Copilot Studio User-Guide
Copilot Studio, previously called 'Power Virtual Agents' is the chatbot implementation within the Microsoft PowerPlatform suite, alongside PowerApps, PowerAutomate PowerBI.
Zenity covers PowerPlatform Copilot Studio with regards to Visibility, Risk Assessment and Governance in a similar manner and standard as customers are accustomed to.
In this guide we will cover the support specifications and limitations regarding Zenity's coverage.
The Zenity User Guide is the centralized Knowledge Base for securing applications built on Low-Code/No-Code development platforms and provides in-depth details on how these applications expose your organization to more risk.
Visibility via the Inventory
The 1st question that comes to mind for customers when enabling Copilot Studio across the business is how can I view and track all the Copilots being built in my organization? As this information is not available.
Shadow Apps/Flows and now Bots are a thing of the past now as customers can view all of them within the Zenity Inventory.
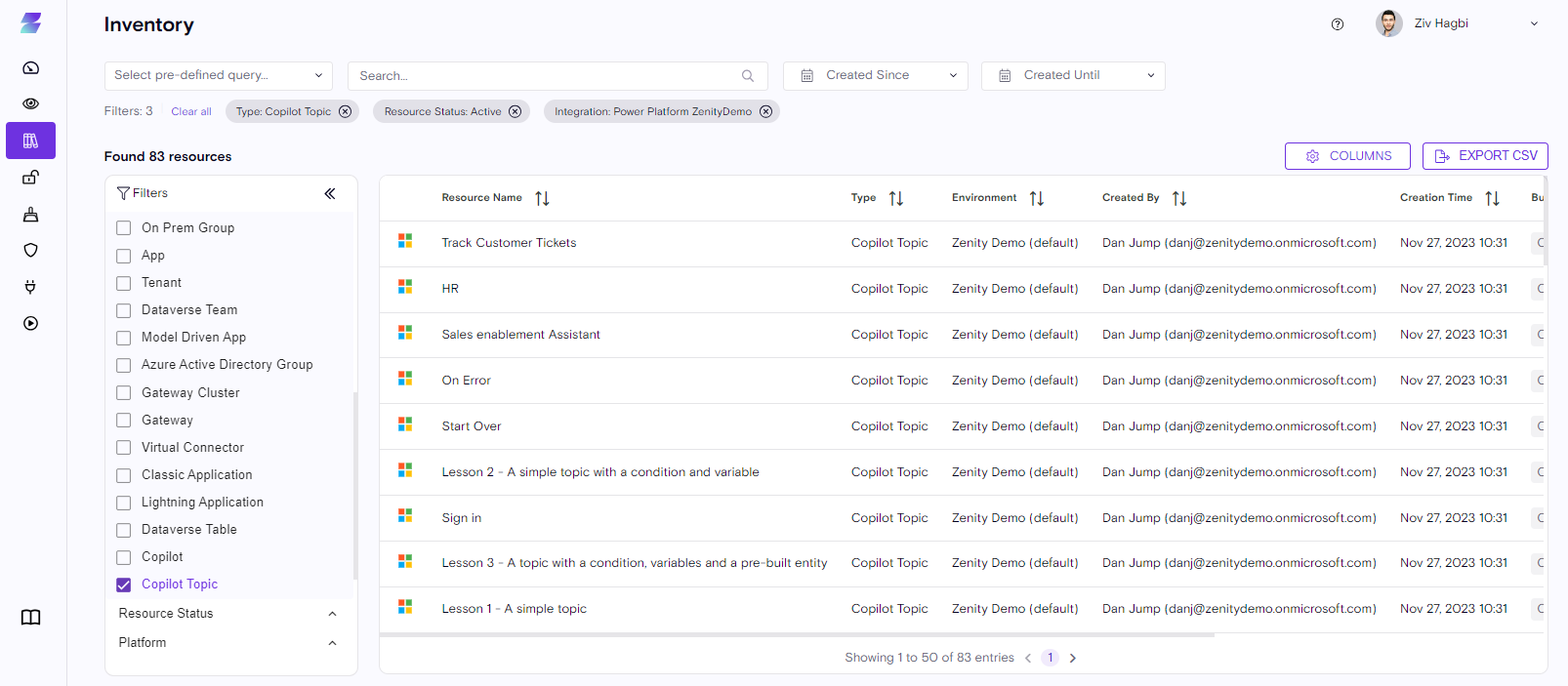
All you have to do is use the 'Resource Type' filter and select 'Copilot' to view all of them.
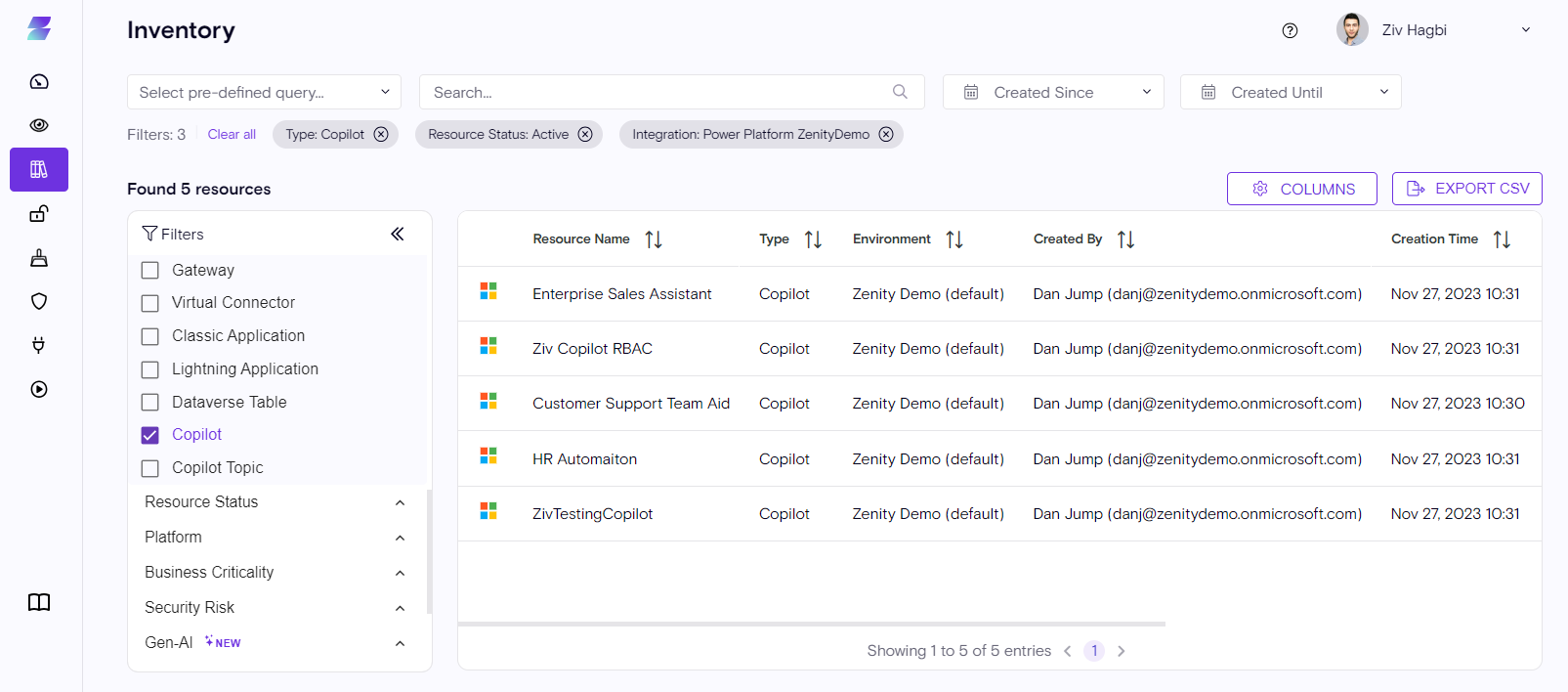
All Copilots created will be available including their high-level details, such as the user who created them, Time of creation, Environment of creation etc...
With a quick glance you can immediately have an accurate number of many Copilots were built thus far.
Zenity allows you to drill down and have a more in-depth look at the Copilot (this is also true for any other resource we surface). In case a customers needs to learn more about the resource all he has to do is click on the Copilot itself.
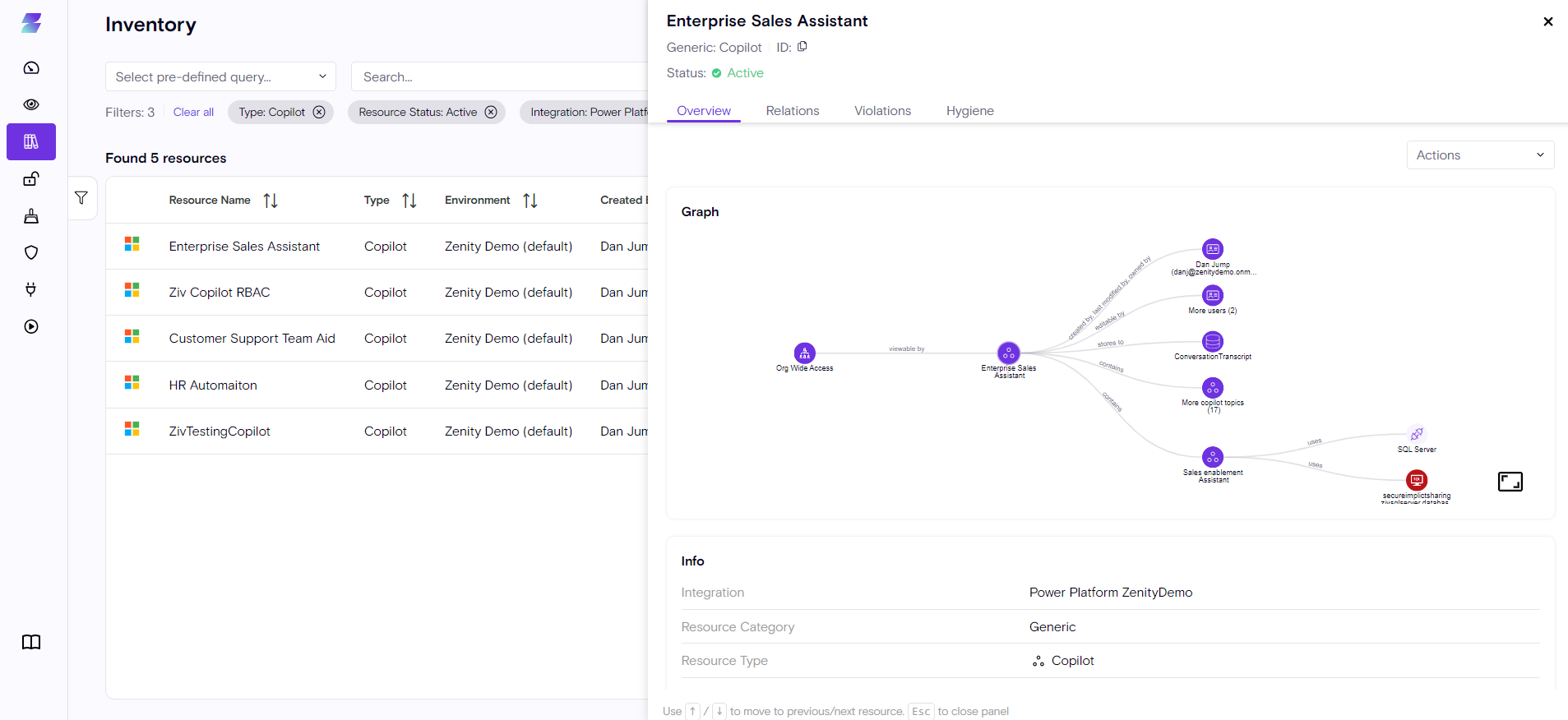
What extra information customers are gaining from this view?
Graph
Visual Context via the Zenity Graph
- Through the Zenity Graph customers can see how every resource relates to the Copilot Itself, for example, what data connections are used or which users have access to it.
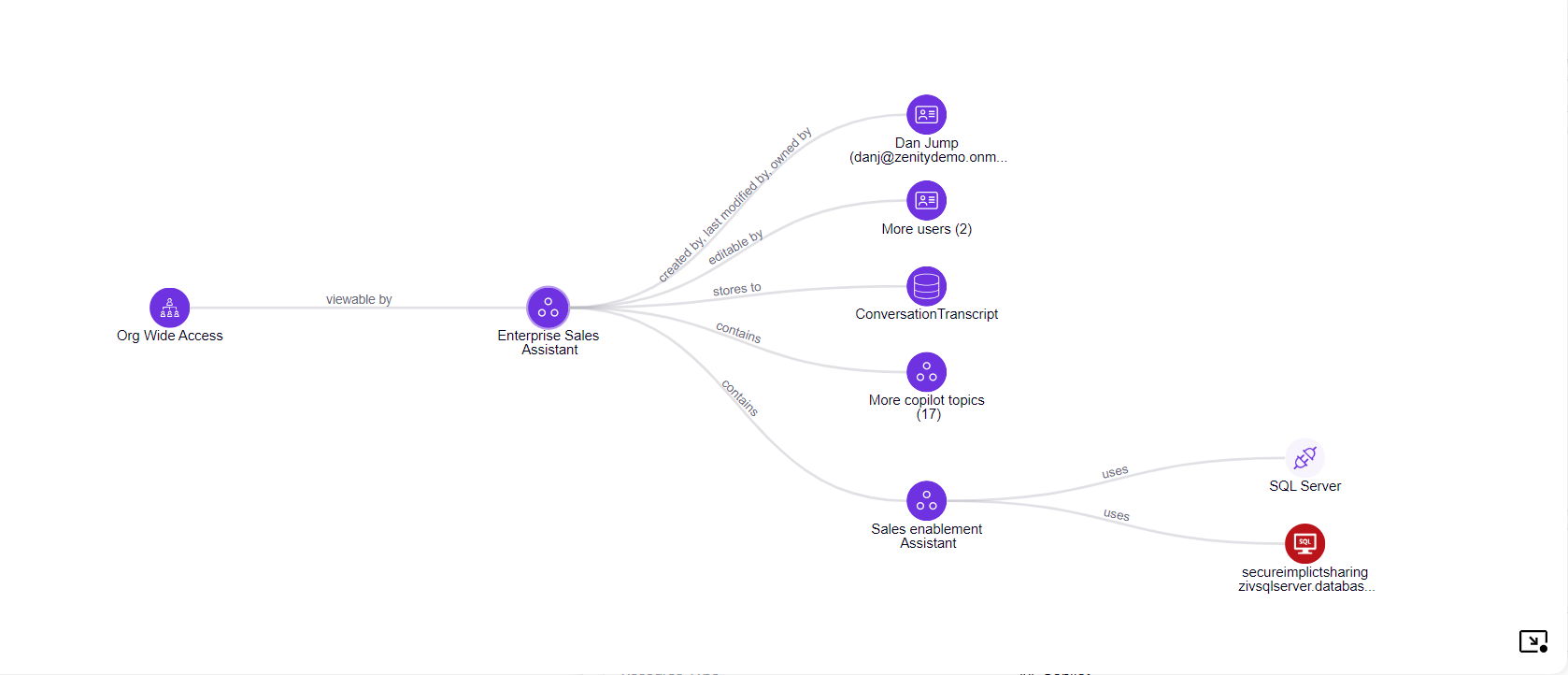
Zenity supports the following resource and resource relations for Copilot Studio, reflected in our Graph.
- Copilot <-> Copilot Topics
- Copilot <-> Identities
- Including Users, Guests & Groups
- Including Users, Guests & Groups
-
Copilot <-> Access
- Org-Wide Access ,allowing anyone in the organization to communicate with the bot).

- Public Access, allowing anyone in the world to communicate with the bot.
- Copilot <-> Transcript table
- Copilot Topic <-> Data Connections
- Copilot Topic <-> Connectors
- Copilot Topics <-> Flows
Info
The Info section of the resource side-panel will provide high-level metadata about Copilot.
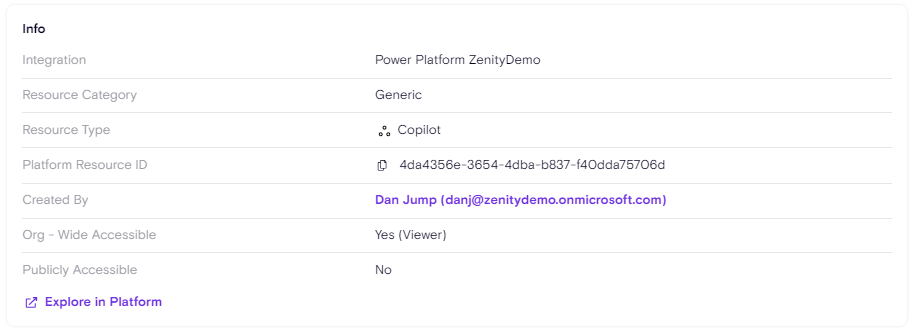
Most of the above are generic for all resources but for Copilot we added the below as well:
Org - Wide Accessible
Applicable values are "Yes (Viewer)" or "No".
-
"Yes (Viewer)" means Anyone with Azure AD authentication can communicate with the bot, given he has access to where the bot is hosted for example, a Canvas App using the bot.
-
"No" means it's not shared with the entire organizaiton.
Publicly Accessible - Yes or No
Applicable values are "Yes" or "No".
-
"Yes" means Anyone in the world can communicate with the bot, given that he has access to the Bot direct link or access to where the bot is hosted, for example a PowerPage or a custom Website.
-
"No" means it's not publicly exposed.
Additional Info
The additional info is a place where we add more custom insights about the resource.
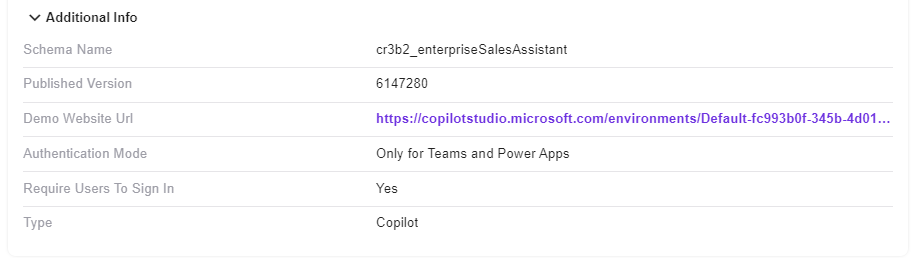
-
Demo Website URL
- The demo website url Copilot provides for every bot that is created.
It is a testing ground for checking how the bot interacts before and after it is shared with other users. The Demo Site URL will only work if the Authentication configured is 'No Authentication' or 'Manual' without selecting the 'Require users to sign in' checkbox.
-
Schema Name
- The unique name for this Copilot in Dataverse
- The unique name for this Copilot in Dataverse
-
Published Version
- The latest version of the specific Copilot Zenity scanned
(without publishing, changes in Copilot will not work)
- The latest version of the specific Copilot Zenity scanned
(without publishing, changes in Copilot will not work)
-
Authentication Mode
- No Authentication
- No AAD authentication is needed, anyone with access to the
bot url can use the bot.
- No AAD authentication is needed, anyone with access to the
bot url can use the bot.
- PowerApps and Teams
- Enforces AAD authentication, meaning anyone in the
organization with access to where the bot is hosted can
use the bot, for example Canvas apps.
- Enforces AAD authentication, meaning anyone in the
organization with access to where the bot is hosted can
use the bot, for example Canvas apps.
- Custom
- Enforces custom authentication using either AAD auth, AAD auth v2 or OAuth.
- Require Users To Sign In
- Enforces whether the users would need to sign in (authenticate
in order to use the bot.
- Enforces whether the users would need to sign in (authenticate
in order to use the bot.
- No Authentication
-
Type
- Distinguishes between the new and improved Copilot and the old Chatbots.
Environment
Identical to PowerApps and PowerAutomate Zenity can map each Copilot and Legacy Chatbot (Power Virtual Agent) to his environment to assist with data governance and sovereignty.
Timeline
Identical to PowerApps and PowerAutomate Zenity continuously scans the tenant and is able to build a timeline that reflects major changes in the life cycle of Copilot, specifically:
-
Created at and by who
-
Last modified at
-
Last published at
- Important, as it reflects whether the last modifications were taken into account, without publishing no changes are taken into consideration.
-
1st seen by Zenity
- The 1st time a Zenity scan identified the resource
Copilot Topics
Alongside Copilot Zenity also surface other Copilot related resources,
the main one is the Copilot Topic.
What is it?
Topics are the business logic of Copilot, they contain the actual workflow the bot needs to work through in actual conversations with end users.
They are composed of 'Triggers' and 'Actions'.
Triggers The phrases that can activate the relevant workflow and conversation.
Actions A set of steps the workflow needs to take in order to provide answers, for example, communicating with HTTP endpoints to retrieve data, using actions and plugins to get data using different connectors, use the GenerativeAI engine to decide what to answer and more.
The Copilot Topic can integrate seamlessly with other parts of PowerPlatform for example, PowerAutomate. Or can use data connections at will to reach out to sensitive business data.
All of which are covered by Zenity.
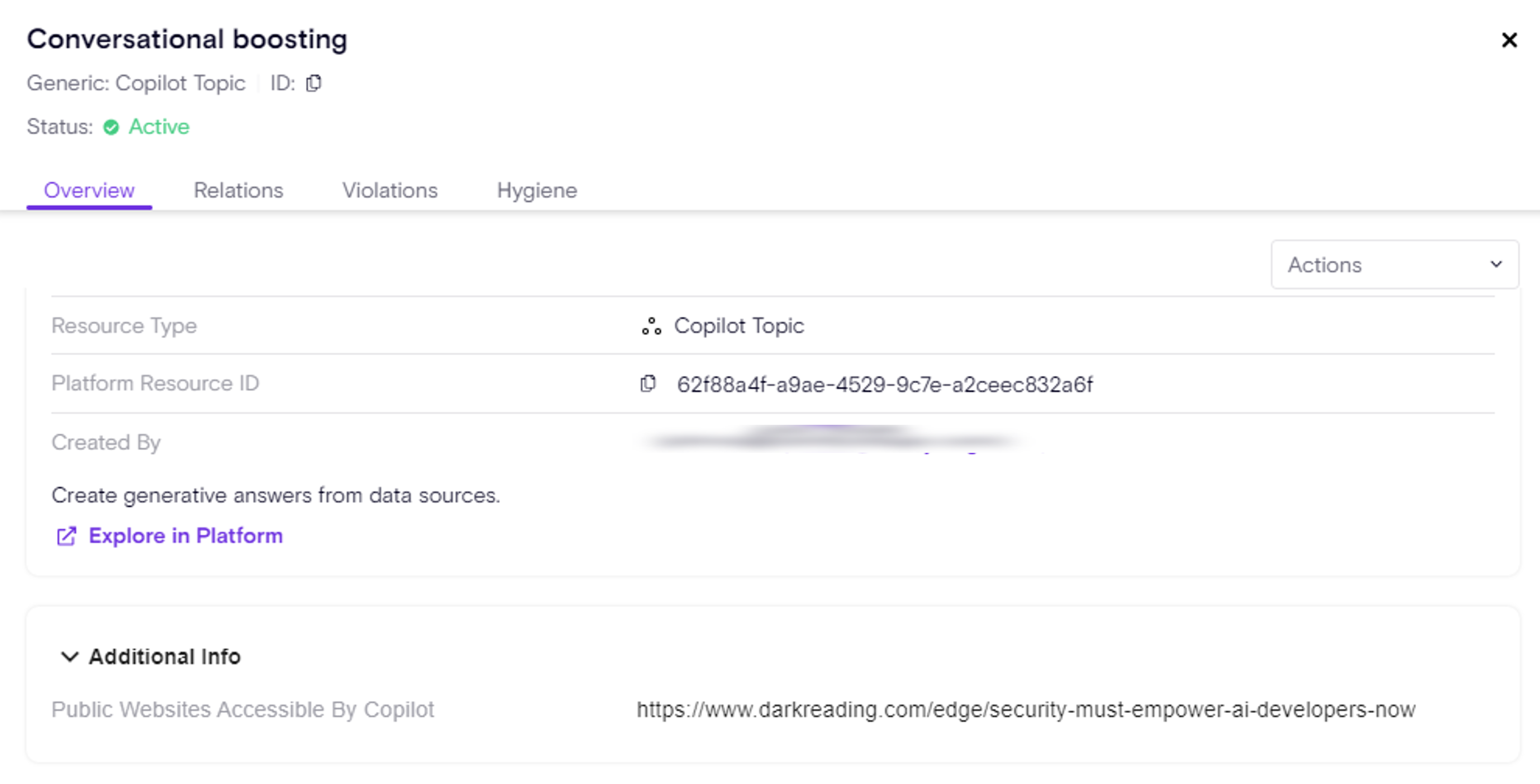
Copilot GenAI Data Access
Topics have the ability to use GenerativeAI capabilities, meaning, based on data accessible to the topic it will figure out the best answer, without an explicit script from the user who built it.
Zenity highlights these data access points used by Copilot to generate answers in real time. meaning Zenity surface where Copilot has access to public information and also Sharepoint Sites. This is critical as data accuracy & data reliance is still tricky for GenAI engines, if Copilot is using bad information what type of answers would it produce? Not to mention that it can lead to SharePoint sites leakage.
Copilot Transcripts
All Copilots (new and old) are storing the entire end users conversations in the transcript table. These conversations might potentially hold sensitive information in the form of PII/PCI/PHI.
Zenity shows the users who can access that table and view the data.
According to the Microsoft Official documentation, in the default environment any user in the default environment can access this table and view any conversations from any bot.
Risk Assessment
Zenity covers a wide range of security use-cases for Copilot Studio,
including:
-
Guest Access
-
Suspicious Endpoints communication
-
Privileged role abuse
-
Sensitive Information exposure (PII/PCI/PHI)
-
Hard-Coded Secrets
-
Authentication issues / Anonymous access
-
Resource Oversharing
-
Data Leakage
All of the above are covered in different violation rules across Zenity, the rule list for Copilot Studio keeps updating and more rules are added.
Risk Scenarios
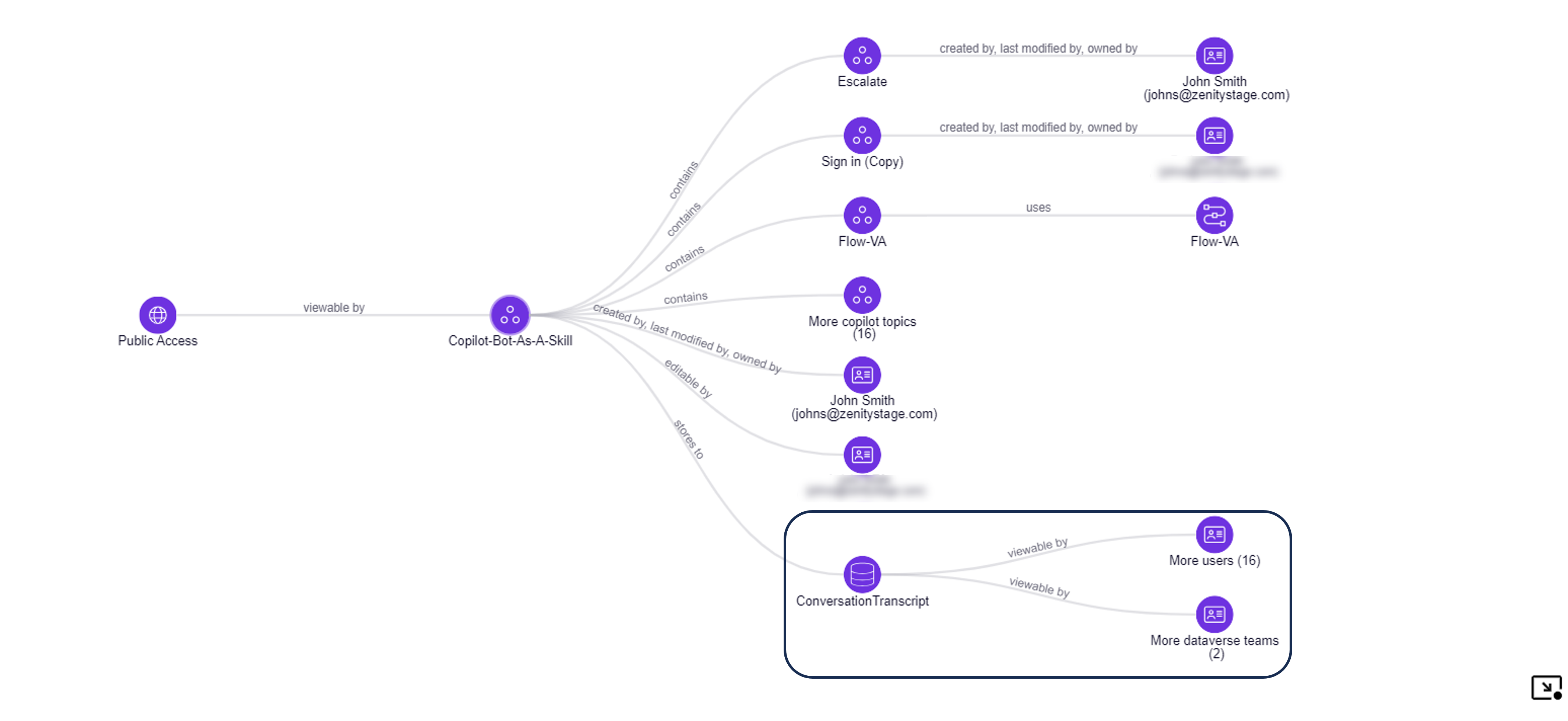
1. Copilot accessible by the entire organization exposes corporate data
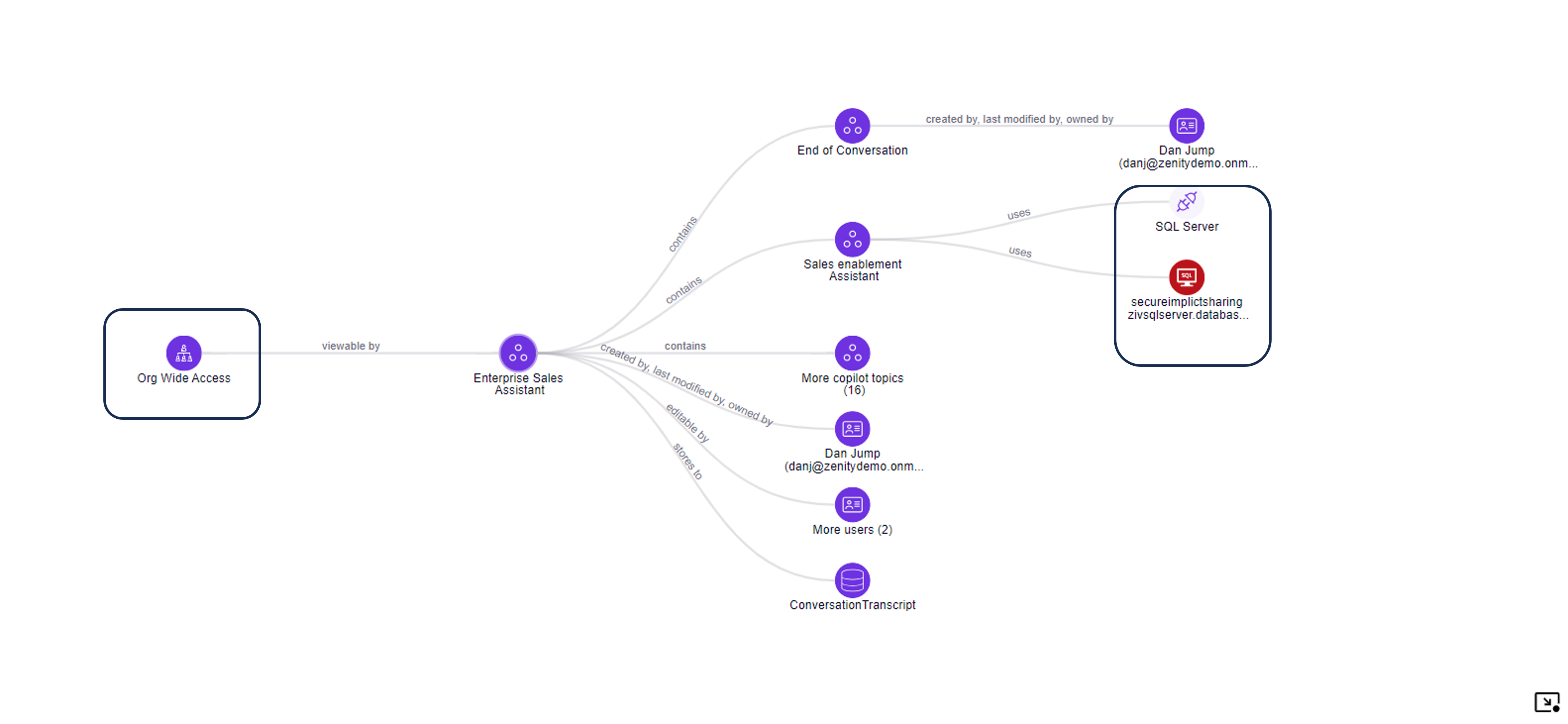
In this scenario, the Copilot is accessible by the entire organization and on the other hand connected to a SQL Server via a shared SQL Connection. Copilot connects to a SQL Server connection via a Copilot Topic, as Copilot is the businss logic of Copilot and can interact with different data sources. The Graph shows the e2e path to exploit and data that is exposed.
This graph shows that any user within the organizaiton (even guests) that can authenticate using AAD authntication can communicate with Copilot and extract data.
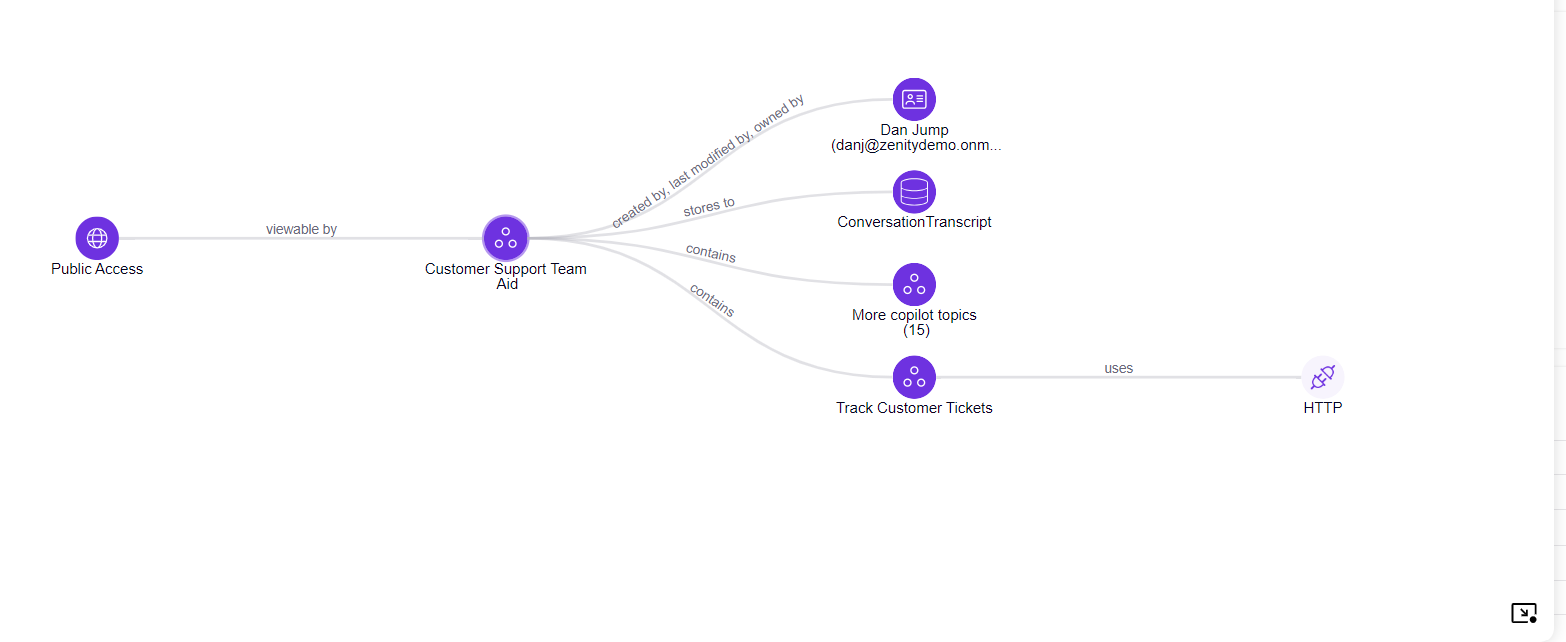
2. Copilot without authentication exposes business data via a PowerAutomate flow
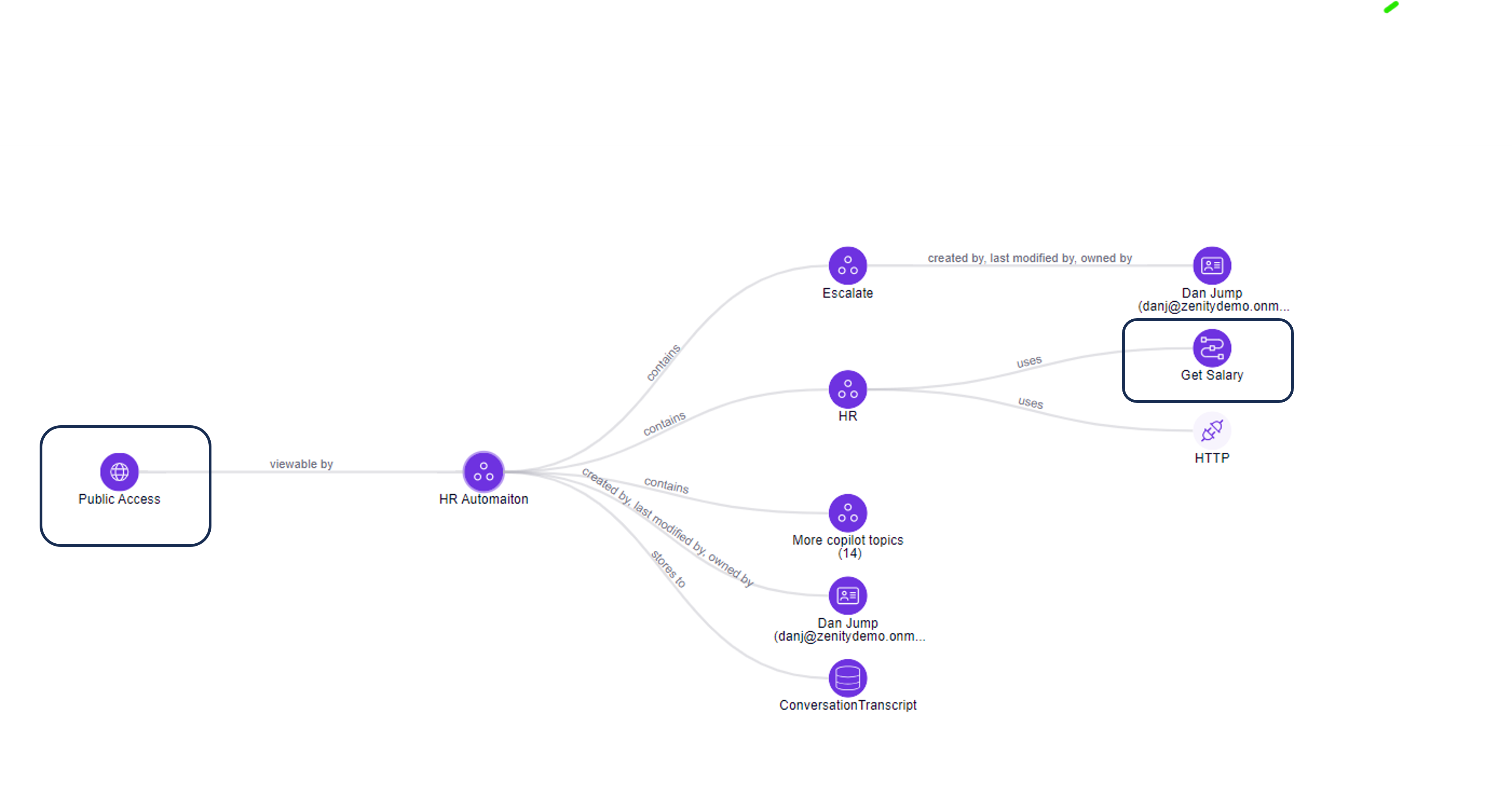
In this scenario, the Copilot is accessible by anyone (no authentication required) and on the other hand connected to business data via a PowerAutomate flow. Copilot connects to the PowerAutomate flow via a Copilot Topic, as Copilot is the businss logic of Copilot and can interact with different data sources. The Graph shows the e2e path to exploit and data that is exposed.
This graph shows that any user with access to the Copilot link (potentially anyone) can communicate with Copilot and extract data.
3. Copilot communicating with a suspicious HTTP endpoint
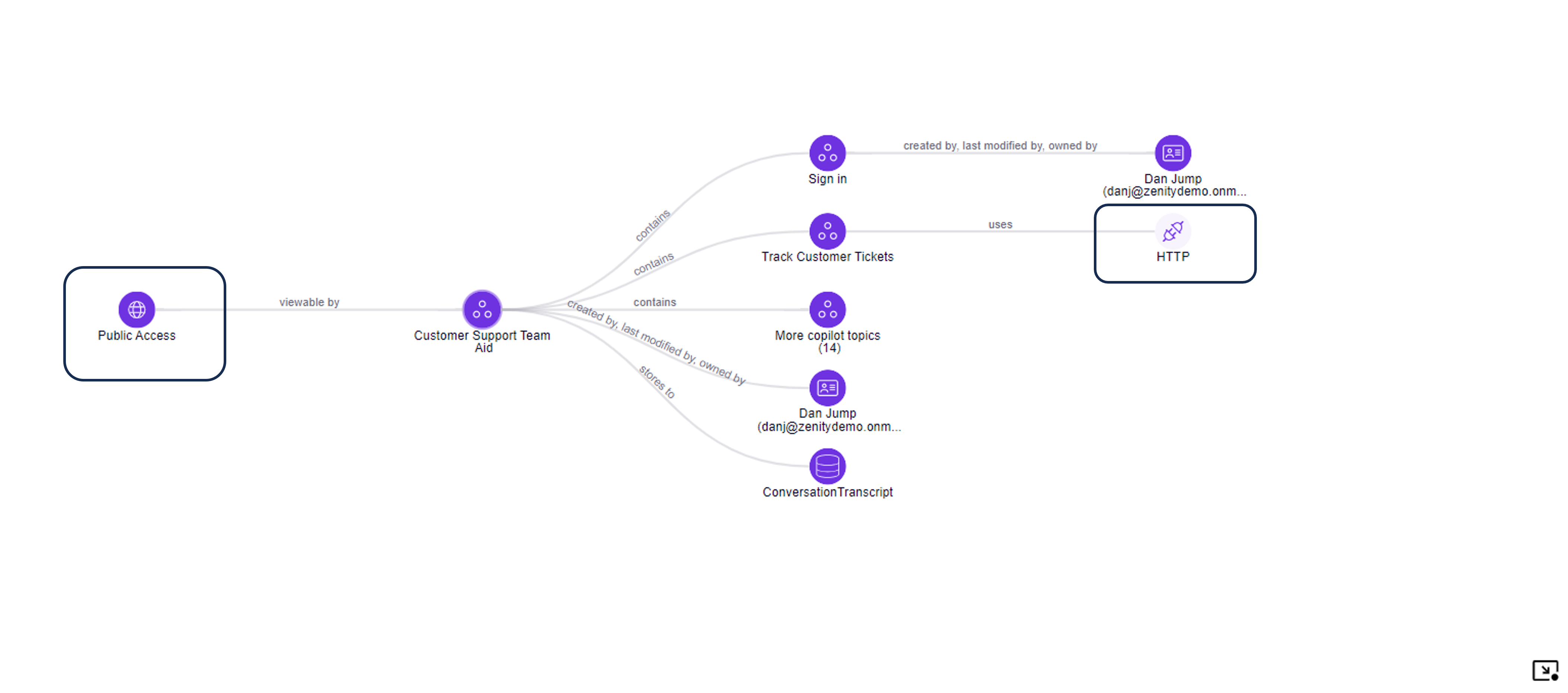
In this scenario, the Copilot is accessible by anyone (no authentication required) and on the other hand connected to business data via an HTTP request. Copilot connects to an external web server via a Copilot Topic, as Copilot is the businss logic of Copilot and can interact with different data sources. The Graph shows the e2e path to exploit and data that is exposed.
This graph shows that any user with access to the Copilot link (potentially anyone) can communicate with Copilot and extract data.
In addition, in case the HTTP URL is not within the 'Endpoint Filtering' allowed list, Zenity will flag this scenario and the violation will show the specific URL used.
4. Copilot Exposes handling coporate data exposed to Guest users
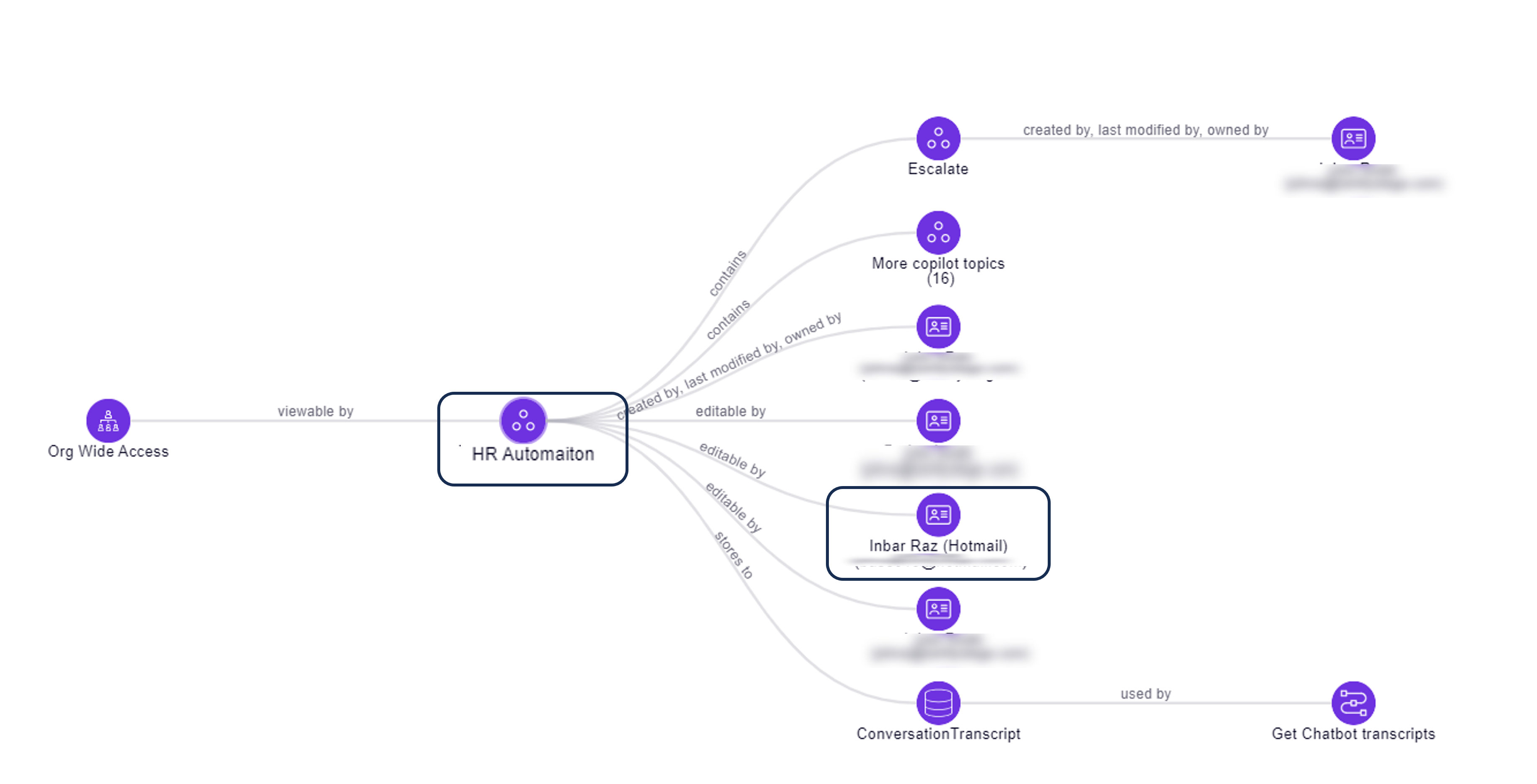
In this scenario, the Copilot is accessible by the entire organization (meaning every user in the org that can authenticated using AAD can communicate with Copilot) but in addition it is also shared with a guest user with privileged access. The guest user not only can communicate with Copilot but it can control it, and update it's logic to his will. For example, if Copilot is using Hard-Coded secrets the guest users will have access to view and use them.
This graph shows that any user within the organizaiton (even guests) that can authenticate using AAD authntication can communicate with Copilot and extract data.
The Graph shows the e2e path to exploit and data that is exposed.