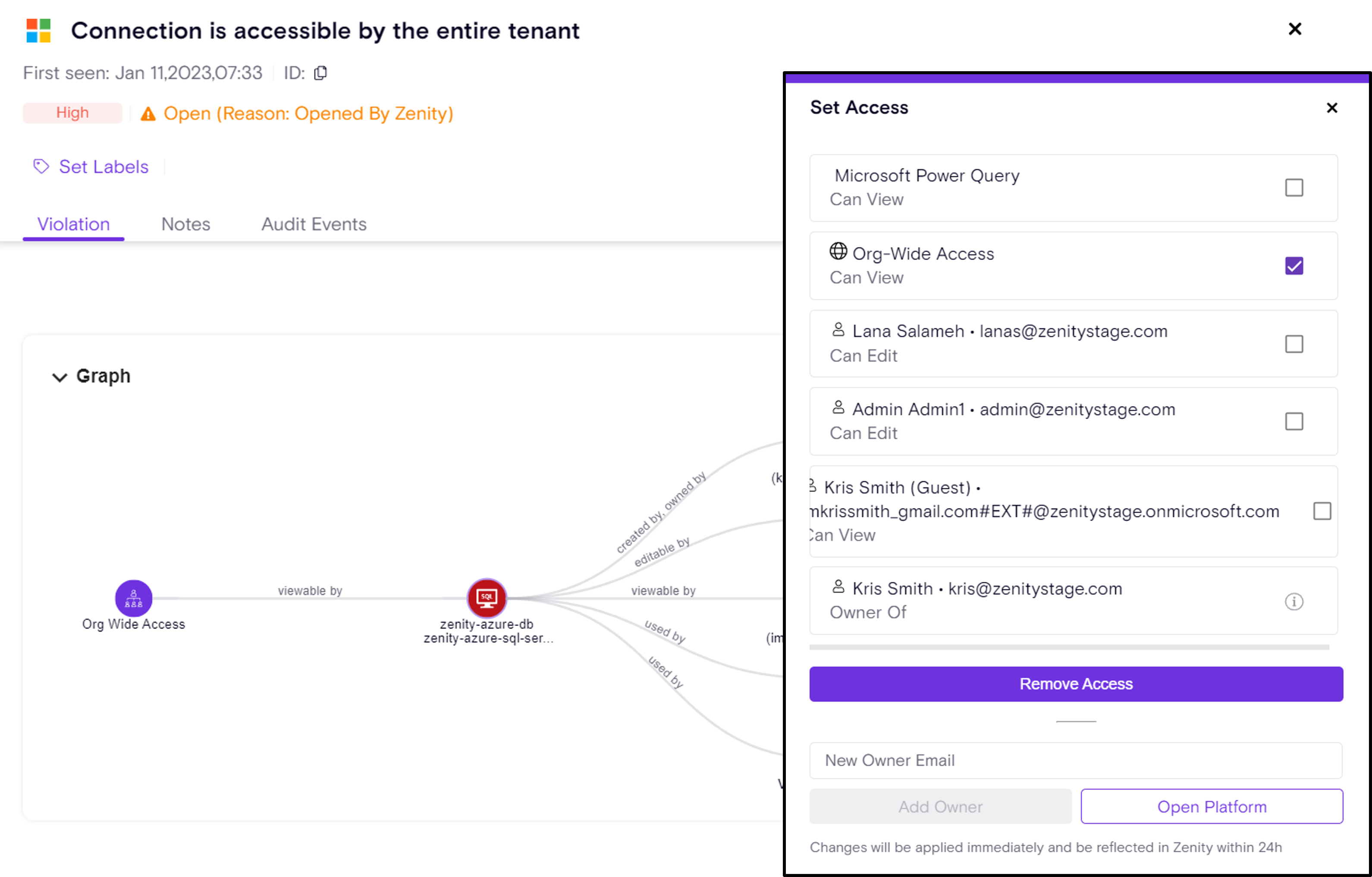
This action is available through both our API and UI.
Enhanced investigation capabilities for sensitive data exposure with the newlyintroduced 'Get Latest Flow Runs' feature
Zenity monitors and flags sensitive data (PII/PCI/PHI) exposed in plain-text in flow logs and can mask it automatically.
When a user wants to investigate such a scenario up until today he needed to locate the sensitive data in the Power Automate flow logs.
In order to assist with this process, Zenity now allows users to ad-hoc pull in real-time the latest flow logs, so users can understand what data passes through the flow and check if it's sensitive.
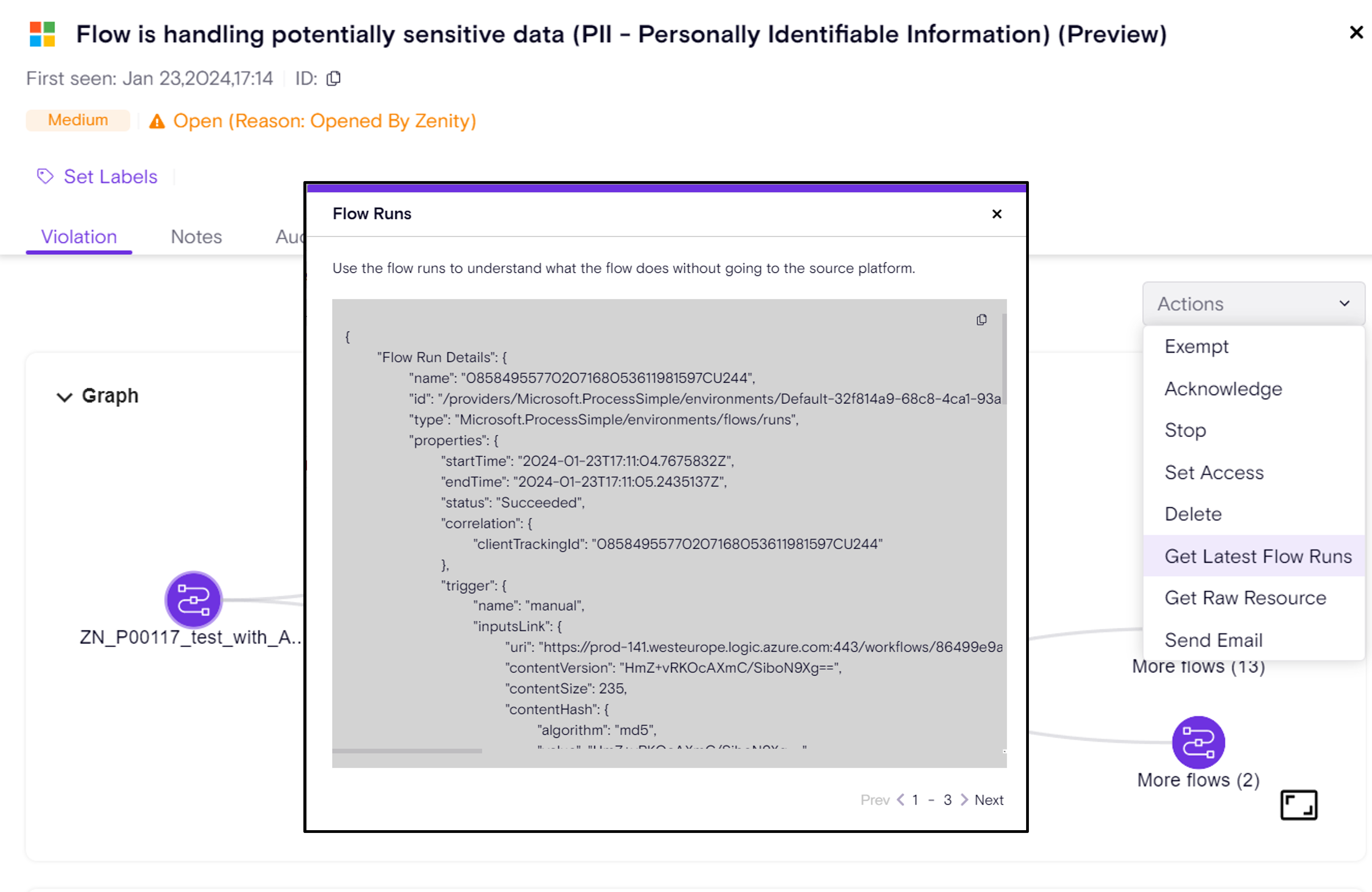
Zenity pulls up to the latest 10 flow runs and Zenity users can browse through them.
Important Update: Rules Deprecations
Zenity is always working on enhancing and improving our rule based and risk assessment as such from time to time we will deprecate rules, either to merge them with others or if they are no longer applicable due to changes in the platform.
Here is the list of rules that we are planning to deprecate by 2.20.2024.
- ZN_P00005 - Flow is accessible by anyone with a link via a webhook (Deprecated)
The rule will be replaced by:- ZN_P00145 - Flow is exposed to the Internet.
- ZN_P00145 - Flow is exposed to the Internet.
- ZN_P00132 - Copilot is accessible by the entire tenant (Deprecated)
The rule will be split and repalced by:- ZN_P00143 - Published Copilot is accessible by the entire tenant
- ZN_P00146 - Unpublished Copilot is accessible by the entire tenant
- ZN_P00143 - Published Copilot is accessible by the entire tenant
Zenity Dec-2023
⭐ Highlights
PowerBI Support (Preview)
PowerBI is the main pillar of analytics/business intelligence within the Microsoft PowerPlatform suite, alongside PowerApps, PowerAutomate and Copilot Studio.
Zenity covers PowerBI with regard to Visibility, Risk Assessment and Governance in a similar manner and standard as customers are accustomed to.
In order to support PowerBI, customers are required to create a new integration with PowerBI. Please verify with the Zenity customer success team that your license covers PowerBI, without the proper license the integration would not work.
Shadow Reports/Dashboards/Datasets/Apps are a thing of the past now as customers can view all of them within the Zenity Inventory.
Zenity uncover all of them in our inventory:
Zenity detects various risk scenarios for PowerBI, including:
-
Guest Access
-
Suspicious Endpoints communication
-
Privileged role abuse
-
Sensitive Information exposure (MIP Labels)
-
Organization wide access
-
Authentication issues / Anonymous access
-
Resource Oversharing
-
Data Leakage
Highlighted Scenarios:
1. PowerBI report is accessible by the entire organization exposes corporate data
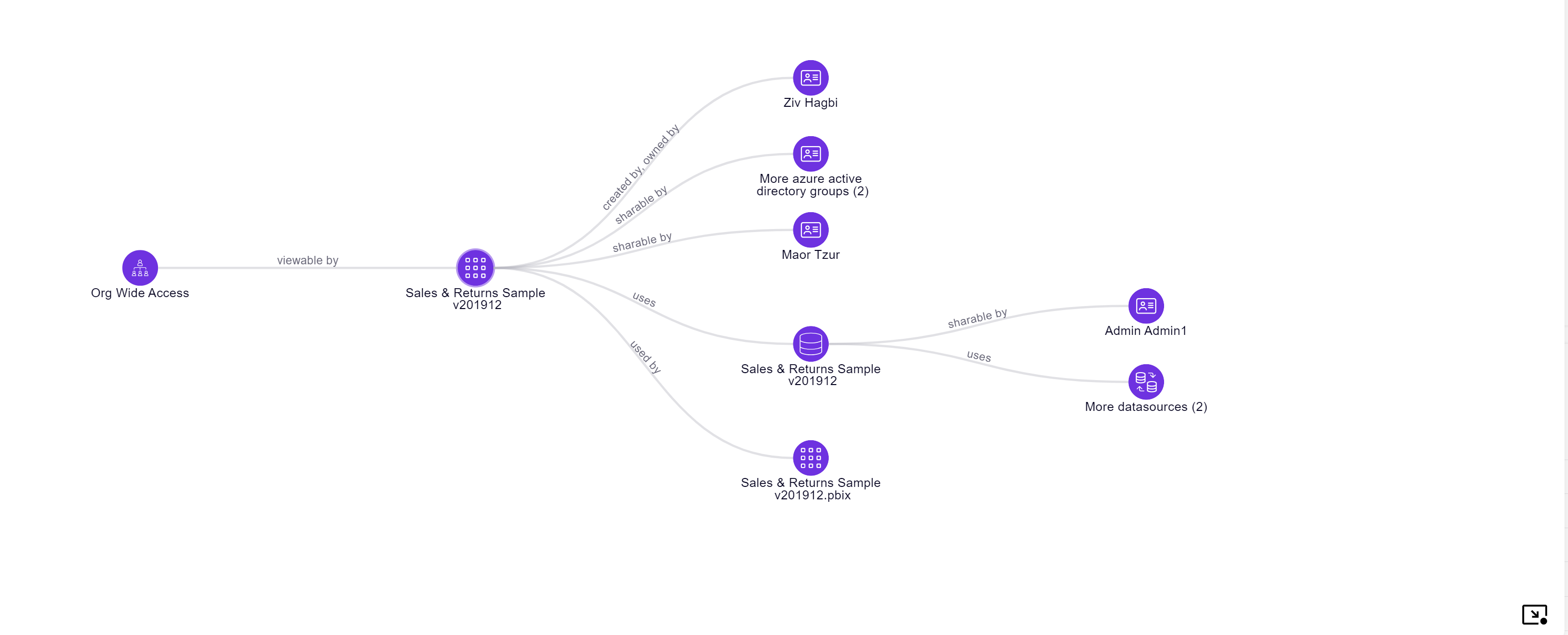
In this scenario, the PowerBI report is accessible by the entire organization and on the other hand connected to a SQL Server via a shared SQL Connection. The Graph shows the e2e path to exploit and data that is exposed.
This graph shows that any member within the organization that has the PowerBI report link, can view the report.
2. PowerBI report without authentication exposes business data
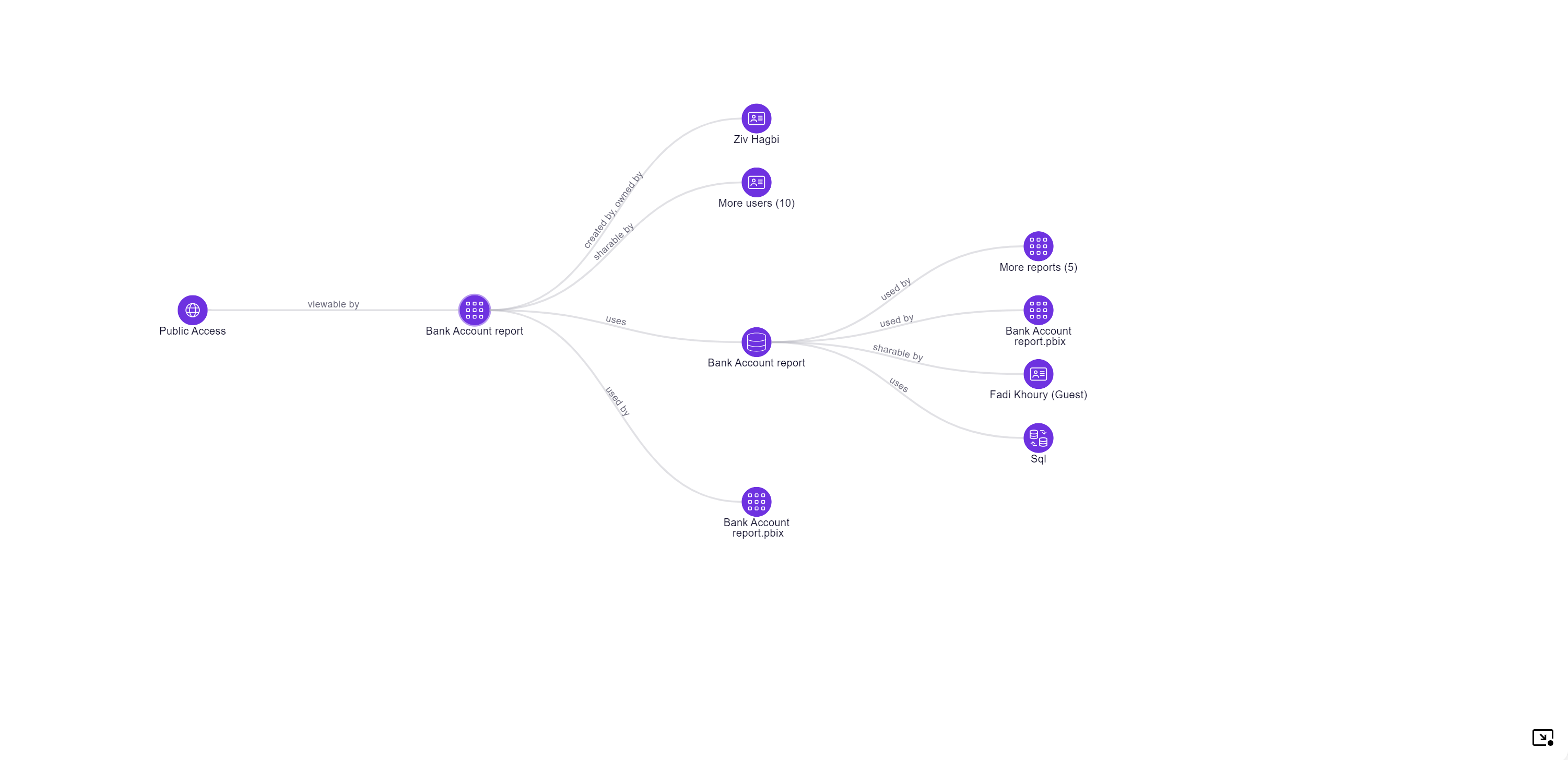
In this scenario, the PowerBI report is accessible by anyone (no authentication required) and on the other hand connected to business data. The Graph shows the e2e path to exploit and data that is exposed.
3. PowerBI Dataset handling corporate data exposed to Guest users
In this scenario, the PowerBI Dataset is accessible by the entire organization (meaning every user in the org that has the report link can view its content) but in addition it is also shared with a guest user with privileged access. The guest user not only has access to the report but it also has access to the underlying dataset. For example, if PowerBI report or dataset expose sensitive data the guest user will have access to both.
For the full documentation, go to the 'PowerBI' in the Docs center.
Copilot Studio
New Mitigation actions
- Set Authentication
Zenity now supports 'Set Authentication' action for Copilot allowing users to restrict the access for Copilot, for example, restrict annonymous access. In addition, it allows to enforce user sign-in, preventing for any Copilot to be publicly exposed via a custom authentication method.
The action, by defult, also restricts any Copilot that is accessible to the entire organization.
The action is available via the the manual action and API.
- Get Raw Resource
In the effort of allowinf for deeper investigation via Zenity, we know allow users to view the resource in its raw form. This action is available for Copilot and Copilot Topics.
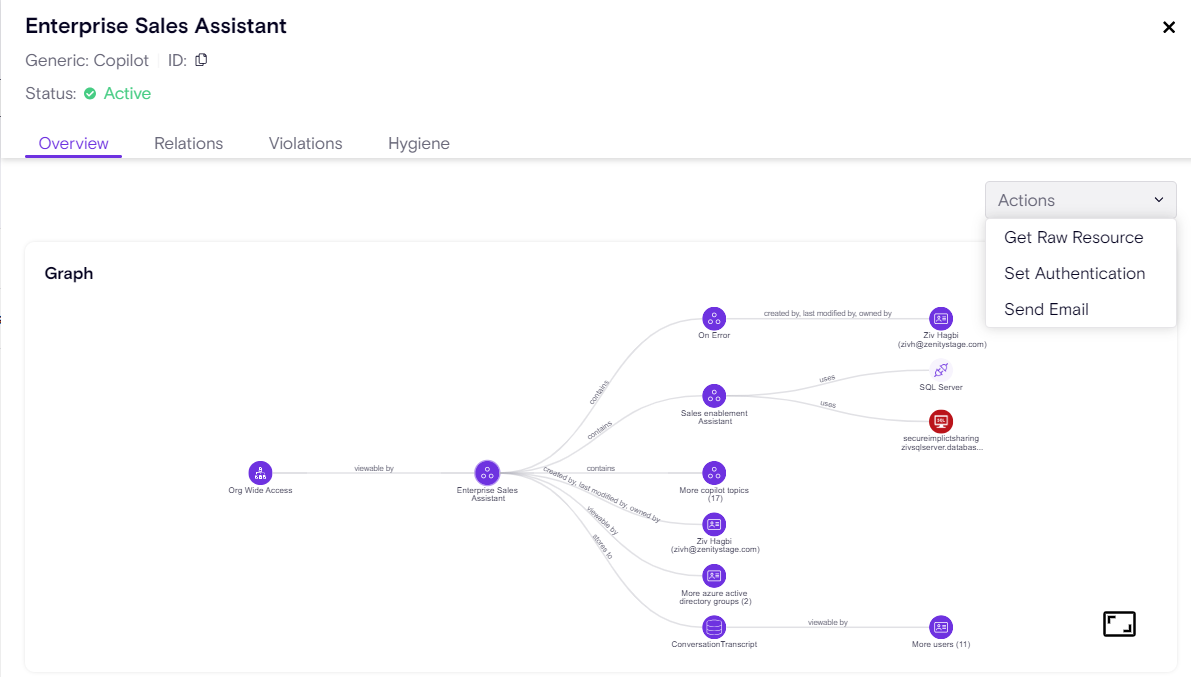
Inventory
- Added the ability to view if a Copilot is using 'Dynamic Changing', which allows Copilot to use generative answers instead of scripted ones, potentially exposing it to prompt injection attacks This is covered by a new violation rule 'ZN_P00142 - Copilot Action plugin is exposed to prompt injection (Preview)'.
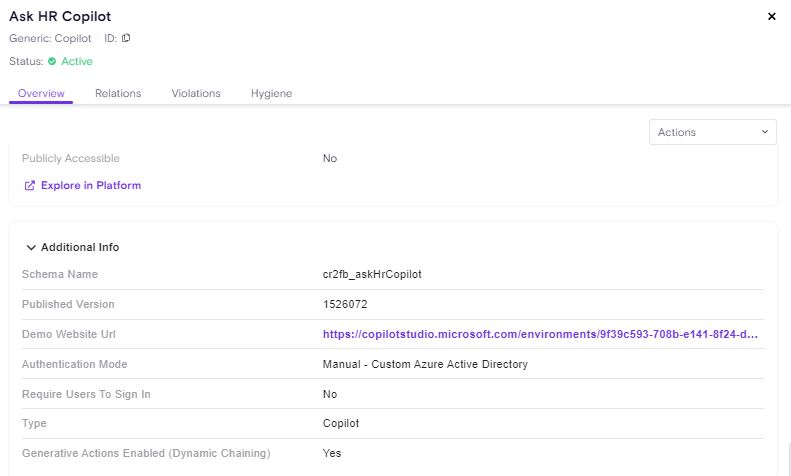
Custom Labels
Zenity now supports custom labels for Violations and Hygine issues. Customers can create and add their own labels to violation via Zenity's UI and via the API. Available abilities:
- Create Label
- Edit Label
- Delete Label
- Add Label to a violation
- Remove Label from violation
The possibilities here are endless, as customers have the granularity to use custom labels in many forms.
Set Labels
Create
Edit
Delete
Policy Configuration Improvements
- In order to avoid FPs and noise, for any new custom policy that is created Zenity will automaitcally populate the trusted domain with the ones configured in the Default policy. Customers can change them at will.
Endpoint Filtering Improvements
- In order to avoid FPs and noise, the Allowed list in the 'Endpoint Filtering' settings will also use the'Trusted Domains' list.
Graph Improvements
-
Automatic collapse In order to not overpopulate the graph and make it easier to focus on the issues, we grouped the graph nodes. The logic is as follows: nodes of the same resource type and relation type of grouped together.
-
Expand / Collapse abilities
Following up on the previous bullet, customers can always expand the graph by clicking on the grouped node.
New Violation Rules (a full description can be found in the Zenity policy page)
- ZN_P00131- Copilot accepting unauthenticated chat (Preview)
- ZN_P00134 - Copilot is handling potentially sensitive data (PII - Personally Identifiable Information) (Preview)
- ZN_P00135 - Copilot is handling potentially sensitive data (PCI - Payment Card Industry) (Preview)
- ZN_P00136 - Copilot is handling potentially sensitive data (PHI - Protected Health Information) (Preview)
- ZN_P00137 - Copilot Topic has access to business data (Preview)
- ZN_P00139 - Copilot Topic is communicating with disallowed endpoints (Preview)
- ZN_P00140 - Copilot has many privileged identities (Preview)
- ZN_P00141 - Copilot authentication is not enforced (Preview)
- ZN_P00142 - Copilot Action plugin is exposed to prompt injection (Preview)
Important Update: Rules Deprecations
Zenity is always working on enhancing and improving our rule based and risk assessment as such from time to time we will deprecate rules, either to merge them with others or if they are no longer applicable due to changes in the platform.
Here is the list of rules that we are planning to deprecate by 1.4.2024.
- ZN_P00057 - Portal App is using custom code (CSS) (Deprecated)
ZN_P00057 will be merged into 'ZN_P00035 - Portal App is using custom code'.
In case you have existing playbooks or other automation using these rules, please replace them with the relevant rules below.
For any question, please contact zenity through your dedicated customer support or open a ticket to support.
Misc
- New pre-defined query - "All Builders"
Through the Zenity pre-defined query in the Inventory page, customers can get a list of all users who have actually built an App or an Automation.
- The 'Department' field to the export CSV functionality
- The 'Label' field to the export CSV functionality
Zenity Nov-2023
⭐ Highlights
Copilot Studio Support
Zenity is on a mission to secure Generative AI in the enterprise.
Today, Zenity has become the 1st company in the world that provide Visibility, Risk Assesment and Goverance for Microsoft Copilot Studio.
Zenity Customers can now gain visibility into all Copilots created via the Copilot Studio. Zenity Assess each Copilot for security vulnerabilities.
What's included in this release?
Visibility for all Legacy Chatbots and newly released Copilots
Copilot & Legacy Chatbots
Copilot Authentication Methods
Zenity can detect the different authentication types Copilot uses. for example, Copilots using 'No Authentication', meaning they can be used by anyone (inside and outside the organization)

Copilot Role-Based-Access-Control
Zenity can provide visibility into the access layer of Copilot, who has access to use it and show if it's overshared.
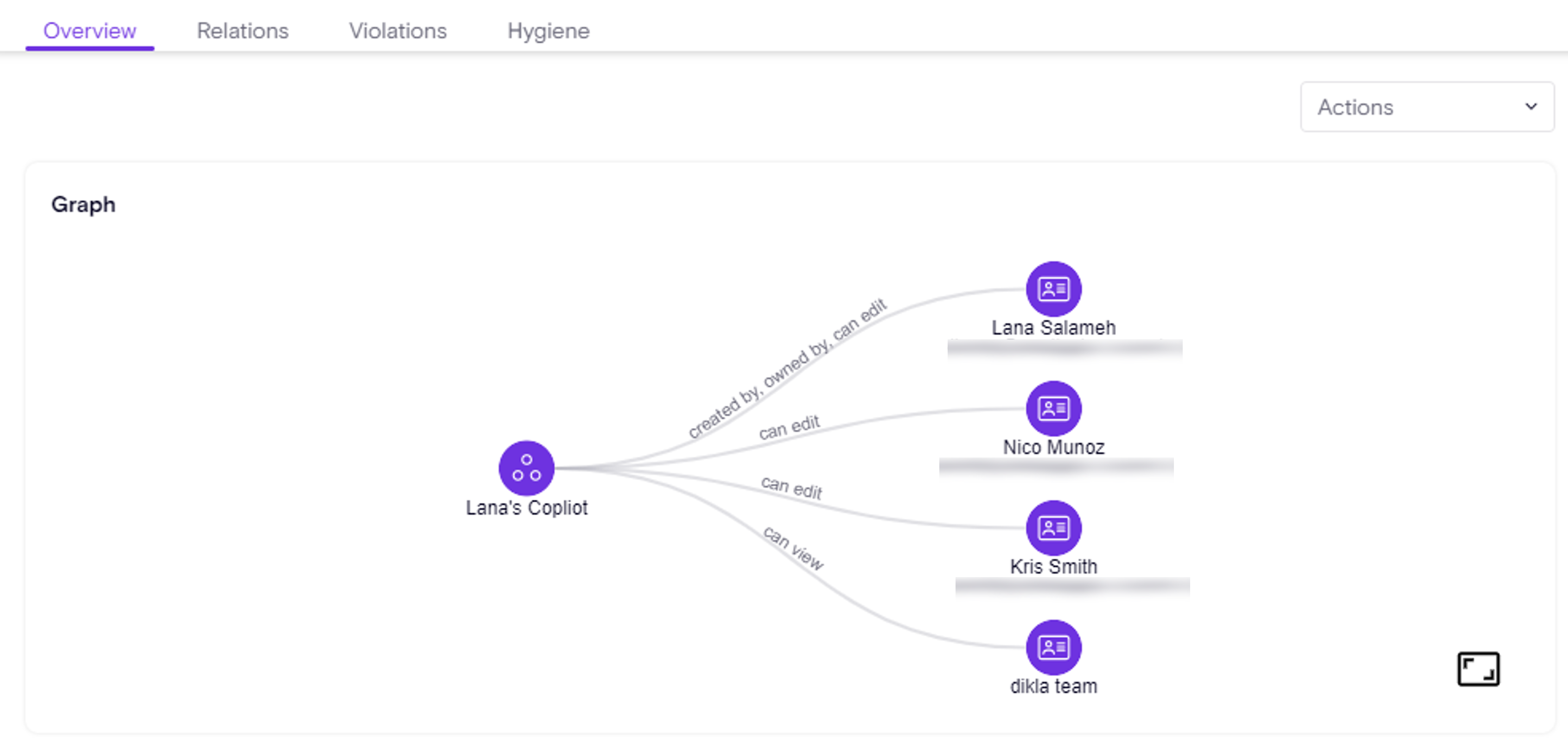
Copilot Timeline
Zeniny continuously scan the customers tenant's and can provide a comprehensive timeline for all Copilots including:
Creation date and by who Last Modified date Last Published
New Violation Rules (a full description can be found in the Zenity policy page)
- ZN_P00132 - Copilot is accessible by the entire tenant
- ZN_P00133 - Flow with access to business data is triggered by Copilot
- ZN_P00212- Untrusted guest has privileged access to Copilot (Preview)
- ZN_P00213 - Untrusted guest has unprivileged access to Copilot (Preview)
- ZN_P00214 - Untrusted member has privileged access to Copilot (Preview)
- ZN_P00215 - Untrusted member has unprivileged access to Copilot (Preview)
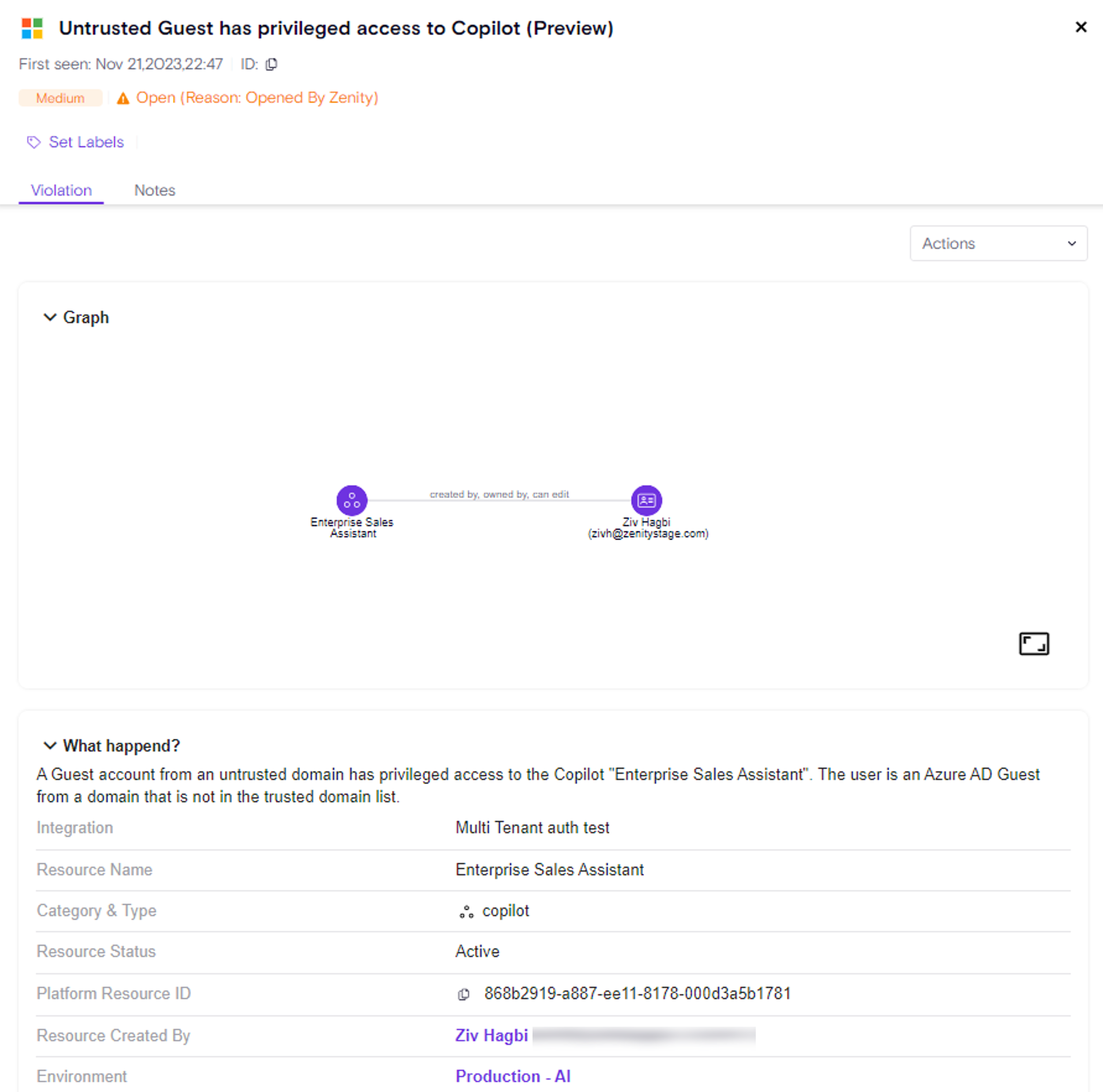
Advanced Flow Visibility & Risk Assessment
In many cases for security professionals to investigate a violation they need to view the flow with their own eyes. A good example, is reviewing cases of hard-coded secrets. As a part of our risk engine, Zenity can discover sensitive information leaking in plain-text for anyone to see (Passwords, Secrets, API keys, etc...).
Zenity does not store that data and until today users needed to go to the source platform in order to see the hard-coded secrets in the flow.
Another example, could be wanting to understand what actions the flow invokes and their sequence for better context.
Now, Zenity enables real-time presentation of the flow structure, with our new 'Get Flow Definition' action. Zenity does not store this information it is fetched and presented in real-time.
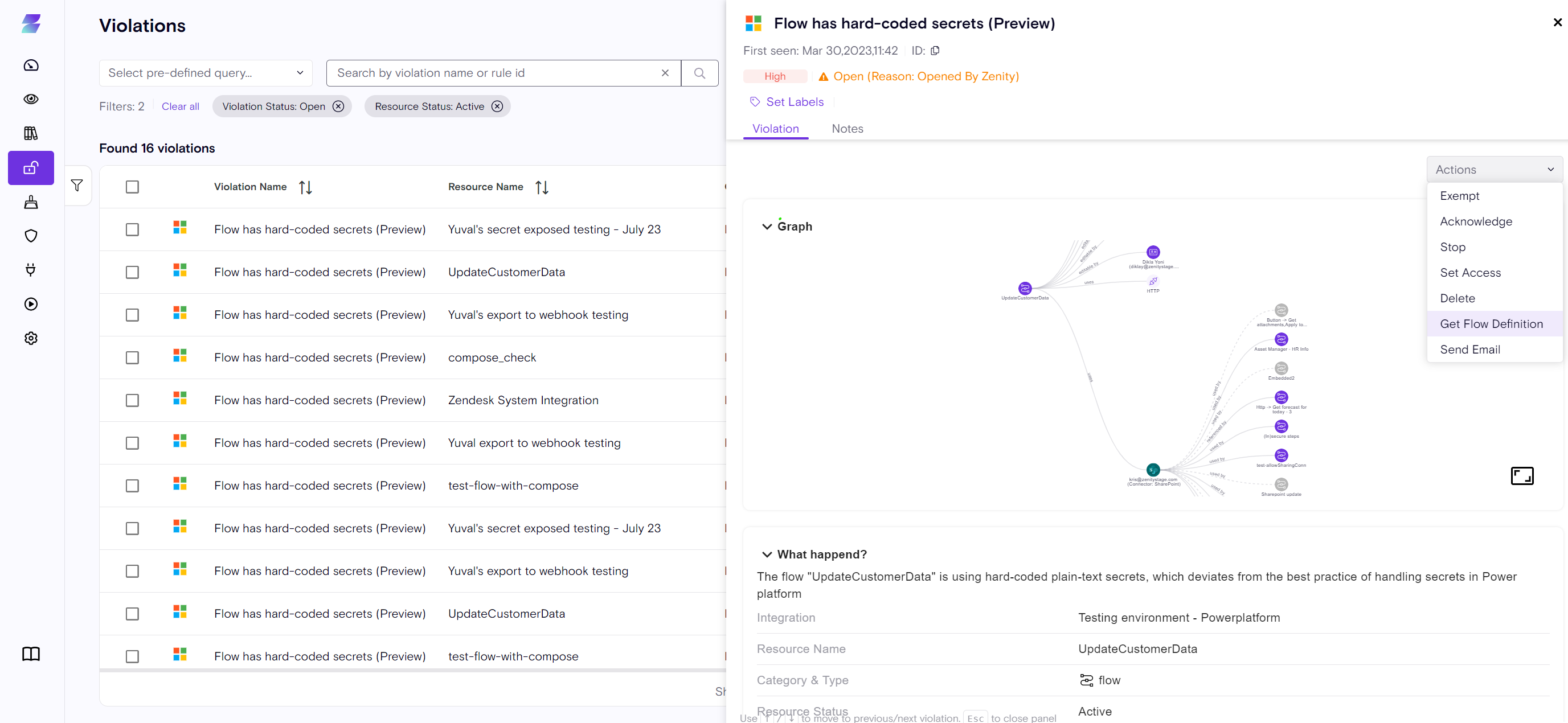
Natively within Zenity, users can view and understand what the flow does, and assess different risks such as: Hard-coded secrets. This action supports both Solution Aware and Non-Solution Aware flows.
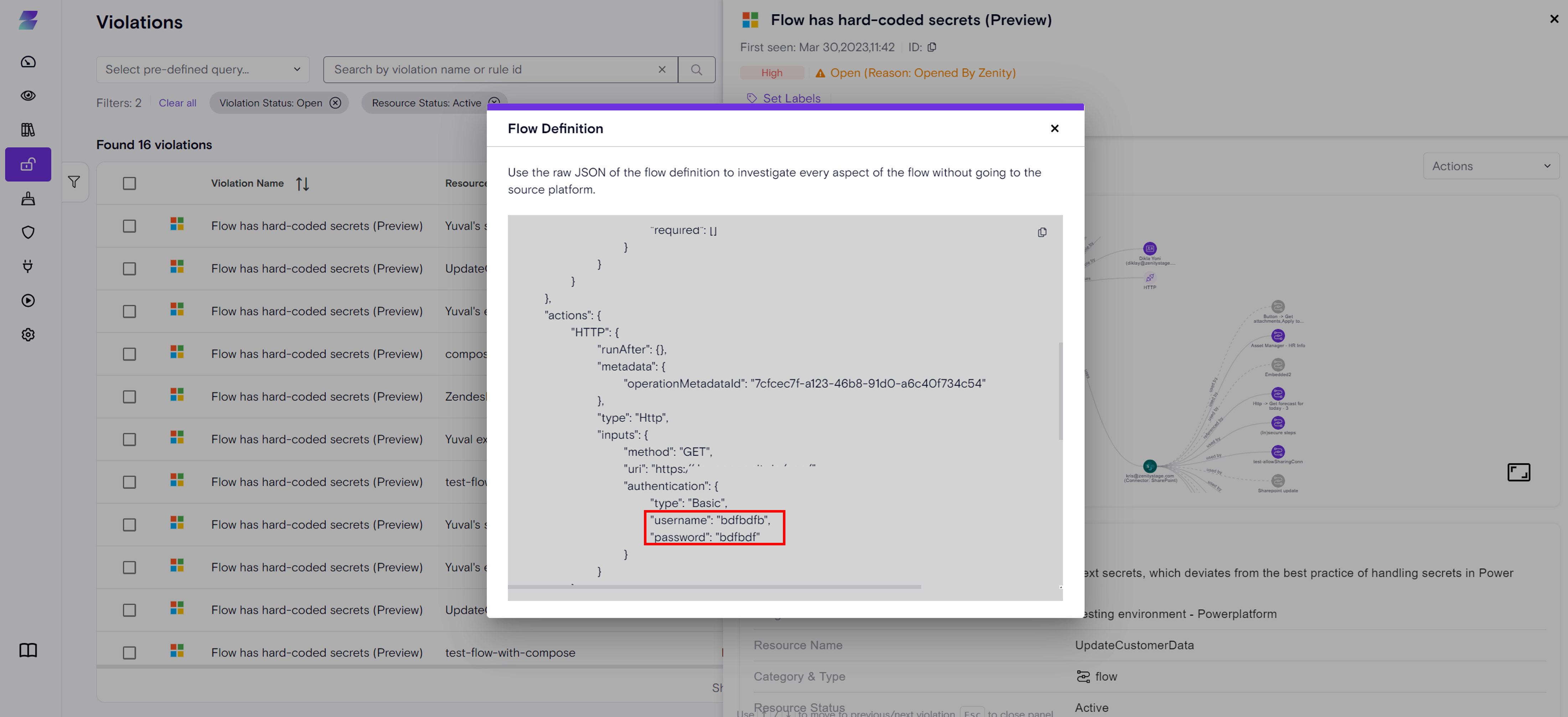
Generative AI
Zenity is now able to bind Generative-AI visibility capabilities with our playbooks. Customers can use the Gen-AI filter to trigger playbooks in case a resource was created with Gen-AI or triggering playbooks for violation on resources that were created by Gen-AI. In addition, customers can utilize the full spec of playbook capabilities and add the Gen-AI filter to focus on specific use-cases, for example.
Trigger a playbook for Flow exposing sensitive data that was created using Gen-AI.
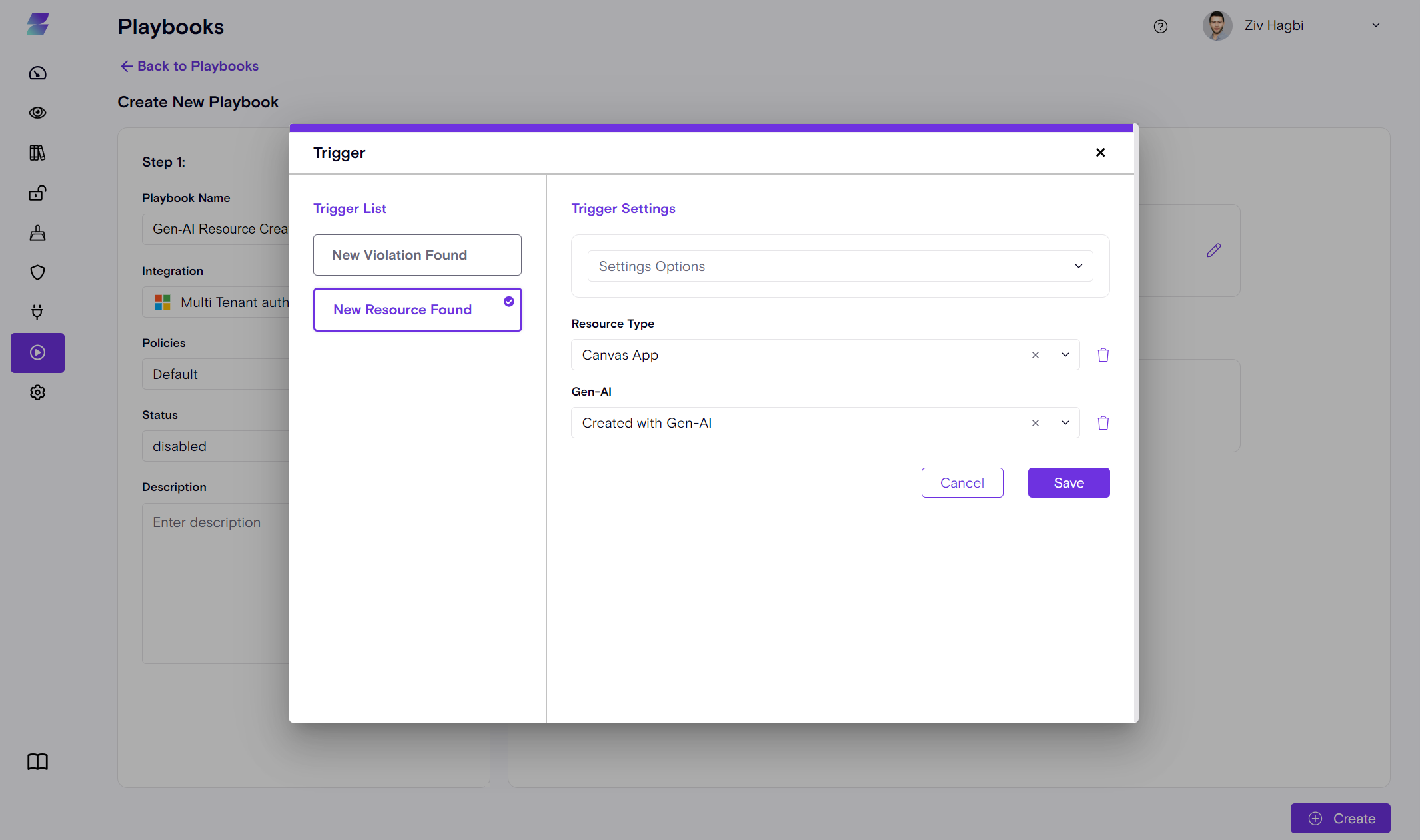
Important Update: CVSS Rules Mapping Update & Rule Deletion
CVSS Rule Mapping Update
In the effort of making the rule severity more accurate Zenity start using the CVSS framework.
As a result some rules will have a new severity level.
The below table shows the rule severity updates that will take place by the end of the year.
No action is required by the users.
Custom rule severities will not be updated.
| Rule ID | Title | Current Severity | New Severity |
|---|---|---|---|
| ZN_P00004 | Connection is using an unofficial, uncertified connector | Medium | High |
| ZN_P00005 | Flow is accessible by anyone with a link via a webhook | Low | High |
| ZN_P00009 | Flow has more than the allowed number of makers | Low | Medium |
| ZN_P00016 | Connection is using an on-prem connector | Low | High |
| ZN_P00017 | Connection is using a deprecated connector | Low | High |
| ZN_P00020 | Connection has no host key fingerprint | Medium | High |
| ZN_P00025 | Connection is using a non-standard port | Medium | Low |
| ZN_P00031 | Environment is using a non-Microsoft managed key | High | Medium |
| ZN_P00035 | Portal is using custom code (Javascript) | Medium | High |
| ZN_P00048 | CanvasApp is accessible by the entire tenant | High | Medium |
| ZN_P00057 | Portal App is using custom code (CSS) | Medium | High |
| ZN_P00058 | Connection is using a deprecated authentication method | Low | High |
| ZN_P00062 | CanvasApp has no valid owners or editors | Low | Medium |
| ZN_P00065 | Connection has no valid owners | Low | High |
| ZN_P00069 | Flow is potentially exposing sensitive data in logs | High | Medium |
| ZN_P00070 | Potential IDOR vulnerability in flow | Low | High |
| ZN_P00074 | Environment has too many privileged users | Medium | High |
| ZN_P00075 | Environment has many privileged users | Low | High |
| ZN_P00076 | Portal enables local sign-in | Medium | High |
| ZN_P00077 | Flow is using arbitrary SQL queries | Medium | High |
| ZN_P00078 | Custom connector enables custom code | Medium | High |
| ZN_P00080 | Custom connector has no authentication method configured | Medium | High |
| ZN_P00086 | Flow is using a potentially hard-coded secret (dynamic input for sensitive parameters) | Medium | High |
| ZN_P00087 | Portal enables untrusted sign-in (untrusted identity provided) | Medium | High |
| ZN_P00088 | Flow is using an unauthenticated HTTP virtual connector | Medium | High |
| ZN_P00089 | Environment enables PCF in apps | Medium | High |
| ZN_P00092 | Flow is handling potentially sensitive data (Credit card numbers) | High | Medium |
| ZN_P00094 | Flow is using connectors which are bypassing the DLP policy | High | Medium |
| ZN_P00095 | Flow has an insecure Azure Key Vault step (Preview) | High | Medium |
| ZN_P00096 | CanvasApp has no connection consent dialog | Medium | High |
| ZN_P00099 | Flow is handling potentially sensitive data (PCI - Payment Card Industry) | High | Medium |
| ZN_P00101 | DLP policy enables risky connectors (Preview) | Medium | High |
| ZN_P00103 | Flow is exposing sensitive data in logs (Preview) | High | Medium |
| ZN_P00104 | Non-production environment is empty (Preview) | Low | Medium |
| ZN_P00107 | Connection is using an OpenAI connector | High | Medium |
| ZN_P00108 | Flow is exposing sensitive data in logs (via flow trigger) (Preview) | High | Medium |
| ZN_P00110 | Custom connector is using OpenAI API | High | Medium |
| ZN_P00111 | Untrusted guest with access to tenant resources | High | Medium |
| ZN_P00112 | Flow has an insecure sensitive step (Preview) | High | Medium |
| ZN_P00113 | Custom connector has custom policies templates | Low | High |
| ZN_P00114 | Connection is using a suspicious domain name | Medium | High |
| ZN_P00116 | Gateway is vulnerable | Medium | High |
| ZN_P00118 | Tenant settings allows non-admin users to manage production environments | Medium | High |
| ZN_P00122 | Connection is stale | Low | Medium |
| ZN_P00124 | Untrusted member with access to tenant resources | High | Medium |
| ZN_P00130 | Flow is sharing sharepoint data over email (Preview) | High | Medium |
| ZN_P00131 | Copilot accepting unauthenticated chat | Medium | High |
| ZN_P00132 | Bot is accessible by the entire tenant | Medium | High |
| ZN_P00133 | Flow with access to business data is triggered by a Virtual Agent | Medium | Low |
| ZN_P00139 | Copilot is communicating with disallowed endpoints (Preview) | Low | High |
| ZN_P00201 | Untrusted guest has unprivileged access to connection | Medium | High |
| ZN_P00202 | Untrusted guest has privileged access to canvasApp | High | Medium |
| ZN_P00204 | Untrusted guest has privileged access to flow | High | Medium |
| ZN_P00207 | Untrusted member has unprivileged access to connection | Medium | High |
| ZN_P00208 | Untrusted member has privileged access to canvasApp | High | Medium |
| ZN_P00210 | Untrusted member has privileged access to flow | High | Medium |
| ZN_P00212 | Untrusted guest has privileged access to Copilot | High | Medium |
| ZN_P00214 | Untrusted member has privileged access to Copilot | High | Medium |
| ZN_P01001 | Custom connector enables custom code | Medium | High |
Rule Deletion
Rules deletion as part of deprecation process
In the October Release Notes, we announced that we would be deprecating various rules.
Please note that those rules are going to be deleted by Thursday the 23rd.
Zenity Oct-2023
⭐ Highlights
Generative AI
Low-Code/No-Code platform made it easy for citizen developers (business users) to become more efficient and productive in their work by building Apps and automation. Generative-AI is the natural extension of Low-Code/No-Code and it lowers the bar even further and makes it so simple, that now business users just need to describe what they need to build and the Platform will do it for them.
This means that citizen developers are moving further away from decision making on how the app is built and trust solely on the Gen-AI model to ensure everything is in order.
Low-Code/No-Code was already sprawling in almost every large organization, and with the introduction of Gen-AI within the platform, it becomes even harder for Admins and Security professionals to keep track on what's being built, by who, and what data is accessible.
The team at Zenity is well aware of the hyper growth of Gen-AI and it's impact on Low-Code/No-Platform, that is why we are happy to present our 1st take on Gen-AI visibility in Low-Code/No-Code platforms.
Using our the Zenity 'Inventory', customers can filter all Canvas Apps and Flows created by the Gen-AI feature in Microsoft PowerPlatform "Co-Pilot".
This provides clarity into who's using Gen-AI in the organization, which departments are using it, which users etc...Where are they utilizing it? Is it being performed for Personal productivity or being used for Production purposes? Who has access to it? Are guests in your tenant using Gen-AI to build automations and Apps? All of these questions can easily be answered using the Zenity.
Zenity is all about risk assessment, hence we added the Gen-AI filter
capabilities also to our 'Violations' page, which provides insights on
Apps and Flows and their existing risk and helps understand how they
were built.
Having this goggles in the violations page helps answer questions like, Do I have a vulnerable flow leaking data that was built by Gen-AI? Do I have An App that is shared with the entire tenant and was built by Gen-AI? Which guest users in my tenant are building Apps with sensitive data using Gen-AI? It provides a new dimension to look through when observing and assessing risk, as now you can ask & know how the resource came to be.
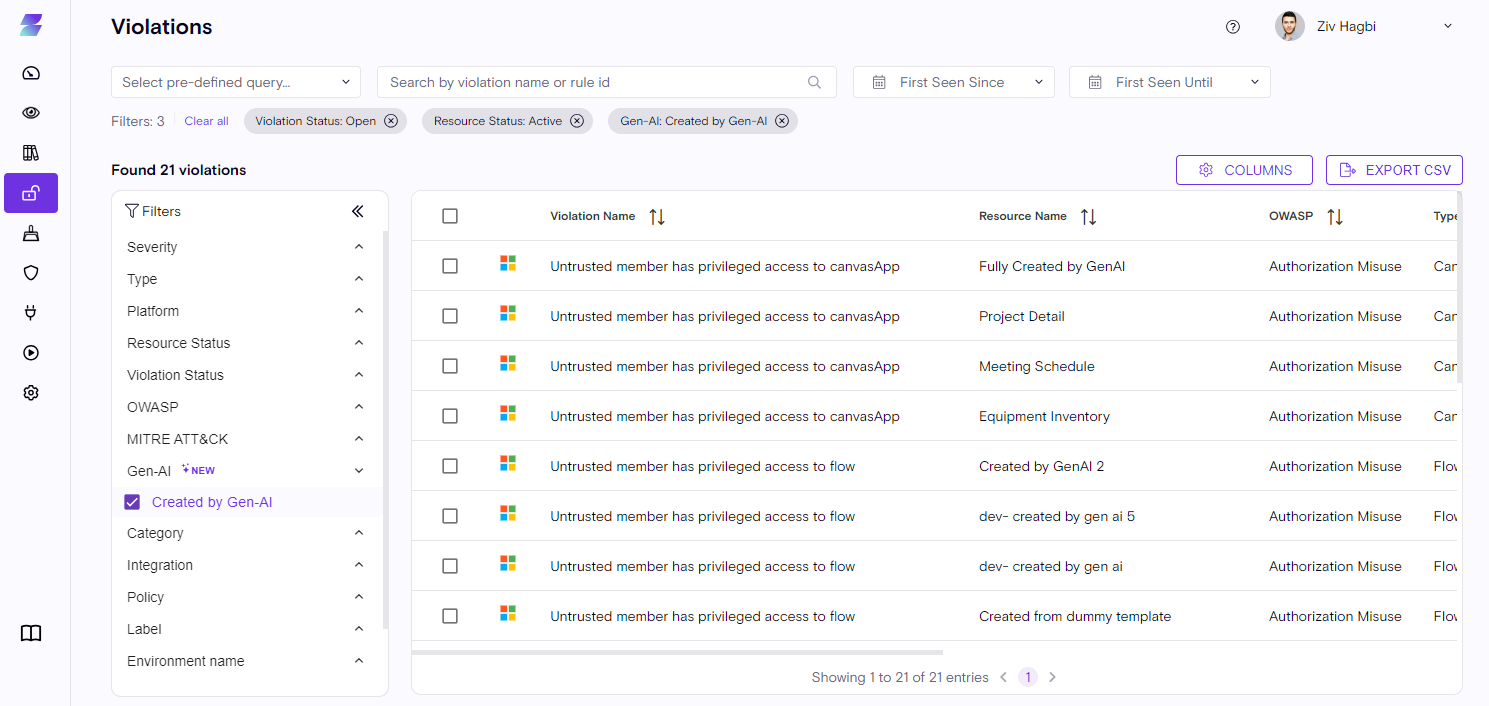
Advanced Remediation
As a part of our risk engine, Zenity can discover sensitive information (PII,PHI,PCI) leaking in plain-text for anyone to see. What should you do if you encounter this violation? Now, Zenity allows you to mask the data ad-hoc, with a new action called "Secure Flow Steps".
Now, Zenity users can use the 'Playbook' feature to enable automatic remediation of such risky scenarios. Zenity will identify sensitive information leaking and will mask it making it a win-win for all. No business interference of impact and increased security.
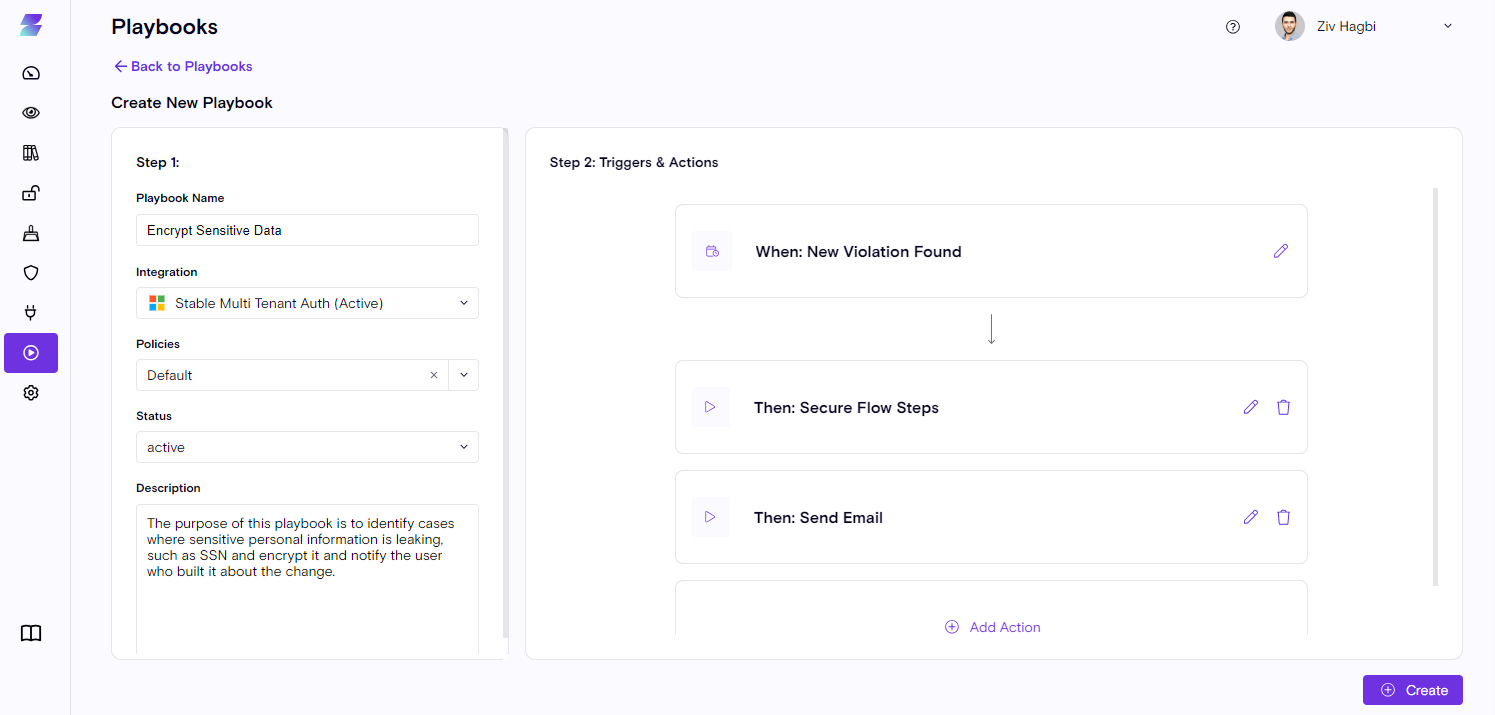
Important Update: API breaking changes
In order to enhance the user experience when working with violations and inventory resources (both API and UI) Zenity is going to better represent the Role-Based-Access-Control of Apps, Flows and Connections.
This will allow us to have better accuracy when showing the type of access a user has with Applications, Flows and Connections, specifically around the difference around Owner vs Co-Owner which are different in PowerPlatform.
In case you are using the Inventory API the inventory relation types
'canEdit' or 'editableBy' are subject to change by the end of year.
In case you are using the inventory actions API 'listResourcePermissions'
the permission type 'canEdit', will also change by the end of year.
Announcement on the actual change will take place ahead of time so customers won't have any impact.
Important Update: Rules Deprecations
Zenity is always working on enhancing and improving our rule based and risk assessment as such from time to time we will deprecate rules, either to merge them with others or if they are no longer applicable due to changes in the platform.
Here is the list of rules that we are planning to deprecate by the end of 2023.
In case you have existing playbooks or other automation using these rules, please replace them with the relevant rules below.
For any question, please contact zenity through your dedicated customer support or open a ticket to support.
| ID | Reason |
|---|---|
| ZN_P00001 | Not Applicable Anymore |
| ZN_P00011 | Replaced by ZN_P00210, ZN_P00204 |
| ZN_P00044 | Replaced by ZN_P00207, ZN_P00201 |
| ZN_P00045 | Replaced by ZN_P00206, ZN_P00200 |
| ZN_P00051 | Replaced by ZN_P00208, ZN_P00202 |
| ZN_P00052 | Replaced by ZN_P00209, ZN_P00203 |
| ZN_P00010 | Replaced by ZN_P00210, ZN_P00204 |
| ZN_P00043 | Replaced by ZN_P00200 |
| ZN_P00047 | Replaced by ZN_P00201 |
| ZN_P00049 | Replaced by ZN_P00202 |
| ZN_P00050 | Replaced by ZN_P00203 |
| ZN_P00053 | Replaced by ZN_P00200, ZN_P00206 |
| ZN_P00054 | Replaced by ZN_P00201, ZN_P00207 |
| ZN_P00055 | Replaced by ZN_P00202, ZN_P00208 |
| ZN_P00056 | Replaced by ZN_P00203, ZN_P00209 |
| ZN_P00004 | Replaced by the 'Custom Connector' Filter in the Inventory and Playbook Trigger |
| ZN_P00088 | Replaced by ZN_P00097 |
Zenity Sep-2023
⭐ Highlights
Endpoint Filtering
Low-Code/No-Code Applications and Automation are highly customizable and can have dozens of data interfaces, such as HTTP or SQL etc... How can security professionals ensure an Automation doesn't communicate with a malicious endpoint, for example a C&C server exposing the company to malware?
How can we help place guardrails and allow users to freely use the extensibility power that Low-Code/No-Code offers without losing sight of what's been used and how?
Zenity now launches the 1st version of our Endpoint filtering which will allow Platform admins and Security Professional to set the boundaries by configuring an HTTP/HTTPs Allowed list.
Any activity outside of the allowed list will result in a violation, search for ZN_P00123 - "[Flow is communicating with disallowed endpoints (Preview)to view violating flows.
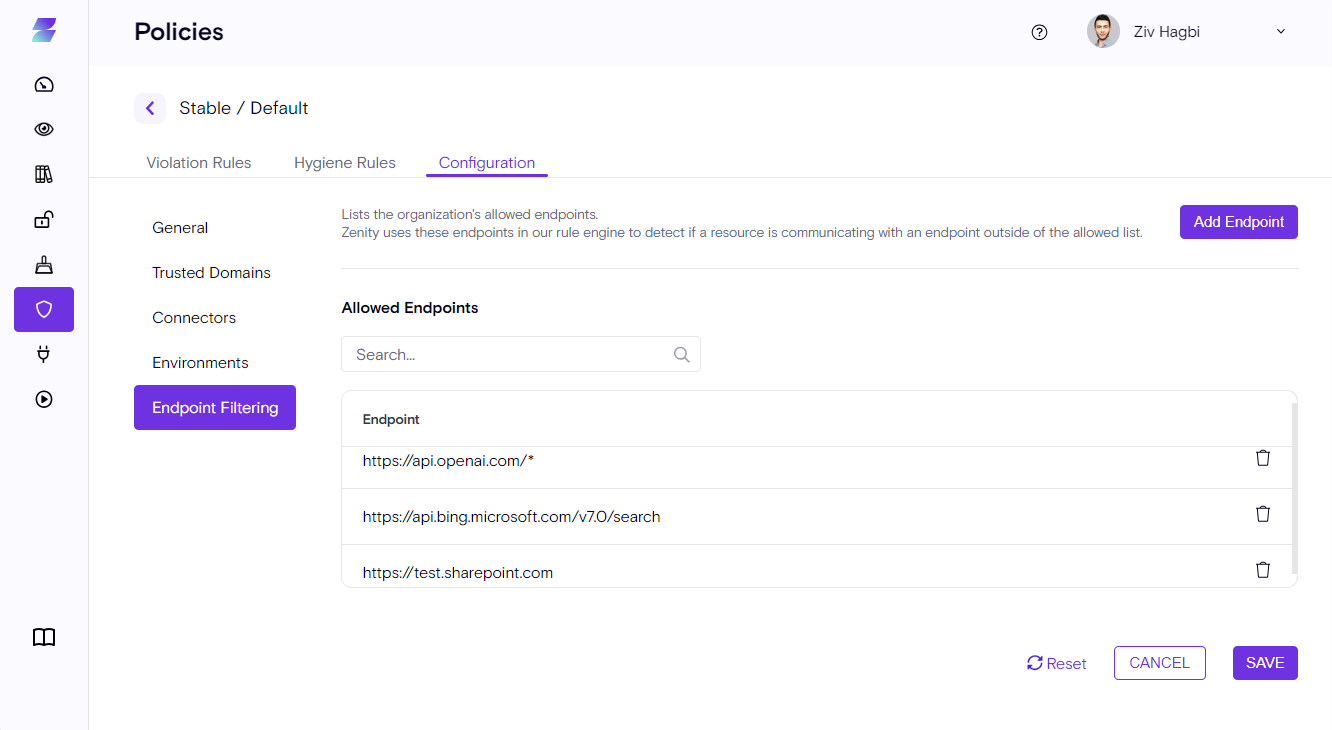
Read more about it in our docs center.
Advanced Remediation
As a part of our risk engine, Zenity can discover sensitive information (PII,PHI,PCI) leaking in plain-text for anyone to see. What should you do if you encounter this violation? Now, Zenity allows you to mask the data ad-hoc, with a new action called "Secure Flow Steps".
As per the action's intent it will be available when sensitive data is found, Zenity users can correlate this to the below rules:
- ZN_P00121 - PHI sensitive data handled by a flow (Preview)
- ZN_P00117 - PII sensitive data handled by a flow (Preview)
- ZN_P00099 - PCI sensitive data handled by a flow
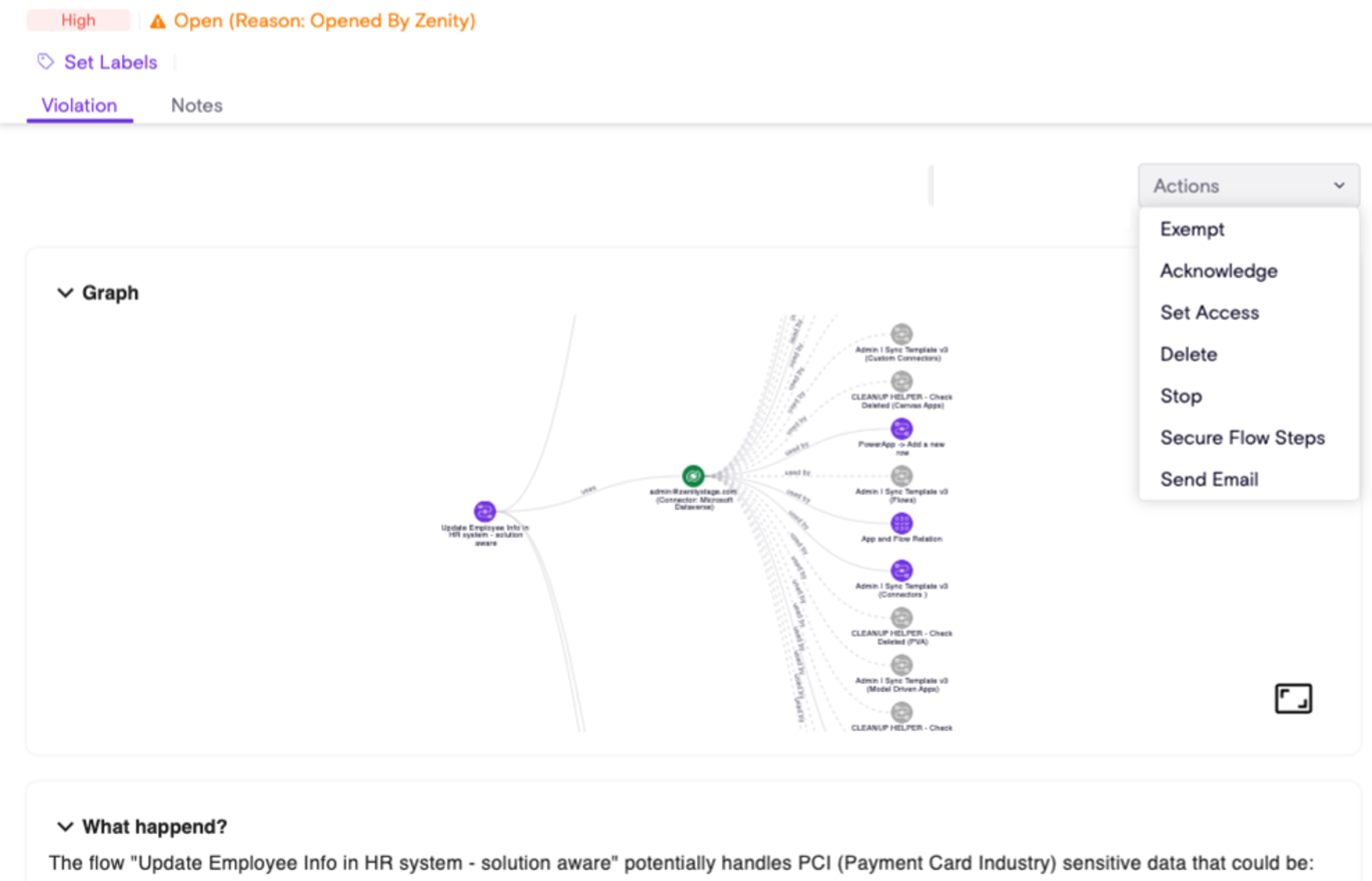
The action currently supports solution aware flows (meaning flows created within a solution).
The action masks the sensitive data in the logs by enabling the 'Secure Input/Output' configuration in PowerAutomate only for the violating steps in the flow.
Customers can use our API today to handle sensitive data exposure by enumerating through all relevant violations and invoking the new action. This will ensure that the sensitive data is protected and hidden.
Known Limitation - The action supports only solution-aware flows at this point.
Reauthenticating an Integration
Integration status can change due to numerous changes on the customer side, up until now, customer had to edit the integration settings to reauthenticate it. In the effort of make it easier for permissions changes to take effect we have introduced a 'Retry' button, used in cases when the Integration 'Failed' (presented through the Integration status)
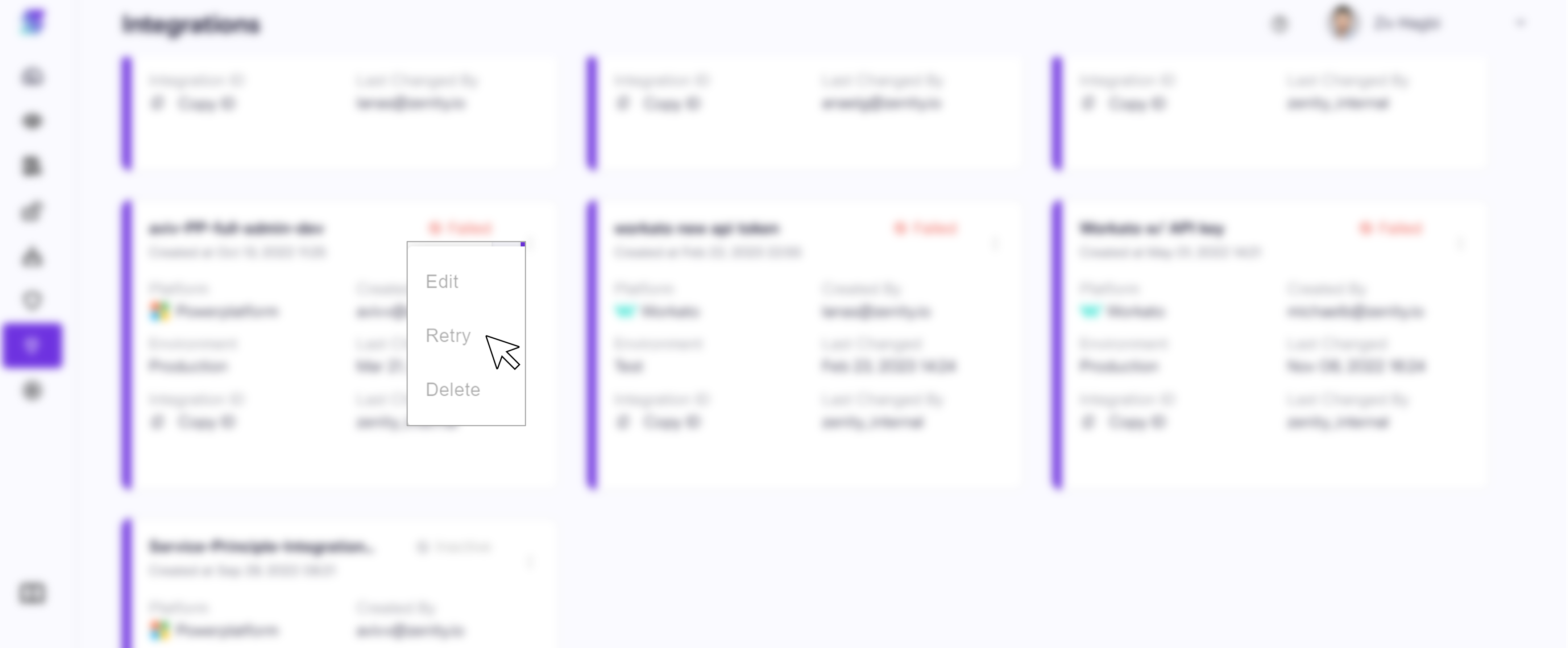
Important Update: Simplifying Zenity Rules Names
On October 4th, we are introducing a change to the naming convention of some of the Zenity rules. This change is part of our ongoing efforts to make our platform more intuitive and user-friendly, and you can find all the updated rule names in the below table.
| Rule IDs | Old Title | New Title |
|---|---|---|
| ZN_P00001 | Use of out-of-tenant user identity | Connection is using an account outside the corporate tenant |
| ZN_P00003 | Use of user account instead of service account | Connection is using a non-service account |
| ZN_P00004 | Custom connector | Connection is using an unofficial, uncertified connector |
| ZN_P00005 | Flow is triggered by a webhook | Flow is accessible by anyone with a link via a webhook |
| ZN_P00009 | Flow should not have more than the allowed number of makers | Flow has more than the allowed number of makers |
| ZN_P00010 | Out-of-tenant account (guest user) with privileged access to flow | Flow is accessible by an account outside the corporate tenant (privileged access) |
| ZN_P00011 | Personal account with privileged access to flow | Flow is accessible by a personal account (privileged access) |
| ZN_P00013 | A combination of cloud business data with high-risk connectors | Flow is bridging business data and high-risk connector |
| ZN_P00014 | A combination of cloud business data with unmanaged cloud endpoint | Flow is bridging business data and unmanaged cloud endpoint connector |
| ZN_P00015 | A combination of cloud with on-prem | Flow is bridging business data and on-prem connector |
| ZN_P00016 | On-premise connection | Connection is using an on-prem connector |
| ZN_P00017 | Connection with deprecated underlying connector | Connection is using a deprecated connector |
| ZN_P00020 | Unconfigured host key fingerprint | Connection has no host key fingerprint |
| ZN_P00024 | Salesforce environment mismatch | PowerPlatform & Salesforce Suspicous Environment Mismatch |
| ZN_P00025 | Suspicious SFTP port | Connection is using a non-standard port |
| ZN_P00027 | Stale connection (Deprecated) | Connection is stale (Deprecated) |
| ZN_P00028 | Environment CDS instance is disabled | Environment has no CDS instance |
| ZN_P00029 | Connection to a CDS database outside of the environment | Flow is bridging two environments |
| ZN_P00030 | An non-default environment accessible to all users | Non-default Environment is accessible by all users |
| ZN_P00031 | Use of customer-managed encryption key | Environment is using a non-Microsoft managed key |
| ZN_P00032 | Insecure communication | Connection enables insecure, unencrypted communication |
| ZN_P00033 | An environment not protected by a DLP policy | Environment has no DLP policy |
| ZN_P00035 | Use of custom JavaScript in webpage | Portal is using custom code (Javascript) |
| ZN_P00036 | A combination of communication systems with high-risk connector | Flow is using communication and a high-risk connector |
| ZN_P00037 | A combination of communication systems with unmanaged cloud endpoint | Flow is using communication and an unmanaged cloud endpoint |
| ZN_P00038 | A combination of on-prem with high-risk connectors | Flow is using on-prem and a high-risk connector |
| ZN_P00039 | A combination of on-prem with social media platform | Flow is using on-prem and social media |
| ZN_P00040 | A combination of on-prem with unmanaged cloud endpoint | Flow is using on-prem and unmanaged cloud endpoint |
| ZN_P00041 | A combination of cloud business data with social media platform | Flow is using business data and social media |
| ZN_P00043 | Out-of-tenant account (guest user) with privileged access to connection | Connection is accessible by a guest account (privileged access) |
| ZN_P00044 | Personal account with reader access to connection | Connection is accessible by a personal account (unprivileged access) |
| ZN_P00045 | Personal account with privileged access to connection | Connection is accessible by a personal account (privileged access) |
| ZN_P00046 | Org-wide access to connection | Connection is accessible by the entire tenant |
| ZN_P00047 | Out-of-tenant account (guest user) with reader access to connection | Connection is accessible by a guest account (unprivileged access) |
| ZN_P00048 | Org-wide access to canvasApp | CanvasApp is accessible by the entire tenant |
| ZN_P00049 | Out-of-tenant account (guest user) with privileged access to canvasApp | CanvasApp is accessible by a guest account (privileged access) |
| ZN_P00050 | Out-of-tenant account (guest user) with reader access to canvasApp | CanvasApp is accessible by a guest account (unprivileged access) |
| ZN_P00051 | Personal account with privileged access to canvasApp | CanvasApp is accessible by a personal account (privileged access) |
| ZN_P00052 | Personal account with privileged reader to canvasApp | CanvasApp is accessible by a personal account (unprivileged access) |
| ZN_P00053 | An account outside of the corporate domain with privileged access to connection | Connection is accessible by an account outside the corporate domain (privileged access) |
| ZN_P00054 | An account outside of the corporate domain with reader access to connection | Connection is accessible by an account outside the corporate domain (unprivileged access) |
| ZN_P00055 | An account outside of the corporate domain with privileged access to canvasApp | CanvasApp is accessible by an account outside the allowed domains (privileged access) |
| ZN_P00056 | An account outside of the corporate domain with reader access to canvasApp | CanvasApp is accessible by an account outside the allowed domains (unprivileged access) |
| ZN_P00057 | Use of custom CSS in webpage | Portal App is using custom code (CSS) |
| ZN_P00058 | Use of deprecated authentication method | Connection is using a deprecated authentication method |
| ZN_P00060 | Stale canvasApp (Deprecated) | CanvasApp is stale (Deprecated) |
| ZN_P00061 | New environment created | Environment is recently created |
| ZN_P00062 | The Canvas App has no valid owners or editors | CanvasApp has no valid owners or editors |
| ZN_P00063 | The flow has no valid owners or editors | Flow has no valid owners or editors |
| ZN_P00064 | Stale flow | Flow is stale |
| ZN_P00065 | The connection has no valid owners | Connection has no valid owners |
| ZN_P00067 | Environment has no valid admins | Environment has no valid admins |
| ZN_P00069 | Potential exposure of sensitive data in flow logs | Flow is potentially exposing sensitive data in logs |
| ZN_P00070 | Potential IDOR | Flow is using a potentially vulnerable trigger (IDOR) |
| ZN_P00072 | A public API exposed via portal apps allows anonymous access to dataverse tables | Dataverse table is accessible by any user (including anonymous) |
| ZN_P00074 | Critical number of privileged users in the environment | Environment has too many privileged users |
| ZN_P00075 | High number of privileged users in the environment | Environment has many privileged users |
| ZN_P00076 | Portal app local sign-in enabled | Portal enables local sign-in |
| ZN_P00077 | A flow is using arbitrary SQL queries | Flow is using arbitrary SQL queries |
| ZN_P00078 | Custom code enabled in custom connector | Custom connector enables custom code |
| ZN_P00079 | Plaintext HTTP communication with custom connector | Custom connector is using insecure HTTP |
| ZN_P00080 | Custom connector missing authentication | Custom connector has no authentication method configured |
| ZN_P00081 | External account connection in developer environment | Developer Environment is accessible by more than just the developer |
| ZN_P00082 | Unsafe throttling settings in portal | Portal has unsafe throttling settings |
| ZN_P00086 | Potential hard coded secret in flow | Flow is using a potentially hard-coded secret (dynamic input for sensitive parameters) |
| ZN_P00087 | Portal app allows sign-in using untrusted identity provider | Portal enables untrusted sign-in (untrusted identity provided) |
| ZN_P00088 | HTTP step without authentication method | Flow is using an unauthenticated HTTP virtual connector |
| ZN_P00089 | Environment PCF is enabled | Environment enables PCF in apps |
| ZN_P00090 | Dataverse auditing is disabled | Environment disables Dataverse auditing |
| ZN_P00091 | CanvasApp with custom code component (PCF) | CanvasApp is using a 3rd-party PCF component |
| ZN_P00092 | Sensitive data hard-coded in a flow | Flow is handling potentially sensitive data (Credit card numbers) |
| ZN_P00094 | DLP enforcement failure | Flow is using connectors which are bypassing the DLP policy |
| ZN_P00095 | Flow has an insecure Azure Key Vault step (Preview) | Flow has an insecure Azure Key Vault step (Preview) |
| ZN_P00097 | Hard coded secret in flow step (Preview) | Flow has hard-coded secrets (Preview) |
| ZN_P00099 | PCI sensitive data handled by a flow | Flow is handling potentially sensitive data (PCI - Payment Card Industry) |
| ZN_P00101 | Risky business data connector (Preview) | DLP policy enables risky connectors (Preview) |
| ZN_P00102 | Connection might be implicitly shared (Preview) | Connection is using a sharable authentication method (Preview) |
| ZN_P00103 | Flow runs log expose sensitive data (Preview) | Flow is exposing sensitive data in logs (Preview) |
| ZN_P00104 | Stale environment (Preview) | Non-production environment is empty (Preview) |
| ZN_P00105 | Connection to an account outside of the corporate domain (Preview) | Connection is configured using an account outside the corporate domain (Preview) |
| ZN_P00106 | Unblockable connector configured in DLP policy | DLP policy has unblockable connectors |
| ZN_P00107 | Connection using the OpenAI connector | Connection is using an OpenAI connector |
| ZN_P00108 | Flow trigger exposes sensitive data (Preview) | Flow is exposing sensitive data in logs (via flow trigger) (Preview) |
| ZN_P00110 | Custom connector is using OpenAI API | Custom connector is using OpenAI API |
| ZN_P00111 | Guest user with access to tenant resources (Preview) | Tenant resource is accessible by an external user (Preview) |
| ZN_P00112 | Flow has an insecure sensitive step (Preview) | Flow has an insecure sensitive step (Preview) |
| ZN_P00114 | Suspicious hostname | Connection is using a suspicious domain name |
| ZN_P00115 | Flow is using OpenAI API via HTTP | Flow is connecting to the OpenAI API via HTTP |
| ZN_P00116 | Vulnerable gateway version | Gateway is vulnerable |
| ZN_P00117 | PII sensitive data handled by a flow (Preview) | Flow is handling potentially sensitive data (PII - Personally Identifiable Information) (Preview) |
| ZN_P00118 | Non-admins can create and manage production environments | Tenant settings allow non-admin users to manage production environments |
| ZN_P00119 | Copilot feature is enabled | Tenant settings enable Copilot |
| ZN_P00120 | Implicitly shared embedded connection in flow | Flow has an implicitly shared embedded connection |
| ZN_P00121 | PHI sensitive data handled by a flow (Preview) | Flow is handling potentially sensitive data (PHI - Protected Health Information) (Preview) |
While the rule names are changing, please note that the underlying
functionality remains unchanged.
If you have any questions or would
like any clarification or assistance, please feel free to reach out
directly to our customer success, contact the support team at support@zenity.io or through our ticketing system.
No user action is required
Zenity Aug-2023
⭐ Highlights
SBOM (Software Bill of Materials) for Low-Code/No-Code Applications
Business & Pro users need more customization and advanced use-cases which in many times involve using classic code within the Low-Code/No-Code platform. In such cases users can code from scratch or import code components from different and untrusted sources, without any validation.
Once that code is imported, who is checking it? Who validates the components? A user can easily import a piece of code using a vulnerable JS library, without even knowing the organization is now exploitable.
Zenity is here to help with the 1st Supply Chain solution for Low-Code/No-Code platforms. Zenity covers SBOM for Canvas Apps, the most used App in PowerPlatform. Using our Manual Action or API customers can easily generate SBOM files. The Zenity SBOM inspection mechanism dives deep into every code component and deduces which code libraries were used for the app.
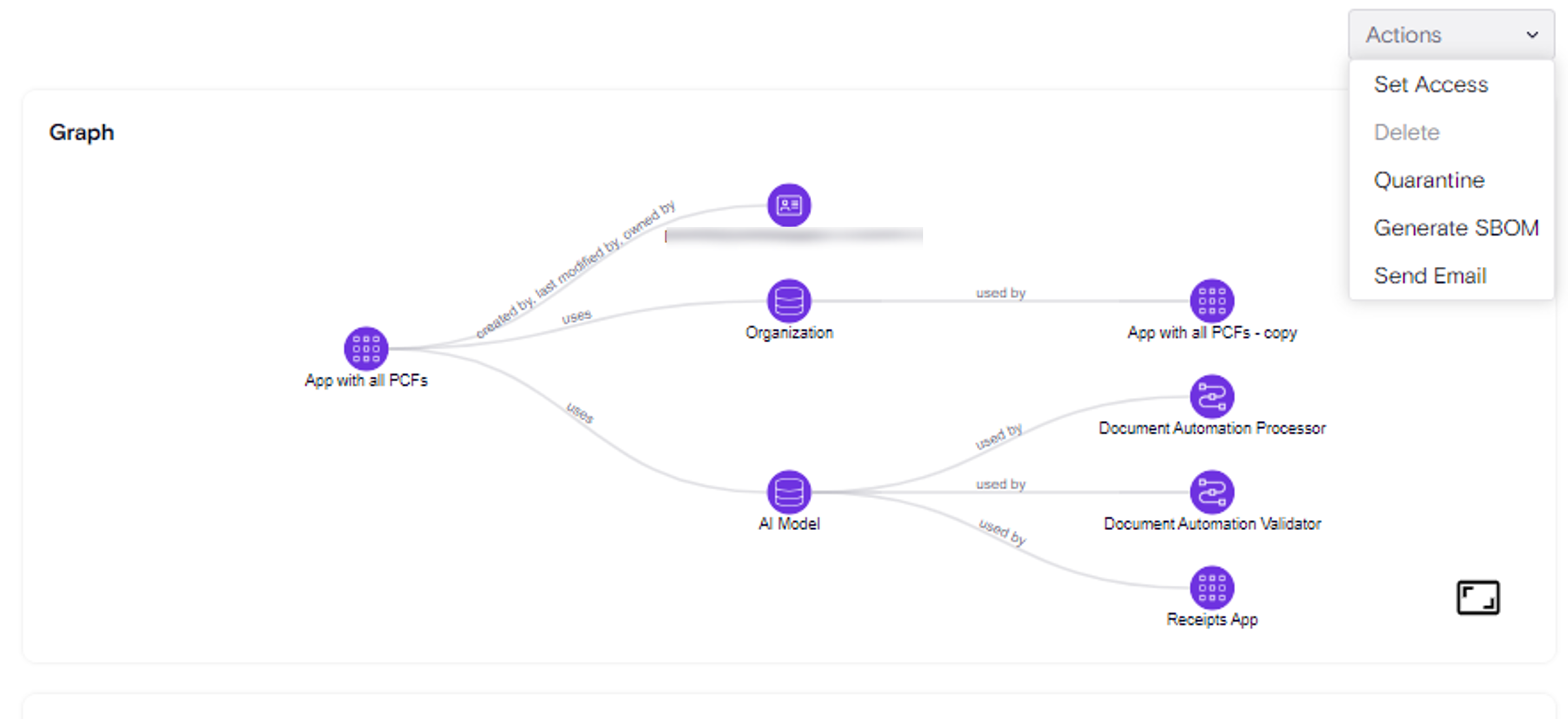
SBOM File Samples
Admin Error Notifications
It's imperative that Zenity Administrators be notified in a timely manner when there are errors in different parts of the platform as they need to take action accordingly.
Now, Zenity admins will receive email notifications for the following scenarios:
-
Integration failures
-
Real-time email notification as the Integration is the sole access point to provide Visibility, Risk assessment and Governance within Zenity.
-
Daily failure report summarizing all failing integrations (complementary to the ad-hoc email)
-
Playbook failures
-
Daily failure reports provide visibility into which playbooks failure occurred to enable admins to assess the failures and re-run the actions if needed.
Dataverse Tables Support
In Zenity we highly believe in the notion of 'you can't protect what you can't see', hence we are constantly expanding our inventory capabilities. In this release we are introducing 'Dataverse Tables' . Now, customers can easily view any DV tables get information about the table and also view which applications and automations are using it.
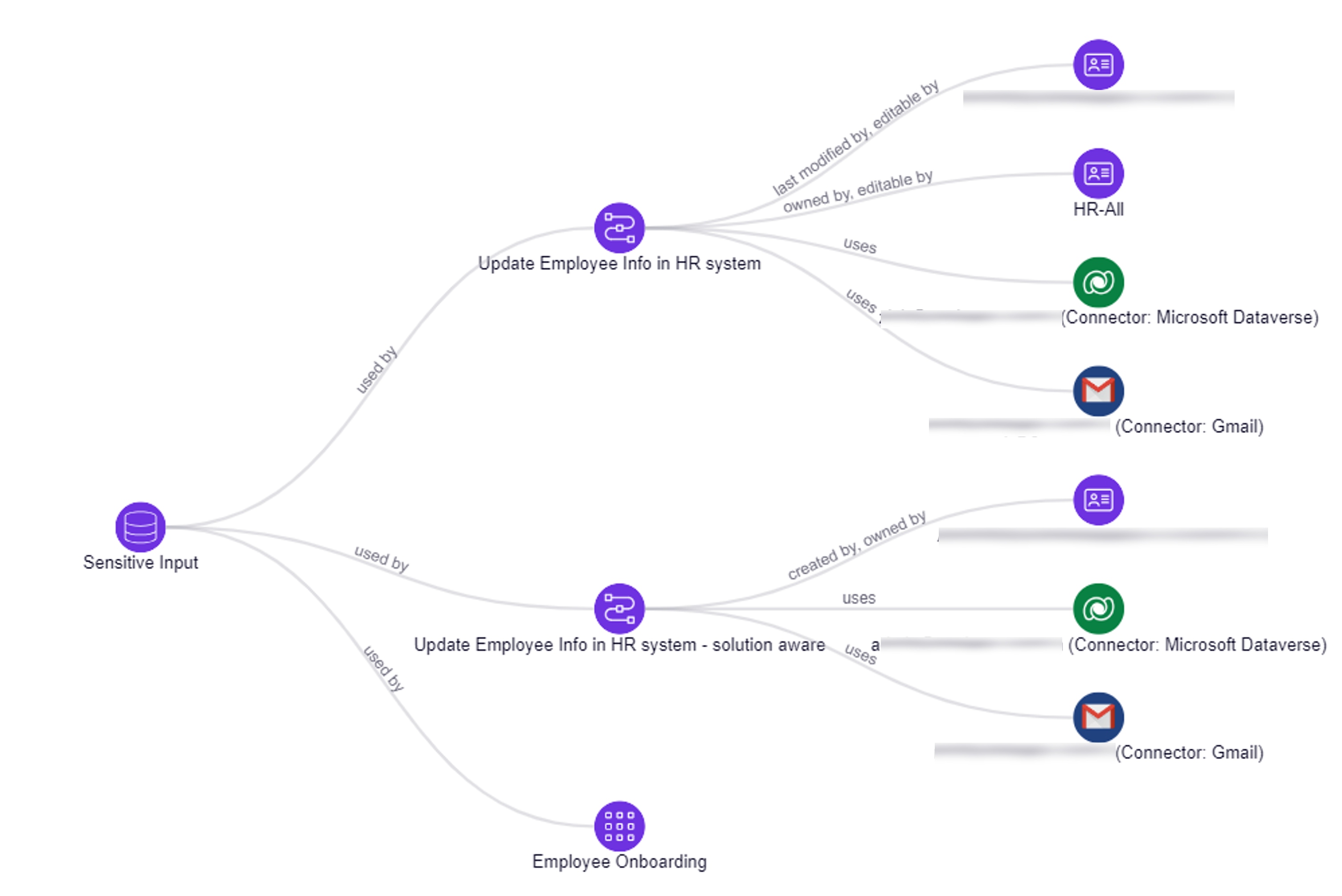
App & Flow insights
In addition to Dataverse tables, we are now providing insights into how Apps and Flows interact with one another, both are visible through both the Attack Graph and the Resource Relations.
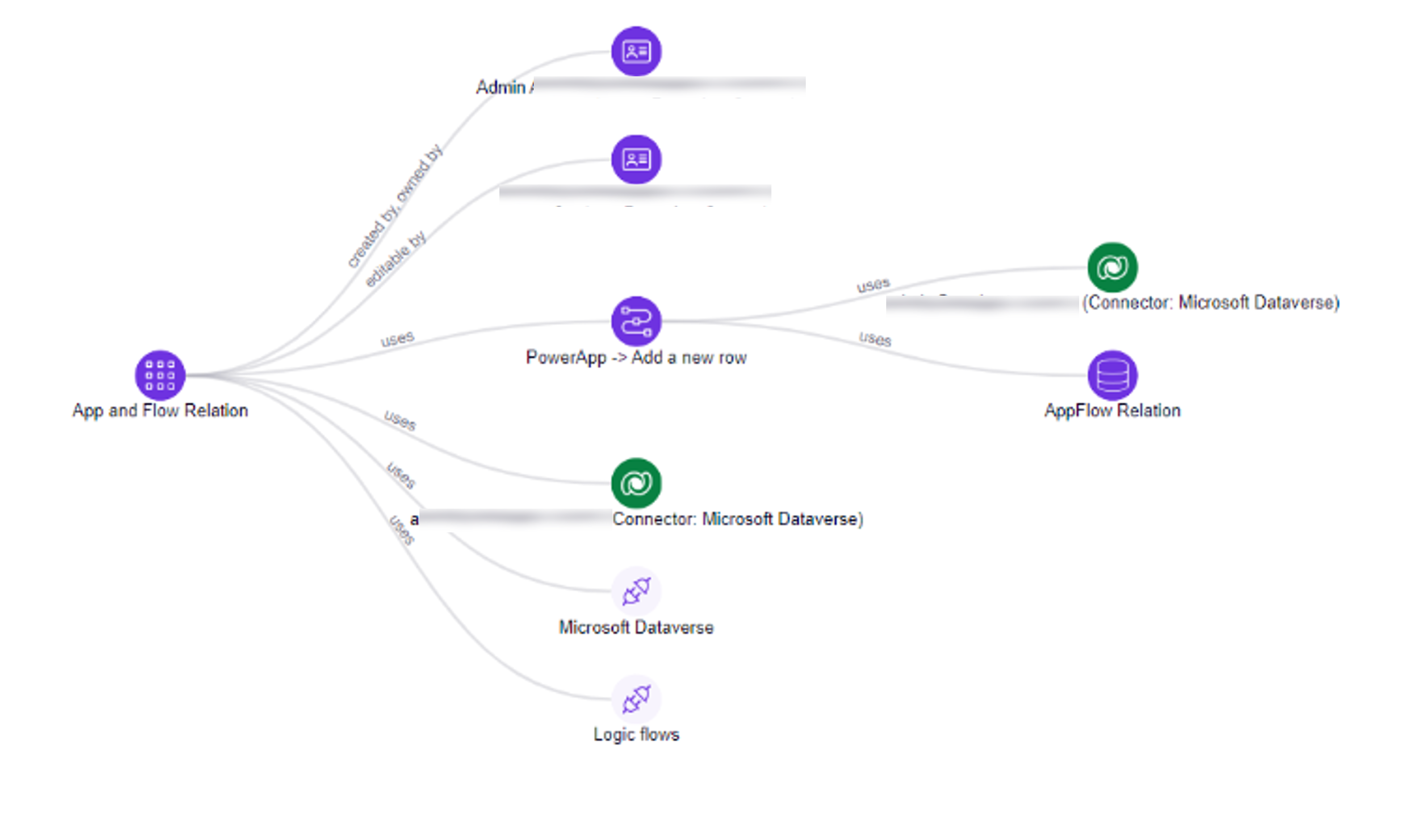
New Remediation Actions
Zenity provides security across the OWASP Top 10, privileged access is one of the keys for securing ang governing your Low-Code/No-Code platform. Zenity can detect all sorts of privileged access, may it be privileged guest access or excessive access to a critical app or even organization wide access.
In order to remediate this issue security professional and Platform admins can now use the new 'Set Access' action to view the entire role based access control of a Canvas App or a Flow and Add / Remove access according to their needs.
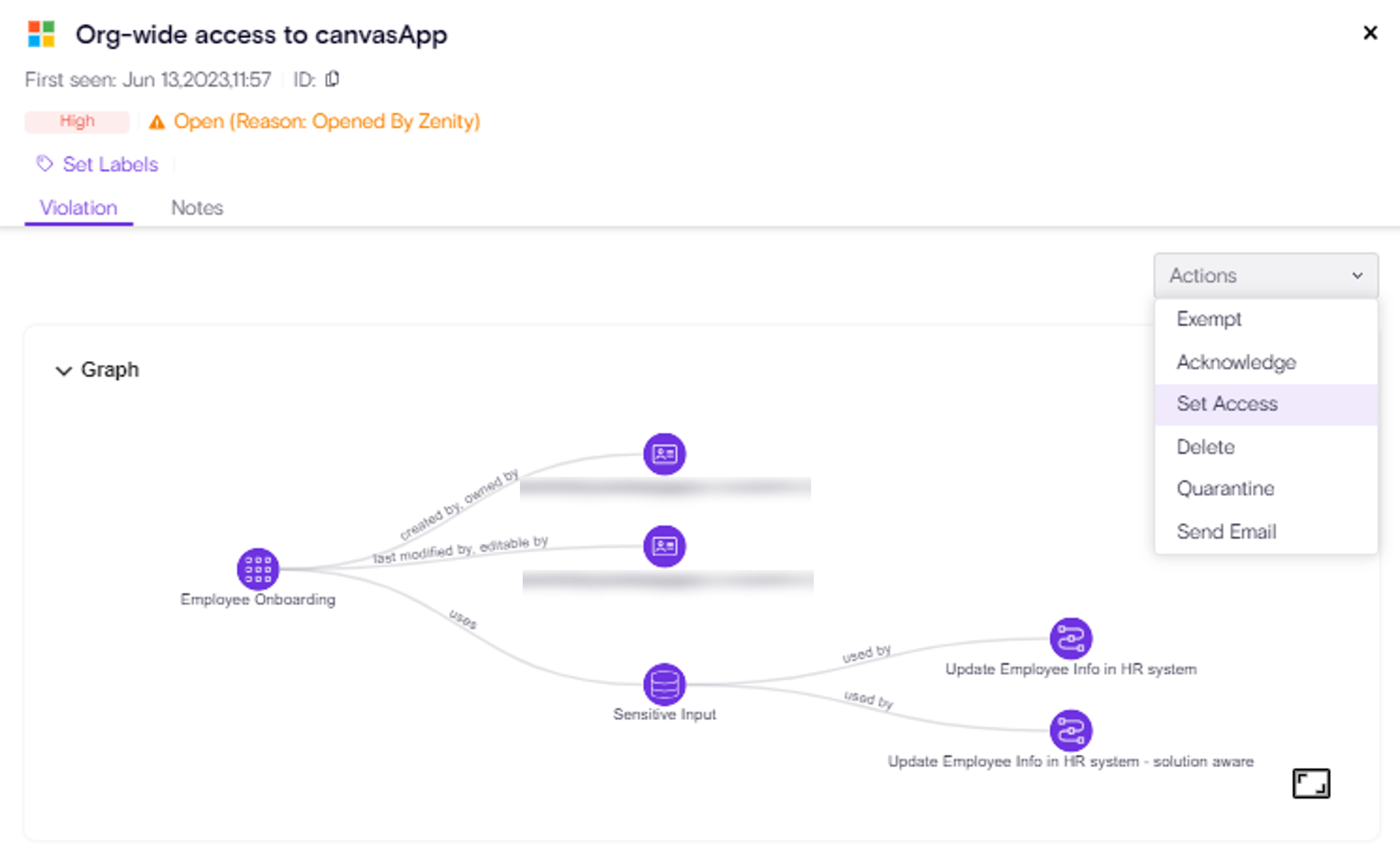
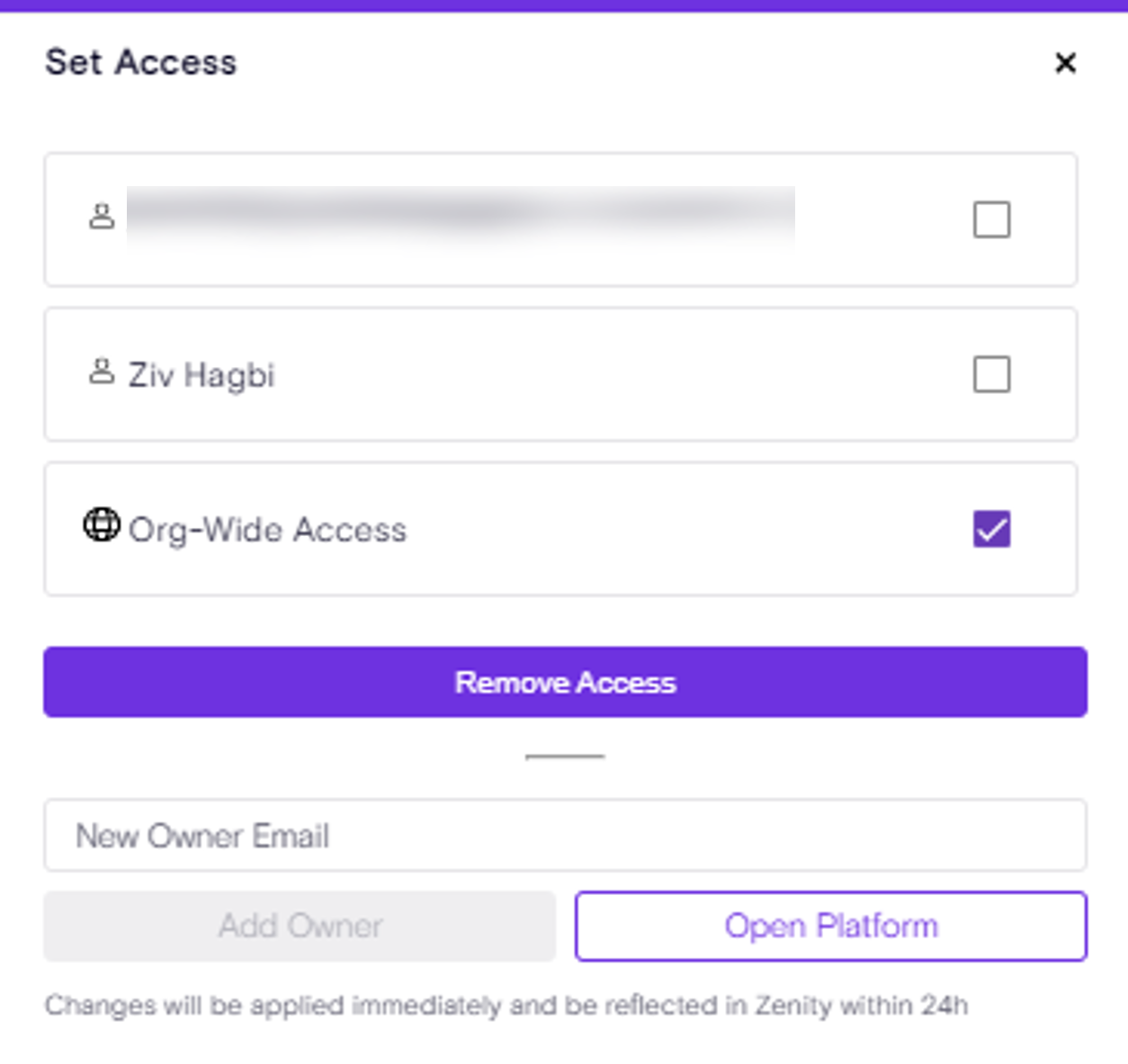
Zenity July-2023
⭐ Highlights
Enhanced Webhook Support
Zenity's ability to engage with the security ecosystem our customers are using is crucial factor in our joint success. To address our customers needs to integrate seamlessly with 3rd party services, customers can use the Zenity Webhook that now contains more relevant data than ever.
Zenity has aligned the API and Webhook so when customers are exporting violations and even resource information from Zenity through Webhook, they get all the information they need, including our findings, knowledge base, remediation path and more.
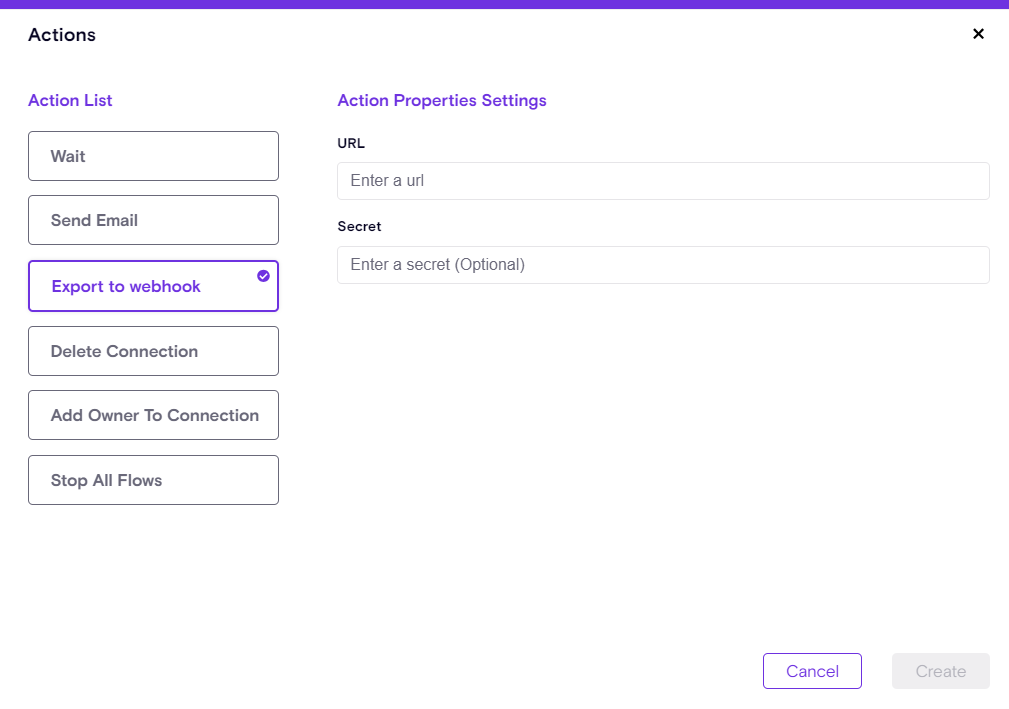
Labels
In Zenity we always strive for accuracy and simplicity in our violations.
Now, team members can provide a clear indication to other team members when a violation is under investigation using the new "Under Review" label.
Labels have supported filters as well and are represented on the main violation table.
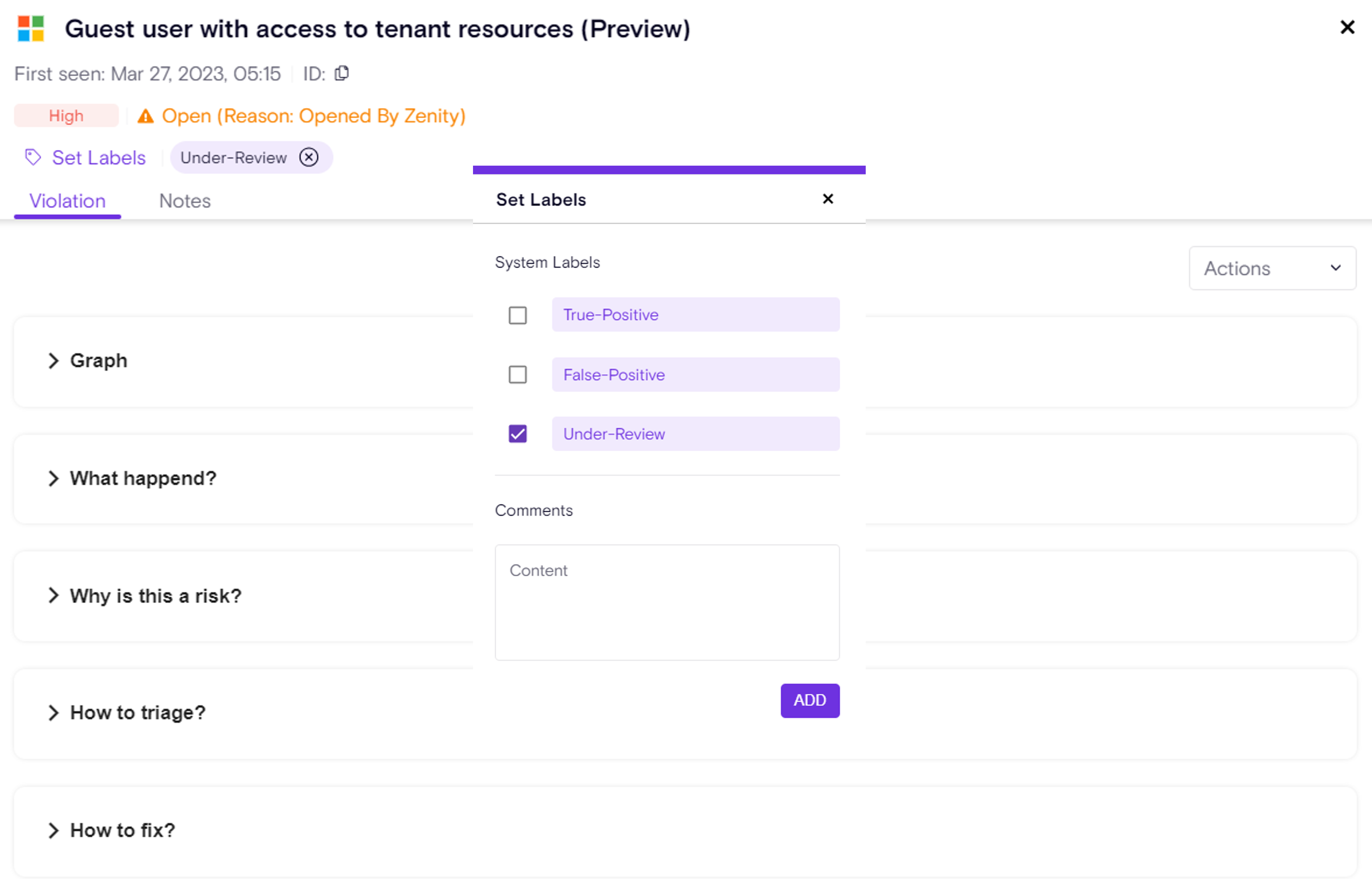
Custom Departments
Low-Code/No-Code is spreading throughout the business across many different departments, Zenity can help you visualize both the low-code/no-code adoption and risk assessment based on user department. As different customers can configure the concept of 'Department' differently in AAD, Zenity now support custom departments for our customers to configure through our support channel.
New & Improved Violation Rules (a full description can be found in the Zenity policy page)
-
ZN_P00091 - CanvasApp with custom code component (PCF)
-
Rule improvement - Zenity now collects all types of PCFs, including OpenSource PCFs imported into your environment from the internet.
-
ZN_P00121 - PHI sensitive data handled by a flow (Preview)
-
Zenity now detects when personal health information is exposed similar to PII and PCI.
-
ZN_P00120 - Implicitly shared embedded connection in flow (Preview)
-
Zenity detects when flows can be triggered by different users other than the original maker's on his behalf using his credentials, basically impersonating as the person who created the flow and using his data connections.
Deprecated rules
ZN_P00027 - Stale Connection
- This rule is going to be deprecated soon and will be replaced with a new and improved rule.
API Support
- Full support for all new features both in API and UI
Zenity June-2023
⭐ Highlights
Labels
In Zenity we always strive for accuracy and simplicity in our violations.
Now, customers can provide an "Analyst Verdict" and mark the violation as "True-Positive" or "False-Positive" using our Labels. Labels have supported filters as well, and are represented on the main violation table.
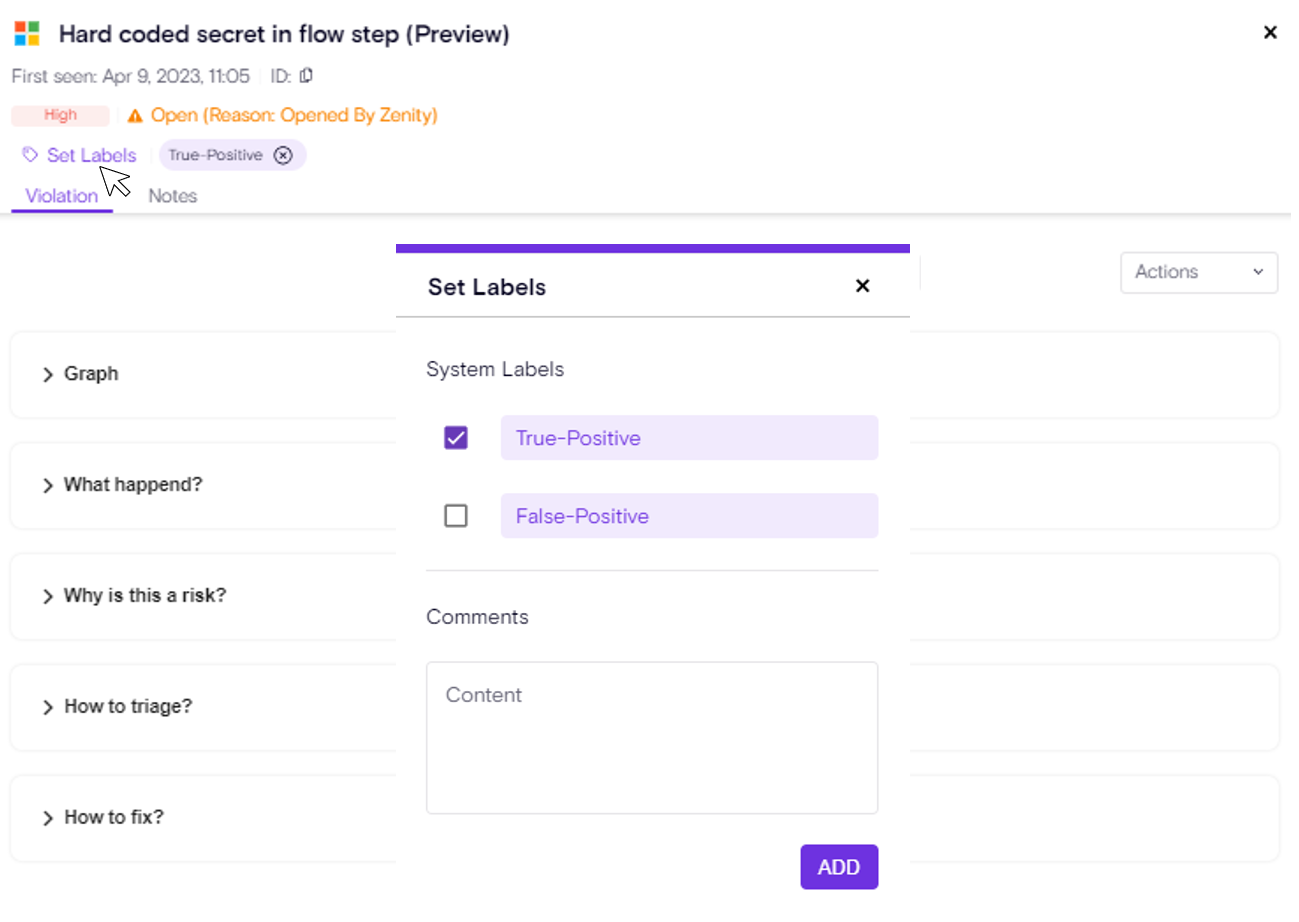
New Resource Playbook Trigger
Security and Oversight of one's environment is crucial to manage risk at scale. But how can you make sure you are on top of all resources being created by business users? Zenity now facilitate this process by allowing you to trigger a playbook everytime a new resource is found.
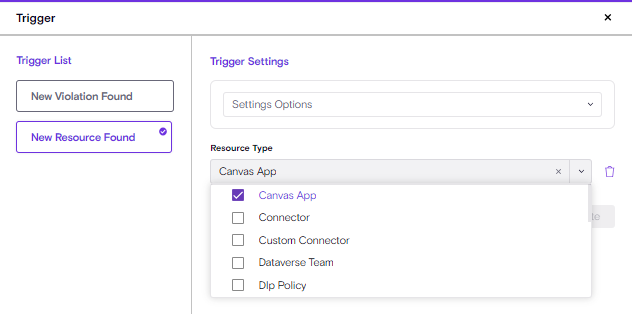
The new trigger opens a new governance dimension as now admins and AppSec team have oversight over resources being built across the business.
In this example, a simple use-case from one customer was to add a Service Account as a co-owner to every new Canvas App, this is now available with Zenity.
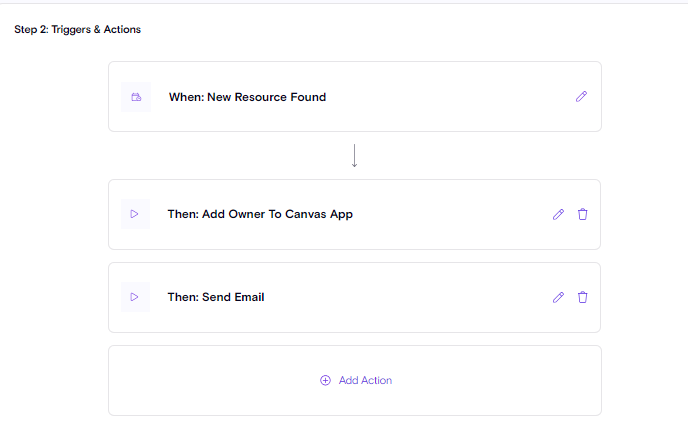
In this example, Zenity identifies that a new Canvas App in PowerPlatform was created, it then adds the relevant ServiceAccount as a co-owner to the app (allowing the team to have full visibility into what's being built) and then sends an email to the maker of the app notifying them about the process.
New PowerPlatform Multi-Tenant Integration
Zenity provides different methods of authentication for PowerPlatform. In order to make the initial setup as simple as possible for customers Zenity now supports a multi-tenant integration which means Zenity does all the configuration and the customer simply needs to consent to his AAD tenant.
For more information, please review the full documentation, here.
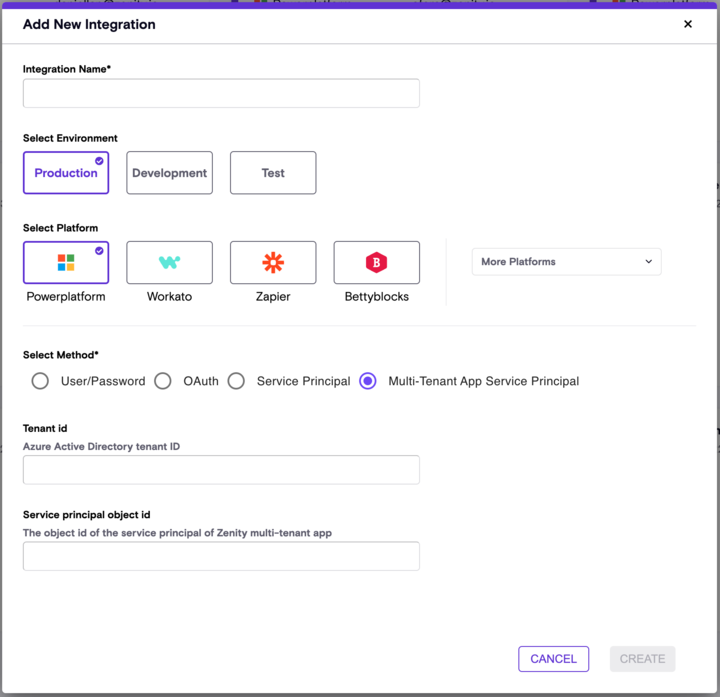
Enhanced Playbooks using 'Wait' duration
Zenity now supports 'Wait' as a condition for a playbook to execute.
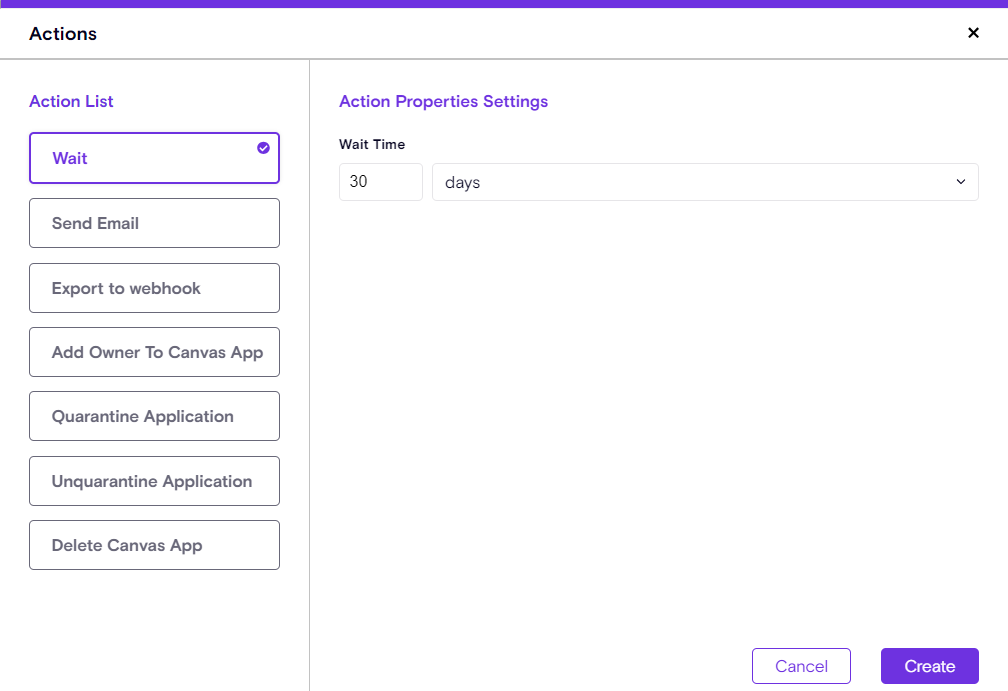
Users can invoke playbooks and add 'Wait' periods to handle cases where the end-user may need sufficient time to act and fix an issue before the team escalates the issue or mitigate it automatically.
In this playbook, Zenity covers an oversharing use-case where a canvas app is shared with the entire organization (including guest users).
Zenity identifies the violations and sends an email to the maker of this applications, then wait for 30 days, if the violation still persists sends another email and waits for 30 more days, after which if the violation still persists quarantine the App and notify the maker and the Admin.
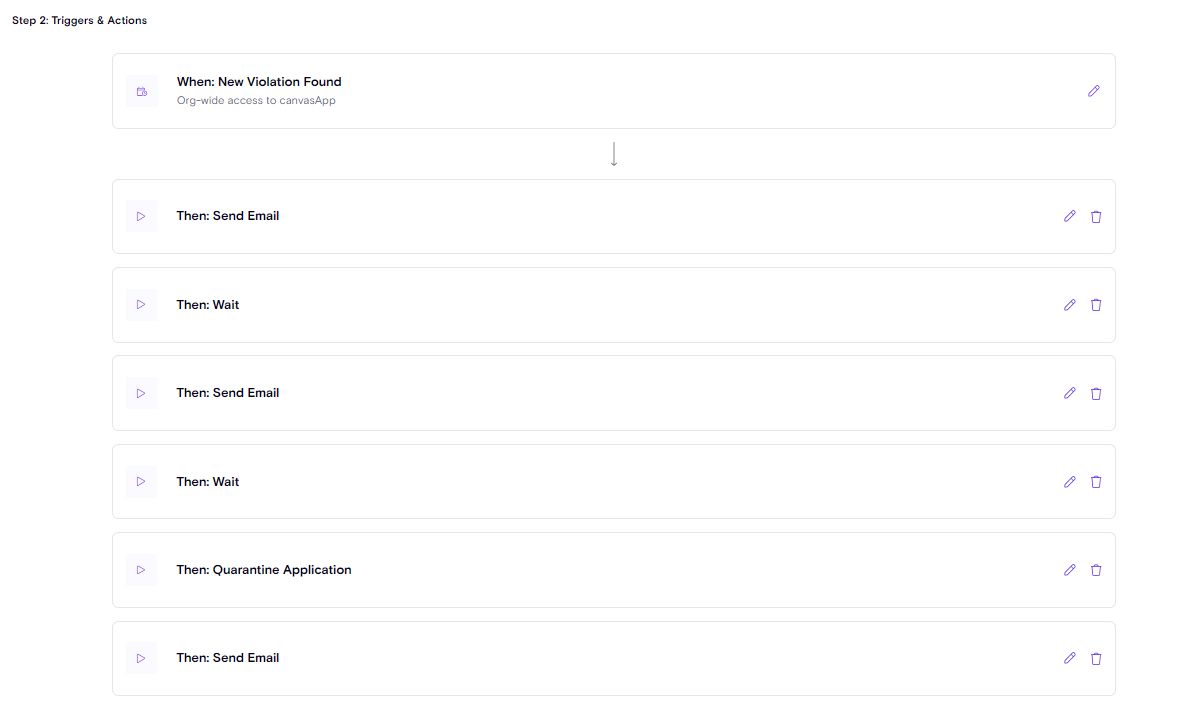
New Violation Rules (a full description can be found in the Zenity policy page)
-
ZN_P00117 - PII sensitive data handled by a flow (Preview)
-
ZN_P00118 - Non-admins can create and manage production environments
-
ZN_P00119- Copilot feature is enabled
API Support
- Full support for all new features both in API and UI
Zenity April-2023
⭐ Highlights
Attack Graph
-
In Zenity we always strive to simplify the complexity of Low-Code/No-Code security, to make it easier for our users to focus on what's critical for them and to be able to understand and remediate issues with full context.
-
Harnessing the power of the Zenity Inventory we modeled the entire LCNC platform and are now visualizing the risk and its impact.
-
Customers can see how different resources relate to one another and understand quickly the magnitude of the issue, without having to browse through the inventory multiple times.
-
The graph is also available through the Inventory where you can explore resources and how they relate to other resources instead of using the table.
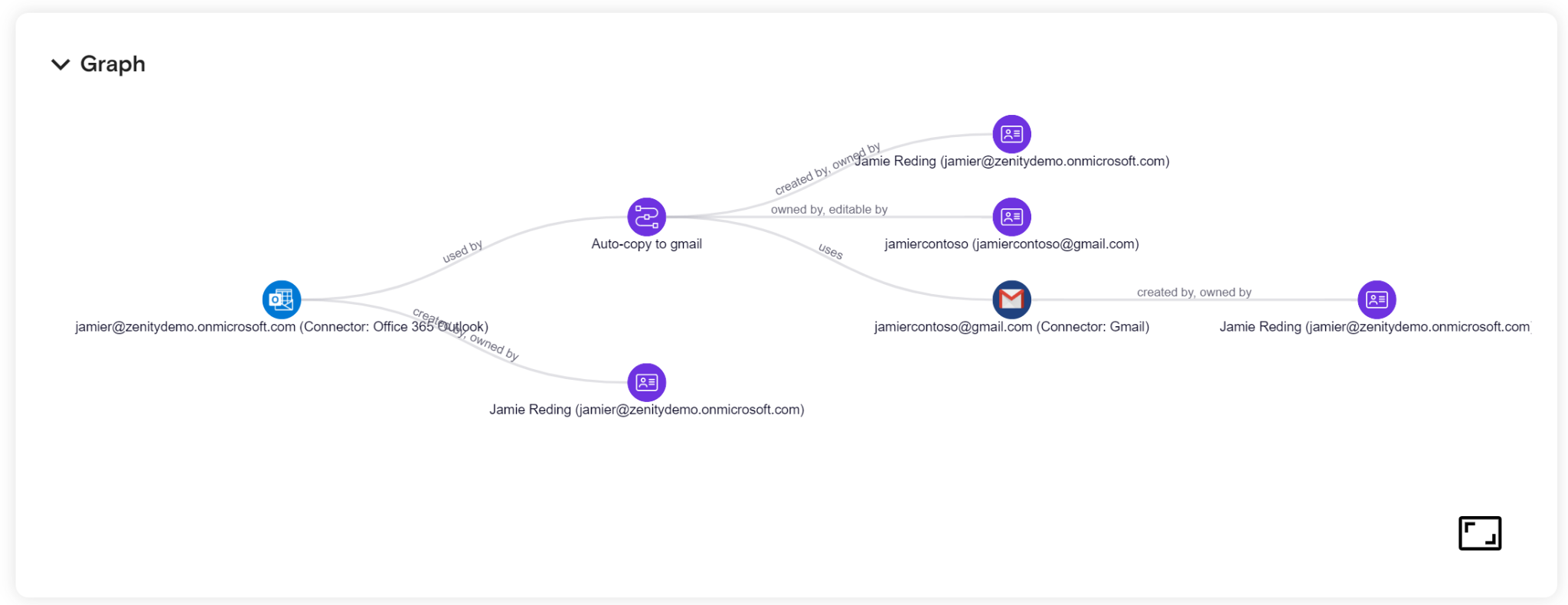
Visibility Dashboard
-
The Zenity Visibility Dashboard offers valuable insights into the data collected from the Low-Code/No-Code platforms, It provides insights on top of the Inventory view.
-
The Visibility Dashboard acts as an aggregator of all data collected from your Low-Code / No-Code application inventory, and is a key component of bringing visibility throughout the business.
For a detailed description of each widget please refer to the User-Guide.
New Table Experience
Zenity table capabilities were updated to provide an easier experience for our users, including:
-
Resizing of columns
-
Add/Remove Columns
-
Reposition columns
New Knowledge Center
Our brand new knowledge center is out with all of our customer documentation.
Now customers have easy access to critical documentation in a unified location. including Integration Docs, User-Guide, Release notes, and more, check it out here.
New Violation Rules (a full description can be found in the Zenity policy page)
-
ZN_P00110 - Custom connector is using Openai API
-
ZN_P00107- Connection using the OpenAI connector
-
ZN_P00116 - Vulnerable gateway version
-
ZN_P00115 - Flow is using OpenAI API
Rules Deletion Announcement
The below rules were privesilouy deprecated and are about to be deleted.
This means all violations triggered from the below rules will be deleted.
Rules deprecation is a normal process Zenity is doing to optimze and make our rules more robust and with a higher TP ratio.
| ID | Reason |
|---|---|
| ZN_P00034 | Replaced by ZN_P00101 |
| ZN_P00071 | Replaced by ZN_P00101 |
| ZN_P00018 | Replaced by ZN_P00102 |
| ZN_P00073 | Replaced by ZN_P00102 |
| ZN_P00042 | Replaced by ZN_P00102 |
| ZN_P00059 | Replaced by ZN_P00104 |
| ZN_P00026 | Replaced by ZN_P00104 |
| ZN_P00012 | Replaced by ZN_P00105 |
| ZN_P00002 | Replaced by ZN_P00105 |
| ZN_P00068 | Replaced by ZN_P00099 |
| ZN_P00022 | Replaced by ZN_P00114 |
| ZN_P00023 | Replaced by ZN_P00114 |
UI/UX Improvements
-
Adjustable Dashboards side, regardless of the screen resolution.
-
Side-menu opens on hover
API Support
- Full support for all new features both in API and UI
Zenity March-2023
⭐ Highlights
New Zenity Dashboard
-
Zenity users can now benefit from a far richer view into their security posture in a single glance.
-
Full alignment with the OWASP for low-code/no-code framework.
-
View your organization adoption of low-code/no-code as a whole
-
Get a better understanding of critical resources with risk needing remediation
Integrations
-
New Workato integration
-
Zenity support the newly introduced Workato API token that supports Workato environments natively.
Access Management
- Zenity now supports client API secret rotation
Security Engine Enhancements
- Zenity's security engine now scans for PIIs and Other types of Sensitive data in PowerPlatform, that is misused or unhandled or in other forms can be exploited.
Ad-hoc Remediation
-
Zenity now supports:
-
taking ownership over Custom Connector to help with investigation of custom code, hard-coded secrets and other use-cases.
-
Stopping all flows for a risky connection
Bulk actions
- Users can now execute all internal actions in bulk on violations. > For example, 'Exempting' or 'Acknowledging' violations in bulk.
[Additional features]{.underline}
Inventory
-
For each PowerPlatform flow which is suspended we added the suspension time to help customers understand when DLP enforcement took place.
-
Zenity now supports user department as a way to view risk in individual departments.
Policy improvements
- Policy Configuration is now a unified experience across all rules, including environments and trusted domains.
New Violation Rules (a full description can be found in the Zenity policy page)
- ZN_P00097 - Hard coded secret in HTTP step
- ZN_P00099 - Sensitive data handled by a flow
- ZN_P00101 - Risky business data connector
- ZN_P00102 - Connection might be implicitly shared
- ZN_P00103 - Flow runs log expose sensitive data
- ZN_P00106 - Unblockable connector configured in DLP policy
- ZN_P00108 - Flow trigger exposes sensitive data
- ZN_P00110 - Flow has a step with hard coded secrets
- ZN_P00112 - Flow has an insecure sensitive step
Customer annoncement - breaking changes
Deprecated Rules (All deprecated rules are marked as (Deprecated) and will be deleted within 30 days alongside their violation.
- This means that violation notes, violation acknowledgements will be removed and playbooks that use violations will no longer work and will have to be updated.
- Please use the below table to view the deprecated rules and asses the impact while switching to the new and improved rules.
| ID | Reason |
|---|---|
| ZN_P00012 | Replaced by ZN_P00105 |
| ZN_P00018 | Replaced by ZN_P00102 |
| ZN_P00002 | Replaced by ZN_P00105 |
| ZN_P00026 | Replaced by ZN_P00104 |
| ZN_P00034 | Replaced by ZN_P00101 |
| ZN_P00042 | Replaced by ZN_P00102 |
| ZN_P00059 | Replaced by ZN_P00104 |
| ZN_P00071 | Replaced by ZN_P00101 |
| ZN_P00073 | Replaced by ZN_P00102 |
| ZN_P00093 | Replaced by ZN_P00097 |
API Support
- Full support for all new features both in API and UI
Zenity Dec-2022
⭐ Highlights
User Management
- Zenity Administrators can now easily control & manage RBAC within Zenity.
-
Administrators can Invite new users, delete existing ones and control their respective permission level.
-
Admin
- Operator
- Viewer
API Management
- Zenity Administrators can now access their account API key and benefit from Zenity's 'API 1st approach'.
- Zenity full functionality is available via API.
Playbook Marketplace
- Zenity users can now benefit from a range of pre-defined playbooks > now users can create custom playbooks from scratch or choose from the marketplace. > The playbooks deliver core value for common use-cases we identified across our customers base. > Zenity empowers its users to set automated guardrails through playbooks for a risk reduction proactive approach.
Customer Support Channel
- Have a question? Want to suggest an idea or feature? Did you come across a Defect? Zenity is opening its door for customers to communicate transparently with our Support team through the new Zenity 'Support' page.
3rd Party Integration via Webhook
- Zenity Users can now integrate with 3rd party platforms such as > SIEMs and SOARs and other LCNC platforms which support webhook. > Zenity implements the Webhook as a part of our automation Pillar using playbooks.
PowerPlatform New Integration Methods
-
Service Principal
-
In the effort of providing an easier and more secure integration Zenity now supports an integration through a Service Principal, which removes the need to authenticate with a user's credentials > For more information, reach out to support.
Inventory
-
New visibility - PowerPlatform Flows Using 'AI Builder' > User can easily find all the flows in PowerPlatform that use AI Models > through the Predefined queries in the Inventory.
-
Added support for Deleted PowerPlatform 'Instagram' connectors > All existing connections are tagged properly and customers are able to clean them up if needed.
-
Added 'Created By' to the Inventory/violation/hygiene tables so Zenity users can easily view & filter who created the resources who triggered the violation.
-
Display the 'CDS URL' for dataverse's environments
-
Added support for Identity provider ID for each user to distinguish between proper email and UPN.
-
Added support for unique resource id to handle resources with duplicate names
-
Display AI Models and the Flow that uses them
Playbooks
-
Clone Playbooks
-
Users can now copy their playbook instead of creating new one from scratch
-
Playbook trigger improvements
-
Users can now freely search through the violation rules in the playbook trigger instead of going through one by one > In addition, the rules are sorted based on the OWASP TOP 10 for Low-Code/No-Code.
-
Support for 'Connectors' in the Playbook trigger > Enables users to focus only on violation originated by a specific connector. For example, a rule that finds personal data access but will trigger the playbook only if the data access was to 'Google Drive'.
New Remediation Actions
-
Support for 'Stop' & 'Start' on PowerPlatform flows using one click fix approach
-
Support 'Quarantine' and 'Unquarantine' for Canvas app to block user access
-
Support for 'Stop' & 'Start' on recipes in Workato to stop unapproved use
-
Update the 'Add Owner' action to add a co-ownership permission to the user instead of replacing the original user.
-
Support for 'Stop all recipes' for a suspicious connection in Workato, so users can easily block a problematic connection on their environment.
-
Email Action improvement > The email action now supports pre-defined placeholders so users can build their own email template based on the violation/resource placeholders.
-
3rd Party Integration via Webhook
-
Zenity Users can now integrate with 3rd party platforms like SIEMs and SOAR and other LCNC platforms who support webhook. > Zenity implements the Webhook as part of our automation Pillar using playbooks.
New Violation Rules (a full description can be found in the Zenity policy page)
-
ZN_P00086 - Flow uses insecure 'Http' step
-
ZN_P00087 - Portal app allows sign-in using untrusted identity provider
-
ZN_P00088 - HTTP step without authentication method
-
ZN_P00089 - Environment PCF is enabled
-
ZN_P00090 - Dataverse auditing is disabled
-
ZN_P00091 - CanvasApp with custom code component (PCF)
-
ZN_P00092 - PII hard-coded in a flow
-
ZN_P00093 - Potential secret leakage
-
ZN_P00094 - DLP enforcement failure
Rule Engine Improvements
-
In the effort of providing more quality detections, the Zenity rule engine was upgraded to trigger violations for designated rules only if the resource in question is indeed active. This will drastically reduce the amount of current open violations.
-
Improve ZN_P00086 & ZN_P00088 to exclude cases where the secret is properly handled by Azure Key Vault.
API Support
- Full support for all new features both in API and UI
UI/UX
- Users can now review the violations or resource using the Up/Down buttons on keyboard navigation.
Zenity October-2022
⭐ Features
-
Governance
-
New "Policy" Concept Policies are a part of the Zenity Governance pillar and assist platform administrator and security teams with applying critical guardrails to enable citizen development to be done without business impact and with security in mind. They aggregate all the security rules Zenity has to offer and help to customize them based on the organization's preference.
-
Default Policy For each Integration configured in Zenity a user has a "Default" Policy, this policy governs all the environments and resources within them by default, meaning that without doing anything the user always has the Zenity best practices guardrails in place.
-
Custom policies Custom Policies allow users to enforce different security controls based on the different environments. It means that Zenity can behave differently both for detection and response for resources found on a Production Environment versus a sandbox environment. It provides granular guardrails as there isn't a 1 fits all in security especially for enterprises.
-
Policy Settings Policy settings holds the violation rule configuration so users can now influence the actual logic of our rule engine.
-
General The General tab exposes some of the basic rule configurations you can have, for example - Allowed number of builders for a flow (to trigger in case we have too many users with privileged access over a resource) or "Allow connections to Production" (alerting in case we see a data connection between a non-production to a Production environment (and vice versa), many more are going to be added.
-
Trusted Domains The trusted domains tab lists your organization's domains, once configured Zenity will consider that in our Data Leak policies to identify data leakage and usage of our tenant accounts. The list can consist of any domain your company owns directly, through a subsidiary and also approved 3rd party domains for example a vendor that provides service to the company and needs access to your low-code/no-code platform.
-
Connectors The connectors tab controls our Data Flow rules. Data Flow rules flag potentially risk data movement. It uses categories like "Social Media", "Cloud Business Data", "High Risk" and more to explain the movement. The user can view and edit the categories to get to his desired controls. For example, an organization prohibits the use of "Google Drive". The user can now add the "Google Drive" connector to the "High-Risk" Category which means that Zenity will review all Automations in the tenant to spot if any of them is using the Google Drive from here on out and will alert accordingly.
-
-
New policy page
- The policy page now shows all violation rules grouped by the OWASP Top 10 for Low-Code/Now-code by default (a MITRE view is also available).
-
New Rule Customization
- Users can now easily change the severity level of each rule (on top of turning them on or off).
-
Environments
- Users are now able to associate different environments to their respective policy, therefore applying different security controls for different environments providing the relevant guardrails for each. For example, an Admin can decide to turn specific rules on for a Production environment and turn them off for other ones.
-
New "Playbook" Concept
Playbooks are Zenity's low-code/no-code concept for automated response.
Users are now able to create remediation workflows based on the different violations found in their tenant.
-
Playbook Execution History Users are able to view every run for any playbook and view its results.
-
New Violation Rules (a full description can be found in the Zenity policy page)
-
ZN_P00069 - Flow run logs expose sensitive data
-
ZN_P00070 - Potential IDOR vulnerability in flow
-
ZN_P00071 - HTTP connector in Business data group
-
ZN_P00072 - A public API exposed via portal apps allows anonymous access to dataverse tables
-
ZN_P00073 - A SQL connection to an Azure service that supports implicit sharing
-
ZN_P00074/75 - Critical number of privileged users in the environment
-
ZN_P00076 - Portal app local sign-in enabled
-
ZN_P00077 - A flow is using arbitrary SQL queries
-
ZN_P00078 - Custom code enabled in custom connector
-
ZN_P00079 - Plaintext HTTP communication with custom connector
-
ZN_P00080 - Custom connector missing authentication
-
ZN_P00081 - External account connection in developer environment
-
ZN_P00082 - Unsafe throttling settings in portal
-
-
Deprecated Rules
ZN_P00066 - Custom connection missing authentication
Zenity now supports a new violation rule (ZN_P00080) that targets the Custom Connectors directly (not on the Connections) as the Connector is the actual root cause. This allows organizations to pinpoint the root cause of active or potential attack vectors, such as: unsupervised custom code execution, lack of authentication to organization backend services and insecure HTTP communication. The rule ZN_P00066 will soon be deprecated and all violations created for affected Connections will be auto-resolved, so you can focus on the new violations on the Custom Connectors themselves which are the root cause.
-
API Support
-
Full support for all new features both in API and UI
🌓 Enhancements
-
Inventory
-
Added the "Maker" URL for PowerPlatform Applications and Flows so an admin can view them as if he is the one who built them in the source platform rather than the Admin center.
-
All users are now displayed with their respective email addresses
-
Endpoint information extraction for more connection such as: SQL, HTTP related connections
-
Enhanced Business Criticality for Connections (on top of Applications and Automations)
-
Remediation Actions
Support for new remediation actions ad-hoc and through playbooks
Workato - Start / Stop Recipe
PowerPlatform - Start / Stop Flow, Delete Connection , Quarantine / Release Application
-
Improved filters & Search
-
Filters now behave as Facest search and are positioned to the left of the table for a more simple experience
-
New filters are available in all our tables (Inventory, Violations, Hygiene). Users are now able to filter using the "Environment Name" variable which means that for example they can find all violations in a specific environment. In addition they can filter using the "Created by" which means that they can find all violations caused by a specific user.
-
Search has been enhanced to support large volumes of data (millions of resources) mere seconds.
-
Inventory New Resource Types Support
-
PowerPlatform
-
Gateways cluster
-
Gateways
-
Zenity June-2022
⭐ Features
-
New Security Policies
-
ZN_P00068 - Potential Sensitive Data in a Flow
- Zenity runs a PII and PSI pattern match on Flows to detect > where sensitive data might be lurking such as credit card, > social security number and more.
-
ZN_P00067 - The environment has no valid admins
-
Indicates that Zenity found a PowerPlatform Environment > without an Owner, this means that the user is either > inactive in Azure Active Directory or was deleted > completely. Helps to keep the hygiene of the platform, > Zenity provides also the ability to add a new Owner or > Delete it.
-
Adding a new owner is possible if the environment > doesn’t have a security group. In case the Environment > has a security group, you can only add an Owner from > the member list in the security group.
-
-
ZN_P00065 - The connection has no valid owners
- Indicates that Zenity found a PowerPlatform Connection > without an owner, this means that the user is either > inactive in Azure Active Directory or was deleted > completely. Helps to keep the hygiene of the platform, > Zenity provides also the ability to delete the connection > if needed.
-
New Security Risk Score
-
Flows and Applications will now have a risk score based on the > violation severity, the highest takes precedence over the > lower ones.
-
New Business Criticality Score
-
Flows and Applications now have a new score that evaluates how > potentially important they are to the business, it relies on > different parameters such as:
-
The number of users it is shared with
-
The lifetime of the resource
-
Connector types used (finance, HR, CRM, etc…)
-
When was it last modified
-
And more
-
-
New Risk Mapping Widget
-
The Zenity main dashboard now hosts a heatmap that helps > pinpoint and focus on Flows and Applications by combining the > Security Risk and the Business Criticality in a single view.
-
Notes
-
Each Violation now has a new notes section for team > collaboration.
-
Each user can view all notes, and add a new note, but only the > respective user who created a note can delete it.
-
Icons
-
For ease of use, we added Icons for the different platforms and > resource types.
-
In-Product Knowledge
-
New descriptions were added for the majority of the entities in > the product using hover for a better overall experience.
-
All policies now have a new and detailed description presented > on the Policies page.
-
Advanced User Insights
-
Identifying external users in the AAD tenant
-
Identifying Inactive users in the AAD tenant
-
Identifying users and their direct managers for escalations > purposes
-
API Support
-
Full support for all new features both in API and UI
🌓 Enhancements
-
New Table Columns
-
Resource Status is now in the violation table and users can use > it to filter & sort.
-
Business Criticality Score and Security Risk Score were added to > the Inventory table and users can use them to filter and sort.
-
Improved Search
-
Support Policy ID as a search field
-
Drastically shorten search time duration
-
Improved sort & filters
-
By default Zenity will sort the violation table by highest > severity & most recent violations
-
By default Zenity will filter out “Resolved” violations
-
Introduction of new Filters on the violation page, now users can > filter using “Resource Type”, “Violation Status”.
-
Filters now support only logical combinations that can lead to > valid outcomes
-
Inventory New Resource Types Support
-
PowerPlatform
-
Portal Apps
-
Power Pages
-
-
Workato
-
Recipe
-
Connections
-
Connectors
-
Custom Connectors
-
Api Collection
-
Api Endpoint
-
On Prem Group
-
User
-
Zenity April-2022
⭐ Features
-
Inventory API support
-
As an API 1st product the Inventory abilities are available via API, users can pull the full list of resources Zenity found and their relations to one another for a holistic view over their PowerPlatform environments.
-
Zenity supports different types of resources such as:
Applications, Automation Flows, Identities, Connectors and Connections. -
RBAC Support
-
Users will now have more control over who can do what in Zenity using the different roles.
Zenity currently supports 3 roles,Viewer, Operator and Administrator. The Viewer role is a read only role, the Operator role who has read/write
access across Zenity except managing Integrations and the
Administrator role who has all of the above and can manage integrations. -
PowerPlatform Integration Authentication via OAuth authorization flow
-
Microsoft Customers are now able to validate and authenticate
their PowerPlatform Integration in Zenity via the Microsoft authentication flow. -
API Data Layer Protection
-
Adds additional validations to API requests, making sure data is thoroughly segregated between customers
-
New Platform support, Zenity now supports make.com.
-
Basic support for data collection and policies.
🌓 Enhancements
-
Canvas Apps Support in the Inventory
-
Portal Apps Support in the Inventory
-
PowerPlatform and Zapier custom connector policy adjustments
🐞 Bugs
-
Support general inventory fields extraction
-
Support related identity extraction for fields that may not exist
-
Support handling violation who are first seen in the first scan after DB migration
-
Fixed custom connector policies for Zapier integrations